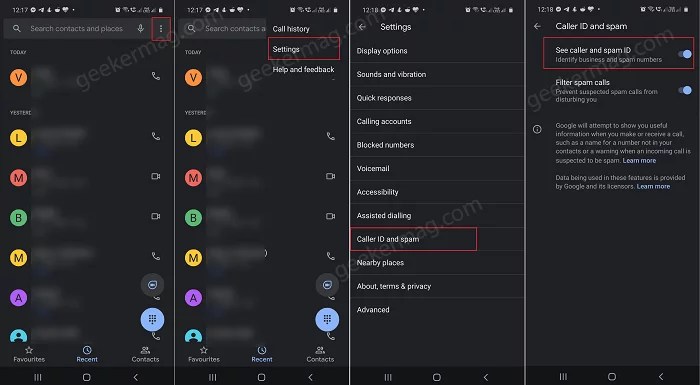
Google phone app verified calls lg samsung context fraud spam reduction – Google Phone app verified calls, LG and Samsung context, fraud and spam reduction – this is a deep dive into the complex world of phone security. We’ll explore various verification methods, from the technical nitty-gritty to the impact on user experience. The article will dissect fraudulent call tactics, analyzing how Google’s phone app tackles spam and fraud attempts.
We’ll also discuss potential vulnerabilities and future trends in call verification, showcasing case studies and real-world examples.
The core of this discussion centers on how verification methods affect the quality and user experience of calls. This includes analyzing security protocols, potential vulnerabilities, and the pros and cons of various approaches. We’ll examine how different phone manufacturers (like LG and Samsung) integrate these verification systems and how the effectiveness of spam reduction measures varies between them.
Ultimately, we aim to provide a comprehensive understanding of the interplay between technology, fraud, and the user experience.
Verified Calls and Authentication Methods
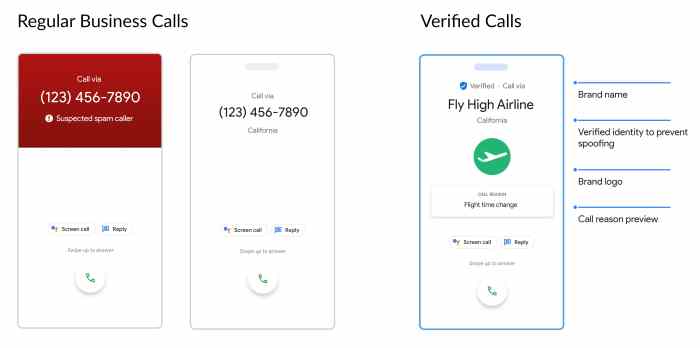
The proliferation of fraudulent calls, often masquerading as legitimate entities, has created a significant need for robust verification methods. Modern communication platforms, including the Google Phone app, are actively addressing this issue by implementing various authentication techniques. This exploration delves into the diverse strategies employed to ensure call authenticity, comparing methods across different phone manufacturers and highlighting the technical aspects involved.Call verification is a critical component in combating fraud.
By verifying the identity of the caller, platforms can mitigate the risk of scams and protect users from financial and personal harm. The methods employed vary significantly, reflecting the evolving nature of fraud and the technical capabilities of different devices.
Verification Methods for Calls
Various methods are employed to verify the caller’s identity, ranging from simple to complex. These methods are crucial in differentiating genuine calls from fraudulent attempts. Different methods have varying degrees of effectiveness, making a multifaceted approach essential.
- Caller ID Verification: This involves cross-referencing the caller’s phone number with a database of legitimate numbers. If the number is registered with a known organization, the call is flagged as potentially legitimate. This basic method is widely used but has limitations in preventing spoofing.
- Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security. A verification code, sent via SMS or another method, must be entered to complete the call. This strengthens security significantly, making it more difficult for fraudsters to impersonate legitimate callers.
- Biometric Verification: This method leverages a user’s unique biometric data (fingerprint, facial recognition) to authenticate calls. This approach enhances security, as it’s tied directly to the user’s device, making it harder to replicate.
- Voice Verification: This method uses speech recognition to match the caller’s voice to a previously recorded sample. This offers high security but requires a user-friendly setup process and accurate recording capabilities.
Comparison Across Manufacturers
The implementation of call verification methods varies between manufacturers like LG and Samsung. While Google Phone app utilizes a unified approach across supported devices, the specific implementation details might differ.
- LG Phones: LG devices may integrate different authentication techniques depending on the specific model and software version. For example, some models may prioritize caller ID verification, while others may incorporate 2FA or voice verification.
- Samsung Phones: Samsung devices often feature a combination of caller ID verification and 2FA. Advanced security features might be contingent on the specific device and its software version.
Technical Aspects of Call Verification
The technical underpinnings of call verification encompass a range of security protocols and algorithms. This includes cryptographic techniques to protect sensitive data during verification processes.
- Security Protocols: TLS (Transport Layer Security) is a common protocol used to encrypt communication channels during call verification. This ensures the confidentiality and integrity of data exchanged during the authentication process.
- Algorithms: Various algorithms are employed for matching caller identities and verifying their legitimacy. These algorithms are crucial in determining the probability of a call being fraudulent. Machine learning algorithms can improve the accuracy of call verification over time, learning from both legitimate and fraudulent calls.
Effectiveness of Verification Methods
The effectiveness of call verification methods depends on the specific technique and its implementation. A table illustrating the comparative effectiveness is provided below.
Google’s phone app is tackling verified calls, focusing on LG and Samsung phones, to combat fraud and spam. This effort to improve security is crucial in today’s digital landscape, especially considering the broader issues in the streaming wars, like the battles between JJ Abrams’ Bad Robot, WarnerMedia, AT&T, Apple, and Netflix, as detailed in this insightful article here.
Ultimately, these efforts to enhance security in the phone app, by verifying calls, directly affect the user experience, reducing the risk of scams and unwanted calls.
| Verification Method | Effectiveness in Preventing Fraud | Description |
|---|---|---|
| Caller ID Verification | Moderate | Checks the caller’s number against a database. |
| 2FA | High | Requires a verification code for authentication. |
| Biometric Verification | Very High | Leverages user’s unique biometric data. |
| Voice Verification | High | Matches caller’s voice to a recorded sample. |
Fraudulent Call Identification and Prevention: Google Phone App Verified Calls Lg Samsung Context Fraud Spam Reduction
Spam calls are a persistent nuisance, costing individuals and businesses significant time and resources. Identifying and preventing these calls is crucial, and various techniques are employed to achieve this. Modern technology, coupled with user vigilance, plays a key role in mitigating this problem.Modern call identification methods go beyond simply blocking numbers. Sophisticated algorithms and machine learning are used to analyze call patterns, identify suspicious s, and flag potentially fraudulent calls.
This allows for more effective prevention and a reduction in unwanted calls.
Techniques for Identifying Fraudulent Calls
Numerous techniques are used to detect fraudulent calls. These methods leverage sophisticated algorithms, analyzing call patterns and identifying suspicious s or phrases within the conversation. Advanced systems examine call logs and caller information for known patterns associated with fraud. Machine learning models are trained on large datasets of legitimate and fraudulent calls to recognize subtle characteristics of fraudulent interactions.
Common Fraudulent Call Tactics
Spammers employ various tactics to trick their targets. Common techniques include:
- Spoofing: This involves masking the caller ID to appear as a legitimate entity, like a bank or government agency. This tactic creates an illusion of legitimacy, potentially leading to unsuspecting victims disclosing personal information.
- Phishing: Spam calls often lead to phishing attempts, directing victims to fake websites or asking for sensitive data like passwords, credit card details, or social security numbers.
- Vishing: This technique uses voice calls to trick victims into revealing personal information. The caller may impersonate a legitimate company to instill trust and prompt the victim to divulge sensitive data.
- Malware Distribution: Some spam calls aim to install malicious software on a victim’s device, enabling the attackers to gain unauthorized access to their personal information or control their devices.
Measures for Reducing Spam Calls
Various measures are taken to minimize spam call occurrences, particularly within the Google Phone app. This includes:
- Improved Call Filtering: The Google Phone app employs sophisticated algorithms to analyze calls and identify suspicious patterns, significantly reducing the number of spam calls reaching users.
- Real-time Data Analysis: The app continuously monitors call data and user reports to identify emerging trends and patterns in fraudulent call tactics, adapting its filtering systems in real-time.
- Community Reporting: Users are encouraged to report fraudulent calls, providing valuable data to improve the app’s filtering mechanisms.
- Collaboration with Carriers: Google Phone collaborates with telecommunication carriers to block known spam numbers and prevent their calls from reaching users.
Methods for Reporting Fraudulent Calls
Reporting fraudulent calls is essential to improve spam call detection.
- Google Phone App: The app usually offers a dedicated reporting mechanism within the call interface to flag suspicious calls, providing details about the call and allowing for user feedback.
- Dedicated Reporting Tools: Some platforms offer specific tools or dedicated channels to report fraudulent activities, often including detailed forms to capture call information and other relevant details.
- Contacting Authorities: In cases of suspected fraud or scams, contacting the relevant authorities, like the Federal Trade Commission (FTC) or local law enforcement, can be beneficial for reporting the issue.
Comparison of Spam Call Detection Methods
| Phone App | Detection Method | Effectiveness |
|---|---|---|
| Google Phone | AI-powered analysis of call patterns, user reports, and carrier collaboration | High |
| Samsung Phone | Combination of blacklists, filtering, and machine learning | Moderate |
| LG Phone | 主にデータベースを利用したスパム対策 | Moderate |
Impact of Verification on Call Quality and User Experience
The proliferation of fraudulent calls and spam has significantly impacted the call experience for many users. Implementing verification methods is crucial to mitigate these issues, but it’s equally important to consider how these processes affect the overall user experience. This discussion delves into the potential effects of verification on call quality and user experience, from the perspective of both the caller and the recipient.Verification procedures, while vital for combating fraud, can introduce new challenges if not carefully designed.
A seamless and efficient verification process is key to ensuring users continue to find value in using the calling platform, while simultaneously enhancing security and trust.
Google’s phone app is working hard on verified calls, especially for LG and Samsung users, to combat fraud and spam. It’s a constant battle, but initiatives like these are crucial for a better user experience. Speaking of impressive displays, did you know that the San Diego Museum has a ship ton of breathtaking boats? this san diego museum has a ship ton of breathtaking boats It’s amazing to see such meticulous preservation and the sheer variety on display.
Back to the topic, this ongoing effort to verify calls is essential for protecting users from scams and unwanted communications.
Verification Process and User Experience
The verification process itself can significantly impact the user experience. A smooth, intuitive process minimizes frustration and ensures users remain engaged. Conversely, a complex or lengthy verification process can deter users, potentially leading to lower adoption rates of verified calling features. This is especially important for users who are less tech-savvy or who may encounter technical issues during the process.
Impact on Incoming Call Quality
Verification plays a crucial role in improving the quality of incoming calls. By confirming the identity of the caller, verification reduces the likelihood of receiving fraudulent or unwanted calls. This results in a cleaner call experience for recipients, as they are less likely to be bothered by spam or scams. A decrease in unwanted calls directly translates into a more positive user experience.
Comparison of Verified and Unverified Calls
The user experience of verified calls differs significantly from that of unverified calls. Verified calls are often perceived as more trustworthy and reliable, reducing the risk of being subjected to fraudulent activity. Unverified calls, on the other hand, often carry a higher risk of being fraudulent or unwanted. This difference in perceived risk directly impacts the user’s emotional response to the call.
Potential Challenges During Verification
Several challenges can arise during the verification process. Technical glitches, such as connection problems or slow verification times, can frustrate users and potentially dissuade them from completing the process. Discrepancies between the verification request and the user’s expected experience can also lead to confusion and disengagement. Effective communication and proactive support are essential to minimize these potential frustrations.
Verification Approaches: Pros and Cons
| Verification Approach | Pros | Cons |
|---|---|---|
| Phone Number Verification | Simple, widely available, and often quick. | Potentially less secure, especially if the phone number is easily obtained or compromised. |
| Email Verification | Often reliable and secure. | Requires an email address, which might not be available for all users. |
| Two-Factor Authentication (2FA) | Provides strong security, increasing the difficulty for fraudsters to impersonate users. | Can be more complex for some users, requiring additional login steps. |
| Biometric Verification | Adds a layer of security and convenience. | Requires compatible devices and can sometimes be less accessible. |
Verification methods each have their advantages and disadvantages, and the ideal approach will depend on the specific context and needs of the platform.
Security Protocols and Vulnerabilities
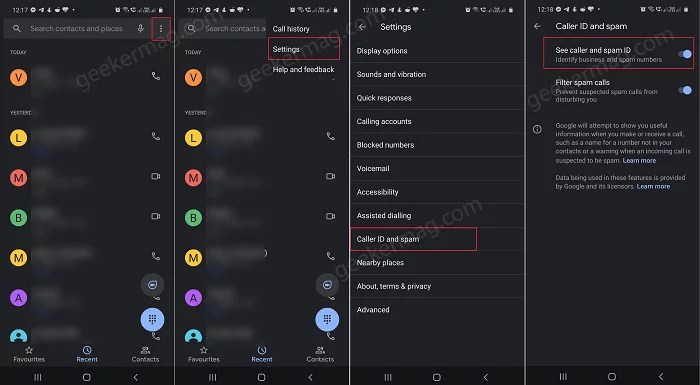
Protecting phone calls from fraud requires robust security protocols. Google Phone’s approach to verified calls relies on a layered defense system. These systems, while effective, are not impenetrable, and understanding potential vulnerabilities is crucial for maintaining trust and preventing malicious activities. This section delves into the specifics of these protocols, their inherent weaknesses, and strategies to enhance their resilience.
Security Protocols Used in Google Phone App
Google Phone employs a combination of authentication methods and verification processes to authenticate caller identities and prevent fraudulent calls. These include, but are not limited to, multi-factor authentication (MFA) using PINs, passwords, or biometric scans, and call verification through trusted networks. The core aim is to establish a clear chain of trust from the caller to the recipient.
This approach helps to filter out malicious calls by verifying the legitimacy of the originating numbers.
Potential Vulnerabilities and Exploits
Despite robust security measures, vulnerabilities exist. One potential weakness lies in the potential for spoofing attacks. Attackers might manipulate caller ID information to disguise their identity, making it difficult to identify fraudulent calls. Another area of concern is the possibility of vulnerabilities in the underlying authentication protocols. These could potentially be exploited by sophisticated attackers to bypass verification measures and gain unauthorized access.
Further, flaws in the verification processes could allow fraudulent calls to slip through, even with multiple layers of authentication. Finally, the constant evolution of technology necessitates ongoing adaptation to new and sophisticated attack vectors.
Trying to reduce fraud and spam calls on my Google phone app, especially with LG and Samsung devices, is a real headache. Fortunately, finding a reliable installer like the backbone pro controller surface pro poker face installer for my Surface Pro might actually help me focus on the problem. I’m hoping this new approach can streamline the process and make it easier to identify and block those pesky calls, improving my overall phone app experience.
Strategies for Enhancing Call Security
Enhancements to the security of calls can include strengthening the underlying authentication protocols to counter evolving attack methods. Implementing advanced algorithms to detect spoofing attempts and verifying call origination against multiple databases of known fraudulent numbers will help. Incorporating machine learning (ML) models to analyze call patterns and identify unusual behavior could also aid in preventing fraud. Furthermore, a strong focus on user education is paramount.
Educating users on recognizing fraudulent call patterns, and on how to report suspicious calls, significantly enhances the effectiveness of the entire system.
Implementation on LG and Samsung Phones
Google Phone’s security protocols are implemented on LG and Samsung devices through a unified platform. This ensures a consistent experience and security across different phone models. The underlying security architecture is designed to handle the specific security requirements of each platform. The protocols are seamlessly integrated into the phone’s operating system and call handling mechanisms, providing a secure environment for all calls.
Table of Security Protocols and Associated Risks
| Security Protocol | Associated Risk |
|---|---|
| Multi-Factor Authentication (MFA) | Potential for credential compromise, bypass of MFA if weak passwords or security questions are used. |
| Call Verification through Trusted Networks | Vulnerability to compromised trusted networks or if the network is subject to manipulation. |
| Spoofing Detection Algorithms | Possibility of evasion by sophisticated spoofing techniques, false positives/negatives. |
| Machine Learning (ML) Models | Bias in the data used to train the models, potential for the models to be fooled by sophisticated attacks. |
Future Trends in Call Verification and Spam Reduction
The fight against fraudulent calls and spam is an ongoing battle. Phone apps are constantly evolving to meet the challenge, and future innovations promise to make calls safer and more reliable. Emerging technologies are poised to revolutionize how we verify calls and identify potentially malicious actors. This exploration delves into the anticipated advancements in call verification and spam reduction.
Emerging Technologies in Call Verification
Advancements in artificial intelligence (AI) and machine learning (ML) are significantly impacting call verification. AI algorithms can analyze voice patterns, speech characteristics, and call metadata to identify potential fraudsters with remarkable accuracy. Sophisticated algorithms can now distinguish between legitimate and spoofed calls with higher precision than traditional methods. This improved accuracy leads to a more reliable user experience and reduces the number of unwanted calls.
Future Trends in Spam Reduction and Fraud Prevention, Google phone app verified calls lg samsung context fraud spam reduction
The volume of spam calls and fraudulent activity continues to rise, demanding proactive measures. Future trends in spam reduction will likely focus on real-time identification and blocking of suspicious calls, leveraging advanced techniques like predictive modeling to anticipate and prevent fraud. Utilizing a combination of AI, big data analytics, and sophisticated algorithms to analyze vast datasets of call data will enable the identification of emerging patterns and anomalies.
These measures will further enhance the effectiveness of call verification and spam filtering.
Evolution of Verification Methods
Verification methods are likely to evolve beyond traditional methods. Biometric authentication, like voice recognition and facial recognition, may become more integrated into call verification systems. This integration could enhance security by verifying the caller’s identity and reducing the risk of impersonation. Furthermore, distributed ledger technologies (DLTs), such as blockchain, could provide secure and tamper-proof records of call verification, increasing trust and transparency in the system.
Potential Innovations in Call Verification and Spam Reduction Processes
Innovative approaches to call verification and spam reduction are continuously being developed. These include leveraging caller location data to identify potential fraud, and integrating caller reputation systems based on historical call data. Moreover, collaborative efforts among telecommunication providers, app developers, and law enforcement agencies to share information and best practices are critical for improving the effectiveness of call verification and spam reduction.
Table Predicting Future Advancements in Call Verification Technologies
| Technology | Description | Impact |
|---|---|---|
| AI-powered Voice Analysis | Algorithms analyze voice patterns and speech characteristics to identify potential fraud. | Increased accuracy in identifying fraudulent calls. |
| Biometric Authentication (Voice/Facial) | Integration of voice and facial recognition for caller verification. | Enhanced security and reduced impersonation risk. |
| Distributed Ledger Technology (Blockchain) | Secure and tamper-proof records of call verification. | Increased trust and transparency in call verification systems. |
| Predictive Modeling | Anticipating and preventing fraud based on analysis of call data patterns. | Proactive fraud prevention. |
| Caller Reputation Systems | Evaluation of caller history for spam or fraud. | Improved spam filtering. |
Case Studies and Real-World Examples
Real-world examples illuminate the effectiveness and limitations of fraud prevention strategies. Analyzing successful implementations and instances of circumvention provides valuable insights into the evolving tactics of fraudsters and the necessary adjustments in verification methods. Understanding how verification processes impact call quality and user experience is crucial for maintaining user trust and adoption.
Successful Fraud Prevention Strategies
Various telecom companies have implemented strategies that have proven effective in reducing fraudulent calls. One such example involves integrating caller ID verification with a robust database of known fraudsters. This proactive approach helps identify and block calls originating from these sources, significantly decreasing the number of fraudulent calls reaching customers. Another strategy involves using advanced algorithms to analyze call patterns and identify suspicious behavior in real-time.
This approach allows for swift action to prevent fraudsters from exploiting vulnerabilities in the system.
Circumvention of Verification Measures
Fraudsters are constantly adapting their techniques to bypass verification measures. Sophisticated techniques include using spoofed caller IDs to mask their origin or employing automated systems to generate and place numerous calls. They may also exploit vulnerabilities in the verification process, such as weak authentication methods or outdated software. The continuous evolution of fraud necessitates a dynamic approach to verification.
Common Patterns in Fraudulent Calls
Analysis of fraudulent calls reveals recurring patterns that can be used to develop effective detection systems. A common pattern involves calls from unfamiliar numbers, especially those with unusual prefixes or international dialing codes. Another frequent pattern involves the use of robocalls with automated messages, often aiming to collect personal information or financial data. These patterns provide insights into common fraud schemes, allowing for targeted countermeasures.
Hypothetical Fraudulent Call Scenario and Analysis
Imagine a scenario where a user receives a call claiming to be from their bank, requesting immediate verification of account details. The caller uses a convincing voice and provides a realistic-sounding automated message. The caller ID displays a legitimate bank number. This is a common tactic used by fraudsters.The analysis reveals that this call exhibits several characteristics of a fraudulent call:
- The caller’s identity is disguised or spoofed.
- The request for sensitive information is unusual and suspicious.
- The caller’s urgency to obtain immediate verification is an indicator of a potential scam.
Furthermore, the verification process should not be based on voice identification alone. The bank should have established a separate verification channel to authenticate the request, like an email or text message. This layered approach to authentication helps mitigate the risk of fraud.
Final Wrap-Up
In conclusion, Google Phone app’s verified calls, while crucial for combating fraud and spam, are not without their challenges. The intricate interplay of verification methods, security protocols, and user experience is complex and dynamic. Future advancements in verification technologies are crucial for staying ahead of evolving fraud tactics. Understanding the nuances of these systems is vital for both users and developers, ultimately shaping the future of secure communications.
We hope this comprehensive look has offered a clear picture of the ongoing fight against fraud and spam in the world of mobile communications.