Securing applications deployed in a vmware nsx t data center deployment guide – Securing applications deployed in a VMware NSX-T data center deployment guide is crucial for modern data centers. This guide delves into the intricacies of securing applications within a virtualized environment, providing a comprehensive approach to protecting your critical systems from threats. It covers everything from foundational concepts to advanced troubleshooting, offering actionable steps and best practices for a robust security posture.
The guide will explore various security considerations, including common threats, security controls offered by NSX-T, and best practices for secure application development. We’ll also delve into specific aspects like network segmentation, micro-segmentation, security policies, identity and access management, and comprehensive monitoring and auditing procedures.
Introduction to VMware NSX-T Data Center
VMware NSX-T Data Center is a software-defined networking and security platform that revolutionizes how applications are deployed and managed in virtualized environments. It provides a comprehensive approach to networking and security, abstracting away the complexities of traditional hardware-based solutions. This allows for greater agility, scalability, and security for modern applications. NSX-T empowers organizations to quickly adapt to changing business needs while maintaining robust security posture.NSX-T fundamentally changes the way networking and security are handled within virtualized environments.
Instead of relying on physical infrastructure, NSX-T leverages software to define and manage network policies and security controls. This virtualization allows for greater flexibility and efficiency in provisioning and managing resources. This flexibility enables rapid scaling and deployment of applications, crucial for modern business demands.
Securing applications in a VMware NSX-T data center deployment is crucial. Modernizing your approach, especially when dealing with the complexities of a virtualized environment, often requires exploring new technologies. For instance, learning about the Microsoft Surface Pro 5 Panos Panay microsoft surface pro 5 panos panay might seem disparate, but understanding how innovative hardware can influence security protocols is key.
Ultimately, securing applications remains paramount in any data center deployment.
Key Functionalities and Benefits
NSX-T’s key functionalities directly enhance application security by providing centralized control over network traffic and security policies. It offers advanced features such as micro-segmentation, which isolates applications and services to limit the impact of security breaches. The platform also provides visibility into network traffic, enabling proactive threat detection and response. These benefits lead to improved security posture and a more robust environment for applications.
Fundamental Concepts of Networking and Security in a Virtualized Environment
Virtualized environments, such as those using VMware vSphere, present unique networking and security challenges. Traditional network segmentation methods may not effectively isolate virtual machines (VMs). NSX-T addresses this by creating a software-defined network overlay that operates independently of the underlying physical infrastructure. This enables fine-grained control over network traffic, providing a more secure and manageable environment.
Architecture of NSX-T
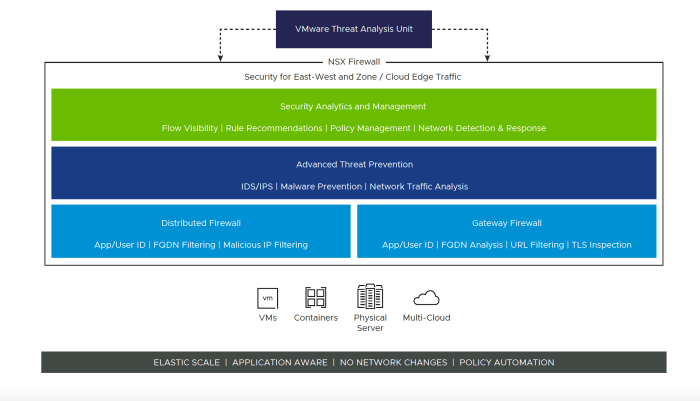
NSX-T’s architecture is modular and flexible, enabling scalability and adaptability. It consists of several key components working together to provide a comprehensive security solution. These include the NSX-T Manager, which acts as the central control plane for the entire system. The NSX-T Data Plane manages network traffic, and the NSX-T Controllers provide distributed control and processing capabilities.
The platform’s modularity enables rapid scaling to accommodate the demands of complex applications.
Common Application Deployment Scenarios
Many scenarios benefit from the capabilities of NSX-T. A typical scenario involves deploying web applications. By using NSX-T, developers can easily implement micro-segmentation policies that limit the access of unauthorized users to critical components of the application. Another example involves deploying microservices architecture. NSX-T’s network virtualization allows developers to isolate each microservice, enabling developers to isolate each microservice while maintaining communication channels between services.
These micro-segmentation policies enhance security by limiting the blast radius of a potential compromise.
Example: Deploying a Web Application
Consider a web application deployed across multiple VMs. Without NSX-T, securing the application would likely involve broad network access rules. Using NSX-T, developers can create micro-segments that isolate specific application components. This isolates sensitive data, reducing the attack surface. For example, database access would be restricted to specific VMs, improving overall security.
Application Security Considerations in NSX-T
Deploying applications in a VMware NSX-T environment presents unique security challenges and opportunities. This section delves into the specific threats faced by applications within an NSX-T Data Center, the robust security controls NSX-T offers, and the crucial role of secure development practices. Understanding these factors is paramount to ensuring the safety and reliability of applications deployed in this environment.Application security in a virtualized environment like NSX-T is multifaceted.
Threats are not just limited to traditional network attacks but also encompass vulnerabilities within the virtualized infrastructure itself. These vulnerabilities, if exploited, can lead to significant data breaches and disruptions to application services.
Security Threats in NSX-T Environments
Applications deployed within an NSX-T Data Center face a range of potential security threats. These threats can stem from various sources, including vulnerabilities in the application code itself, misconfigurations within the NSX-T infrastructure, and malicious actors attempting to compromise the virtualized environment. Common threats include unauthorized access to application resources, injection attacks targeting application logic, and vulnerabilities in the underlying virtual machine infrastructure.
Furthermore, denial-of-service attacks, which aim to overwhelm the application, are a concern in any virtualized environment.
Security Controls Offered by NSX-T
NSX-T provides a comprehensive suite of security controls to protect applications. These controls span various layers of the network and application stack, ensuring a multi-layered defense. Security features include micro-segmentation, which isolates applications and resources, and network intrusion prevention, which actively detects and mitigates malicious network traffic. Access control lists (ACLs) enforce granular control over network traffic flow, while advanced threat protection capabilities offer enhanced detection and response to emerging threats.
Securing applications in a VMware NSX-T data center deployment is crucial. Understanding the nuances of this process is key, and a solid guide can make a real difference. Fortunately, services like the sd quickstart service for software NGFW private cloud can help by offering a streamlined approach to setting up your software-defined networking (SDN) security infrastructure.
This allows for a more efficient and secure environment for your applications deployed within your VMware NSX-T data center.
Importance of Secure Application Development
Secure application development practices are crucial when deploying applications within an NSX-T environment. This includes incorporating security considerations from the initial design phase. Security should be an integral part of the software development lifecycle, not an afterthought. Implementing secure coding practices, conducting thorough penetration testing, and regularly updating applications with security patches are all vital aspects of a secure development approach.
This approach minimizes vulnerabilities within the application code itself.
Methods for Securing Applications in NSX-T
Various methods can be employed to enhance application security within an NSX-T Data Center. These methods range from implementing robust access controls to utilizing advanced security tools and services. Employing a zero-trust security model, limiting network access to only necessary resources, and using strong authentication methods all contribute to a more secure environment. Integrating security information and event management (SIEM) tools with NSX-T further enhances threat detection and response capabilities.
Comparison with Other Virtualization Platforms
Comparing security controls in NSX-T with other virtualization platforms reveals NSX-T’s strengths. While other platforms may offer basic network security features, NSX-T’s comprehensive approach, including micro-segmentation and advanced threat protection, sets it apart. NSX-T’s ability to integrate security into the underlying virtualization layer provides a more robust and unified security architecture. This integration is a key differentiator, often absent in other virtualization platforms.
Securing applications deployed in a VMware NSX-T data center deployment guide is crucial for robust infrastructure. While I’m diving deep into those configurations, I can’t help but notice how Google Messages beta is adding support for iMessage reactions, a neat feature. This functionality, as detailed in this article google messages beta adds support for imessage reactions , highlights the evolving landscape of mobile communication.
Back to the nitty-gritty of securing applications, the security measures outlined in the guide are essential for a reliable system.
Securing Applications in a VMware NSX-T Environment
Securing applications deployed within a VMware NSX-T Data Center is paramount for maintaining business continuity and data integrity. This guide delves into the specifics of securing various application types, utilizing NSX-T’s powerful micro-segmentation capabilities. Effective application security in NSX-T hinges on a multi-layered approach, encompassing network segmentation, access control, and intrusion detection.Application security in NSX-T goes beyond simply securing the network perimeter.
It involves understanding the unique security needs of different applications and implementing tailored security policies that effectively isolate vulnerabilities. This detailed guide will show you how to achieve this.
Enforcing Security Policies for Different Application Types
Implementing tailored security policies is crucial for protecting diverse application types, such as web applications, databases, and internal services. This necessitates understanding the unique vulnerabilities and attack surfaces associated with each type.
- Web Applications: Web applications often face threats like cross-site scripting (XSS) and SQL injection. Security policies for web applications should incorporate web application firewalls (WAFs) to filter malicious traffic and enforce strict input validation rules. Using load balancers with SSL offloading can further enhance security by protecting the application server from direct client connections. Implementing regular security audits and penetration testing is also crucial.
- Databases: Database servers are prime targets for data breaches. Security policies should restrict network access to only authorized users and applications. Using network segmentation to isolate database servers from other systems can significantly limit the impact of a potential breach. Implementing strong access controls and regular security updates is critical.
- Internal Services: Internal services often rely on specific protocols and communication patterns. Defining clear communication channels and restricting access to only necessary ports and services is vital. Implementing intrusion detection systems (IDS) can proactively monitor for malicious activity and alert security teams to potential threats.
Network Segmentation for Application Isolation and Security
Network segmentation is a fundamental principle in securing applications within a VMware NSX-T environment. It involves logically dividing the network into smaller, isolated segments, each containing specific applications and resources. This isolates potential vulnerabilities, limiting the impact of a breach to a single segment rather than the entire network.
- Applying VLANs and Virtual Networks: Utilizing VLANs and virtual networks allows for creating isolated network segments for different applications. This enhances security by controlling communication flows between applications and limiting lateral movement in the event of a compromise.
- Using Security Groups and Firewall Rules: Security groups and firewall rules within NSX-T provide granular control over network traffic between segments. These policies can define allowed communication paths and block unauthorized access, creating a secure perimeter around each application.
Configuring Micro-Segmentation with NSX-T
Micro-segmentation, a powerful feature of NSX-T, allows for fine-grained control over network access. It enables the creation of extremely small, isolated network segments around individual resources, significantly enhancing security and reducing the attack surface.
- Defining Security Profiles: Defining security profiles within NSX-T allows administrators to create customized security policies for specific applications and resources. These profiles dictate which ports and protocols are allowed or denied between segments, ensuring only necessary communication flows.
- Using Network Segmentation Rules: Defining network segmentation rules based on application type, function, and access requirements helps enforce granular security policies. These rules restrict access to specific services and resources, preventing unauthorized access to critical data.
Security Policies for Different Application Types
This table Artikels example security policies for different application types. These are illustrative examples and may need adjustments based on specific deployment requirements.
| Application Type | Security Policy Description | Network Segmentation | Access Control |
|---|---|---|---|
| Web Application | Enforces strict input validation, utilizes WAF, and restricts access to specific ports. | Separate VLAN for web servers, isolated from database servers. | User authentication and authorization, HTTPS enforced. |
| Database Server | Restricts network access to only authorized applications, enforces strong authentication. | Dedicated VLAN for database servers. | Network ACLs limiting access to specific IPs/applications. |
| Internal Service | Defines specific communication channels, limits access to necessary ports. | Isolated VLAN based on service function. | Application-specific authentication and authorization. |
Implementing Network Security Policies for Applications: Securing Applications Deployed In A Vmware Nsx T Data Center Deployment Guide
Implementing robust security policies is crucial for protecting applications deployed within a VMware NSX-T environment. These policies define the permissible traffic flows, preventing unauthorized access and ensuring compliance with security standards. Effective policies are essential for maintaining data integrity, confidentiality, and availability.Defining and implementing security policies within NSX-T involves several key steps. These steps are designed to establish a secure perimeter around applications, allowing only authorized traffic to interact with them.
Defining Firewall Rules for Application Traffic
Firewall rules are fundamental components of application security policies. They specify which network traffic is allowed or blocked based on various criteria, such as source and destination IP addresses, ports, and protocols. Creating precise firewall rules ensures only legitimate traffic reaches the applications, preventing malicious activity and unauthorized access.
- Identifying Application Traffic Characteristics: Determine the specific protocols (e.g., HTTP, HTTPS, SSH) and ports (e.g., 80, 443, 22) utilized by the application. This information is essential for crafting accurate firewall rules.
- Defining Source and Destination Segments: Identify the network segments from which the application traffic originates and the segments where the application is accessible. This ensures that traffic is confined to authorized networks.
- Creating Firewall Rules: Utilize NSX-T’s graphical or programmatic interfaces to create firewall rules. Specify the source and destination segments, protocols, ports, and any additional criteria. For instance, a rule might allow all HTTP traffic from the web server segment to the external network.
Implementing Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS systems monitor network traffic for malicious activity and can block suspicious traffic before it reaches the application. Implementing IDS/IPS in NSX-T provides an extra layer of security against threats.
- Choosing an IDS/IPS Solution: Select an IDS/IPS solution compatible with the NSX-T environment. Consider factors like detection capabilities, performance, and integration with existing security tools.
- Configuring IDS/IPS within NSX-T: Configure the IDS/IPS system to monitor network traffic flowing through the NSX-T infrastructure. Define rules to identify and block malicious activity based on known signatures or anomalies.
- Monitoring IDS/IPS Alerts: Actively monitor the IDS/IPS system for alerts. Investigate alerts to understand the nature of the threat and take appropriate action, such as blocking malicious traffic or adjusting firewall rules.
Designing a Network Topology for Secure Application Deployment
A well-designed network topology is critical for secure application deployment. This topology must isolate applications, control traffic flow, and provide multiple layers of security.
- Segmenting Networks: Divide the network into separate segments based on application needs and security requirements. This isolates applications from each other and minimizes the impact of potential breaches.
- Implementing Micro-segmentation: Further divide network segments into smaller, isolated sub-segments to restrict the scope of any potential security incident. This approach is particularly important for applications with sensitive data.
- Using VPNs and other security mechanisms: Consider VPNs for secure remote access and other security mechanisms to control traffic flow and access to the applications.
Application Security Policy Table, Securing applications deployed in a vmware nsx t data center deployment guide
This table demonstrates a sample configuration for securing applications within an NSX-T environment.
| Application | Security Policy | Network Segment |
|---|---|---|
| Web Server | Allow HTTP/HTTPS traffic from the internet to the web server segment, and from the web server segment to the database segment | Web Server Segment |
| Database Server | Allow database traffic from the web server segment to the database segment | Database Segment |
| Internal Application | Allow internal application traffic within the internal network | Internal Application Segment |
Identity and Access Management (IAM) within NSX-T
Identity and Access Management (IAM) is crucial for securing applications deployed within a VMware NSX-T environment. Proper IAM ensures only authorized users and applications can access specific resources, preventing unauthorized access and maintaining data integrity. This crucial layer of security adds another dimension to the comprehensive protection afforded by NSX-T.Effective IAM in NSX-T is about controlling who can do what, within the network and application infrastructure.
By defining roles and permissions, organizations can ensure that sensitive data and resources remain secure. This is especially important in today’s interconnected world where applications often span multiple environments and require access to various resources.
Authentication Methods for Application Access
Various authentication methods are available within NSX-T, enabling different levels of security and user experience. These methods include, but are not limited to, username/password, multi-factor authentication (MFA), and integration with existing identity providers. Each method offers varying degrees of security and complexity, necessitating careful consideration based on the specific security requirements. For instance, using MFA adds an extra layer of protection against unauthorized access attempts.
Authorization and Resource Access Control
Defining and enforcing granular access controls is a critical aspect of IAM in NSX-T. This involves assigning specific roles to users and granting them permission to access particular resources. These roles can be tailored to match the user’s responsibilities, thereby allowing administrators to grant specific permissions for accessing or modifying resources. For example, a developer role might allow access to specific application components but not to production database servers.
Integrating IAM Solutions with NSX-T
Integrating IAM solutions with NSX-T enhances security and simplifies management. This often involves configuring NSX-T to interact with external identity providers (IdPs) such as Active Directory, Okta, or Azure Active Directory. This integration allows for streamlined user authentication and authorization, reducing the administrative overhead. The integration also benefits from enhanced security features provided by the IdP.
Comparison of IAM Solutions
IAM Solution Pros Cons Active Directory Mature, widely adopted, and well-integrated with many existing systems. Can be complex to integrate with NSX-T. May not offer the level of granularity needed for very specific use cases. Okta Cloud-based solution with robust security features and seamless integration capabilities. Requires subscription fees; might need additional configuration to fully integrate with existing systems. Azure Active Directory Highly scalable and integrated with other Azure services. Requires understanding of Azure architecture; may introduce complexity for smaller deployments.
This table offers a basic comparison of common IAM solutions usable with VMware NSX-T. The optimal choice depends on the organization’s specific needs, budget, and existing infrastructure. Factors like ease of integration, security features, scalability, and cost should be carefully evaluated when selecting an IAM solution.
Monitoring and Auditing Application Security
Monitoring application security in a VMware NSX-T environment is crucial for maintaining a secure and reliable data center. Effective monitoring provides insights into potential vulnerabilities, allows for rapid incident response, and helps ensure compliance with security regulations. This proactive approach minimizes the impact of security breaches and strengthens the overall resilience of your application infrastructure.Application security monitoring in NSX-T involves a multifaceted approach, encompassing network traffic analysis, security event logging, and the implementation of informative dashboards.
These tools provide a comprehensive view of application security posture, allowing administrators to proactively identify and address potential risks.
Importance of Network Traffic Monitoring
Network traffic monitoring is essential for detecting malicious activity and identifying anomalies that might indicate a security threat. By analyzing patterns in network traffic, you can quickly pinpoint suspicious behavior, such as unusual data volume or connections from unauthorized IP addresses. This proactive approach significantly enhances the security posture of applications deployed within the NSX-T environment. Analyzing traffic flows helps uncover potential intrusions and provides early warning signals.
Identifying Security Events
NSX-T provides robust tools for monitoring and logging security events. These events encompass a wide range of activities, from successful login attempts to failed authentication attempts, unauthorized access attempts, and unusual network behavior. Identifying these events is vital for understanding potential security risks and enabling timely responses. Tools like NSX-T’s security analytics capabilities are crucial for collecting, correlating, and analyzing security events.
Leveraging Logging and Auditing Tools
Comprehensive logging and auditing are essential for tracking security events and maintaining a detailed record of activities within the NSX-T environment. This enables forensic analysis in case of security incidents and assists in regulatory compliance. By correlating logs from various sources, such as firewalls, intrusion detection systems, and application servers, you can gain a more complete picture of security events.
NSX-T’s logging capabilities provide detailed records of security-related actions. Robust logging allows for detailed analysis of application-level events, providing a valuable record of user activity and potential security breaches.
Security Dashboards for Tracking Application Security Posture
Security dashboards provide a centralized view of application security metrics, enabling proactive identification and resolution of security issues. These dashboards can display key metrics such as the number of security events, the types of threats detected, and the overall security posture of applications. Visualization of key metrics simplifies understanding of the security state of the environment. This facilitates timely intervention in case of escalating security threats.
Designing an NSX-T Application Security Dashboard
A comprehensive NSX-T application security dashboard should display key metrics related to application security. The dashboard should visually represent the number of security events, categorized by type (e.g., intrusion attempts, unauthorized access, etc.). It should also display the number of applications vulnerable to specific threats, the success rate of security controls, and the overall application security posture. The dashboard should be customizable to focus on specific metrics relevant to the organization’s needs.
For example, it could show the number of blocked malicious connections per application, or the rate of successful login attempts for each application. Real-time monitoring capabilities are crucial for providing immediate alerts on security incidents.
- The dashboard should present a summary of security events, allowing quick identification of anomalies.
- The dashboard should include visualizations, such as graphs and charts, for easier interpretation of data.
- Customization options should allow focusing on specific metrics crucial to the organization.
Best Practices for Application Security in NSX-T
Securing applications in a VMware NSX-T environment requires a multifaceted approach, encompassing various best practices. Implementing these strategies effectively minimizes vulnerabilities and enhances the overall security posture of your deployed applications. This section dives into key strategies for bolstering application security within an NSX-T infrastructure.
Regular Security Assessments and Penetration Testing
Regular security assessments and penetration testing are crucial for identifying potential weaknesses in your application infrastructure. These assessments, performed periodically, help uncover vulnerabilities before malicious actors exploit them. Penetration testing simulates real-world attacks, enabling you to evaluate the effectiveness of your security controls. Proactive identification of vulnerabilities empowers you to implement corrective measures and enhance your security defenses.
Thorough testing should encompass all aspects of your application’s interaction with the NSX-T network, from the application layer to the underlying infrastructure.
Maintaining Security Updates
Maintaining security updates for all components within the NSX-T environment is paramount. Regularly updating the NSX-T platform, hypervisors, and other supporting components patches known vulnerabilities, enhancing overall security. This proactive approach mitigates risks associated with exploited vulnerabilities and ensures your environment remains resistant to known threats. Staying abreast of security advisories and promptly implementing updates is essential for a robust security posture.
Security Awareness Training for Users
Security awareness training for all users is essential for a comprehensive security strategy. Training programs should educate users about potential threats, phishing attempts, and best practices for secure online behavior. By empowering users with the knowledge to recognize and avoid security risks, you significantly reduce the likelihood of internal security breaches. This proactive approach complements technical security measures and enhances the overall security posture.
Security Tools Applicable to NSX-T
A comprehensive suite of security tools is applicable to NSX-T deployments. These tools can assist in monitoring network traffic, detecting intrusions, and responding to security incidents.
- NSX-T Security Policies: Policies define access controls and security rules for virtual machines and networks. Effective policy design is essential to enforce secure network configurations, restricting access to sensitive data and resources.
- NSX-T Firewall: The NSX-T firewall provides granular control over network traffic, preventing unauthorized access and protecting applications. Detailed firewall rules and configurations are critical to ensuring the security of network traffic.
- NSX-T Intrusion Prevention System (IPS): The IPS feature identifies and mitigates malicious network activities. Its effectiveness relies on the thorough configuration and maintenance of its rule set, effectively identifying and mitigating threats.
- Security Information and Event Management (SIEM) tools: SIEM solutions consolidate security logs from various sources, providing centralized visibility into security events and potential threats. A SIEM solution can significantly improve the ability to detect and respond to security incidents, helping you maintain a comprehensive security posture.
- Network Analysis Tools: These tools analyze network traffic patterns, identifying unusual activity that might indicate a security breach. This includes traffic analysis tools, intrusion detection systems, and security information and event management (SIEM) solutions.
Troubleshooting Application Security Issues
Troubleshooting application security issues in a VMware NSX-T environment requires a systematic approach, combining network analysis, log examination, and incident response procedures. Effective troubleshooting ensures quick identification and resolution of problems, minimizing downtime and maintaining application availability and security. This section details common issues, troubleshooting methods, and incident response strategies.
Common Application Security Issues
Several issues can arise in NSX-T environments impacting application security. These include misconfigurations of security policies, network connectivity problems between applications and resources, vulnerabilities in application code, and unauthorized access attempts. Properly identifying these issues is crucial for swift resolution.
Troubleshooting Network Connectivity Problems
Network connectivity problems are a frequent cause of application security issues in NSX-T deployments. They can manifest as slow response times, intermittent connection failures, or complete inaccessibility. Troubleshooting involves checking NSX-T’s network policies, verifying firewall rules, and ensuring proper routing configurations. Using NSX-T’s built-in network diagnostics tools is essential for identifying the root cause.
Analyzing Security Logs for Identifying Security Events
Security logs are invaluable for detecting security events and understanding the context of application security issues. Logs record activities like failed login attempts, unauthorized access attempts, and suspicious network traffic patterns. Analyzing these logs in conjunction with network monitoring tools helps to quickly pinpoint potential threats and their sources.
Steps for Isolating and Resolving Application Security Incidents
A well-defined incident response process is critical for handling application security incidents effectively. This involves isolating the affected application or service, identifying the cause of the incident, implementing temporary mitigation measures, and finally, implementing permanent fixes.
Troubleshooting Guide
| Step | Action | Expected Outcome | Troubleshooting Notes |
|---|---|---|---|
| 1 | Verify network connectivity using NSX-T’s network diagnostics tools. Check the status of virtual network interfaces and logical switches. | Verify successful connectivity or identify specific points of failure. | Ensure correct configurations of virtual networks, routers, and firewalls within the NSX-T environment. |
| 2 | Review security policies to identify any misconfigurations that might be impacting application access or security. | Identify misconfigured policies or missing rules. | Verify firewall rules, access controls, and network segments related to the application. |
| 3 | Examine security logs for patterns of failed login attempts, unauthorized access, or unusual network traffic. | Identify potential threats or malicious activities. | Correlate log entries with network activity to understand the context of the event. |
| 4 | Isolate the affected application or service by temporarily disabling network access or blocking specific ports. | Prevent further damage or unauthorized access. | Carefully plan the isolation process to minimize disruption to other applications. |
| 5 | Identify the root cause of the incident, whether it is a configuration error, a vulnerability, or a malicious attack. | Understand the specific problem causing the incident. | Use appropriate tools and techniques to analyze the situation and determine the root cause. |
| 6 | Implement temporary mitigation measures to contain the impact of the incident and restore basic functionality. | Stabilize the situation and prevent further harm. | Consider temporary firewall rules or access restrictions to limit the scope of the problem. |
| 7 | Implement permanent fixes to address the root cause of the incident. | Prevent future occurrences of the issue. | Document the fix and update relevant configurations to prevent similar issues in the future. |
Concluding Remarks
In conclusion, securing applications in a VMware NSX-T environment is a multifaceted process that requires a deep understanding of networking, security controls, and application architectures. This guide provided a practical framework for implementing robust security measures. By following the detailed steps and best practices Artikeld, organizations can significantly enhance the security of their applications and maintain a resilient data center.