IoT security vs OT security is a critical discussion in today’s interconnected world. IoT, encompassing smart devices and connected systems, faces unique vulnerabilities, while OT, crucial for industrial processes, demands a different approach. Understanding the fundamental differences between these two domains is essential for developing robust security strategies. This exploration delves into the specific challenges, comparing and contrasting security approaches, and examining the future of these interconnected systems.
IoT systems, characterized by their diverse and often insecure architectures, are vulnerable to a wide array of threats. In contrast, OT systems, while critical to industrial operations, are often isolated from the broader internet, making them vulnerable to different types of threats. This article will unpack the nuances of these differences, providing a clear picture of the challenges and potential solutions for each.
Introduction to IoT and OT Security
The Internet of Things (IoT) is rapidly transforming our lives, connecting everyday objects like smart refrigerators and wearables to the internet. This interconnectedness allows for unprecedented data collection and automation, but it also introduces significant security vulnerabilities. Operational Technology (OT), on the other hand, forms the backbone of industrial processes, controlling everything from power grids to manufacturing lines.
Understanding the unique characteristics of both IoT and OT systems is crucial for developing effective security strategies.Operational technology (OT) systems are fundamentally different from IoT systems, demanding distinct security approaches. OT systems prioritize reliability and real-time performance over flexibility and connectivity, which often results in unique security considerations. Both environments face the threat of malicious actors seeking to disrupt operations or gain unauthorized access to sensitive data.
IoT System Overview
IoT systems encompass a wide range of interconnected devices, from smart home appliances to industrial sensors. Their primary function is data collection and communication. These devices typically have limited processing power and storage capacity, leading to a focus on lightweight protocols and streamlined communication. The diverse nature of IoT devices, coupled with their widespread deployment, poses unique challenges for security.
Thinking about IoT security versus Operational Technology (OT) security? It’s a crucial distinction, especially when considering the different levels of risk. While exploring tech deals, I stumbled upon a fantastic Vivitek projector sale – find projector fit your budget viviteks one day sale just 130. This sale is a great reminder that even in everyday tech purchases, we can find value while also keeping an eye on the security of our devices and systems, and that applies to OT and IoT security alike.
Data from IoT devices often includes information about environmental conditions, user behavior, and even location, creating opportunities for both legitimate and malicious data analysis.
OT System Overview
OT systems are crucial for the smooth operation of critical infrastructure and industrial processes. They control physical assets like machinery, pipelines, and power grids. OT systems are characterized by their real-time nature and the critical role they play in maintaining operations. OT systems often rely on specialized protocols and communication networks, requiring dedicated security measures to safeguard against disruptions.
Examples include supervisory control and data acquisition (SCADA) systems and programmable logic controllers (PLCs). Security considerations often include the potential for physical damage, cyberattacks, and human error.
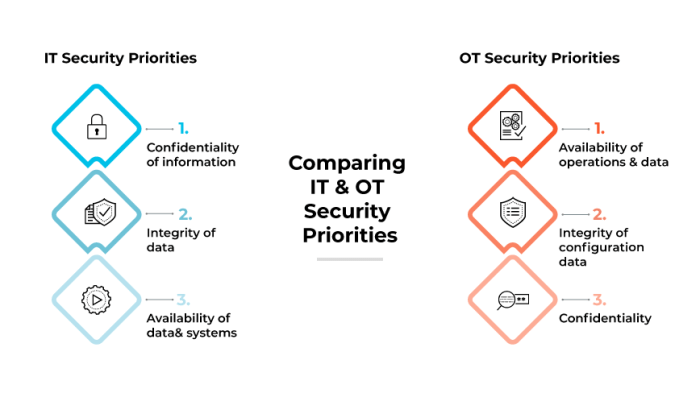
Key Differences Between IoT and OT Systems
The following table highlights the key distinctions between IoT and OT systems in terms of architecture, data types, and security requirements:
| Feature | IoT | OT | Key Differences |
|---|---|---|---|
| Architecture | Typically decentralized, with diverse devices and protocols. | Often hierarchical, with specific communication protocols for industrial control systems. | OT systems are more centralized and structured for efficient control, while IoT systems are more diverse and distributed. |
| Data Types | Varied data types, including sensor readings, user interactions, and environmental information. | Primarily focused on process data, such as temperature, pressure, and flow rates. | IoT data is broader and less directly related to physical processes, while OT data is highly specific and crucial for process control. |
| Security Requirements | Focus on confidentiality, integrity, and availability, with a balance between security and usability. | High emphasis on availability and real-time operation, requiring fault tolerance and minimal disruption. | OT security prioritizes resilience and minimal downtime, whereas IoT security often considers a wider range of threats. |
Understanding these fundamental differences is critical for implementing effective security strategies for both IoT and OT environments.
IoT security versus OT security is a crucial consideration, especially as smart devices become more integrated into our lives. Think about the potential security risks in a connected world, like the upcoming Apple Watch X redesign with microLED and magnetic band Series 9. Apple Watch X redesign microled magnetic band series 9 might seem a world away from industrial control systems, but the core principles of securing interconnected systems remain the same.
Ultimately, safeguarding both our personal devices and critical infrastructure demands robust security measures across the board.
Security Challenges in IoT
The Internet of Things (IoT) has revolutionized numerous industries, connecting everyday objects to the digital world. However, this interconnectedness comes with significant security vulnerabilities. These vulnerabilities, if exploited, can have far-reaching consequences, impacting not only individual devices but also entire critical infrastructure systems. Understanding these challenges is crucial for building robust IoT security strategies.IoT devices often lack robust security features, making them susceptible to various attacks.
This vulnerability is exacerbated by the often-limited resources and capabilities of these devices, which restrict the implementation of advanced security measures. Consequently, security breaches can lead to severe disruptions and potentially catastrophic outcomes in diverse sectors.
Unique Vulnerabilities of IoT Devices
IoT devices frequently employ weak passwords, outdated software, and insufficient security protocols. This combination of factors creates a perfect storm for attackers, enabling them to easily gain unauthorized access. The inherent limitations of many IoT devices, such as their limited processing power and memory, often prevent the implementation of sophisticated security measures, leaving them exposed to attack. Furthermore, the large number of interconnected devices within an IoT network can amplify the impact of a single security breach.
This distributed nature of the IoT makes centralized security management a significant challenge.
Potential Impact of IoT Security Breaches
The consequences of IoT security breaches can be devastating across numerous sectors. Critical infrastructure, like power grids and water treatment facilities, can be disrupted, leading to widespread outages and societal instability. In the healthcare sector, compromised medical devices could potentially endanger patient lives. Financial institutions could be targeted for financial losses, and personal data breaches could result in identity theft and fraud.
Moreover, the interconnected nature of IoT systems means that a breach in one area can have ripple effects throughout the entire network.
Common Attack Vectors Targeting IoT Systems
Attackers employ various methods to exploit vulnerabilities in IoT systems. These tactics often target weaknesses in the device firmware, network protocols, or the overall system architecture. Understanding these attack vectors is crucial for developing effective mitigation strategies.
- Weak Authentication and Authorization: Many IoT devices rely on weak passwords or default credentials, making them easily accessible to attackers. This lack of strong authentication mechanisms can lead to unauthorized access and control over the device.
- Outdated Firmware and Software: The continuous evolution of software and firmware demands regular updates. Failing to update devices with the latest security patches leaves them vulnerable to known vulnerabilities.
- Vulnerable Network Protocols: The use of insecure network protocols can expose IoT devices to attacks, such as man-in-the-middle attacks. These attacks can allow attackers to intercept and manipulate communication between devices.
- Malware Infections: Malicious software can be installed on IoT devices, granting attackers control and potentially enabling them to steal data or disrupt operations. This is a major threat vector.
- Denial-of-Service (DoS) Attacks: Attackers can flood IoT devices or networks with traffic, rendering them unavailable to legitimate users. This can cause significant disruptions to services.
Attack Vectors Targeting IoT Systems: Detailed Analysis
| Attack Vector | Description | Potential Impact | Mitigation Strategies |
|---|---|---|---|
| Weak Authentication and Authorization | Devices use easily guessable passwords or default credentials. | Unauthorized access, data breaches, system compromise. | Strong passwords, multi-factor authentication, regular credential changes. |
| Outdated Firmware and Software | Lack of timely updates exposes devices to known vulnerabilities. | Exploitable vulnerabilities, system compromise. | Automated update mechanisms, security patches, vulnerability scanning. |
| Vulnerable Network Protocols | Insecure communication channels allow attackers to intercept or manipulate data. | Data breaches, unauthorized access, system manipulation. | Secure protocols (e.g., HTTPS), encryption, network segmentation. |
| Malware Infections | Malicious software infects devices, granting attackers control. | Data theft, system disruption, data manipulation. | Anti-malware software, intrusion detection systems, regular security audits. |
| Denial-of-Service (DoS) Attacks | Flooding devices or networks with traffic, rendering them unavailable. | Service disruption, system downtime, financial losses. | Traffic filtering, intrusion prevention systems, load balancing. |
Security Challenges in OT: Iot Security Vs Ot Security
Operational Technology (OT) environments, unlike Information Technology (IT) systems, are designed for real-time control and automation of industrial processes. This criticality demands a different approach to security, as a compromise can have severe consequences ranging from production downtime to safety hazards. The focus shifts from simple data breaches to potential physical damage and disruption.OT systems are often interconnected with various devices and equipment, creating a complex network that is vulnerable to attacks if not properly secured.
The unique characteristics of these environments, including their reliance on legacy systems, limited visibility, and stringent real-time requirements, present specific security challenges that are not typically encountered in IT environments.
Criticality of Industrial Processes
Industrial processes are often continuous and require constant monitoring and control. A security breach in an OT system can lead to significant disruptions, impacting production, safety, and profitability. For instance, a compromised power grid automation system could cause widespread blackouts, while a malfunctioning chemical plant control system could lead to hazardous releases.
Examples of OT System Compromises
Malicious actors can exploit vulnerabilities in OT systems in various ways. A common method involves using compromised human-machine interfaces (HMIs) to gain unauthorized access to control systems. Another method involves targeting industrial communication protocols, such as Modbus, for data breaches. These attacks can manipulate control logic, leading to incorrect operation of machinery and equipment.One example of a compromise includes a scenario where a cybercriminal gains access to a water treatment plant’s SCADA system.
By manipulating the control parameters, the criminal could alter the water quality or even shut down the entire system, resulting in public health crises and significant economic losses.
Challenges of Maintaining Real-Time Operations
Implementing robust security measures in OT environments while maintaining real-time operations presents a significant challenge. Security solutions must be integrated without compromising the performance or reliability of the industrial processes. Security audits and patching should be performed without interrupting critical operations. This is often difficult due to the complex and dynamic nature of OT environments.
Specific Security Threats in OT
Various security threats are particularly relevant to OT environments. These threats include malware designed specifically for industrial control systems (ICS), phishing attacks targeting OT personnel, and denial-of-service (DoS) attacks designed to disrupt operations. Additionally, insider threats pose a considerable risk as authorized personnel might inadvertently or intentionally compromise security protocols.
Examples of Targeted Industrial Control Systems
Industrial control systems (ICS) are susceptible to a variety of attacks, which can have devastating consequences. For instance, a compromised supervisory control and data acquisition (SCADA) system in a power plant could lead to widespread blackouts. Another example involves a targeted attack on a pipeline system, resulting in material leakage or explosions. The following table summarizes some potential targets and potential consequences:
| Target | Potential Consequences |
|---|---|
| Power grids | Widespread blackouts, economic disruption |
| Water treatment plants | Water contamination, public health crisis |
| Chemical plants | Hazardous releases, environmental damage |
| Oil and gas pipelines | Material leakage, explosions |
Comparing IoT and OT Security Approaches
Protecting the interconnected systems of the modern world, from smart homes to critical infrastructure, requires robust security measures. Both Internet of Things (IoT) and Operational Technology (OT) environments face unique challenges, demanding tailored security strategies. Understanding the similarities and differences in their approaches is crucial for developing effective defenses against evolving threats.The diverse nature of IoT and OT networks necessitates distinct security considerations.
IoT devices often prioritize ease of use and rapid deployment, while OT systems are designed for reliability and stability, prioritizing safety and functionality. These differences in design and operational requirements influence the security protocols and measures employed.
Common Security Protocols in IoT and OT
Various protocols are used for communication and data exchange in both IoT and OT environments. These protocols, while potentially similar in their basic structure, differ significantly in their implementation and security features. For example, MQTT (Message Queuing Telemetry Transport) is frequently used in IoT for lightweight communication, while Modbus is a standard in OT for industrial control systems.
Security Measures in IoT and OT Networks
Different security measures are employed in protecting IoT and OT networks. IoT systems often rely on authentication protocols like TLS/SSL to ensure secure communication between devices and the cloud. OT systems, on the other hand, prioritize secure communication channels for their critical control systems and may use specialized protocols like IEC 61850 for power grids.
Effectiveness of Security Measures
The effectiveness of security measures varies depending on the specific threat and the implementation. IoT systems, with their numerous devices and potentially weak security configurations, are often vulnerable to widespread attacks. OT systems, with their critical nature, are generally more resistant to common attacks but may be susceptible to targeted, sophisticated attacks that exploit vulnerabilities in their specific control protocols.
Data Security and Privacy in IoT and OT
Data security and privacy are crucial for both IoT and OT. IoT systems collect vast amounts of user data, raising concerns about privacy violations. OT systems handle sensitive operational data, impacting critical infrastructure and public safety. Data encryption, access controls, and data loss prevention are essential to safeguard sensitive information in both environments.
Comparison of Security Approaches
| Feature | IoT Security | OT Security | Comparison |
|---|---|---|---|
| Common Vulnerabilities | Weak passwords, insecure APIs, lack of device hardening, insufficient access controls | Outdated protocols, lack of patching, poor physical security, limited visibility | IoT systems often face broader, more widespread vulnerabilities, while OT vulnerabilities can be more localized and result in catastrophic consequences. |
| Common Countermeasures | Strong passwords, secure APIs, device hardening, access control lists | Regular patching, updated protocols, physical security measures, intrusion detection systems | Both benefit from strong authentication, secure communication, and access controls, but the implementation varies greatly due to the different environments. |
| Unique Vulnerabilities (IoT) | Device proliferation, lack of standardization, difficulty in patching, potential for botnets, and denial-of-service attacks. | Targeted attacks, specific vulnerabilities in control protocols, cascading failures, potential for physical manipulation. | IoT’s large scale and heterogeneous nature create unique challenges. |
| Unique Vulnerabilities (OT) | Lack of dedicated security expertise in many organizations, difficulty in patching due to legacy systems. | Lack of standardization, difficulty in isolating vulnerabilities, potential for catastrophic consequences of failures. | OT systems are designed for reliability and stability, potentially making them vulnerable to specialized attacks. |
| Unique Countermeasures (IoT) | Device-level security, cloud-based security solutions, automated vulnerability scanning. | Specialized security protocols, redundant systems, safety instrumented systems. | IoT systems require a focus on device security and cloud-based solutions, while OT systems demand focus on specialized protocols and redundant systems. |
| Unique Countermeasures (OT) | Security awareness training, incident response plans, penetration testing. | Cybersecurity training for OT personnel, specialized security monitoring tools. | OT systems require specific security expertise and specialized countermeasures. |
Security Frameworks and Standards for IoT and OT
Security frameworks and standards play a crucial role in ensuring the safety and reliability of interconnected devices and systems, particularly in the context of IoT and OT. These frameworks provide a structured approach to managing security risks, promoting best practices, and enabling organizations to demonstrate compliance with regulatory requirements. Without these guidelines, securing complex systems like industrial control systems or smart homes becomes a daunting task, leading to potential vulnerabilities and breaches.
Significance of Security Frameworks
Security frameworks, like the NIST Cybersecurity Framework, offer a comprehensive structure for managing cybersecurity risks. These frameworks provide a common language and a structured approach to identifying, assessing, and mitigating risks across diverse systems. By establishing a common understanding of security controls, organizations can better coordinate efforts and implement consistent security practices across their infrastructure. Furthermore, these frameworks provide a standardized methodology for evaluating the effectiveness of security controls, enabling organizations to demonstrate compliance and build trust with stakeholders.
NIST Cybersecurity Framework, for example, helps organizations establish a baseline for cybersecurity and improve their overall security posture.
Role of Industry-Specific Standards
Industry-specific standards are vital in enhancing security in IoT and OT environments. These standards address the unique security challenges associated with particular industries or technologies, offering specific guidelines and best practices. For example, the standards provide tailored approaches for managing sensitive data, securing communication channels, and implementing access controls. These industry-specific standards, while building upon broader frameworks, often offer more granular guidance to meet the specific requirements of particular sectors.
Implementation Considerations
Implementing security frameworks and standards requires careful planning and execution. Organizations need to assess their current security posture, identify gaps, and develop a phased implementation plan. Training employees on the use of new security tools and procedures is also crucial. Regular security assessments and audits are essential for identifying and addressing vulnerabilities as they emerge. The implementation process should involve collaboration between IT and OT teams to ensure a holistic approach that addresses the specific needs of both domains.
Role of Regulations and Compliance
Regulations and compliance requirements play a critical role in driving security best practices in IoT and OT environments. These requirements often mandate the implementation of specific security controls and procedures, which in turn incentivize organizations to adopt best practices. Compliance with these regulations not only protects against potential legal repercussions but also enhances public trust and confidence in the systems.
Thinking about IoT security versus OT security? It’s a fascinating field, but sometimes a bit abstract. Imagine the complexities of securing systems in a game like Death Stranding. The recent Death Stranding Hideo Kojima PS4 release date trailer death stranding hideo kojima ps4 release date trailer highlights the intricate connections between various systems, and that mirrors the interconnected nature of modern industrial control systems.
Ultimately, understanding these intricacies is crucial for bolstering the security of both IoT and OT systems in today’s digital world.
For instance, regulatory frameworks related to data privacy and industrial control systems security drive organizations to implement robust security measures.
Examples of Relevant Security Standards
Standards like ISA99 are critical for securing OT environments. ISA99, for example, provides guidelines for securing industrial automation and control systems. These standards define specific requirements for securing communication protocols, implementing access controls, and managing vulnerabilities. By following standards like ISA99, organizations can improve the security posture of their OT systems, mitigating potential risks and ensuring the reliability of critical infrastructure.
| Standard | Focus Area | Application in OT |
|---|---|---|
| ISA99 | Industrial automation and control systems security | Securing SCADA systems, programmable logic controllers (PLCs), and other critical infrastructure devices. |
Security Measures and Best Practices
Securing IoT and OT environments requires a multi-layered approach encompassing various security measures. These measures must be tailored to the specific needs of each environment, considering factors like the criticality of the data being handled, the potential impact of a security breach, and the inherent vulnerabilities of the devices and systems involved. A robust security posture necessitates proactive measures, regular assessments, and ongoing monitoring.
Access Control and Authentication Mechanisms
Robust access control and authentication are paramount in securing IoT and OT systems. Effective access control mechanisms restrict access to sensitive data and resources based on user roles and privileges. Authentication ensures that only authorized users can access the system, preventing unauthorized access and manipulation. Multi-factor authentication (MFA) adds an extra layer of security by requiring multiple verification methods, such as passwords, security tokens, or biometric data.
Implementing strong password policies and regularly updating credentials are crucial elements of a comprehensive access control strategy.
Data Encryption and Secure Communication Protocols
Data encryption plays a vital role in protecting sensitive information transmitted over networks. Encrypting data at rest and in transit safeguards against unauthorized access and manipulation. Secure communication protocols, such as TLS/SSL, are essential for encrypting communication channels between devices and systems, preventing eavesdropping and data breaches. The use of strong encryption algorithms and key management practices is critical for ensuring data confidentiality and integrity.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion detection and prevention systems (IDS/IPS) are crucial for monitoring network traffic and detecting malicious activity. IDS systems identify suspicious patterns and alert administrators to potential threats. IPS systems actively block or mitigate malicious attacks, preventing them from reaching vulnerable systems. Regularly updating IDS/IPS signatures and configurations is essential for maintaining their effectiveness against evolving threats. Properly configured and maintained IDS/IPS systems are an important component of a comprehensive security strategy.
Best Practices for Securing IoT and OT Devices and Networks
Implementing robust security measures necessitates adherence to best practices across all aspects of the IoT and OT environments. Following a structured approach, including regular security audits and penetration testing, helps identify vulnerabilities and implement necessary safeguards.
- Regular Software Updates and Patching: Keeping all software, firmware, and operating systems updated with the latest security patches mitigates known vulnerabilities and reduces the risk of exploitation. Outdated systems are prime targets for attackers, highlighting the importance of proactive updates.
- Network Segmentation and Isolation: Segmenting the network into smaller, isolated sections limits the impact of a breach to a specific segment. This minimizes the risk of lateral movement and the potential spread of malware.
- Strong Passwords and Access Controls: Implementing strong password policies and multi-factor authentication (MFA) for all users, devices, and systems ensures only authorized personnel can access sensitive information. Enforcing regular password changes and enforcing strong password complexity standards is critical.
- Device Hardening and Security Configuration: Hardening devices by disabling unnecessary services and features reduces the attack surface. Configuring security settings appropriately minimizes vulnerabilities, and this should be done consistently across all devices and systems.
- Regular Security Audits and Penetration Testing: Conducting regular security audits and penetration testing helps identify vulnerabilities and weaknesses before they can be exploited. This proactive approach ensures that security measures remain effective against evolving threats.
- Incident Response Planning: Having a well-defined incident response plan ensures that the organization can effectively respond to and recover from security incidents. A comprehensive plan Artikels procedures for containing, investigating, and mitigating the effects of a security breach.
Case Studies and Examples of Successful and Unsuccessful Security Measures
Real-world examples of successful and failed security implementations in IoT and OT environments offer valuable lessons. Analyzing these cases helps us understand the complexities and vulnerabilities of these interconnected systems, and pinpoint crucial areas for improvement. Understanding both successful and unsuccessful deployments provides a clearer picture of the effectiveness of security measures.
Successful Implementations in IoT
Implementing robust security measures in IoT devices and networks can significantly reduce vulnerabilities. One successful approach involves the use of secure communication protocols like HTTPS for data transmission between devices and cloud platforms. Implementing multi-factor authentication for user access enhances security further. Employing regular security audits and vulnerability assessments helps identify and patch potential weaknesses. The use of device-level encryption safeguards sensitive data during transit and storage.
A strong example is the successful implementation of secure protocols in smart home devices, preventing unauthorized access to personal data. Companies like Nest have implemented advanced encryption techniques in their smart thermostat devices, minimizing risks associated with data breaches.
Successful Implementations in OT
Implementing security measures in operational technology (OT) environments often involves securing industrial control systems (ICS). Implementing network segmentation isolates critical control systems from less secure networks. Implementing intrusion detection systems (IDS) helps monitor network traffic for suspicious activity. Regular security awareness training for OT personnel is critical to prevent social engineering attacks. A strong example is the use of secure protocols like Secure Shell (SSH) for remote access to industrial control systems.
By implementing these measures, organizations can significantly reduce vulnerabilities in their OT infrastructure.
Security Breaches in IoT
Several high-profile IoT security breaches highlight the vulnerability of these interconnected devices. The Mirai botnet attack, for instance, leveraged vulnerabilities in internet-connected devices to launch massive distributed denial-of-service (DDoS) attacks. Other breaches involved unauthorized access to sensitive data stored on IoT devices or compromised systems. A critical lesson learned is the importance of device-level security and regular updates.
This example emphasizes the critical need for robust security protocols in the design and implementation of IoT systems.
Security Breaches in OT
Security breaches in OT environments can have devastating consequences, affecting production processes, safety, and even human lives. The Stuxnet worm, a highly sophisticated malware, targeted industrial control systems, demonstrating the potential for devastating disruptions. Another example involves a power grid attack, showcasing the vulnerability of critical infrastructure to cyber threats. Lessons learned include the importance of robust network segmentation and intrusion detection systems to mitigate the impact of attacks.
Lessons Learned from Security Incidents
The analysis of successful and unsuccessful security measures reveals key lessons. Prioritizing security throughout the entire lifecycle of an IoT or OT system, from design to deployment, is paramount. The use of security best practices, such as regular patching, secure coding, and secure configuration, can prevent many vulnerabilities. The importance of incident response planning and preparedness is evident in both domains.
Companies must have incident response teams and protocols in place to address security breaches swiftly and effectively.
Importance of Incident Response Planning
Effective incident response planning is crucial for mitigating the impact of security breaches. Planning should include identifying potential threats, developing response procedures, and training personnel. This includes having a well-defined communication strategy to keep stakeholders informed during an incident. Creating a detailed incident response plan helps ensure that organizations can react swiftly and effectively to any security breaches.
Summary of Case Studies
Case studies highlight the significant real-world impact of security breaches in both IoT and OT environments. The consequences can range from financial losses to operational disruptions and even loss of life. Implementing robust security measures is crucial for safeguarding these systems from attacks. Protecting these systems is essential for maintaining operational efficiency, preventing disruptions, and safeguarding critical infrastructure.
Future Trends in IoT and OT Security
The landscape of IoT and OT security is constantly evolving, driven by the rapid advancement of technology and the increasing sophistication of cyber threats. Predicting the future is inherently challenging, but by analyzing current trends and emerging technologies, we can gain insights into the security challenges and opportunities that lie ahead. This analysis will delve into the evolving threat landscape, explore the impact of emerging technologies, and highlight potential security solutions.
Future Security Challenges in IoT
The interconnected nature of IoT devices creates significant vulnerabilities. As more devices are added to networks, the attack surface expands, increasing the potential for widespread disruption. Furthermore, the often-limited security features of many IoT devices make them easy targets for exploitation. The lack of consistent security standards and the difficulty in updating software on these devices exacerbate the problem.
The potential for supply chain attacks, where malicious code is introduced during the manufacturing or distribution process, also poses a serious concern.
Future Security Challenges in OT
OT environments, while often critical infrastructure, face unique challenges. The integration of IoT devices into OT networks introduces new attack vectors. The need for continuous operation, the often-rigid infrastructure, and the limited resources dedicated to security create vulnerabilities. Advanced persistent threats (APTs) targeting OT systems are also emerging, with the potential for significant damage to critical infrastructure.
The rising complexity of industrial control systems (ICS) adds to the challenge, as these systems often rely on legacy hardware and software, making them more difficult to secure.
Impact of Emerging Technologies on IoT and OT Security
Emerging technologies, while offering numerous benefits, introduce new security challenges. Cloud computing, for example, while offering scalability and cost savings, can introduce vulnerabilities if not properly secured. Artificial intelligence (AI) can be used for both offensive and defensive purposes, with malicious actors leveraging AI to develop more sophisticated attacks and security professionals utilizing AI to detect and respond to threats.
The growing use of machine learning (ML) in security solutions can enhance threat detection and response capabilities, but requires careful consideration of bias and accuracy.
Evolving Threat Landscape, Iot security vs ot security
The threat landscape is becoming more diverse and sophisticated. The rise of ransomware attacks targeting industrial control systems (ICS) is a major concern. Advanced persistent threats (APTs) targeting critical infrastructure are increasingly prevalent. Phishing attacks, social engineering, and supply chain attacks continue to be significant risks. These threats are often interconnected, with attacks on one system potentially cascading to others.
Emerging Security Solutions
Emerging security solutions offer the potential to address future threats. Zero-trust security models, which assume no trust, are becoming more prevalent. AI-powered threat detection and response systems are becoming more sophisticated. Improved security protocols, such as blockchain technology, offer the possibility of enhanced data integrity and security. Security information and event management (SIEM) systems are evolving to better integrate with IoT and OT environments.
Table of Emerging Technologies and Their Impact on IoT and OT Security
| Technology | Potential Impact | Security Implications | Mitigation Strategies |
|---|---|---|---|
| Cloud Computing | Increased scalability and accessibility, but potential for increased attack surface | Data breaches, unauthorized access, vulnerabilities in cloud providers | Implement strong access controls, encrypt data in transit and at rest, regular security audits of cloud providers |
| Artificial Intelligence (AI) | Enhanced threat detection and response, but also potential for malicious use | Sophisticated attacks, bias in AI algorithms, lack of transparency in AI-powered systems | Develop robust AI security frameworks, prioritize explainability in AI systems, implement regular audits and testing |
| Machine Learning (ML) | Improved threat detection and prediction, but potential for false positives and bias | Misidentification of threats, biases in data training, lack of interpretability of ML models | Use diverse and representative datasets, implement validation and testing procedures, prioritize transparency and explainability |
| Blockchain | Enhanced data integrity and security, but potential complexity and scalability issues | Complexity in implementation, potential for vulnerabilities in blockchain protocols | Thorough security testing of blockchain solutions, use of trusted platforms, focus on security audits |
Closing Notes
In conclusion, IoT and OT security differ significantly due to their unique architectures, data types, and operational needs. While IoT security focuses on protecting consumer-grade devices, OT security prioritizes the safety and integrity of critical industrial processes. Understanding these differences is crucial for developing tailored security strategies and mitigating the risk of potential breaches in both domains. This comparison highlights the importance of a comprehensive approach to cybersecurity that considers the specific needs and vulnerabilities of each system.