The statewide next generation security operations center defend together initiative is a critical step towards a more robust and resilient security posture for the entire state. This initiative leverages cutting-edge technologies and collaborative partnerships to proactively identify and mitigate emerging threats. It will examine the concept of a statewide SOC, its history, and successful implementations. The next generation of security will be explored, along with the critical role of automation and AI in this new paradigm.
Collaboration, design, data management, public outreach, and evaluation metrics will also be addressed.
The center’s design will incorporate a comprehensive framework for incident response and threat analysis, coupled with effective data management and analytics to support timely and informed decisions. Public-facing security information will be paramount in fostering trust and transparency, while security metrics and evaluation will ensure the initiative’s continued effectiveness. Finally, the ‘defend together’ approach will highlight the importance of collaboration and shared responsibility in safeguarding the state.
Introduction to Statewide Security Operations Center
A statewide security operations center (SOC) is a centralized hub for monitoring and responding to cybersecurity threats across an entire state. It leverages shared resources, expertise, and technology to improve the security posture of all state agencies and critical infrastructure. This centralized approach allows for a more coordinated and effective response to threats that may impact multiple entities.The concept of a statewide SOC stems from the growing interconnectedness of digital systems and the escalating sophistication of cyberattacks.
A single, unified approach to threat detection and response is often more effective than fragmented efforts across numerous individual agencies. This concept is increasingly recognized as crucial for defending against sophisticated cyber adversaries.
History of Statewide SOCs
The development of statewide SOCs has paralleled the evolution of cybersecurity threats and the increasing reliance on digital infrastructure. Early SOCs focused primarily on detecting and responding to network intrusions. As cyber threats became more complex, the need for centralized, coordinated response became apparent. Over time, statewide SOCs have expanded their scope to encompass broader security concerns like data breaches, phishing attacks, and ransomware campaigns.
The statewide next-generation security operations center, “Defend Together,” is a crucial initiative. While exploring new security measures, it’s also fascinating to see how these advancements are affecting mobile experiences, like the new Android 15 DP2 Pixel Fold swipe-up continue feature here. Ultimately, both initiatives highlight a commitment to better security and user experience, a trend that’s shaping the future across many sectors.
Examples include the establishment of specific government bodies dedicated to cybersecurity and incident response.
Examples of Successful Statewide SOC Implementations
Several states have successfully implemented statewide SOCs, achieving demonstrable improvements in their security posture. One example is the establishment of a comprehensive cybersecurity framework that includes mandatory security controls for all state agencies. Another model includes collaborative partnerships with private sector cybersecurity firms, enabling the sharing of threat intelligence and best practices. These examples illustrate the potential of statewide SOCs to effectively address the evolving threat landscape.
Key Benefits of a Statewide SOC
A statewide SOC offers significant benefits, including improved threat detection and response, reduced costs through shared resources, enhanced security awareness and training, and increased collaboration between state agencies. These benefits stem from the centralized approach, allowing for faster response times, better threat intelligence sharing, and more effective coordination.
- Improved Threat Detection and Response: By consolidating resources and expertise, a statewide SOC can identify and respond to threats more quickly and effectively than individual agencies could on their own. This centralized approach enhances the speed and efficiency of incident response, reducing the potential for damage and disruption.
- Reduced Costs Through Shared Resources: Statewide SOCs leverage shared resources such as personnel, tools, and infrastructure, resulting in significant cost savings compared to individual agency investments. This consolidation allows for economies of scale and maximizes the use of resources.
- Enhanced Security Awareness and Training: Statewide SOCs can develop and deliver comprehensive security awareness and training programs to all state agencies. This ensures consistent security practices and reduces the likelihood of human error, a common vulnerability.
- Increased Collaboration Between State Agencies: A centralized platform for threat intelligence and incident response fosters collaboration and communication between different state agencies. This cooperation is vital in effectively responding to complex threats that may impact multiple agencies simultaneously.
Components of a Statewide SOC
A statewide SOC typically consists of several key components, including personnel, technology, processes, and partnerships. A strong foundation in these areas is critical for the successful operation of the center.
- Personnel: A skilled and dedicated team of security analysts, incident responders, and other experts is essential. The team needs expertise in various security domains and the ability to collaborate effectively.
- Technology: Sophisticated security information and event management (SIEM) tools, threat intelligence platforms, and other technologies are vital for threat detection, analysis, and response. Advanced tools can provide automated alerts and comprehensive threat hunting capabilities.
- Processes: Well-defined incident response procedures, threat intelligence sharing protocols, and other processes are crucial for efficient and effective operation. Clear communication channels and established workflows are critical.
- Partnerships: Collaboration with private sector security firms, federal agencies, and other stakeholders is crucial for accessing threat intelligence, best practices, and resources. These partnerships enhance the overall effectiveness of the SOC.
Comparison of Statewide and Regional SOCs
| Feature | Statewide SOC | Regional SOC |
|---|---|---|
| Scope | Covers the entire state | Covers a specific region or set of agencies |
| Resources | Larger pool of resources, potentially including specialized personnel and advanced technologies | Resources are limited by the region’s size and capacity |
| Response Time | Potentially faster response time due to centralized resources | Response time may be slower due to distance and regional limitations |
| Coordination | Improved coordination across all state agencies | Coordination is limited to the region’s agencies |
| Cost | Potential for cost savings due to economies of scale | Costs may be higher due to limited resource sharing |
Defining “Next Generation” Security
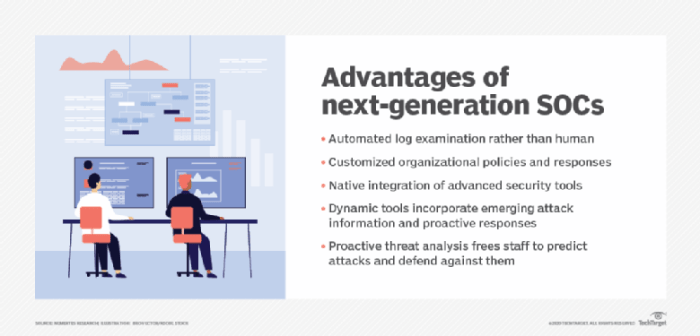
The landscape of cybersecurity is constantly evolving, driven by the ever-increasing sophistication of cyber threats and the rapid advancement of technology. This necessitates a paradigm shift in how we approach security, moving beyond reactive measures to proactive and integrated strategies. “Next-generation” security encompasses a multifaceted approach, focusing on advanced threat detection, automated responses, and the integration of cutting-edge technologies.Next-generation security is not merely an upgrade; it represents a fundamental change in mindset and methodology.
It demands a proactive, anticipatory posture, leveraging advanced technologies to identify and mitigate threats before they can cause significant damage. It’s about building resilience into the very fabric of our security systems.
Characteristics of Next-Generation Security Technologies
Next-generation security technologies are characterized by their ability to adapt to evolving threats, automate responses, and leverage advanced analytics. They prioritize prevention and mitigation over mere detection, fostering a more comprehensive and holistic approach to cybersecurity. These technologies aim to predict and preempt attacks, rather than simply reacting to them.
The statewide next-generation security operations center, “Defend Together,” is a crucial initiative for bolstering state-level cybersecurity. While this focus on collective defense is paramount, it’s also worth noting the ongoing evolution of mobile messaging platforms, such as the SVP Android invitation for Apple RCS texting on iPhones. svp android invitation apple rcs texting iphone highlights the importance of staying ahead of the curve in the tech world, which ultimately strengthens the overall security posture.
The statewide initiative, therefore, needs to adapt and consider these evolving tech trends to remain effective.
Comparison of Current and Future Security Practices
Current security practices often rely on signature-based detection, which can be ineffective against unknown or polymorphic threats. Future trends lean towards behavioral analytics, machine learning, and AI-powered threat intelligence. This shift allows for a more dynamic and adaptive security posture, enabling organizations to respond to threats in real-time. Traditional security models often struggle to keep pace with the ever-changing threat landscape, whereas next-generation security systems are designed for adaptability and resilience.
Emerging Threats and Vulnerabilities Impacting States
States face unique challenges in cybersecurity due to their critical infrastructure and sensitive data. Emerging threats like ransomware-as-a-service, supply chain attacks, and nation-state-sponsored cyber espionage pose significant risks. The growing interconnectedness of systems across government agencies increases the potential for widespread disruptions. The use of advanced persistent threats (APTs) that remain undetected for extended periods is also a critical concern.
Cyberattacks on state-level systems can have devastating consequences, impacting public services and citizen trust.
Role of Automation and AI in Next-Generation Security
Automation and artificial intelligence (AI) play a pivotal role in next-generation security. AI-powered tools can analyze vast amounts of data to identify patterns indicative of malicious activity, automate incident response, and predict potential threats. This allows security teams to focus on more complex and strategic tasks, optimizing their effectiveness and reducing response times. Automated threat hunting and response processes are increasingly crucial in maintaining a proactive security posture.
Framework for Evaluating Next-Generation Security Solutions
A robust framework for evaluating next-generation security solutions should consider factors such as: scalability, integration capabilities, ease of use, adaptability to evolving threats, and cost-effectiveness. Evaluating solutions should also assess their ability to integrate with existing security infrastructure, ensuring a smooth transition and minimizing disruptions. The framework should also emphasize the ability to adapt to emerging threats, ensuring continuous improvement and maintaining a proactive posture.
Examples of Innovative Security Tools and Techniques
Innovative security tools and techniques include:
- Machine Learning-based Intrusion Detection Systems (IDS): These systems can identify subtle anomalies and patterns indicative of malicious activity, improving detection accuracy and response times. Examples include using anomaly detection algorithms to identify unusual network traffic patterns.
- AI-powered Threat Intelligence Platforms: These platforms collect, analyze, and disseminate threat intelligence in real-time, enabling proactive threat hunting and response. This involves integrating multiple data sources and employing predictive models to identify potential threats.
- Automated Incident Response Platforms: These platforms automate incident response procedures, reducing response times and minimizing the impact of security breaches. Automated systems can isolate compromised systems, contain the spread of malware, and restore affected systems.
Collaboration and Partnerships
Statewide security is a multifaceted challenge that demands a unified approach. Isolated efforts by individual agencies often fall short of comprehensive protection. A robust security operations center (SOC) requires seamless information sharing and coordinated responses among various stakeholders, from public agencies to private sector partners. Effective collaboration ensures that threats are identified and mitigated efficiently, strengthening the overall security posture of the state.
Importance of Collaboration
Collaboration is crucial in a statewide security context because threats often transcend jurisdictional boundaries. A single agency may not possess the resources, expertise, or complete picture of a complex cyberattack or other security incident. Sharing information and coordinating responses among multiple agencies provides a more comprehensive understanding of the threat landscape, leading to faster incident response and reduced impact.
Information shared across agencies helps build a stronger defense against evolving threats.
Interagency Cooperation
Different state agencies possess unique capabilities and resources. For example, the Department of Transportation might have expertise in managing critical infrastructure, while the Department of Health may be crucial in responding to cyberattacks affecting healthcare systems. By leveraging each agency’s strengths, a collaborative approach can enhance overall security. This could involve joint training exercises, information sharing agreements, and established communication channels to ensure seamless coordination during emergencies.
Public-Private Partnerships
Public-private partnerships are essential for enhancing statewide security. Private sector entities often possess specialized knowledge, cutting-edge technologies, and real-time threat intelligence that can complement government efforts. These partnerships allow for the exchange of information and best practices, leading to a more robust and adaptive security framework. Private companies can contribute to early warning systems and incident response capabilities, bolstering the state’s overall security posture.
Successful Collaboration Examples
Several examples highlight the effectiveness of interagency collaboration. One notable example is the establishment of regional threat intelligence sharing centers, which bring together various law enforcement agencies and private sector entities to share information on emerging threats. Another example involves state-level initiatives that facilitate collaboration between healthcare providers and cybersecurity experts to protect sensitive patient data from breaches.
These collaborations often lead to faster detection and response, mitigating the impact of security incidents.
Information Sharing Protocols
Clear protocols for information sharing are crucial for maintaining trust and efficiency among partners. These protocols should Artikel the types of information to be shared, the methods of sharing (e.g., secure communication channels, dedicated platforms), and the roles and responsibilities of each partner. Standardized reporting formats and clear communication channels are essential for effective information exchange and to ensure consistent responses to security incidents.
Potential Partners for a Statewide SOC
| Partner Category | Potential Partners | Contribution |
|---|---|---|
| Law Enforcement Agencies | State Police, Local Police Departments, FBI | Threat intelligence, incident response, investigation |
| Government Agencies | Department of Transportation, Department of Health, Department of Education | Protecting critical infrastructure, sensitive data, and public services |
| Healthcare Providers | Hospitals, Clinics, Insurance Companies | Protecting patient data, ensuring continuity of care |
| Private Sector Entities | Financial Institutions, Telecommunication Companies, Critical Infrastructure Providers | Specialized expertise, threat intelligence, incident response |
| Academic Institutions | Universities, Research Labs | Research and development, threat analysis, training |
Security Operations Center Design

Building a statewide Security Operations Center (SOC) is a complex undertaking, requiring careful planning and execution. This involves more than just throwing together some tools and hoping for the best. A robust statewide SOC needs a well-defined architecture, a clear incident response process, and a dedicated team of skilled professionals to effectively detect, respond to, and mitigate threats across the entire state’s digital infrastructure.The design of a statewide SOC must consider the unique challenges and opportunities presented by a geographically dispersed network of assets.
This necessitates a centralized approach to security monitoring and incident management while respecting the decentralized nature of the state’s various agencies and departments. Scalability and adaptability are key considerations, as the SOC’s capacity must grow alongside the state’s expanding digital footprint.
Statewide SOC Design
A statewide SOC should adopt a tiered architecture, integrating multiple layers of security monitoring and analysis. This allows for a comprehensive view of the state’s overall security posture. A tiered approach ensures that the SOC can handle both large-scale events and smaller, localized incidents. This multi-layered structure allows for effective prioritization and response, focusing resources on critical incidents while maintaining vigilance across all monitored assets.
Architecture of the Security Operations Center
The architecture of a statewide SOC should be highly modular and scalable. A cloud-based architecture provides flexibility and scalability, allowing for easy integration with existing systems and future growth. Key components should include:
- Security Information and Event Management (SIEM) System: A central repository for security logs and events, providing a comprehensive view of security activity across the state. This system is critical for threat detection and incident response.
- Endpoint Detection and Response (EDR) System: For comprehensive endpoint protection and incident response capabilities, allowing for real-time monitoring and analysis of devices across the state.
- Security Orchestration, Automation, and Response (SOAR) System: For automating security tasks and workflows, speeding up incident response and improving overall efficiency. This helps streamline the process of threat hunting and incident handling.
- Threat Intelligence Platform: Integration with threat intelligence feeds and platforms allows the SOC to stay updated on the latest threats and adapt security measures accordingly.
Key Functionalities of a Statewide SOC
A statewide SOC must possess a range of key functionalities, ensuring proactive threat detection and timely incident response:
- Security Monitoring and Analysis: Continuous monitoring of security logs, events, and network traffic, enabling the identification of potential threats and anomalies.
- Threat Hunting: Proactive identification of advanced persistent threats (APTs) and zero-day exploits, using advanced techniques to find hidden threats.
- Incident Response: Implementing established processes to effectively manage and resolve security incidents, including containment, eradication, and recovery.
- Vulnerability Management: Identifying and mitigating vulnerabilities in systems and applications across the state, improving overall security posture.
Staffing and Personnel Requirements
A dedicated team of skilled professionals is crucial for the success of a statewide SOC. This includes a mix of security analysts, engineers, incident responders, and management personnel. The staffing requirements should be carefully considered based on the volume and complexity of security events.
- Security Analysts: These analysts are responsible for monitoring security logs, identifying potential threats, and escalating incidents.
- Incident Response Team: This team is responsible for managing and resolving security incidents, working with affected agencies and departments.
- Security Engineers: These engineers are responsible for maintaining and improving the SOC’s infrastructure and tools.
- Management Personnel: These individuals are responsible for overseeing the SOC’s operations, setting priorities, and ensuring compliance.
Incident Response and Threat Analysis Process
A well-defined incident response process is vital for effective incident handling and threat analysis.
- Incident Identification: Identifying and classifying security incidents based on severity and impact.
- Incident Containment: Containing the incident to prevent further damage and data loss.
- Eradication: Removing the threat and restoring systems to a secure state.
- Recovery: Recovering from the incident and implementing preventative measures.
- Post-Incident Analysis: Evaluating the incident to identify lessons learned and improve future responses.
Incident Handling Workflow Diagram
[A detailed workflow diagram, which can’t be presented here due to limitations, would illustrate the incident handling process. This diagram would visually represent the steps involved, from initial detection to final resolution.]
Data Management and Analytics
Building a statewide Security Operations Center (SOC) hinges on robust data management and analytics. Effective threat detection and response rely heavily on the ability to collect, store, analyze, and visualize security data. This necessitates careful consideration of data sources, storage methods, analytical tools, and reporting mechanisms. Privacy and security considerations are paramount in this process.
Data Collection and Storage Methods
The statewide SOC must establish a standardized approach to data collection. This involves defining specific data points relevant to security events and incidents. Centralized data repositories, leveraging cloud-based storage solutions or a combination of cloud and on-premises solutions, are crucial for scalability and accessibility. Data must be categorized and tagged consistently to facilitate searching and analysis. Data encryption throughout the lifecycle, from collection to archival, is essential to protect sensitive information.
Role of Data Analytics in Threat Detection and Response
Data analytics plays a pivotal role in identifying patterns and anomalies indicative of potential threats. Advanced analytics techniques, including machine learning and artificial intelligence, can be employed to detect subtle indicators of malicious activity that might be missed by traditional methods. Sophisticated algorithms can correlate various data points across different systems to uncover complex threats. Real-time analysis capabilities enable rapid response to emerging threats.
Data-driven insights can improve incident response strategies, minimizing damage and maximizing recovery time.
Methods for Reporting and Visualization of Security Data
Effective reporting and visualization are essential for conveying security insights to stakeholders. Clear, concise reports, generated automatically, should highlight key security metrics and trends. Dashboards with interactive visualizations, like graphs and charts, allow for quick identification of potential problems and their impact. Real-time dashboards and alerts provide immediate visibility into security events, enabling faster response to threats.
Customizable reports and visualizations cater to the diverse needs of various stakeholders, from security analysts to executive leadership.
Security and Privacy Considerations Related to Data
Protecting the confidentiality, integrity, and availability of security data is paramount. Implementing robust access controls and adhering to data privacy regulations is crucial. Data anonymization and pseudonymization techniques should be employed where appropriate. Compliance with relevant regulations, like GDPR or CCPA, is mandatory. Regular security audits and penetration testing help maintain the security posture of the data repositories.
Data Sources for a Statewide SOC
The SOC’s effectiveness depends on its ability to collect data from various sources. A comprehensive data strategy must include a diverse range of information.
| Data Source | Description |
|---|---|
| Network Security Devices (Firewalls, Intrusion Detection/Prevention Systems) | Provide logs of network traffic, security events, and potential threats. |
| Endpoint Detection and Response (EDR) Systems | Monitor and collect data from endpoints, including workstations, servers, and mobile devices. |
| Security Information and Event Management (SIEM) Systems | Collect, correlate, and analyze security events from various sources. |
| Vulnerability Management Systems | Identify and track vulnerabilities in systems and applications. |
| Application Logs | Contain details about application activities, errors, and user interactions. |
| User Activity Logs | Track user actions across different systems and applications. |
| Third-Party Systems | Collect data from third-party vendors or services integrated with the statewide systems. |
Public-facing Security Information
Public trust is paramount in any security operation, especially one as critical as a statewide security operations center. Effective communication with the public about security issues is essential to fostering understanding and cooperation. Transparency and proactive engagement can help mitigate fear, promote informed decision-making, and ultimately enhance overall security.Open dialogue and readily available information are vital to building public confidence.
By proactively addressing concerns and providing clear explanations, the security operations center can effectively manage public perception and ensure that the community feels empowered to participate in a shared security effort.
Importance of Communicating Security Issues to the Public
Effective communication builds trust and understanding between the security operations center and the public. Public awareness campaigns help prevent panic and misinformation, encouraging proactive security measures. Open communication fosters a sense of shared responsibility in protecting the community. Transparent communication, even during challenging situations, strengthens the community’s trust in the security operations center.
Different Methods of Public Awareness Campaigns
Various methods can be employed to reach diverse audiences. Public service announcements (PSAs) on radio, television, and social media platforms can disseminate vital information widely. Educational materials, such as brochures and online resources, provide detailed information and can be tailored to specific demographics. Community events, town halls, and workshops offer direct interaction and engagement with the public.
The statewide next-generation security operations center, “Defend Together,” is a really cool initiative. It’s all about bolstering security across the state, which is crucial in today’s environment. This kind of collaborative approach reminds me of the insights gained in the far cry 5 ubisoft montreal interview , which highlighted the importance of teamwork in overcoming challenges. Ultimately, initiatives like “Defend Together” are vital for protecting our communities and fostering a secure future.
Utilizing local media outlets and partnerships with community leaders enhances the effectiveness of the campaigns.
Examples of Effective Public Awareness Campaigns
Numerous successful campaigns demonstrate the power of public awareness. For instance, campaigns highlighting the importance of strong passwords and secure online practices have significantly reduced cybercrime rates. Public awareness campaigns addressing potential threats like natural disasters or infrastructure vulnerabilities have demonstrated their value in preparedness and mitigation. These campaigns effectively used diverse media channels and community partnerships to communicate critical information to the public.
The key is to tailor the message to the specific audience and the type of threat.
Importance of Transparency and Trust in Public-facing Communication
Transparency in communication is crucial. Honest and straightforward information-sharing builds trust and reduces public anxiety. Providing accurate details about security incidents, while respecting privacy considerations, is essential. Trust is the cornerstone of a successful security operation. When the public understands the procedures and actions taken, they are more likely to cooperate and remain informed.
Potential Communication Channels for Public Outreach
| Communication Channel | Description | Strengths | Weaknesses |
|---|---|---|---|
| Local News Outlets | Utilizing local newspapers, radio stations, and television channels. | Wide reach, credibility, established relationships. | Potential for limited control over message framing. |
| Social Media Platforms | Utilizing Facebook, Twitter, and other platforms for direct communication. | Direct interaction, immediate updates, diverse audience reach. | Risk of misinformation spread, potential for negative feedback. |
| Community Events | Hosting town halls, workshops, and other public events. | Direct engagement, opportunity for questions and feedback. | Limited reach compared to mass media, scheduling challenges. |
| Website and Online Resources | Creating dedicated sections on the security operations center website. | 24/7 access to information, detailed explanations. | Requires ongoing maintenance and updates. |
| Public Service Announcements (PSAs) | Creating short, impactful announcements for radio and television. | High visibility, memorable messages. | Limited time for in-depth explanations. |
Security Metrics and Evaluation: The Statewide Next Generation Security Operations Center Defend Together
Measuring the effectiveness of a statewide security operations center (SOC) requires a robust framework for evaluating performance and demonstrating its value. A well-defined set of key performance indicators (KPIs) is crucial for tracking progress, identifying areas for improvement, and ultimately, justifying the investment. This section delves into the essential metrics, evaluation methods, and benchmarks for a successful statewide SOC.A statewide SOC’s success hinges on its ability to prevent and mitigate cyber threats while maintaining operational efficiency.
Quantifiable metrics allow stakeholders to assess the SOC’s impact on overall security posture and return on investment (ROI). This section Artikels how to establish meaningful KPIs, measure effectiveness, and evaluate the SOC’s ROI.
Key Performance Indicators (KPIs)
Effective KPIs provide a clear picture of the SOC’s performance. These metrics should be aligned with the overall security objectives of the state and should be measurable, achievable, relevant, and time-bound (SMART). They must also be tailored to the specific threats and vulnerabilities faced by the state.
- Incident Detection Rate: This KPI measures the speed and accuracy with which the SOC identifies and responds to security incidents. A high detection rate indicates a well-trained and efficient team capable of swiftly responding to threats. For example, a 95% detection rate within 24 hours of incident initiation is considered a good benchmark.
- Incident Resolution Time: This metric assesses the time it takes to resolve security incidents once detected. Faster resolution times minimize the impact of attacks and maintain service availability. An average resolution time of 24 hours or less is a common goal.
- Mean Time To Recovery (MTTR): This measures the time taken to restore systems or services after a security incident. Lower MTTR signifies quicker recovery, minimizing downtime and financial losses. A target MTTR of 12 hours is a frequently cited benchmark.
- False Positive Rate: This KPI tracks the number of alerts that are not actual security incidents. A low false positive rate minimizes unnecessary investigations and resource consumption, ensuring the team focuses on genuine threats. A target false positive rate of less than 10% is desirable.
- Security Awareness Training Completion Rate: This metric measures the success of educating users about security threats. High completion rates indicate an engaged workforce and a greater chance of preventing phishing attacks and other user-related incidents.
Measuring Effectiveness
A multifaceted approach is essential to measuring the effectiveness of a statewide SOC. Metrics should not only focus on incident response but also on proactive security measures.
- Threat Landscape Analysis: The SOC should regularly analyze the evolving threat landscape to identify emerging threats and adapt security strategies accordingly. This proactive approach helps stay ahead of potential vulnerabilities.
- Vulnerability Management: Measuring the rate at which vulnerabilities are identified and mitigated demonstrates the SOC’s effectiveness in proactive security measures. Regular vulnerability scanning and patching are essential.
- Compliance with Regulations: The SOC should ensure that the state’s security practices comply with relevant regulations and standards. Measuring adherence to regulations is crucial for avoiding penalties and maintaining trust.
Return on Investment (ROI)
Quantifying the ROI of a statewide SOC involves linking security improvements to financial gains or avoided losses.
- Cost Savings: The SOC can reduce costs associated with incident response, data recovery, and legal settlements. This cost savings aspect is a key component of demonstrating ROI.
- Reduced Downtime: Minimizing downtime due to security incidents saves significant financial resources and maintains operational efficiency. The SOC should track downtime to highlight the ROI in terms of reduced service disruption.
- Improved Brand Reputation: A strong security posture enhances public trust and confidence in the state’s digital infrastructure. This can contribute to a positive brand image and, indirectly, to economic benefits.
Overall Impact Assessment
Evaluating the overall impact of the statewide SOC requires a comprehensive view of its contributions to the state’s security posture.
- Security Posture Improvement: The SOC’s effectiveness can be measured by analyzing the improvement in the overall security posture of the state’s systems and data. This is often demonstrated through reduced attack surface, increased security awareness, and better threat intelligence.
- Stakeholder Feedback: Collecting feedback from state agencies and the public provides insight into the SOC’s performance. Positive feedback and a perceived improvement in security can significantly influence the SOC’s overall impact.
- Benchmarking: Comparing the statewide SOC’s performance against industry benchmarks provides a clearer understanding of its effectiveness and areas for improvement. Benchmarks allow the SOC to set realistic goals and evaluate its performance against its peers.
Benchmarking Statewide SOC Performance
Benchmarking provides a framework for comparing a statewide SOC’s performance against industry standards and best practices.
- Industry Standards: The SOC should regularly compare its KPIs against industry standards and benchmarks established by organizations like NIST or SANS. This provides a framework for evaluating performance.
- Peer Comparisons: Comparing the statewide SOC’s performance against other statewide or national SOCs provides insights into best practices and potential areas for improvement. Regular comparisons help the SOC stay current with industry trends.
Defend Together – Collaboration in Action
The “Defend Together” concept is more than just a catchy slogan; it’s a fundamental shift in how we approach cybersecurity. It emphasizes the interconnectedness of our digital world and the critical need for shared responsibility in protecting our systems and data. Successful defense requires a collective effort, not isolated silos. This approach recognizes that no single entity possesses all the necessary resources or expertise to combat sophisticated threats effectively.Building a robust and resilient security posture requires a unified front, where organizations, agencies, and individuals work collaboratively.
This proactive approach leverages diverse skillsets and resources, leading to a stronger and more effective defense against cyber threats. This section dives into the strategies and practical steps for fostering a “Defend Together” security culture.
Importance of the “Defend Together” Concept
The “Defend Together” concept recognizes that cyber threats are complex and multifaceted. No single entity can fully protect itself or its resources. Sharing information, resources, and expertise is crucial to mitigating risks and effectively responding to threats. A collaborative approach allows for the rapid dissemination of threat intelligence, facilitating quicker responses and preventing widespread damage. The strength of the whole network is far greater than the sum of its parts.
Strategies for Building a Strong Sense of Community
Cultivating a strong sense of community is crucial for effective collaboration. Open communication channels, trust-building exercises, and shared experiences are vital components of this process. Promoting transparency and fostering a culture of mutual support and respect will establish the necessary foundation for “Defend Together” to thrive.
Steps for Fostering a Collaborative Security Culture
- Establish Clear Communication Channels: Implementing secure and efficient communication channels is essential for sharing threat intelligence, incident reports, and best practices. Regular meetings, dedicated forums, and secure platforms can foster a culture of open communication and information sharing. Examples include dedicated Slack channels, encrypted messaging platforms, or a secure internal website.
- Develop Joint Training Programs: Collaborative training programs can enhance the skills and knowledge of security professionals across various organizations. Joint workshops, webinars, and exercises can provide consistent training, increasing awareness of emerging threats and best practices.
- Create Shared Threat Intelligence Platforms: A centralized platform for sharing threat intelligence enables timely detection and response to potential attacks. This platform can be a secure repository for threat indicators, vulnerabilities, and attack vectors. This facilitates quick and effective information sharing, reducing the time to respond to incidents.
- Foster Trust and Transparency: Transparency in sharing information and vulnerabilities is crucial for building trust among participants. Regular updates, clear reporting procedures, and open communication regarding security incidents are essential.
Examples of How “Defend Together” Can Be Implemented, The statewide next generation security operations center defend together
- Joint Cybersecurity Exercises: Regularly conducting joint cybersecurity exercises, such as tabletop exercises and simulated attacks, allows organizations to practice their response procedures and improve their collective capabilities in a safe environment.
- Information Sharing Agreements: Formal agreements between organizations Artikel the process for sharing sensitive information related to cyber threats and incidents. These agreements ensure that information is exchanged responsibly and in accordance with legal and ethical guidelines.
- Collaborative Incident Response Teams: Establishing joint incident response teams allows organizations to pool their resources and expertise to handle significant security incidents more effectively. This enables a coordinated response, minimizing the impact of the incident.
Flowchart for the “Defend Together” Process
A flowchart depicting the “Defend Together” process would visually represent the steps involved in sharing threat intelligence, responding to incidents, and collaborating on security measures. It would illustrate the flow from threat detection to response, emphasizing the importance of communication and collaboration at each stage. The steps would include identification of the threat, escalation, coordination with other entities, and implementation of mitigation strategies.
(Note: A flowchart cannot be presented here, but it would clearly demonstrate the sequential nature of the process, highlighting the interconnectedness of each step and the importance of communication.)
Final Summary
In conclusion, the statewide next generation security operations center defend together initiative offers a comprehensive approach to state-level security. By combining advanced technology, strategic partnerships, and a culture of collaboration, this initiative aims to build a stronger, more resilient security infrastructure. This robust framework will enhance threat detection, response, and overall security posture for the state. The initiative is vital for a safe and secure future.




