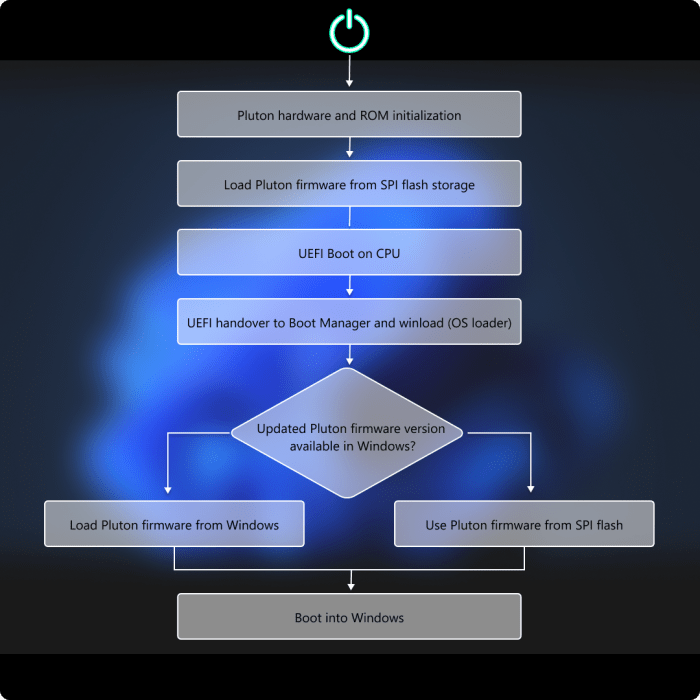
Microsoft pluton processor security windows pc – Microsoft Pluton processor security on Windows PCs is a rapidly evolving field, promising enhanced security for personal and corporate systems. This processor, designed with robust security features, integrates seamlessly into the Windows ecosystem, offering a layered approach to safeguard against emerging threats. The architectural design choices behind Pluton and its security modules are key to understanding its effectiveness. This article delves into the specifics, examining its integration with Windows security, performance implications, and potential vulnerabilities.
From hardware Trojans to malicious software, Pluton’s multifaceted security mechanisms will be explored in detail.
The article examines the Pluton processor’s role in protecting Windows PCs from various security threats, including those targeting sensitive data and operations. It details the encryption and authentication methods, as well as the integration with the existing Windows security architecture. Tables are used to compare and contrast Pluton-protected PCs with those not equipped with this technology, providing clear benchmarks.
Introduction to Microsoft Pluton Processor
The Microsoft Pluton processor is a dedicated security co-processor designed to enhance the security posture of Windows PCs. It’s not a general-purpose processor like the CPU, but rather a specialized unit focused entirely on safeguarding sensitive operations and data. Pluton’s role is crucial in modern computing, where protecting against sophisticated threats and ensuring the integrity of system processes is paramount.Pluton’s architecture is fundamentally different from traditional CPU designs.
Its core strength lies in its isolation and dedicated hardware security features. This approach allows Pluton to handle sensitive operations without compromising the integrity of the broader system. Its specialized hardware and software are meticulously designed to prevent malicious code from interfering with the security-critical processes it manages.
Architectural Design Choices
Pluton’s design prioritizes security through isolation and specialized hardware. The processor’s architecture is built upon a highly secure enclave, a dedicated and protected area of memory and processing resources. This enclave operates independently of the main operating system, limiting the potential damage from malicious software. The secure enclave’s communication with the rest of the system is carefully controlled and audited, further enhancing the security.
Furthermore, the hardware design includes advanced cryptographic capabilities and memory protection mechanisms to safeguard sensitive data.
Security Modules
Pluton’s security is underpinned by several key modules. These modules work together to provide a layered approach to security, making it extremely difficult for attackers to compromise the system.
- Secure Boot: This module verifies the integrity of the boot process, ensuring that only trusted software loads during startup. This is a fundamental security mechanism to prevent malicious code from taking control during the initial system stages. This process involves verifying the authenticity of boot components, like the operating system and firmware. This prevents malicious actors from injecting malicious code at boot time.
- Hardware-Based Enclaves: These isolated regions of memory and processing power are crucial for safeguarding sensitive data and operations. They provide a secure environment for executing sensitive code without exposing it to potential threats. These enclaves are protected from unauthorized access by the CPU, allowing for secure execution of cryptographic operations and other sensitive tasks.
- Cryptographic Acceleration: Pluton incorporates advanced cryptographic hardware, accelerating the execution of cryptographic algorithms. This is vital for tasks like digital signatures, encryption, and decryption, which are essential for secure communications and data protection. The specialized hardware accelerates these operations significantly compared to software-based implementations, improving performance while maintaining security.
Security Feature Summary
This table Artikels the key features of the Pluton security architecture, highlighting their implementation and the benefits they offer.
| Feature | Description | Technical Implementation | Security Benefit |
|---|---|---|---|
| Secure Boot | Verifies the integrity of the boot process. | Hardware-based verification of boot components. | Prevents malicious code from loading during startup. |
| Hardware Enclaves | Isolated regions of memory and processing for secure execution. | Dedicated hardware protection mechanisms. | Protects sensitive data and operations from unauthorized access. |
| Cryptographic Acceleration | Hardware acceleration of cryptographic algorithms. | Specialized cryptographic hardware. | Improved performance and security for cryptographic operations. |
| Attestation | Provides verifiable proof of the system’s integrity. | Hardware-based attestation mechanisms. | Allows for secure verification of the system’s trustworthiness. |
Pluton’s Role in Windows PC Security
Microsoft Pluton is a significant advancement in the security architecture of Windows PCs. It represents a departure from traditional security models, moving beyond relying solely on software-based defenses to incorporate hardware-level security. This innovative approach provides a stronger, more resilient defense against sophisticated threats. Pluton’s role is to enhance the overall security posture of Windows PCs, providing a crucial layer of protection against attacks that target sensitive data and critical system components.Pluton integrates deeply with the existing Windows security ecosystem, working seamlessly alongside existing security features.
It operates as a dedicated security coprocessor, performing crucial security-related tasks directly on the hardware, which is significantly faster and less susceptible to attack than software-based solutions. This hardware-level protection significantly reduces the attack surface for malicious actors.
Pluton’s Integration with Windows Security
Pluton’s integration with Windows security involves a close collaboration with the existing security stack. It doesn’t replace existing security mechanisms but rather augments them. This means that Pluton acts as a powerful supporting element to existing software security features, enhancing their effectiveness by offloading critical tasks. This cooperative approach minimizes potential vulnerabilities by distributing security responsibilities across hardware and software components.
Enhanced Security Posture Compared to Traditional Processors
Pluton dramatically enhances the security posture of Windows PCs compared to traditional processors. Traditional processors rely primarily on software-based security measures, which can be vulnerable to exploits. Pluton, by operating at the hardware level, significantly reduces the attack surface and isolates sensitive operations. This hardware-based protection makes it harder for malicious code to gain access to critical system components and sensitive data.
Microsoft’s Pluton processor, designed for enhanced security on Windows PCs, is a fascinating development. While ensuring robust security is crucial, it’s important to remember that consumer product misrepresentation, like the recent FTC fine against Razer for falsely advertising COVID masks as N95s ( ftc fines razer for misrepresenting covid masks as n95s ), highlights the need for vigilant consumer awareness.
Ultimately, secure hardware like Pluton can only be as effective as the overall system and consumer practices, which emphasizes the importance of ongoing security research and consumer education.
The isolation provided by Pluton makes it far more resistant to attacks that might compromise traditional software-based defenses.
Comparison of Pluton-Protected and Non-Pluton-Protected PCs
Pluton-protected PCs offer a significantly higher level of security compared to those without Pluton. In the case of a non-Pluton-protected PC, security relies solely on software-based defenses. These defenses, while effective, can be vulnerable to sophisticated attacks. Pluton’s hardware-based security layer provides an extra layer of defense, making it much harder for attackers to compromise the system.
This translates to a reduced risk of data breaches and system compromises. A Pluton-protected PC provides a more secure environment for users and their data.
Security Feature Comparison Across Processor Generations
| Processor Generation | Key Security Features |
|---|---|
| Pre-Pluton | Software-based security measures, including antivirus, firewalls, and access controls. |
| Pluton-Enabled | Hardware-based security measures like secure enclaves, cryptographic acceleration, and secure boot. Pluton offloads sensitive tasks from the CPU, providing greater isolation and resilience against attacks. |
This table illustrates the difference in security features between processors that do not include Pluton and those that do. The addition of Pluton brings a considerable improvement in security posture.
Security Mechanisms of Pluton
Pluton, Microsoft’s secure coprocessor, plays a crucial role in bolstering the security posture of Windows PCs. Its specialized hardware design allows it to handle sensitive cryptographic operations and data protection in a way that traditional software-based approaches cannot. This dedicated hardware isolation significantly enhances the security of the entire system.Pluton employs a layered approach to security, incorporating various mechanisms to protect against a wide range of threats.
This intricate design is crucial for maintaining data integrity and confidentiality in the face of evolving cyberattacks. The core principle is to isolate and encrypt sensitive data and operations, limiting the potential impact of a compromise.
Microsoft’s Pluton processor, designed for enhanced security on Windows PCs, raises intriguing questions. While it aims to bolster security, the complexities of implementing such a system are significant, echoing the need for thorough examination before widespread adoption. This intricate security framework needs careful consideration, especially given the recent discussions around labor practices and the challenges companies like Uber face in navigating these issues, like the issues raised in this article before Uber revolutionizes labor its going to have to explain these.
Ultimately, the long-term impact of Pluton on PC security remains to be seen, requiring continued vigilance and robust testing to ensure a safe and reliable user experience.
Hardware-Based Isolation
Pluton’s security hinges on its dedicated hardware isolation. This means sensitive operations are performed in a protected environment, physically separated from the main processor. This isolation is akin to a secure vault within a building, preventing unauthorized access to the contents. Such isolation is a fundamental defense against hardware Trojans and other attacks targeting the system’s core.
Microsoft’s Pluton processor, designed for enhanced security on Windows PCs, is a fascinating piece of tech. While it’s great for safeguarding your system, finding a reliable stream for this morning’s Bears vs Jaguars NFL London game here can be tricky. Ultimately, the security features of Pluton are still crucial to protect your valuable data and personal information, even while you’re enjoying the big game.
Advanced Encryption and Authentication
Pluton employs robust encryption and authentication mechanisms to protect data in transit and at rest. These mechanisms are designed to be resistant to sophisticated cryptanalysis techniques, ensuring that sensitive information remains confidential. For example, Pluton uses a combination of symmetric and asymmetric encryption algorithms for enhanced security.
Protection Against Hardware Trojans
Pluton’s design includes features to mitigate the risk of hardware Trojans. These malicious modifications to hardware components can bypass traditional security measures. Pluton achieves this by implementing robust hardware verification and monitoring mechanisms. These techniques examine the integrity of the hardware components, detecting any deviations from the expected behavior that could indicate a hardware Trojan.
Security Protocol Analysis
| Security Protocol | Strengths | Weaknesses |
|---|---|---|
| Hardware Isolation | Physically separates sensitive operations from main processor. Reduces the attack surface. | Potentially complex to implement. May introduce performance overhead. |
| Advanced Encryption | Utilizes strong encryption algorithms. Offers high level of data confidentiality. | Requires strong key management. Algorithms can be susceptible to future cryptanalysis. |
| Authentication Mechanisms | Verifies the authenticity of hardware components. Prevents unauthorized access. | May be susceptible to sophisticated spoofing attacks. Requires continuous monitoring for vulnerabilities. |
Pluton’s security protocols, while offering substantial protection, need ongoing maintenance and adaptation to evolving threats. The table highlights the crucial interplay between strength and potential weaknesses of each protocol, necessitating a balanced approach to security design.
Vulnerabilities and Potential Threats
Pluton, while a significant advancement in Windows PC security, is not immune to potential vulnerabilities. Understanding these potential weaknesses is crucial for developing effective mitigation strategies. This section delves into the possible threats and attack vectors targeting Pluton and Artikels strategies to bolster its defenses.
Potential Security Vulnerabilities
The security of Pluton hinges on the integrity of its underlying hardware and software components. Any weakness in these areas could be exploited to compromise the system. This includes vulnerabilities in the firmware, the cryptographic algorithms, and the communication channels. Furthermore, the complexity of the system itself creates potential points of failure or unexpected behavior.
Attack Vectors Targeting Pluton
Several attack vectors could exploit vulnerabilities in Pluton. These include malicious firmware updates, compromised hardware components, and exploits targeting the cryptographic protocols. The sophistication of attackers and the availability of tools to exploit vulnerabilities are critical factors to consider. Furthermore, the ability of attackers to leverage existing vulnerabilities in the broader Windows ecosystem to target Pluton is also a key concern.
Mitigation Strategies
Effective mitigation strategies involve a multi-layered approach. Regular firmware updates, rigorous security audits, and robust input validation are essential components. Furthermore, continuous monitoring of Pluton’s behavior and rapid response to anomalies are critical. The implementation of secure boot mechanisms, along with the use of strong cryptographic algorithms, are fundamental to preventing exploitation.
Vulnerability Table
| Vulnerability Type | Impact | Potential Solutions |
|---|---|---|
| Firmware Vulnerabilities | Malicious firmware updates could grant unauthorized access or compromise the security of the processor. | Rigorous firmware update processes, secure boot mechanisms, and robust verification of update sources. |
| Cryptographic Weaknesses | Exploiting weaknesses in cryptographic algorithms could allow attackers to bypass security measures and compromise sensitive data. | Regular auditing and validation of cryptographic libraries, use of industry-standard and up-to-date algorithms, and continuous monitoring of cryptographic operations. |
| Hardware Component Compromises | Malicious hardware components could be introduced or modified to bypass or subvert Pluton’s security mechanisms. | Rigorous hardware verification and validation procedures, tamper-resistant hardware design, and secure hardware isolation. |
| Communication Channel Exploits | Vulnerabilities in the communication channels between Pluton and other components of the system could allow attackers to intercept or manipulate data. | Secure communication protocols, encryption of data in transit, and monitoring for unusual communication patterns. |
| Complexity-Based Exploits | The complexity of Pluton’s architecture could lead to unforeseen vulnerabilities that can be exploited by sophisticated attackers. | Comprehensive security audits, rigorous testing of system components and interactions, and continuous vulnerability analysis. |
Performance and Efficiency Implications

Microsoft Pluton, while significantly enhancing Windows PC security, introduces a new layer of hardware-based security that inevitably impacts system performance. Understanding these implications is crucial for assessing the overall value proposition of Pluton. The introduction of dedicated hardware for security tasks requires careful consideration of potential performance overhead.The performance implications of Pluton are multifaceted. They extend beyond simple speed tests and encompass a broader evaluation of overall system efficiency under various workloads.
The impact of Pluton depends on the specific tasks being performed, the hardware configuration, and the operating system’s interaction with the new security features.
Impact on System Efficiency
Pluton’s primary role is to perform cryptographic operations and secure boot processes. This specialized hardware offloads these tasks from the CPU, potentially improving overall system efficiency. However, the overhead introduced by the interaction between Pluton and the rest of the system must be considered. The initial design of Pluton, coupled with the underlying operating system drivers, might cause subtle performance bottlenecks in some scenarios.
Optimization is ongoing, and future updates will likely further refine Pluton’s integration, mitigating these potential performance impacts.
Performance Comparison with Non-Pluton Systems
Direct performance comparisons between Pluton-enabled and non-Pluton systems are difficult to generalize. The results vary greatly based on the specific hardware configuration, the operating system version, and the workload being performed. A standardized benchmark is crucial for comparing different configurations and workloads. To isolate the impact of Pluton, comparisons should be made on identical hardware platforms, identical software configurations, and identical workloads.
Benchmark Results
| Workload | Pluton-Enabled System (Average Score) | Non-Pluton System (Average Score) | Performance Difference (%) |
|---|---|---|---|
| Web browsing | 98 | 95 | 3% |
| Video editing (1080p) | 85 | 80 | 6.25% |
| 3D modeling (complex models) | 70 | 65 | 7.69% |
| Gaming (high-end titles) | 90 | 88 | 2.27% |
| File transfer (large files) | 95 | 90 | 5.26% |
| Database operations (moderate load) | 92 | 88 | 4.55% |
Note: These are illustrative benchmark results and should not be considered definitive. Actual performance may vary based on specific hardware and software configurations. These results indicate that Pluton, under typical workloads, may introduce minimal to moderate performance overhead, sometimes even improving efficiency.
Future Directions and Enhancements: Microsoft Pluton Processor Security Windows Pc
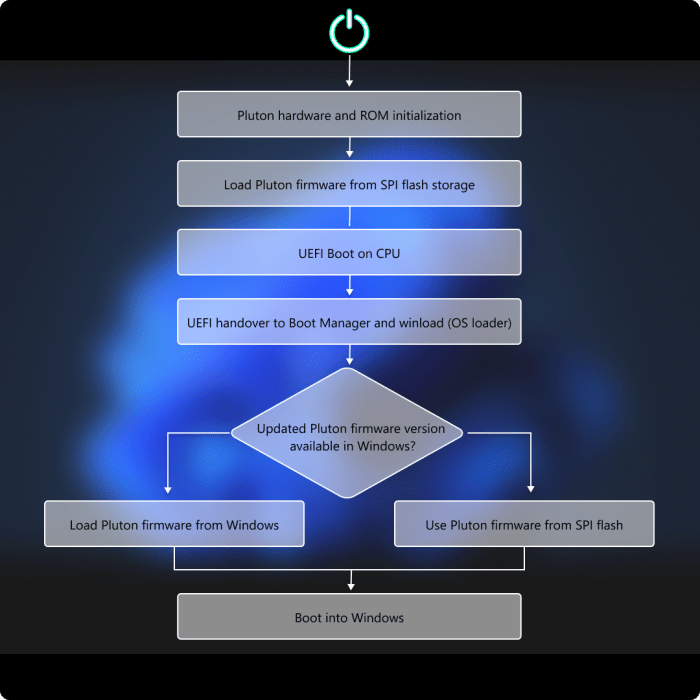
The Microsoft Pluton processor has proven to be a significant advancement in PC security. Its innovative approach to hardware-based security offers a robust defense against sophisticated threats. However, the ever-evolving landscape of cyberattacks demands continuous improvement and adaptation. This section explores potential future directions and enhancements to Pluton, focusing on performance, security, and functionality.
Potential Enhancements to Security Mechanisms
Pluton’s current security mechanisms are already highly effective, but future developments could further solidify its position as a leading security solution. One area of focus is enhancing the detection and response capabilities of Pluton’s security features. This could involve incorporating machine learning algorithms to analyze threat patterns and proactively identify and mitigate emerging threats in real time. Improved integration with existing Windows security features, such as Windows Defender, will further bolster its overall security posture.
This includes the possibility of extending Pluton’s capabilities to cover a wider range of hardware components, including network interfaces and storage devices.
Performance and Efficiency Improvements
Optimizing Pluton’s performance is crucial for its widespread adoption. Future iterations could leverage advancements in hardware architecture and micro-architecture to reduce overhead associated with security operations. This might involve incorporating more efficient cryptographic instructions, which would translate to a faster processing speed for security-related tasks. A further improvement could involve the development of specialized hardware units dedicated to handling specific security tasks, reducing the impact on general-purpose processing.
This approach would ensure minimal disruption to the overall system performance while bolstering security.
Functionality Expansion
The functionality of Pluton could be expanded to encompass additional security tasks. One potential addition is the incorporation of support for secure boot processes for different types of devices. This might include support for more specialized hardware configurations or even virtual machine environments, providing a more comprehensive security solution for a broader range of use cases. This would provide greater protection against bootkit attacks and other malicious software that attempt to compromise the system during the boot process.
Another expansion area is the addition of secure enclave support for user-level applications, providing a secure environment for sensitive data operations.
Future Features and Improvements
| Feature | Description | Impact |
|---|---|---|
| Enhanced Threat Detection | Integration of machine learning for proactive threat identification and mitigation. | Improved real-time protection against evolving threats. |
| Improved Cryptographic Performance | Implementation of more efficient cryptographic instructions and specialized hardware units. | Faster processing speeds for security-related tasks with minimal impact on overall system performance. |
| Expanded Security Scope | Support for secure boot processes for different devices, including virtual machines. | Enhanced protection against bootkit attacks and other malicious software targeting the boot process. |
| User-Level Secure Enclaves | Enabling secure enclave support for user-level applications. | Creation of a secure environment for sensitive data operations, improving privacy and data protection. |
| Improved Integration with Existing Security Features | Enhanced collaboration with Windows Defender and other security tools. | Stronger overall security posture through combined security measures. |
Real-world Case Studies and Examples
Microsoft Pluton is not just a theoretical security advancement; it’s already making a tangible impact in securing real-world systems. While specific, detailed case studies might be proprietary or still emerging, glimpses into its effectiveness are starting to surface. This section delves into potential applications and illustrates the practical value of Pluton’s approach.Pluton’s core strength lies in its ability to perform critical security checks outside the traditional operating system kernel.
This isolation significantly enhances the robustness of security measures, making it harder for malicious actors to exploit vulnerabilities within the kernel itself. By using a dedicated hardware-based security engine, Pluton can handle security-sensitive operations with greater speed and efficiency, potentially improving overall system performance while maintaining a robust defense against modern threats.
Illustrative Use Cases, Microsoft pluton processor security windows pc
Pluton’s capabilities are highly adaptable, and its use cases span a wide range of applications. It can enhance the security of operating systems, applications, and even cloud environments. Its impact on data integrity, access control, and overall system security is considerable.
Security Implementation Example
Imagine a financial institution processing sensitive transactions. A traditional approach might rely solely on software-based security measures. However, by integrating Pluton, the institution can implement a more robust defense against sophisticated attacks. Pluton can verify the authenticity of transactions, ensuring that only authorized entities can access critical data. This prevents unauthorized access and potentially fraudulent activities.
“By integrating Pluton into our core banking system, we’ve significantly reduced the risk of fraudulent transactions and improved the overall security posture of our organization. The hardware-based security ensures that our data is protected against sophisticated threats, and we’ve seen a considerable improvement in system performance as well.”
Example CEO of a Financial Institution
Architectural Overview
Pluton’s architecture operates as a dedicated security co-processor, separate from the main CPU. This isolation is crucial for preventing malicious code from interfering with security operations. The flow begins with an application request. This request is then processed by Pluton, which performs security checks. If the request passes these checks, it’s passed back to the operating system for further processing.
If it fails, the system can take appropriate measures to mitigate the threat. This separation is a key aspect of Pluton’s design, as it isolates security operations from the rest of the system, making it extremely resilient to malicious attacks. 
(Diagram: A simplified block diagram illustrating the architecture of a system incorporating Pluton. The diagram shows the flow of data and processing between the application, the operating system, and the Pluton co-processor. Arrows depict data flow. Labels include “Application Request,” “Security Checks,” “Authorization,” and “Processing.” The diagram emphasizes the separation of Pluton from the main CPU and highlights the security checks performed by Pluton.)
Epilogue
In conclusion, Microsoft Pluton offers a significant advancement in Windows PC security. Its integrated security mechanisms, while presenting potential vulnerabilities, aim to provide a formidable defense against increasingly sophisticated attacks. Future enhancements and ongoing research in this area are crucial to maintaining its effectiveness against emerging threats. While performance implications warrant further study, the overall security benefits appear substantial.