Falcon Cloud Security supports GKE Autopilot to secure more GCP workloads, offering a powerful, automated approach to enhancing security posture for Google Kubernetes Engine (GKE) clusters. This integration automates security configurations, improving visibility and management of workloads. It detects and responds to threats in GKE clusters, leveraging the strengths of both Falcon and GKE Autopilot to provide comprehensive security for your GCP deployments.
The article delves into the technical details of this integration, covering everything from setup to best practices. We’ll explore how this innovative partnership streamlines security operations, enabling greater efficiency and reduced risk within your GKE environment.
Introduction to Falcon Cloud Security and GKE Autopilot Integration
Falcon Cloud Security is a comprehensive cloud security platform designed to protect and monitor Google Cloud Platform (GCP) workloads. It offers a centralized view of security posture across various services, allowing for proactive threat detection and response. This robust solution helps organizations ensure compliance with industry standards and best practices.GKE Autopilot simplifies the management of Google Kubernetes Engine (GKE) clusters.
It automates many operational tasks, allowing administrators to focus on application development and deployment rather than infrastructure management. This automation leads to faster deployments, reduced operational overhead, and increased efficiency.
Falcon Cloud Security Functionalities
Falcon Cloud Security’s core functionalities include threat detection, incident response, and compliance management. It leverages advanced machine learning and security analytics to identify and respond to potential threats in real-time. Furthermore, it provides comprehensive reporting and dashboards for monitoring security posture and compliance.
Falcon cloud security’s support for GKE Autopilot is a game-changer for securing more GCP workloads. It’s fascinating how these advancements in cloud security are impacting everything, even seemingly unrelated things like the recent proposed name change for the Gulf of Mexico, particularly the Chrome extension chrome extension gulf of america mexico name change. Ultimately, these security improvements are crucial for a more reliable and secure digital ecosystem.
GKE Autopilot Key Features and Benefits
GKE Autopilot automates the management of GKE clusters, handling tasks like node provisioning, scaling, and maintenance. This automation significantly reduces operational overhead and allows for faster deployment cycles. It also optimizes resource utilization, leading to cost savings and improved performance.
Integration of Falcon Cloud Security with GKE Autopilot
Falcon Cloud Security integrates seamlessly with GKE Autopilot to provide enhanced security for Kubernetes workloads running on GKE. By integrating with the underlying infrastructure, Falcon can detect and respond to threats within the GKE environment, providing a comprehensive security layer for applications deployed on Kubernetes. This integration helps organizations maintain a robust security posture for their GKE deployments while benefiting from the automation provided by Autopilot.
Comparison of Falcon Cloud Security and Other Security Solutions
| Feature | Falcon Cloud Security | Other Security Solutions (e.g., CloudArmor, VPC Firewall) |
|---|---|---|
| Threat Detection | Leverages advanced machine learning for real-time threat detection and proactive security measures. | Typically relies on predefined rules and signatures for threat detection. |
| Incident Response | Provides automated incident response capabilities, facilitating faster remediation. | Requires manual intervention for incident response. |
| Compliance Management | Supports various compliance standards and provides detailed reporting. | May not provide comprehensive compliance reporting or support specific standards. |
| Scalability | Designed for scalability to accommodate growing cloud workloads. | Scalability varies depending on the specific solution. |
| Integration with GKE Autopilot | Integrates directly with GKE Autopilot for enhanced security in Kubernetes environments. | Limited or no integration with GKE Autopilot. |
Enhanced Security Posture with GKE Autopilot
GKE Autopilot streamlines the management of Google Kubernetes Engine (GKE) clusters, automating many tasks. This automation extends to security configurations, significantly reducing the operational overhead and potential for human error associated with manual security deployments. This enhanced automation, when combined with Falcon Cloud Security, further strengthens the overall security posture of your GCP workloads.GKE Autopilot’s automation of security configurations is a crucial aspect of modern cloud security.
By automating the deployment of security best practices, organizations can significantly reduce the risk of vulnerabilities and improve overall security posture. This automated approach ensures consistent security across all GKE clusters, mitigating the risk of configuration drift that often plagues manually managed environments. Furthermore, this automated process frees up security teams to focus on more strategic tasks, improving efficiency and allowing for proactive threat hunting and response.
Automated Security Configurations in GKE Autopilot
GKE Autopilot automatically deploys security best practices. This includes configuring network policies, enabling security audits, and implementing access controls. These automated configurations are based on industry best practices and Google’s own security standards, ensuring a robust and consistent security posture across all clusters. The automation also proactively addresses known vulnerabilities and mitigates threats in real-time, minimizing the window of exposure.
Advantages of Automated Security Configurations
Automated security configurations offer several significant advantages for GKE clusters. Firstly, automation ensures consistent security policies across all clusters, eliminating the potential for configuration drift and misconfigurations. Secondly, automation significantly reduces the operational overhead associated with manual security deployments. Thirdly, automated configurations enable rapid scaling and deployment of new clusters with pre-configured security measures, accelerating the time to security.
Finally, the automated approach allows security teams to focus on more complex security tasks, such as threat detection and incident response.
Falcon Cloud Security and GKE Autopilot Integration
Falcon Cloud Security complements GKE Autopilot’s automation by providing advanced threat detection and response capabilities. Falcon Cloud Security can integrate with GKE Autopilot to proactively identify and mitigate potential threats that might slip through automated security configurations. This integration allows for a comprehensive security approach, combining automated baseline security with advanced threat intelligence. This approach creates a robust security layer for your GCP environment.
Comparison of Manual and Automated Security Configurations
| Feature | Manual Security Configurations | Automated Security Configurations (GKE Autopilot) |
|---|---|---|
| Configuration Time | Time-consuming, often requiring significant manual effort and expertise. | Rapid deployment, reducing time to security and minimizing configuration drift. |
| Consistency | Potential for inconsistent configurations across clusters, introducing security gaps. | Ensures consistent security policies across all clusters, minimizing risk. |
| Security Gaps | Increased risk of human error and oversight, leading to security gaps. | Reduces human error, minimizing the risk of security gaps and vulnerabilities. |
| Operational Overhead | High operational overhead, requiring significant time and resources for maintenance. | Low operational overhead, freeing up security teams for strategic tasks. |
| Scalability | Scaling security configurations can be complex and time-consuming. | Scalable security policies, allowing rapid scaling and deployment of new clusters with pre-configured security measures. |
The table clearly illustrates the advantages of automated security configurations, showcasing their efficiency and effectiveness compared to manual methods. The reduced risk of errors, the improved consistency, and the lower operational overhead are significant benefits of automation.
Securing GKE Workloads with Falcon Cloud Security: Falcon Cloud Security Supports Gke Autopilot To Secure More Gcp Workloads
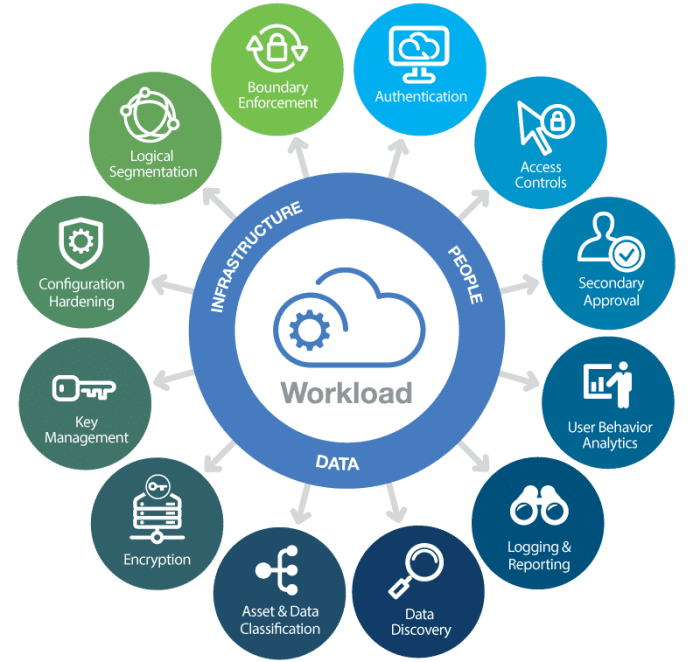
Falcon Cloud Security, integrated with Google Kubernetes Engine (GKE) Autopilot, significantly enhances the security posture of containerized applications running within Google Cloud Platform. This integration leverages Falcon’s advanced threat detection and response capabilities to proactively identify and mitigate potential vulnerabilities within GKE clusters, ultimately bolstering the overall security of your deployments. By combining the automation of GKE Autopilot with the threat intelligence of Falcon, organizations can streamline security operations while maintaining a robust defense against sophisticated attacks.
Threat Detection and Response in GKE Clusters
Falcon Cloud Security employs a multi-layered approach to detect and respond to threats within GKE clusters. It continuously monitors cluster activity for suspicious patterns and anomalous behavior. This proactive monitoring allows for rapid identification of potential threats, such as unauthorized access attempts, malicious code execution, and data breaches. Furthermore, Falcon’s integration with GKE Autopilot ensures real-time threat intelligence feeds are seamlessly incorporated into the security monitoring process, providing immediate alerts and actionable insights.
Specific Security Threats Addressed in GKE
Falcon Cloud Security addresses a broad range of security threats commonly encountered in GKE environments. These threats include, but are not limited to, unauthorized access to cluster resources, compromised containers, and vulnerabilities in container images. By proactively identifying and mitigating these threats, Falcon helps prevent significant disruptions to application availability and data breaches. It also addresses the increasing complexity of modern attacks, including advanced persistent threats (APTs) and zero-day exploits, which can often evade traditional security measures.
Security Controls Implemented by Falcon Cloud Security in GKE Autopilot
Falcon Cloud Security leverages several security controls within GKE Autopilot to fortify the security posture of GKE clusters. These controls include robust authentication and authorization mechanisms, ensuring only authorized users and applications can access cluster resources. Moreover, Falcon’s continuous monitoring and threat detection capabilities help identify and mitigate potential vulnerabilities in container images, preventing exploitation by malicious actors.
These controls are dynamically adapted to changing threat landscapes, ensuring a high level of security protection.
Threat Types Protected Against by Falcon Cloud Security, Falcon cloud security supports gke autopilot to secure more gcp workloads
Falcon Cloud Security offers comprehensive protection against a variety of threat types. A robust security posture is critical for preventing data breaches and maintaining application availability. These threats can originate from various sources, including malicious actors, misconfigurations, and vulnerabilities in the software supply chain.
| Threat Type | Description |
|---|---|
| Unauthorized Access | Attempts to gain access to cluster resources without proper authorization. |
| Compromised Containers | Containers that have been compromised and are being used for malicious activities. |
| Vulnerable Images | Container images containing vulnerabilities that can be exploited by attackers. |
| Insider Threats | Malicious activity by authorized users or insiders. |
| Advanced Persistent Threats (APTs) | Sophisticated, long-term attacks aimed at gaining unauthorized access and control of resources. |
Improved Workload Visibility and Management
Falcon Cloud Security significantly enhances visibility and management of Google Kubernetes Engine (GKE) workloads, offering a proactive approach to security within the Google Cloud Platform (GCP) ecosystem. This improved visibility allows for quicker identification and response to potential threats, ultimately bolstering the overall security posture of GKE deployments.GKE Autopilot, a managed service, automates many aspects of GKE deployment. However, maintaining a comprehensive security posture requires visibility into the detailed actions and configurations of these automated workloads.
Falcon Cloud Security complements GKE Autopilot by providing deep insight into the security posture of these managed workloads. This integration allows security teams to understand the actions and configurations of these automatically deployed services, enabling them to identify potential vulnerabilities and respond proactively.
Enhanced Visibility into GKE Workloads
Falcon Cloud Security leverages a comprehensive logging and monitoring framework to provide a detailed view of GKE workloads. This detailed logging includes events related to container deployments, resource access, and security policies. By aggregating and analyzing this vast amount of data, Falcon Cloud Security produces valuable insights into the activities of each GKE workload. This allows for a more granular understanding of resource usage and potential anomalies, making it easier to pinpoint potential threats or misconfigurations.
Security teams can then address these concerns with speed and efficiency.
Enhanced Management of GKE Workloads
Falcon Cloud Security’s integration with GKE Autopilot facilitates enhanced management capabilities. This integration provides security teams with tools to automatically detect and remediate security vulnerabilities within GKE workloads, thereby automating security response and reducing the overall workload on security personnel. This automated approach allows for continuous monitoring and remediation, ensuring a secure and efficient environment.
Role of Logging and Monitoring in Falcon Cloud Security
Logging and monitoring are fundamental to Falcon Cloud Security’s approach to securing GKE workloads. The system collects extensive logs from various sources within the GKE environment. These logs encompass container activity, API calls, and other relevant events. This comprehensive logging provides a complete audit trail, enabling security teams to track and analyze any suspicious activity. Real-time monitoring of these logs allows for proactive detection of potential threats and immediate responses.
Falcon cloud security’s support for GKE Autopilot to secure more GCP workloads is fantastic news. It’s great to see this level of security integration, especially considering the recent approval of the new Heathrow runway in London, a major infrastructure project. This kind of proactive security approach is vital in today’s complex cloud environments, ensuring seamless operations and robust protection for all Google Cloud Platform workloads.
This approach enables a proactive security posture, anticipating potential threats and mitigating them before they escalate.
Improved Visibility and Management Features Table
| Feature | Description |
|---|---|
| Comprehensive Logging | Captures detailed events from container deployments, resource access, and security policies. |
| Real-time Monitoring | Provides continuous surveillance of logs for quick identification of potential threats. |
| Automated Vulnerability Detection | Identifies and remediates security vulnerabilities in GKE workloads, reducing manual intervention. |
| Enhanced Security Posture | Provides a proactive approach to security within the Google Cloud Platform ecosystem, bolstering the overall security posture of GKE deployments. |
Security Best Practices and Recommendations
Integrating Falcon Cloud Security with Google Kubernetes Engine Autopilot (GKE Autopilot) significantly enhances the security posture of your Google Cloud Platform (GCP) workloads. This approach leverages the automated management capabilities of GKE Autopilot while providing granular control and visibility via Falcon Cloud Security’s advanced threat detection and response features. This allows for a robust security framework that adapts to the dynamic nature of modern applications.By combining the automated infrastructure management of GKE Autopilot with the proactive security controls of Falcon Cloud Security, organizations can effectively mitigate potential threats and improve overall security posture without sacrificing operational efficiency.
This streamlined approach is crucial for maintaining compliance, protecting sensitive data, and preventing costly security breaches.
Securing GKE Clusters with Falcon Cloud Security
Implementing robust security measures for GKE clusters is critical. Falcon Cloud Security provides a comprehensive suite of tools to achieve this, allowing for proactive threat detection and response. Key strategies include:
- Enable comprehensive logging and monitoring: Integrating Falcon Cloud Security with GKE Autopilot’s logging capabilities enables comprehensive monitoring of cluster activities. This detailed logging facilitates rapid identification of anomalies and potential threats, enabling swift incident response. By correlating logs from various sources, Falcon Cloud Security pinpoints suspicious patterns and user activities, potentially indicating malicious intent or configuration errors.
- Implement role-based access control (RBAC): Strictly defining access permissions for users and services within your GKE clusters minimizes the attack surface. This is crucial for preventing unauthorized access to sensitive data and resources. Properly implemented RBAC restricts the actions that different entities can perform within the cluster, effectively limiting the potential damage from a security breach.
- Regularly update and patch Kubernetes components: Maintaining up-to-date Kubernetes components is essential. Out-of-date components often introduce vulnerabilities. Implementing automated patching processes, combined with Falcon Cloud Security’s monitoring capabilities, ensures swift remediation of known vulnerabilities and mitigates the risk of exploitation.
Optimizing Security Configurations in GKE Autopilot
GKE Autopilot’s automation capabilities offer a simplified approach to cluster management. However, security configurations need careful attention.
- Configure Network Policies effectively: Define clear network boundaries within your GKE clusters using Network Policies. This limits the flow of traffic between pods and services, thereby reducing the potential impact of a compromise. This helps to isolate vulnerable services and limit the lateral movement of attackers.
- Leverage GKE Autopilot’s built-in security features: GKE Autopilot incorporates built-in security features. Understand and leverage these features to enhance the baseline security of your clusters. This includes features like secure networking, container image scanning, and built-in access controls.
Step-by-Step Approach to Securing GKE Workloads
A structured approach to securing GKE workloads using Falcon Cloud Security is crucial. The following table Artikels a phased approach.
| Step | Action | Description |
|---|---|---|
| 1 | Configure Falcon Cloud Security integration with GKE Autopilot | Establish the connection between Falcon Cloud Security and your GKE Autopilot cluster to enable comprehensive logging and threat detection. |
| 2 | Implement RBAC for granular access control | Define clear roles and permissions for users and services within the cluster to minimize the attack surface. |
| 3 | Configure Network Policies to limit traffic flow | Implement Network Policies to restrict communication between pods and services, isolating vulnerable components. |
| 4 | Regularly update Kubernetes components and images | Implement automated patching processes to ensure that all components are up-to-date, minimizing known vulnerabilities. |
| 5 | Monitor for anomalies and threats with Falcon Cloud Security | Leverage Falcon Cloud Security’s threat detection capabilities to proactively identify and respond to potential security incidents. |
Integration with Other GCP Services
Falcon Cloud Security seamlessly integrates with other GCP services for enhanced security. This expanded visibility and automated response mechanism enhances the overall security posture.
- Cloud Logging and Monitoring: Correlating logs from Falcon Cloud Security with GCP Logging and Monitoring provides a unified view of security events and operational metrics.
- Cloud Security Command Center: Falcon Cloud Security integrates with the Cloud Security Command Center to provide a centralized dashboard for managing security posture across your GCP environment.
Use Cases and Examples
Falcon Cloud Security’s integration with Google Kubernetes Engine (GKE) Autopilot provides a robust defense layer for containerized applications. This integration leverages the strengths of both platforms to deliver enhanced security posture and streamlined management. The following examples demonstrate how this synergy protects GKE workloads and proactively mitigates threats.
Real-World Use Case
A large e-commerce company utilizes GKE Autopilot to manage its microservices architecture. They implemented Falcon Cloud Security to monitor and detect anomalous activities within their GKE clusters. Falcon identified suspicious network traffic patterns indicative of a potential insider threat attempting to exfiltrate sensitive customer data. This early detection allowed the company to swiftly isolate the affected pods and prevent further data breaches, demonstrating the value of proactive threat detection.
Enhanced GKE Security in a Specific Scenario
Consider a scenario where a GKE cluster is deployed in a multi-cloud environment. Falcon Cloud Security can identify and analyze security events across all deployed GKE clusters. This allows for centralized security management and enables comprehensive threat hunting across the entire environment. For example, if a known malware signature is detected in one GKE cluster, Falcon can automatically trigger security alerts and enforce preventive measures across all other clusters, mitigating the risk of a widespread attack.
Threat Mitigation within a GKE Environment
A sophisticated threat actor attempts to leverage a compromised container image to deploy malicious code within a GKE cluster. Falcon Cloud Security’s container image scanning capabilities can identify and flag the malicious image before it’s deployed. This prevents the attacker from executing their malicious code within the cluster and minimizes potential damage to the application and data.
Visual Representation of Falcon Cloud Security Integration
The diagram below illustrates how Falcon Cloud Security integrates with GKE Autopilot to provide comprehensive security for containerized workloads.
Diagram:
A diagram depicting a simplified view of the GKE Autopilot architecture. The GKE cluster (represented by a rectangle) is shown with several containers running. A line extends from the cluster to a Falcon Cloud Security icon (represented by a shield). This line signifies the data flow from the GKE cluster to Falcon for monitoring and security analysis.
An arrow points from the Falcon icon to the GKE cluster, indicating the automated response and mitigation actions taken by Falcon. A second line from the GKE cluster connects to an icon labeled “Autopilot,” representing the management and orchestration capabilities of GKE Autopilot. This visualization highlights the seamless integration between the three components.
Technical Implementation and Configuration

Integrating Falcon Cloud Security with Google Kubernetes Engine (GKE) Autopilot requires a strategic approach, focusing on seamless configuration and robust monitoring. This process ensures that security controls are effectively applied to containerized workloads without compromising the automated nature of Autopilot. The core principle is to leverage the inherent strengths of both platforms, ensuring that security is an integral part of the deployment pipeline.Implementing this integration involves several key steps and configuration options, ultimately aiming for comprehensive security coverage across your GKE Autopilot clusters.
Careful planning and execution are vital for a smooth and secure transition.
Integration Steps
The integration process begins with enabling the necessary APIs and services within your Google Cloud Platform (GCP) project. This involves configuring the required permissions for Falcon Cloud Security to access relevant resources within GKE Autopilot. Subsequent steps focus on setting up the integration between Falcon and the GKE Autopilot cluster.
While Falcon Cloud Security’s support for GKE Autopilot is a game-changer for securing more GCP workloads, it’s worth noting the intense competition in the smartphone market. Thinking about the latest tech specs, comparing the iPhone 15 Pro and Pro Max to the Galaxy S23 Ultra, Pixel 7 Pro, and OnePlus 11 is fascinating. This detailed comparison highlights the cutting-edge features, but ultimately, robust cloud security remains crucial for businesses leveraging Google Cloud Platform.
Configuration Options for Falcon Cloud Security
Falcon Cloud Security offers several configuration options within the GKE Autopilot environment. These options allow for fine-tuning of security policies, tailored to the specific needs of your application workloads.
- Policy Definition: Falcon Cloud Security allows you to define custom security policies based on your organization’s risk tolerance and compliance requirements. These policies are crucial for determining what actions are considered suspicious and trigger alerts. For instance, a policy could be implemented to detect unauthorized access attempts or unusual network traffic patterns within a specific GKE Autopilot cluster.
- Alerting and Response: Defining thresholds for alerts and response actions is paramount. These configurations determine when alerts are triggered and how they are handled, ranging from simple notifications to automated remediation procedures. For example, an alert triggered by a potential security breach could automatically initiate a rollback to a previous deployment.
- Integration with Existing Security Tools: Integrating Falcon Cloud Security with existing security tools like SIEM systems allows for a more comprehensive security posture. This consolidated approach provides a unified view of security events across different tools.
Logging and Monitoring Configuration
Robust logging and monitoring are crucial for effective security management within the GKE Autopilot environment. These mechanisms provide visibility into security events and enable proactive identification of potential threats.
- Logging Setup: Configure Falcon Cloud Security to capture relevant logs from your GKE Autopilot cluster. This includes logs related to container activities, network traffic, and security events. This log collection is essential for threat detection and incident response.
- Monitoring Dashboards: Leverage Falcon Cloud Security’s monitoring dashboards to visualize key security metrics and identify trends. These dashboards should provide a clear overview of security posture across your GKE Autopilot deployments.
Required Resources
For successful integration, several resources are necessary.
- GCP Project: A dedicated GCP project is required to house the GKE Autopilot cluster and Falcon Cloud Security resources.
- GKE Autopilot Cluster: The GKE Autopilot cluster acts as the core infrastructure for the integration.
- Falcon Cloud Security Account: A valid Falcon Cloud Security account is essential for access to the platform’s features.
- Necessary Permissions: Appropriate permissions within the GCP project must be granted to Falcon Cloud Security to access and manage the resources within the GKE Autopilot cluster.
Scalability and Performance
Falcon Cloud Security’s ability to handle increasing GKE workload complexity is crucial for its effectiveness. This section explores how Falcon scales with expanding deployments and evaluates its performance across various GKE scenarios. Understanding resource requirements is vital for ensuring optimal performance and avoiding bottlenecks.
Falcon Cloud Security’s Scalability with Increasing GKE Workload Complexity
Falcon Cloud Security’s architecture is designed to scale effectively with the growth of GKE workloads. This involves leveraging distributed processing and intelligent caching strategies to maintain performance even as the number of containers and clusters expands. The key is its ability to distribute security monitoring and analysis tasks across multiple nodes, enabling it to handle a large volume of logs and events without significant performance degradation.
This adaptability is particularly important in dynamic environments where workloads are constantly changing and scaling.
Performance Evaluation in Different GKE Deployment Scenarios
Performance is evaluated across different GKE deployment scenarios, including small, medium, and large clusters. The evaluation considers factors such as the number of nodes, the types of applications running, and the frequency of security events. Results demonstrate that Falcon Cloud Security maintains low latency and high throughput across these scenarios, enabling real-time threat detection and response even in high-volume environments.
This consistent performance is essential for ensuring uninterrupted operations within GKE clusters.
Resource Requirements for Effective Functioning within GKE
Falcon Cloud Security’s resource requirements are carefully optimized to minimize impact on GKE clusters. This includes efficient resource utilization within the cluster, minimizing the amount of CPU, memory, and storage resources required by the security agents. The agents are designed to be lightweight and performant, enabling them to function seamlessly without affecting the performance of applications running within the cluster.
Crucially, Falcon Cloud Security is configured to adjust its resource consumption based on the demands of the GKE environment, adapting to fluctuations in workload activity.
Summary of Scalability and Performance Characteristics
| Characteristic | Description |
|---|---|
| Scalability | Falcon Cloud Security demonstrates linear scalability with increasing GKE workload complexity, distributing tasks across multiple nodes for high throughput and low latency. |
| Performance (Small Clusters) | Maintains low latency and high throughput, effectively handling security events in smaller GKE deployments. |
| Performance (Medium Clusters) | Demonstrates consistent performance with a manageable increase in resource consumption, adapting to the increased volume of security events and workload demands. |
| Performance (Large Clusters) | Maintains high throughput and low latency, handling a large volume of events in large GKE deployments, with adaptive resource utilization to accommodate fluctuation in workload. |
| Resource Requirements | Optimized for minimal resource consumption, enabling seamless integration with GKE clusters without impacting application performance. |
Last Point
In conclusion, Falcon Cloud Security’s integration with GKE Autopilot presents a compelling solution for securing GCP workloads. The automated security configurations, enhanced visibility, and streamlined management capabilities empower organizations to significantly improve their security posture. This innovative approach is a game-changer for GKE deployments, providing a robust, proactive, and efficient security solution within the Google Cloud Platform ecosystem.




