Google G Suite Twitter account hacked bitcoin scam is a prevalent and insidious issue. Criminals exploit vulnerabilities in both G Suite and Twitter to trick unsuspecting users into handing over their hard-earned money. This often involves elaborate phishing campaigns, social engineering tactics, and impersonation of legitimate entities. The scams can range from individuals to large corporations, resulting in substantial financial and reputational damage.
This detailed guide explores the intricacies of this scam, from the initial attack vectors to the recovery process and preventive measures.
The modus operandi frequently begins with a seemingly legitimate email or message, often mimicking support notifications or important account updates. These messages usually contain malicious links or attachments, luring victims into revealing crucial information. This initial compromise often leads to unauthorized access of the victim’s G Suite and Twitter accounts. Criminals then use these accounts to execute their schemes, spreading further deceit and potentially compromising other accounts connected to the victim’s compromised profiles.
Defining the Scam
The digital landscape is rife with malicious actors seeking to exploit vulnerabilities in online platforms. One particularly insidious form of fraud targets individuals and businesses using Google Workspace (G Suite) and Twitter accounts. These scams often involve the deceptive use of compromised accounts to extort money, frequently in the form of Bitcoin. Understanding the modus operandi of these attacks is crucial for prevention and mitigation.Compromised accounts are frequently leveraged for a coordinated campaign of deception.
The perpetrators meticulously craft a series of steps designed to gain trust and extract payment. This begins with the initial compromise of the account, typically via phishing or malware.
Typical Modus Operandi
The typical Bitcoin scam related to hacked G Suite and Twitter accounts involves several stages. Initially, attackers compromise the victim’s account, often through social engineering tactics or malware. Once access is gained, they alter account settings, such as email addresses and passwords, to prevent detection. This is followed by sending phishing emails to contacts, impersonating the victim or a trusted entity.
Ugh, the Google G Suite Twitter account hacked bitcoin scam is seriously frustrating. It’s a real headache dealing with these kinds of scams, but hey, at least there’s a good deal on a portable power station right now. If you’re looking for a reliable backup power source, check out this Anker portable power station back down best price 187.
Hopefully, this will help people avoid falling prey to scams like this one involving compromised accounts.
These emails frequently demand immediate payment to resolve the “hacking” issue, often demanding the payment be made in Bitcoin.
Heard about that Google G Suite Twitter account hack and the bitcoin scam? Yikes! It’s a reminder to be extra careful online, especially when it comes to sensitive data like login credentials. It’s all too easy to fall prey to these scams, especially with the ever-changing landscape of online privacy and security. Fortunately, companies like Oculus are proactively updating their privacy policies, including their GDPR compliance.
Check out the latest Oculus GDPR Privacy Center Terms of Service update here for a deeper dive into privacy best practices. Ultimately, we all need to stay vigilant about these scams and keep our online information secure.
Stages of the Scam
The progression of a hacked account Bitcoin scam typically unfolds in these phases:
- Account Compromise: Attackers infiltrate the victim’s account through phishing emails, malware, or exploiting vulnerabilities in security protocols. Compromised credentials, weak passwords, and clicking malicious links are frequent entry points.
- Impersonation and Deception: The attackers then impersonate the victim or a trusted entity (e.g., a company representative or bank). They craft convincing messages, often mimicking official communication channels like support tickets, to deceive contacts and gain their trust.
- Demand for Payment: The attackers create a sense of urgency, demanding payment in Bitcoin to “restore” the account or prevent further damage. They often leverage fear tactics and the victim’s unawareness of the situation to pressure them into compliance.
- Bitcoin Transfer and Escape: The victim, believing they are dealing with a legitimate authority, transfers the requested Bitcoin. The perpetrators then disappear, making recovery difficult.
Methods of Deception
Various methods are used to deceive victims in these scams. Understanding these methods is key to avoiding becoming a victim.
- Phishing Emails: These emails often appear to come from legitimate sources (e.g., Google, Twitter, banks) and contain links to malicious websites designed to steal login credentials. The emails frequently contain urgent demands or threats to trick the victim.
- Fake Support Tickets: Attackers may create fake support tickets or messages impersonating legitimate technical support teams. These messages lead victims to believe they are interacting with official support channels, further reinforcing the deception.
- Social Engineering: Attackers use psychological manipulation to exploit the victim’s trust and emotions. This may involve creating a sense of urgency, fear, or a perceived need for immediate action. This includes impersonating a friend or a trusted contact.
Role of Impersonation
Impersonation plays a central role in these scams. Attackers often pose as representatives of legitimate entities, such as the victim’s employer or a tech support team, to gain access to the victim’s account. The impersonation extends to both G Suite and Twitter, where attackers utilize stolen credentials to impersonate the victim and send fraudulent messages to contacts.
So, the Google G Suite Twitter account hack and the Bitcoin scam are definitely concerning. It’s a reminder of how vulnerable our online accounts can be. Interestingly, this sort of security breach parallels the recent news about Instagram Threads shutting down, part of Meta’s messaging platform overhaul. This underscores the need to be extra cautious when using social media and to avoid suspicious links, especially when dealing with financial transactions.
The whole Google G Suite Twitter account hacked Bitcoin scam situation highlights the importance of strong passwords and security measures, and it’s not just limited to Twitter anymore. instagram threads shutting down meta messaging seems to be a small piece of the bigger puzzle of how vulnerable we all are online.
Classification of Bitcoin Scams
| Scam Type | Tactics Used | Typical Target Audience |
|---|---|---|
| Account Compromise & Bitcoin Extortion | Phishing, malware, impersonation, fake support tickets | Individuals and businesses using G Suite and Twitter, especially those with valuable contacts |
| Fake Recovery Services | Impersonation, social engineering, fake support websites | Individuals and businesses who believe their accounts are compromised |
| Romance Scams with Bitcoin Demands | Social engineering, relationship building, impersonation | Individuals seeking romantic relationships online |
Identifying the Attack Vectors
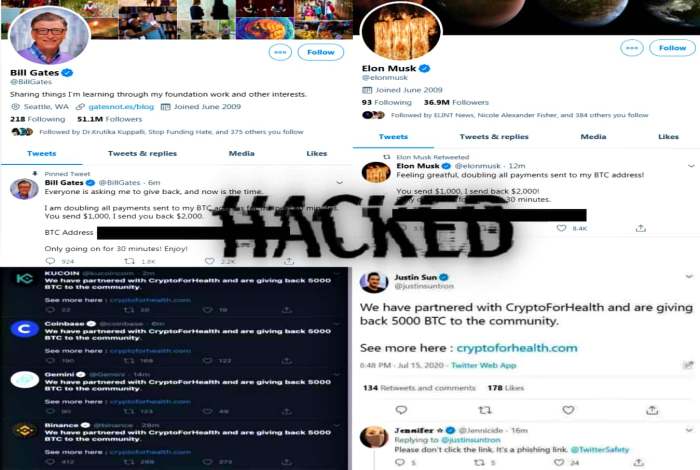
Compromised Google Workspace and Twitter accounts are often the entry points for sophisticated scams, particularly those involving cryptocurrency theft. Understanding the methods used by attackers to gain access is crucial for protecting personal and organizational accounts. These methods range from exploiting technical vulnerabilities to employing manipulative social engineering tactics. This section will detail the primary attack vectors employed in these scams, illustrating the technical and social engineering strategies used.The primary attack vectors used to compromise Google Workspace and Twitter accounts share some commonalities, but also exhibit distinct characteristics.
Criminals leverage both technical weaknesses and human vulnerabilities to gain unauthorized access. This analysis will delve into the specific attack vectors and illustrate the common phishing techniques used in these scams.
Primary Attack Vectors for Compromised Accounts
The primary attack vectors for compromising Google Workspace and Twitter accounts are multifaceted, encompassing technical vulnerabilities and social engineering tactics. Attackers meticulously target weaknesses in both platforms, aiming to gain unauthorized access.
Technical Vulnerabilities Exploited
Attackers often exploit vulnerabilities in web applications, including Google Workspace and Twitter. These vulnerabilities can include:
- Outdated Software: Software that is not regularly updated often contains known security flaws. Attackers can leverage these vulnerabilities to gain access to systems or data. Examples include outdated versions of operating systems, browsers, or software applications, leading to easily exploited security holes. Criminals can exploit these vulnerabilities through crafted exploits, taking advantage of outdated software’s known vulnerabilities.
- Weak or Default Passwords: Using weak or default passwords makes accounts vulnerable to brute-force attacks. Attackers use automated tools to try various combinations until they find a match. Many users reuse passwords across multiple platforms, creating a domino effect. Criminals can gain access to numerous accounts using easily guessable passwords.
- Unpatched Security Holes: Failing to install security patches promptly allows attackers to exploit known vulnerabilities. Regular security updates are crucial for maintaining system integrity and preventing unauthorized access. Attackers can exploit security flaws in unpatched systems to gain control of accounts or systems.
Social Engineering Techniques
Social engineering is a powerful tool in the arsenal of attackers, leveraging human psychology to manipulate victims into revealing sensitive information. Criminals craft convincing phishing emails and messages to trick individuals into divulging passwords, account credentials, or other sensitive data.
- Phishing Emails: Phishing emails are crafted to appear legitimate, often mimicking official communications from trusted organizations like Google or Twitter. These emails typically contain links to malicious websites designed to steal credentials. These emails are often personalized to target specific individuals, increasing their believability and thus the chances of a successful attack.
- Spear Phishing: Spear phishing targets specific individuals or organizations, tailoring the phishing emails to their specific interests or roles. This personalized approach increases the likelihood of the recipient clicking on malicious links or providing sensitive information.
- Baiting: Baiting involves enticing victims with something of value, such as a prize or reward, in exchange for sensitive information. Criminals create a false sense of urgency or opportunity, encouraging the victim to take action and reveal their credentials.
Examples of Phishing Emails and Malicious Links
Phishing emails often contain deceptive elements, designed to trick victims into revealing sensitive information.
- Fake Account Suspension Notifications: Phishing emails might claim an account has been suspended and require immediate action to reinstate it. These emails often include malicious links that redirect to fraudulent websites.
- Urgent Security Updates: Emails might falsely claim an urgent security update is required, urging the recipient to click on a link to download a malicious file or provide credentials. The emails often use threatening language to increase the sense of urgency and increase the chances of the recipient clicking the malicious link.
Comparison of Attack Vectors
| Attack Vector | Google Workspace | |
|---|---|---|
| Outdated Software | Vulnerable applications within the suite | Outdated platform and associated apps |
| Weak Passwords | Compromised Google accounts | Compromised Twitter accounts |
| Unpatched Security Holes | Unpatched vulnerabilities in Google Workspace applications | Unpatched vulnerabilities in Twitter applications |
| Phishing Emails | Spoofed Google communications | Spoofed Twitter communications |
| Spear Phishing | Targeted emails to employees | Targeted emails to prominent users |
Impact of the Scam
The Google Workspace (G Suite) account compromise and subsequent bitcoin scam exemplifies the devastating consequences of cyberattacks. Beyond the immediate financial losses, victims often face significant emotional distress and reputational damage. Understanding the full scope of this type of attack is crucial for individuals and businesses to better protect themselves and mitigate potential harm.The impact of such a scam extends far beyond a simple financial transaction.
It can shatter trust, erode confidence, and cause considerable stress for both individuals and organizations. The ripple effects can be felt throughout various aspects of their lives and operations, from personal finances to business reputation.
Financial Losses
The potential financial losses associated with a G Suite account compromise and bitcoin scam are substantial. Victims may lose money directly through fraudulent transactions initiated by hackers using compromised credentials. They may also face additional expenses related to recovery efforts, such as legal fees, forensic analysis, and account restoration. The scope of financial loss depends on factors such as the amount of money involved in fraudulent transactions and the timeliness of intervention.
For example, a small business that loses access to its financial records or customer data could incur substantial costs in restoring its operations.
Emotional Distress
Victims experience significant emotional distress due to the loss of control and trust. The feeling of vulnerability and betrayal can be overwhelming, leading to anxiety, depression, and post-traumatic stress. Furthermore, the associated reputational damage can further exacerbate emotional distress. For instance, a small business owner who experiences a breach of their email account could experience substantial anxiety about the safety of their clients’ sensitive information and their own business continuity.
Reputational Damage
Reputational damage is another significant consequence of a G Suite account compromise. The exposure of sensitive information or the perpetration of fraudulent activities in a victim’s name can severely damage their reputation, particularly in the case of businesses. This damage can lead to a loss of customers, partners, and investors. A compromised account could lead to false information being disseminated about the company, potentially damaging its brand image and client trust.
Legal Ramifications
The legal ramifications for those involved in perpetrating these scams can be severe. Perpetrators face criminal charges, including fraud, identity theft, and computer crimes. The severity of the charges depends on the extent of the financial losses, the number of victims, and the nature of the fraudulent activities. Legal proceedings can be costly and time-consuming, potentially leading to significant penalties and imprisonment for those involved.
Impact on Businesses and Individuals
Compromised accounts can disrupt business operations significantly. The loss of access to essential communication tools, financial records, and customer data can lead to downtime, lost productivity, and decreased profitability. For individuals, a compromised account can lead to financial losses, identity theft, and privacy concerns. The implications can be particularly severe for businesses relying heavily on online communication and data management.
Potential Losses by Victim Type
| Victim Type | Financial Losses | Emotional Distress | Reputational Damage |
|---|---|---|---|
| Individual | Loss of savings, fraudulent charges, identity theft | Anxiety, stress, loss of trust | Damage to personal reputation, difficulty in regaining trust |
| Small Business | Loss of revenue, lost customer data, disruption of operations | Stress, fear of losing clients, concern about business continuity | Damage to brand image, loss of customer trust, decreased sales |
| Large Corporation | Significant financial losses, legal costs, reputational damage | High-level stress, damage to executive confidence, fear of regulatory scrutiny | Loss of investor confidence, damage to corporate image, legal battles |
Protecting Against Scams
Falling victim to a scam like the one targeting G Suite and Twitter accounts with Bitcoin demands can be incredibly frustrating and costly. Understanding how these attacks work is crucial, but just as important is knowing how to safeguard your accounts and data from future attempts. Proactive measures are vital in preventing compromise and minimizing potential losses.Protecting yourself from scams requires a multi-layered approach.
It’s not enough to just be aware of the scams; you need to actively implement security measures and foster a culture of security within your organization or personal life. This involves reinforcing your online defenses, practicing safe habits, and being prepared to react if you believe your accounts have been compromised.
Strengthening G Suite Security
Robust G Suite security begins with implementing strong password policies and multi-factor authentication (MFA). Regularly updating passwords with unique, complex combinations and enabling MFA significantly reduces the risk of unauthorized access.
- Password Management: Utilize a password manager to generate and store strong, unique passwords for each account. Avoid reusing passwords across different platforms.
- Multi-Factor Authentication (MFA): Activating MFA adds an extra layer of security by requiring a second verification method, such as a code from your phone, in addition to your password. This significantly mitigates the impact of a compromised password.
- Regular Security Audits: Conduct periodic security assessments of your G Suite account to identify and address any potential vulnerabilities.
- Restrict Access: Implement granular access controls to limit who can access sensitive data and applications within your G Suite environment. Only grant necessary permissions.
Securing Twitter Accounts
Protecting your Twitter account from compromise follows similar principles as securing G Suite. A layered approach, combining strong passwords, MFA, and vigilance, is essential.
- Strong Passwords: Use strong, unique passwords for your Twitter account. Avoid using easily guessable passwords, and incorporate a mix of uppercase and lowercase letters, numbers, and symbols.
- Multi-Factor Authentication (MFA): Activating MFA on your Twitter account provides an extra layer of security, requiring a second verification step.
- Beware of Phishing Attempts: Be highly suspicious of any unsolicited messages or links that ask for your login credentials. Never click on links from unknown sources.
- Review Permissions: Regularly review the applications and websites that have access to your Twitter account. Revoke any suspicious or unwanted permissions.
Importance of Multi-Factor Authentication
Multi-factor authentication (MFA) is a cornerstone of modern security. It adds an extra layer of security, making it significantly harder for attackers to access your accounts even if they have your password.
“MFA significantly increases the difficulty for attackers to gain access, even if they have obtained your password.”
Strong Passwords
Strong passwords are crucial for online security. A strong password is one that is difficult to guess and that is unique to each account.
“Use a mix of uppercase and lowercase letters, numbers, and symbols in your passwords. Avoid using easily guessable words or phrases.”
Security Awareness Training
Security awareness training equips employees and individuals with the knowledge and skills needed to recognize and avoid security threats. Training should cover topics like phishing, malware, and social engineering tactics.
- Phishing Recognition: Training should focus on how to identify phishing emails, messages, and websites that try to trick you into revealing personal information.
- Malware Avoidance: Training should cover how to recognize and avoid malicious software, including viruses, spyware, and ransomware.
- Social Engineering Prevention: Training should address how social engineering tactics work and how to resist pressure to provide sensitive information.
Account Compromise Response Plan, Google g suite twitter account hacked bitcoin scam
Having a plan in place for responding to suspected account compromise is essential. A structured approach can help limit the damage and ensure swift recovery.
| Step | Action |
|---|---|
| 1 | Immediately change your password. |
| 2 | Report the compromised account to the respective platform (e.g., Google, Twitter). |
| 3 | Monitor your accounts for any unusual activity. |
| 4 | Contact your bank or financial institution if you suspect unauthorized transactions. |
| 5 | Review your recent online activity. |
Case Studies

Unfortunately, real-world examples of Google Workspace and Twitter account hacks related to Bitcoin scams are often kept confidential for security and legal reasons. Publicly available information is limited, making it difficult to compile comprehensive case studies. However, some general patterns and lessons learned can be extrapolated from reported incidents.The lack of widespread, publicly available case studies highlights the secretive nature of these sophisticated scams.
Victims often experience significant financial losses and reputational damage, which discourages them from sharing details. Furthermore, the technical complexities involved in these attacks make it challenging to fully document and analyze the incidents.
Real-World Examples and Patterns
This section illustrates common patterns and Artikels the potential impact of these scams. The limited data available suggests a common modus operandi: hackers gain unauthorized access to a victim’s accounts (Google Workspace or Twitter) and use the platform to spread phishing emails or messages that encourage victims to invest in fake cryptocurrency schemes or transfer funds to fraudulent addresses.
The perpetrators often leverage social engineering techniques to manipulate victims into believing the request is legitimate.
Victim Profiles and Tactics
Victims in these scenarios often exhibit a common profile: individuals or businesses who may not be fully aware of the potential risks associated with online security or those with limited experience in handling sensitive financial information. Scammers frequently exploit this lack of awareness. Their tactics often involve creating convincing phishing emails that appear to be legitimate communications from trusted sources, such as the targeted platform.
These emails or messages frequently include urgent requests for action, such as account verification or security updates, which can be highly effective in tricking unsuspecting individuals.
Law Enforcement Response and Outcomes
The limited availability of publicly reported cases makes it challenging to discuss the specific investigations and outcomes. However, in general, law enforcement agencies often face significant hurdles in prosecuting these types of cybercrimes. The perpetrators are often located in jurisdictions with weak or no extradition treaties, making prosecution difficult. Moreover, the technical complexities of the attacks and the decentralized nature of cryptocurrency transactions can further complicate investigations.
Lessons Learned and Prevention Strategies
The limited case study data underscores the importance of proactive security measures. Businesses and individuals should implement robust security protocols to protect their accounts. These protocols should include multi-factor authentication, strong passwords, regular account monitoring, and awareness training to recognize phishing attempts. Education is paramount in combating these scams. Users should be taught to recognize suspicious emails, messages, and requests.
They should also be aware of the potential risks associated with investing in cryptocurrency and should always verify the legitimacy of any investment opportunities.
Summary Table of Case Studies (Hypothetical)
| Case Study | Victim Type | Scam Tactics | Outcome | Lessons Learned |
|---|---|---|---|---|
| Case 1 | Small Business | Spoofed email claiming account suspension | Significant financial loss; account recovery partially successful | Implement multi-factor authentication; conduct regular security audits |
| Case 2 | Individual Investor | Fake cryptocurrency investment platform | Complete loss of investment funds | Verify legitimacy of investment opportunities; avoid suspicious links |
| Case 3 | Large Corporation | Phishing email impersonating executive | Transfer of funds to fraudulent account; significant reputational damage | Enhanced employee training on phishing awareness; strong internal controls |
Reporting and Prevention
Protecting yourself from scams like the Google Workspace/Twitter hack Bitcoin scam requires a multi-faceted approach. A crucial part of this strategy is knowing how to report suspicious activity and what resources are available for recovery. This section details the procedures for reporting compromised accounts and phishing attempts, emphasizing the importance of swift action to minimize damage.
Reporting Compromised Accounts
Prompt reporting of compromised accounts to the affected platforms is critical. This allows for swift action to secure the account and prevent further financial loss or damage to your reputation. Ignoring the issue often exacerbates the problem.
- Google Workspace: Google provides a dedicated support system for resolving account issues. Visit the Google Workspace help center for detailed instructions on reporting compromised accounts. They offer various channels for assistance, including email, phone support, and online chat. Specific instructions vary depending on the nature of the compromise, but reporting is usually a first step towards recovery.
Expect to provide supporting documentation.
- Twitter: Twitter’s support channels are designed to address account security issues. Access their help center to find guidance on reporting a hacked account. You’ll likely need to provide proof of identity and information about the compromise. Similar to Google, the specifics of reporting depend on the details of the situation.
Resources for Account Recovery
In addition to reporting to the platforms, victims can utilize resources to aid in account recovery and financial restitution.
- Account Recovery Tools: Each platform has built-in account recovery options. Utilize these resources to attempt regaining access. Often, this requires verification through alternate email addresses or phone numbers associated with the account.
- Financial Institutions: Contact your financial institution immediately if you suspect fraudulent transactions associated with your account. Report any unauthorized activity promptly to prevent further losses.
- Cybersecurity Professionals: Consult with cybersecurity professionals for advanced recovery strategies if the initial attempts are unsuccessful. They can assist with complex recovery procedures or identify any remaining vulnerabilities in your systems.
Importance of Reporting to Authorities
Reporting such scams to relevant authorities is essential for wider impact.
- Law Enforcement: Reporting to law enforcement agencies is critical in combating cybercrime. By documenting the incident, authorities can gather evidence to track down the perpetrators and prevent future attacks. This includes filing a police report to support your claim.
- Regulatory Bodies: Contact relevant regulatory bodies, depending on the jurisdiction and the nature of the scam, to report the incident. This helps build a comprehensive record of the attack.
Reporting Phishing Attempts and Malicious Websites
Reporting phishing attempts and malicious websites helps protect others from similar attacks.
- Reporting Phishing Emails/Messages: Report suspicious emails, texts, or other messages to the appropriate platform. Provide details of the message and any links included. Use the reporting mechanisms offered by your email provider or messaging platform.
- Reporting Malicious Websites: Report malicious websites to the website hosting provider or relevant cybersecurity authorities. Provide details about the website and its harmful content. Platforms like Google, and others, often have dedicated reporting tools.
Reporting Procedures
A table summarizing the reporting procedures for Google Workspace and Twitter.
| Platform | Reporting Procedure | Contact Information |
|---|---|---|
| Google Workspace | Visit the Google Workspace help center for instructions. | Google Workspace support channels (email, phone, chat). |
| Access the Twitter help center for guidance. | Twitter support channels (help center). |
Last Recap: Google G Suite Twitter Account Hacked Bitcoin Scam
In conclusion, the Google G Suite Twitter account hacked bitcoin scam underscores the critical need for heightened security awareness and proactive measures. By understanding the attack vectors, the impact of the scam, and the preventative steps, individuals and businesses can significantly reduce their vulnerability to these sophisticated cybercrimes. This comprehensive guide equips readers with the knowledge and tools to safeguard their accounts and finances from falling prey to these deceptive schemes.




