Google Password Manager sharing function spotted! This exciting development promises a new level of collaborative password management, potentially revolutionizing how we handle sensitive information. Imagine effortlessly sharing login credentials with family members, colleagues, or even trusted service providers. The function’s details are still emerging, but early reports suggest various access levels and security measures are in place to safeguard shared passwords.
This new feature, likely to be integrated into Google’s existing password management platform, will enable streamlined access to accounts for multiple users. It’s a significant step towards more efficient and secure collaborative access, though the specifics on how this sharing works are still under wraps. The introduction of such a feature will undoubtedly impact existing password management practices and spark debate about security and privacy implications.
Google Password Manager Sharing Function Overview
Google’s Password Manager now allows you to securely share passwords with other users. This feature enhances collaboration and simplifies password management for groups, such as families or work teams. It’s designed to provide a secure and streamlined approach to sharing access to saved login credentials.This feature offers granular control over access permissions, ensuring only authorized individuals can access sensitive information.
Understanding the nuances of access levels and the secure sharing process is crucial for safeguarding your accounts and maintaining data privacy.
Sharing Access Levels and Permissions
The Password Manager sharing function grants different access levels, enabling you to customize the permissions for each shared account. These levels determine what actions authorized users can perform. This granular control ensures that only necessary information is accessible, maintaining a balance between collaboration and security.
- Full Access: Users with full access can view, edit, and delete the shared credentials.
- View-Only Access: Users with view-only access can only view the credentials but cannot modify or delete them.
Enabling and Configuring Password Sharing
The process for enabling and configuring password sharing is straightforward and user-friendly. It involves a few steps to set up and manage access for different users.
- Select the Account to Share: Identify the specific account you want to share within the Google Password Manager interface.
- Choose the Sharing Recipient: Select the individual or group you want to share the account with, specifying the desired access level. This step is critical for maintaining security.
- Confirm Sharing Permissions: Once the recipient is selected, confirm the sharing permissions to finalize the process. Ensure you understand the permissions you are granting before confirming.
Security Implications of Password Sharing
Sharing passwords introduces security considerations. Carefully evaluate the security implications and potential risks before sharing credentials. Consider the trustworthiness of the recipient and the potential impact of compromised access.
“The security of the shared account depends heavily on the trustworthiness and security practices of the recipient.”
Sharing passwords, while convenient, necessitates a heightened awareness of potential vulnerabilities. Understanding the risks and implementing necessary safeguards is paramount to mitigating potential threats.
Use Cases and Benefits
Password sharing, a relatively new feature in Google Password Manager, unlocks significant potential for streamlining access and collaboration within households, businesses, and other groups. This function addresses the need for secure and efficient password management in various contexts, offering distinct advantages over traditional methods. Understanding the diverse use cases and benefits is crucial for effectively leveraging this powerful tool.Sharing passwords can be incredibly beneficial in a variety of scenarios, fostering trust and collaboration while mitigating the risks associated with individual password management.
By centralizing access and control, password sharing facilitates secure and efficient workflows within groups.
Household Use Cases
Password sharing within a household simplifies access to shared accounts, such as Netflix, Spotify, or online banking. This ensures everyone in the family can easily access accounts without needing individual logins. It simplifies the process for family members who may not be as tech-savvy.
- Joint accounts for streaming services, like Disney+ or Hulu, eliminate the need for separate logins, facilitating easier access for all family members.
- Shared access to online shopping accounts for joint purchases simplifies the process for everyone in the family, especially when multiple people are involved.
- Facilitating shared access to educational platforms for parents and children ensures everyone in the family can access resources easily.
Business Use Cases
In a business setting, password sharing within teams or departments streamlines access to critical resources and applications. This can be particularly useful for project-based work, collaborative document sharing, and team communication tools.
- Teams can easily share access to project files and documents, streamlining collaboration and increasing productivity.
- Shared access to company accounts and platforms improves efficiency, reduces friction, and allows employees to access information more quickly.
- Accountability and control can be improved by limiting access to sensitive data to authorized personnel only, safeguarding important information.
Comparison with Other Collaborative Access Methods
Password sharing offers a secure and efficient alternative to other methods of collaborative access.
| Method | Description | Security | Ease of Use | Cost |
|---|---|---|---|---|
| Password Sharing (Google Password Manager) | Centralized password management for shared accounts, accessible by authorized users. | High, with strong encryption and user authorization. | High, with a user-friendly interface. | Free (with Google account). |
| Shared Credentials (Spreadsheets, Documents) | Manually sharing login credentials through external documents. | Low, credentials are vulnerable to breaches or unauthorized access. | Low, prone to errors and inconsistencies. | Low (often free). |
| Group Accounts | Creating accounts with group permissions. | Moderate, depends on the platform’s security features. | Moderate, requires understanding of account setup. | Variable (depends on the platform). |
Password sharing through Google Password Manager is demonstrably more secure and user-friendly than other methods, offering a streamlined approach to collaborative access while mitigating security risks.
Technical Implementation
Google’s Password Manager Sharing function leverages a robust and secure architecture to enable seamless collaboration while maintaining user privacy. This section delves into the technical mechanisms behind this functionality, highlighting the security protocols and the components involved.The technical implementation of password sharing involves several crucial steps, each designed to safeguard sensitive data and maintain user control. These steps encompass secure data transfer, storage, and access control.
The core principles of encryption, authorization, and audit trails are fundamental to the design.
Secure Data Transfer Mechanisms
The transfer of shared passwords between users is accomplished using industry-standard encryption protocols. These protocols ensure that the data is unintelligible to unauthorized parties during transit. A key aspect of this process is the use of end-to-end encryption, meaning that only the intended recipient can decrypt the shared data.
Data Storage and Access Control
Shared passwords are stored securely in Google’s encrypted database. This storage mechanism utilizes multiple layers of security, including data encryption at rest. Furthermore, access control mechanisms restrict access to the shared passwords to only authorized users. This is achieved through the use of unique access keys and strict authentication procedures.
Security Measures for Shared Passwords
Protecting shared passwords involves multiple layers of security, extending beyond encryption. Robust access controls, multi-factor authentication, and regular security audits are crucial elements of this approach. Furthermore, the system implements measures to detect and mitigate potential security threats.
Components of the Password Sharing Process
The following diagram illustrates the key components involved in the password sharing process:
+-----------------+ +-----------------+ +-----------------+
| User 1 |-----| Password Manager |-----| User 2 |
+-----------------+ +-----------------+ +-----------------+
| |
| Secure Data Transfer (encrypted) |
| |
| Data Storage (encrypted) |
| |
| Access Control (Authorization) |
| |
| Multi-Factor Authentication (MFA) |
+-----------------+ +-----------------+ +-----------------+
| Security Audits |--------------------------------| Security Audits |
+-----------------+ +-----------------+
This diagram illustrates the simplified flow of data within the system.
Spotted: Google’s password manager is apparently getting a sharing function. This got me thinking about how cloud services are changing the way we interact with digital tools, like mach makes his point about Fortnite and cloud gaming , and how they could revolutionize password management. Imagine being able to seamlessly share access with family or colleagues, without the hassle of remembering separate logins.
It’s definitely a fascinating development for password management.
Each component plays a critical role in ensuring secure password sharing. User 1 initiates the sharing request, which is processed by the Password Manager. The Password Manager encrypts the data and securely transmits it to User 2, ensuring confidentiality. Security audits at each stage help to detect and address potential vulnerabilities. Multi-factor authentication adds an extra layer of security to the process, preventing unauthorized access.
Security Considerations
Password sharing, while convenient, introduces significant security risks. Careless implementation can expose sensitive data to unauthorized individuals, leading to financial losses, identity theft, and reputational damage. Understanding these vulnerabilities and implementing robust mitigation strategies is crucial for safeguarding shared passwords.
Potential Security Vulnerabilities
Password sharing, even within trusted relationships, can create entry points for malicious actors. A compromised account within a shared group can expose all shared credentials, opening the door to unauthorized access to various online services. Phishing attacks, malware infections, or social engineering tactics can be leveraged to gain access to a shared password. This vulnerability is further amplified when the shared password is not regularly reviewed or updated.
Risks of Unauthorized Access and Misuse
Unauthorized access to shared passwords can lead to a cascade of problems. Malicious actors could drain bank accounts, make unauthorized purchases, access personal information, or even impersonate individuals. The misuse of shared passwords can result in significant financial and reputational damage. For example, a compromised account associated with a shared password could allow attackers to access sensitive financial data, making it easier to conduct fraudulent transactions.
Steps to Mitigate Security Threats
Robust security measures are essential to protect shared passwords. These measures should include:
- Regular password reviews and updates. Regularly reviewing and updating shared passwords can help mitigate the risks associated with static credentials. This is especially important in cases where there’s a significant change in the relationship or access rights of the involved parties.
- Strong password generation and management. Using strong, unique passwords for each shared account is paramount. Implementing a robust password management system, like a password manager, can help ensure that all shared passwords are complex and difficult to crack.
- Secure communication channels. Sharing passwords through secure channels, like encrypted messaging apps or VPNs, is vital. Avoid sharing sensitive information over public or insecure networks.
- Implementing multi-factor authentication (MFA). Enabling MFA adds an extra layer of security, requiring multiple verification steps to access shared accounts.
- Regular security awareness training. Educating users about potential threats and best practices for password security is essential. This can involve workshops, online courses, or informative materials to highlight common scams and security threats.
Best Practices for Secure Password Sharing
Implementing a well-defined set of rules and protocols can significantly improve the security of shared passwords.
| Best Practice | Description |
|---|---|
| Establish clear roles and responsibilities | Define who is authorized to access and modify shared passwords, and under what circumstances. |
| Employ strong, unique passwords | Use complex passwords that are difficult to guess or crack. Avoid using easily guessable words or personal information. |
| Regular password rotation | Change shared passwords at predetermined intervals to mitigate risks associated with static credentials. |
| Secure communication channels | Use encrypted messaging or secure channels when sharing passwords to prevent eavesdropping. |
| Regular security audits | Conduct periodic reviews of shared password practices to identify and address potential vulnerabilities. |
Comparison with Competitors
Password sharing is a crucial feature in modern password management. Google’s approach, while innovative, sits within a broader landscape of similar functionality offered by competitors. Understanding how Google’s implementation stacks up against others provides valuable context for users considering their options.
Key Differences in Implementation
Google’s approach to password sharing leverages the existing Google ecosystem. This seamless integration with other Google services, such as Gmail and Drive, is a significant advantage, streamlining the user experience. However, this integration might not be universally appealing to users who prefer a more standalone password manager experience. Competitors often have different strategies for sharing passwords, which can impact the level of security and ease of use.
User Experience Comparison
The user experience of password sharing varies significantly across different platforms. Some solutions prioritize a streamlined, intuitive interface, while others might be more complex. Google’s design, with its familiar Google interface, aims for a user-friendly experience. Conversely, other password managers may have distinct interfaces, requiring users to adapt to a different workflow. Factors like ease of setup, the visibility of shared items, and the clarity of access permissions are key considerations.
Security Considerations in Password Sharing
Security is paramount in password sharing. Google emphasizes robust security measures, likely incorporating end-to-end encryption and access controls. However, the security posture of other solutions varies. Some competitors may offer similar security measures, while others might rely on less sophisticated techniques. A user’s choice should be influenced by the security measures adopted by each platform and how well they address potential vulnerabilities.
Comparative Table of Password Sharing Features
| Feature | Google Password Manager | LastPass | 1Password | Bitwarden |
|---|---|---|---|---|
| Integration with other Google services | High (seamless access) | Moderate (some integration) | High (tight integration) | Low (limited integration) |
| Ease of setup | High (intuitive) | High (straightforward) | Moderate (slightly more complex) | High (easy to use) |
| Visibility of shared items | Good (clear organization) | Excellent (detailed visibility) | Excellent (thorough controls) | Good (well-organized) |
| Access Permissions | Good (flexible controls) | Excellent (granular controls) | Excellent (detailed access) | Good (clear control) |
| Security Features | Robust (end-to-end encryption likely) | Robust (strong security protocols) | Robust (strong security practices) | Robust (secure architecture) |
Note: This table provides a general comparison. Specific features and implementation details may vary depending on the specific version or plan.
Strengths and Weaknesses of Google’s Approach
Google’s password sharing function benefits from its seamless integration with other Google services. This ease of use is a key strength. However, this integration might limit flexibility for users who prefer a more independent password management solution. Competitors, such as LastPass and 1Password, often offer more advanced features, including granular access controls and customizable sharing settings, potentially making them a better choice for specific use cases.
A comprehensive understanding of the specific requirements and priorities is essential when making a decision.
User Experience
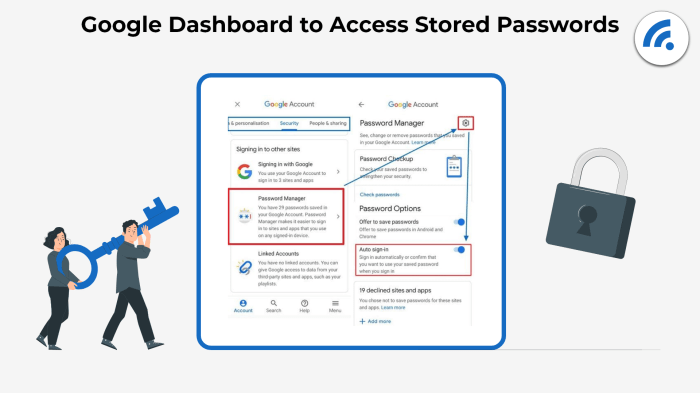
Sharing passwords within Google Password Manager is designed for intuitive and secure access. The user interface prioritizes simplicity and clarity, allowing users to easily grant access to others while maintaining control over sensitive information. This approach is crucial for streamlining collaboration and enhancing security in shared environments.
Sharing Passwords
The process for sharing passwords within Google Password Manager is straightforward. Users can select the specific accounts they wish to share, granting varying levels of access. This granular control ensures that only necessary information is shared, minimizing potential security risks.
- Selecting Accounts: Users identify the accounts they want to share by navigating to the specific account within Google Password Manager. A clear selection interface allows for a targeted approach, avoiding accidental sharing of unnecessary data.
- Choosing Recipients: Once the accounts are selected, users can choose the recipients for the shared access. This might involve selecting individual users or groups of users within the context of a team or organization.
- Defining Access Levels: Users can define the extent of access for each recipient. This allows for fine-grained control, granting limited or full access depending on the requirements of the situation. For example, a team member might only need access to view login credentials for a specific project, whereas a full administrator might require access to all accounts within the organization.
Managing Shared Passwords
Users maintain oversight over shared passwords through a dedicated management interface. This includes monitoring access levels and revoking access as needed. Real-time updates ensure that changes are reflected immediately.
- Monitoring Access: A clear overview of all shared passwords, recipients, and access levels is provided within the management interface. Users can easily review and track who has access to what accounts.
- Revoking Access: If a user needs to revoke access for a particular recipient, the process is straightforward and reversible. This feature ensures that sensitive information is secured from unauthorized individuals.
- Updating Access Levels: Adjusting the access level for shared passwords is easily managed within the system. For example, a user might need to modify a team member’s access to a specific project. This is easily done through the interface without affecting other users or access levels.
Step-by-Step Guide
This guide details the procedure for sharing passwords within Google Password Manager:
- Open Google Password Manager: Launch the application on your chosen device.
- Select Accounts: Navigate to the account you wish to share.
- Choose Recipients: Select the recipient(s) for shared access. This could involve adding a specific user or a group of users. A clear user interface will display options for selection.
- Define Access Levels: Determine the appropriate access level for each recipient. For example, “View Only,” “Edit,” or “Full Access” can be selected. This step ensures that only necessary access is granted.
- Review and Confirm: Review the shared access details before confirming. Confirming shares your password information with the selected recipient(s).
- Manage Shared Passwords: Navigate to the management interface to monitor, update, or revoke shared passwords as needed.
Potential Impact on Users

Google Password Manager’s sharing function promises to revolutionize how we manage our online accounts. This new capability has the potential to dramatically alter user behavior, making password management both easier and more collaborative. However, it also introduces new security considerations and requires careful consideration of the implications.
This function will undoubtedly influence how users approach password security and the sharing of sensitive information. It will affect not only individual users but also the dynamics of family, professional, and social relationships. Understanding the potential positive and negative consequences is crucial for users to make informed decisions about adopting this feature.
User Behavior Changes
The availability of password sharing will likely lead to a shift in user behavior. Users may be more inclined to share passwords with family members or trusted colleagues for joint access to accounts. This collaborative approach could streamline tasks and improve efficiency, especially in shared households or work environments. Conversely, users might become more reliant on shared passwords, potentially increasing the risk of breaches if security protocols are not followed.
Positive Consequences of Password Sharing
Password sharing offers numerous advantages. Users can streamline their daily online tasks, avoiding the need to individually manage multiple passwords for shared accounts. This is particularly useful for families managing household accounts or for colleagues working on collaborative projects. Sharing also reduces the cognitive load associated with remembering and managing unique passwords for every account.
Hey everyone! Just saw that Google’s password manager is getting a sharing function. Pretty cool, right? This is a huge step forward for collaborative password management, especially for families or couples. Meanwhile, there’s been a lot of buzz surrounding the Chevy Bolt battery issues, and a class action lawsuit has been filed for compensation. If you own a Chevy Bolt, you might want to check out the details on chevy bolt gm compensation class action batteries to see if you’re eligible for compensation.
Regardless, I’m excited to see how this Google password sharing feature will work in practice.
Examples of Daily Use Cases
Users can leverage password sharing in various ways. For instance, a family could share access to their online banking accounts, enabling parents to oversee their children’s accounts or help them manage online purchases. Similarly, shared access to streaming services could simplify managing accounts for a group of friends or family members. In a business setting, password sharing allows team members to access shared projects and resources without needing to remember individual login credentials.
Benefits for Users
Password sharing provides numerous benefits. Users can enhance their overall efficiency by simplifying access to shared accounts. Streamlined account management can free up valuable time, allowing users to focus on other tasks and responsibilities. Reduced password complexity also contributes to better overall security, as users are less prone to using weak or easily guessed passwords. Furthermore, the ability to collaborate on account management can improve the quality of interactions and experiences within a shared environment.
Potential Negative Consequences of Password Sharing, Google password manager sharing function spotted
The convenience of password sharing comes with potential downsides. Increased reliance on shared credentials could create a single point of failure. If a shared account is compromised, all users with access to the password could be affected. The responsibility for maintaining account security becomes a collective effort, and any lapses in security practices by one user can have a cascading effect on the entire group.
It’s essential for users to establish clear protocols and expectations for password security when sharing credentials.
Security Considerations
Users need to be aware of the heightened security risks associated with password sharing. Robust security protocols, including strong password requirements, two-factor authentication, and regular account reviews, are essential for protecting shared accounts. Transparency and communication between users are critical for establishing a shared understanding of security best practices. Password managers can play a vital role in managing and securing shared passwords.
Future Implications
Google’s Password Manager Sharing function has the potential to reshape how we manage and share sensitive information. Its future evolution hinges on user needs and security considerations. This exploration delves into potential developments, their impact on users, and the evolving security landscape.
Google’s password manager sharing function is a pretty big deal, making it easier for families to share logins. While that’s great, it got me thinking about another aspect of digital safety, like another look at child influencers on Instagram. Another look at child influencers on Instagram raises important questions about online safety for kids. Ultimately, Google’s password sharing feature, while useful, needs to be coupled with responsible digital habits, whether it’s for parents or kids.
The future of password sharing is likely to involve greater integration with other Google services and platforms. Imagine seamlessly sharing login credentials for a subscription service with a trusted family member or colleague, all within the Google ecosystem. This level of integration will likely depend on careful consideration of privacy and security protocols.
Potential Improvements to User Experience
Streamlined sharing processes and intuitive interfaces are crucial for user adoption and satisfaction. The current system might benefit from an improved visual representation of shared accounts, providing users with a clear overview of who has access to which data. Furthermore, clear guidelines and prompts regarding the level of access granted would enhance transparency. This enhanced clarity will make the sharing process less error-prone and more understandable for the average user.
Enhanced Security Features
Security enhancements are paramount. Future developments could incorporate multi-factor authentication (MFA) specifically for shared accounts. This would add an extra layer of protection beyond basic username/password combinations. Additionally, the system could leverage advanced threat detection and prevention mechanisms to flag suspicious activity related to shared accounts. Real-time monitoring of access patterns could help identify and mitigate potential breaches, safeguarding sensitive data.
Integration with Other Google Services
Seamless integration with other Google services is a significant possibility. Imagine the ability to share login credentials for a shared Google Workspace account or a specific Google Drive folder directly through the password manager. This would enhance collaboration and data management within the Google ecosystem. The integration would likely leverage existing security protocols to ensure data integrity.
Future Evolution of Sharing Types
The types of sharing could evolve beyond simple “read-only” access. The potential for controlled “edit” or “admin” access to shared accounts might arise in the future. This could streamline workflows for collaborative projects or support access to sensitive information for authorized personnel. Examples include shared access to subscriptions for family or business needs.
Addressing Privacy Concerns
Future implementations must address privacy concerns with greater precision. Implementing granular control over access permissions and data visibility would be essential. Transparency in data usage and sharing policies would build trust and alleviate user apprehensions about privacy breaches. A detailed privacy policy with user-friendly explanations would address this issue.
Technical Specifications
The Google Password Manager Sharing function, while promising, hinges on robust technical underpinnings. Understanding these specifications is crucial for appreciating the security and practicality of this feature. A secure and user-friendly system relies on careful consideration of encryption protocols, data storage, identity verification, and credential protection.
Encryption Protocols and Data Storage
The security of shared passwords is paramount. This necessitates robust encryption protocols to protect sensitive data during transmission and storage. Google likely utilizes industry-standard encryption algorithms, such as Advanced Encryption Standard (AES), to safeguard the confidentiality of shared credentials. This involves encrypting the passwords before they are shared, ensuring that even if an unauthorized party intercepts the data, it remains unintelligible.
The encrypted data is stored in Google’s secure servers, employing advanced data protection measures. Data is likely organized in a manner that facilitates secure retrieval and access for authorized users, while limiting access for unauthorized ones.
Verification of User Identities During Sharing
Ensuring the authenticity of users sharing and receiving passwords is crucial. Google likely employs multi-factor authentication (MFA) or similar identity verification methods to prevent unauthorized access. This involves a series of checks to confirm the identity of the user requesting and the user receiving the shared password. These measures could include requiring a one-time password, a biometric scan, or a combination of verification methods.
This layered approach minimizes the risk of unauthorized password sharing.
Protection of Shared Credentials
Protecting shared credentials requires a multi-layered approach. Google likely implements access controls and permission management systems to restrict access to shared passwords. These controls might include time-limited access, restricting access to specific devices, or implementing granular permissions based on user roles. Furthermore, Google might employ auditing mechanisms to track access and usage patterns, allowing for rapid identification and response to any potential security breaches.
Regular security audits and updates are critical to maintaining the integrity of the system. These protocols should be adaptable to new threats and evolving security landscapes.
Last Point: Google Password Manager Sharing Function Spotted
The Google Password Manager sharing function, while promising, presents a complex interplay of security and convenience. Understanding the intricacies of access levels, security protocols, and potential vulnerabilities is crucial. This new functionality will undoubtedly shape how users approach password management in the future, and its success hinges on robust security measures and clear user guidelines. Further details on the technical implementation, user experience, and security considerations are eagerly awaited.