CrowdStrike and industry partners release open cybersecurity schema framework, a groundbreaking initiative aiming to reshape how organizations approach cybersecurity. This framework promises a standardized, interoperable approach to data exchange, significantly enhancing threat detection, incident response, and overall security posture across the industry. The open nature of the schema facilitates collaboration and accelerates the development of innovative security solutions.
This detailed exploration delves into the framework’s core principles, technical specifications, and potential impact on various sectors.
The framework’s open structure fosters collaboration among security vendors, allowing them to share threat intelligence and data in a standardized format. This interoperability will undoubtedly lead to faster threat detection and response times. The framework’s modular design also allows for flexibility, allowing organizations to tailor the framework to their specific needs. We will delve into the technical architecture, highlighting the data formats, security considerations, and potential vulnerabilities.
Overview of the Framework
The CrowdStrike and industry partner initiative to create an open cybersecurity schema framework represents a significant step forward in the fight against increasingly sophisticated cyber threats. This collaborative effort aims to standardize data exchange and improve threat intelligence sharing, ultimately bolstering the collective security posture of organizations worldwide. This framework promises to enhance interoperability and facilitate the creation of more robust and effective security solutions.
Key Objectives and Intended Use Cases
The primary objectives of this open schema framework are to foster standardization in cybersecurity data formats and improve the efficiency of information sharing among security tools and platforms. This means that various security systems, regardless of vendor, can seamlessly communicate and exchange data, enriching the overall security picture. The framework’s intended use cases include automated threat detection, improved incident response, and proactive security posture assessments.
This facilitates faster identification of potential vulnerabilities and quicker response to attacks.
Significance of Open Standards in Cybersecurity
Open standards in cybersecurity are crucial for driving interoperability and collaboration among various security tools and systems. By establishing common formats for data exchange, organizations can avoid vendor lock-in and build more flexible and adaptable security infrastructures. This allows for a wider range of solutions to be integrated, ultimately leading to a more robust and comprehensive approach to cybersecurity.
The open nature of the framework promotes competition and innovation, ensuring that the cybersecurity landscape adapts to the ever-evolving threat environment.
Potential Impact on the Cybersecurity Industry
The adoption of this open cybersecurity schema framework will likely have a profound impact on the cybersecurity industry. Increased interoperability between security systems will lead to more effective threat detection and faster response times. This will benefit both large enterprises and smaller organizations, leveling the playing field in terms of cybersecurity capabilities. Furthermore, the framework’s open nature will encourage the development of innovative security solutions and tools, leading to a more dynamic and resilient cybersecurity ecosystem.
The framework will contribute to a more unified and collaborative approach to cybersecurity, creating a collective defense against cyber threats.
Key Features of the Framework
| Feature | Description | Benefits | Example Use Case |
|---|---|---|---|
| Standardized Data Formats | Defines common formats for representing cybersecurity data, such as threat intelligence, vulnerability information, and security events. | Facilitates seamless data exchange between various security tools and platforms. | Integrating threat intelligence from multiple sources into a single security information and event management (SIEM) platform. |
| Extensible Schema | Allows for the addition of new data elements and attributes as needed, ensuring the framework remains relevant in the face of evolving threats. | Ensures the framework’s long-term viability and adaptability to new threats. | Adding metadata about malicious actors to enhance threat profiling and analysis. |
| Interoperable APIs | Provides standardized APIs for data exchange, allowing various security tools to interact seamlessly. | Reduces integration complexity and enhances automation capabilities. | Automatically correlating security events from firewalls, intrusion detection systems, and endpoint security solutions. |
| Community-Driven Development | Encourages participation from the wider cybersecurity community, ensuring the framework remains relevant and adaptable. | Promotes innovation and collaboration among security professionals and researchers. | Creating new threat detection rules and contributing to the shared knowledge base. |
Technical Specifications
This framework’s technical specifications provide a deep dive into its architecture, data formats, underlying technologies, and security considerations. Understanding these details is crucial for implementing and utilizing the schema effectively, while also ensuring its robustness against potential threats. A strong foundation in these technical aspects is vital for any organization looking to leverage this open schema for improved cybersecurity.
Technical Architecture and Implementation, Crowdstrike and industry partners release open cybersecurity schema framework
The framework employs a microservices architecture, facilitating modularity and scalability. Individual services are responsible for specific aspects of data processing, analysis, and reporting. This decentralized approach allows for independent development and deployment of components, promoting flexibility and adaptability. Communication between services relies on a standardized messaging protocol, enabling seamless data exchange. The architecture is designed with security as a core principle, employing robust authentication and authorization mechanisms at each interaction point.
Data Formats and Structures
The schema utilizes JSON (JavaScript Object Notation) as the primary data format. This choice provides a lightweight and human-readable format for data exchange. The JSON structure is meticulously designed to accommodate diverse cybersecurity events, with specific fields for event type, source, timestamp, severity, and affected assets. This structured format facilitates efficient data processing and analysis by various security tools.
Nested JSON objects can be used to store detailed information about specific events, allowing for granular analysis.
Underlying Technologies and Standards
The framework leverages widely adopted industry standards for communication and data exchange. These include RESTful APIs for service interactions, enabling seamless integration with existing security tools and platforms. Open standards are fundamental to the framework’s interoperability, ensuring smooth integration with various security information and event management (SIEM) systems. This reliance on open standards facilitates integration with a wide range of security solutions.
For example, using industry-standard logging formats enables easy integration with existing SIEM systems.
Security Considerations and Potential Vulnerabilities
Security is paramount in the framework’s design. However, potential vulnerabilities are addressed through a layered security approach. Robust input validation prevents malicious data from corrupting the system. Regular security audits and penetration testing are essential for identifying and mitigating potential vulnerabilities before deployment. Security measures are also incorporated at the data storage level, including encryption and access controls.
For example, using HTTPS for communication protects data transmitted between services. Regular updates to address any newly discovered vulnerabilities are crucial.
Data Flow and Interaction
This table illustrates the data flow and interaction between key components of the framework.
| Component A | Component B | Action | Data Format |
|---|---|---|---|
| Event Collector | Event Processor | Sends event data | JSON |
| Event Processor | Threat Intelligence Service | Queries threat intelligence | Structured Query Language (SQL) |
| Threat Intelligence Service | Security Analyst Dashboard | Provides threat context | JSON |
| Security Analyst Dashboard | Security Operations Center (SOC) | Displays alerts | JSON with alert metadata |
Industry Adoption and Impact: Crowdstrike And Industry Partners Release Open Cybersecurity Schema Framework
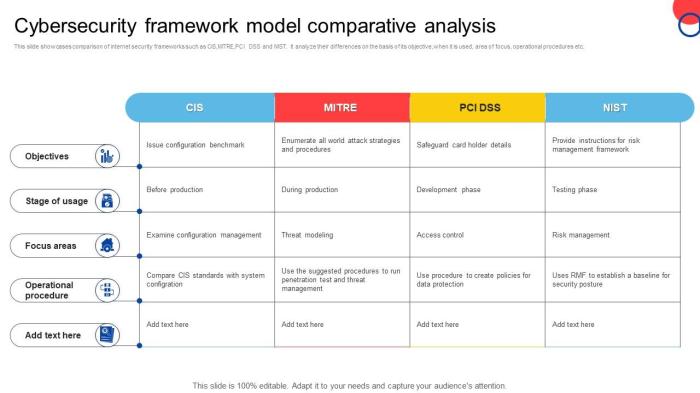
This open cybersecurity schema framework promises to revolutionize how organizations approach and manage cybersecurity. Its potential for widespread adoption across diverse industries is significant, offering a common language and standardized approach to data security. This standardization will undoubtedly streamline the process of vulnerability identification, incident response, and overall security posture improvement.The framework’s comprehensive nature and adaptability make it a compelling alternative to existing fragmented solutions.
It’s designed to address specific needs while aligning with broader industry best practices. This unified approach should lead to more effective security measures, minimizing vulnerabilities and reducing the overall risk profile.
Potential for Widespread Adoption
The framework’s modular design and adaptability to various industries and organizational structures make it attractive for a wide range of businesses. Its flexibility allows tailoring to specific security needs, avoiding unnecessary complexities and costs for implementing a one-size-fits-all solution. By standardizing data exchange and information sharing, the framework can facilitate quicker incident response and enhance collaboration among organizations.
This will be crucial for improving the overall resilience of the cybersecurity ecosystem.
Comparison with Existing Standards
The framework distinguishes itself by offering a holistic approach to cybersecurity, going beyond traditional standards like NIST Cybersecurity Framework or ISO 27001. It integrates various best practices, consolidating them into a cohesive schema. This unification addresses the fragmented nature of existing standards, reducing the complexity of implementing multiple frameworks. The framework’s open nature allows for ongoing evolution and adaptation, ensuring it remains relevant and effective in the face of evolving threats.
Potential Challenges to Adoption
Resistance to change and the need for significant organizational restructuring are among the potential challenges. Organizations accustomed to specific methodologies and tools may encounter hurdles adapting to a new framework. Ensuring proper training and support for employees to adopt new processes is crucial for a smooth transition. The cost of implementation, particularly for smaller organizations, is also a potential barrier.
Furthermore, ensuring interoperability between existing systems and the framework can be challenging. However, these challenges are surmountable with proactive planning and appropriate resources.
Examples of Framework Leverage
A healthcare organization could leverage the framework to standardize data encryption and access controls, significantly reducing the risk of patient data breaches. A financial institution could use it to improve the security of transaction processing, ensuring compliance with regulations and minimizing financial losses. Manufacturing companies can leverage it to secure industrial control systems (ICS), protecting critical infrastructure from cyberattacks.
By aligning security protocols with the framework, organizations can achieve consistent and comprehensive security.
Potential Impact on Different Industry Sectors
| Industry | Impact | Challenges | Opportunities |
|---|---|---|---|
| Healthcare | Improved patient data protection, enhanced regulatory compliance, reduced risk of breaches. | Integration with existing electronic health record (EHR) systems, staff training and adoption. | Reduced financial penalties, enhanced patient trust, improved operational efficiency. |
| Finance | Strengthened security of financial transactions, improved compliance with regulations, reduced fraud risk. | Complexity of integrating with legacy financial systems, potential cost of implementation. | Enhanced customer trust, minimized financial losses, increased operational resilience. |
| Manufacturing | Improved security of industrial control systems (ICS), reduced risk of supply chain disruptions, enhanced operational continuity. | Integration with existing industrial automation systems, ensuring operational safety during implementation. | Increased production efficiency, minimized downtime, enhanced operational security. |
| Retail | Enhanced security of customer data and payment systems, improved fraud detection and prevention, reduced risk of data breaches. | Integration with existing point-of-sale (POS) systems, adapting to e-commerce security standards. | Enhanced customer trust, increased sales, reduced losses from fraud. |
Security Implications and Best Practices

An open cybersecurity schema framework, while offering significant benefits, introduces new security considerations. Careful planning and implementation are crucial to mitigating potential risks and ensuring the framework enhances, rather than compromises, overall security posture. Understanding the potential pitfalls and adopting best practices is paramount for successful deployment and utilization.Open frameworks, by their nature, are exposed to a wider range of potential attacks and vulnerabilities.
This necessitates a proactive approach to security, focusing on secure design principles and rigorous testing throughout the framework’s lifecycle. A strong emphasis on secure data handling and transmission is also essential to maintain confidentiality, integrity, and availability.
Security Implications of Open Schema Frameworks
Open schema frameworks, by their very nature, require more vigilance in terms of security. The shared and public nature of the framework makes it susceptible to malicious actors who might exploit vulnerabilities to gain unauthorized access, modify data, or disrupt operations. Malicious actors might seek to inject or manipulate data within the schema, potentially leading to significant security breaches.
Furthermore, the wide adoption of the schema by diverse organizations with varying security protocols can introduce inconsistencies in security standards and practices. Understanding and addressing these risks are crucial for successful implementation.
CrowdStrike and industry partners just released an open cybersecurity schema framework, a move that could significantly improve industry-wide threat detection. This echoes recent developments in legal tech, like the tweet to legal filing pipeline working at record speed for Rudy Giuliani , highlighting the growing importance of streamlined data sharing in both cybersecurity and legal processes. Ultimately, this open framework could lead to better, more collaborative solutions for protecting sensitive information across the board.
Potential Risks and Mitigation Strategies
Several potential risks arise from the adoption of an open schema framework. These include vulnerabilities in the schema itself, which could be exploited by attackers to gain unauthorized access or manipulate data. Improper handling of sensitive data within the framework also poses a serious threat. Furthermore, misconfigurations and inadequate security controls within the implementing organizations can expose the entire framework to compromise.
Mitigation strategies include rigorous security audits, penetration testing, and vulnerability assessments throughout the development and implementation phases. Implementing robust access controls and encryption mechanisms is critical to protect sensitive data within the framework.
Best Practices for Implementing the Framework Securely
Implementing the framework securely requires adherence to a series of best practices. Security considerations should be integrated into the framework’s design and development phases, not as an afterthought.
- Secure Data Handling: Implement strong encryption for data at rest and in transit. Employ access control lists (ACLs) to restrict data access based on user roles and permissions. Regularly audit data access logs to detect suspicious activity.
- Secure Data Transmission: Use secure communication protocols, such as HTTPS, to protect data transmitted across networks. Implement robust authentication mechanisms to verify the identity of users and systems interacting with the framework.
- Vulnerability Management: Establish a process for identifying and addressing vulnerabilities in the framework. Regularly update the framework’s components to patch known vulnerabilities. Conduct periodic penetration testing to identify potential weaknesses.
- Incident Response: Develop and implement a comprehensive incident response plan to handle security breaches or incidents. Establish clear communication channels for reporting and responding to security incidents.
“Security should be a core principle, not an add-on, throughout the entire lifecycle of the open schema framework.”
Future Development and Evolution
The CrowdStrike and industry partner open cybersecurity schema framework represents a significant step towards standardized threat intelligence sharing and analysis. However, cybersecurity is a dynamic field, and the framework must evolve to remain effective in the face of emerging threats and technologies. This section explores potential future enhancements, research areas, and new use cases to ensure the framework’s long-term viability.
Potential Future Enhancements
The framework’s initial release provides a solid foundation. However, continuous improvement is crucial to address evolving threat landscapes and emerging technologies. Future enhancements should focus on broader adoption, increased interoperability, and improved scalability.
- Enhanced Data Modeling: The framework should incorporate more granular data points and richer contextual information to facilitate more sophisticated threat detection and response. This might include details on attack vectors, attack chains, and attacker motivations.
- Improved Scalability and Performance: The schema needs to be designed for massive datasets and real-time processing to effectively manage the volume of threat intelligence generated by a growing network of security tools and devices. This necessitates improvements in data ingestion and processing mechanisms. A good example is the need to accommodate the increasing volume of data from IoT devices, a key component of modern infrastructures.
- Integration with Emerging Technologies: The framework should accommodate emerging technologies such as artificial intelligence (AI) and machine learning (ML) for automated threat analysis and incident response. This includes incorporating data formats and standards used by AI/ML models for efficient analysis.
- Cross-Platform Compatibility: Enhancing compatibility across diverse security platforms and systems will accelerate adoption and streamline information exchange. This requires standardized data formats that can be easily translated and processed across various platforms.
Areas for Research and Development
The framework’s effectiveness depends on continuous research and development. Key areas for future exploration include:
- Automated Threat Intelligence Correlation: Developing algorithms to automatically correlate diverse data points from various sources to identify complex threats and potential attack patterns is critical. This allows security teams to quickly assess the severity and potential impact of threats.
- Predictive Threat Modeling: Leveraging machine learning to predict potential future attacks based on historical data and current threat intelligence. This can help organizations proactively implement preventative measures and strengthen their defenses.
- Zero-Trust Architecture Integration: The framework should be adaptable to the evolving zero-trust architecture paradigm. This involves identifying and verifying entities attempting to access resources, creating a granular approach to access control.
- Enhanced Threat Hunting Capabilities: Developing methods for automated threat hunting, enabling security analysts to identify and investigate threats that traditional systems might miss. This would enhance the framework’s ability to proactively identify and respond to evolving threats.
Potential New Use Cases
The framework has potential applications in various emerging technologies.
CrowdStrike and industry partners have released an open cybersecurity schema framework, which is a huge step forward. This framework is really important for standardizing security data, making it easier to share information and potentially identify threats faster. While we’re focused on cybersecurity, sometimes you just need a new USB-C cable for your OnePlus 2. If you’re looking for options, check out here are places you can buy USB-C cables for your OnePlus 2.
This open framework will hopefully lead to more collaborative efforts and ultimately better security for everyone.
- Industrial Control Systems (ICS): Integrating the framework with ICS systems will improve the detection and response capabilities for industrial cyberattacks, which are becoming increasingly sophisticated. This can be crucial in protecting critical infrastructure.
- Cloud Security: The framework can help standardize cloud security posture assessments and improve the sharing of threat intelligence across various cloud environments. This would provide more comprehensive and real-time threat visibility.
- Blockchain Technology: Using the framework to analyze and understand blockchain-related threats, potentially through integrating blockchain-specific data models and standards, could enhance security in this emerging technology.
Adapting to Evolving Cybersecurity Threats
The threat landscape is constantly changing. The framework must be adaptable to new attack vectors, vulnerabilities, and techniques. This requires constant monitoring and updates to maintain its effectiveness.
CrowdStrike and industry partners just dropped an open cybersecurity schema framework, a pretty big deal for improving industry-wide security. It’s exciting to see this kind of collaboration, and it’s a definite step forward. Meanwhile, if you’re in the market for a used Samsung Galaxy S8 Plus, knowing the pricing and release date for unlocked models is crucial. Check out this resource for details on samsung unlocked galaxy s8 plus pricing release date.
Ultimately, this new schema framework from CrowdStrike and partners should help to strengthen security measures across the board.
| Feature | Description | Impact | Timeline |
|---|---|---|---|
| Enhanced Data Modeling | Adding more granular data points and contextual information. | Improved threat detection and response. | Phase 2 (12-18 months) |
| Improved Scalability | Increased capacity to handle large datasets. | Enhanced real-time threat analysis. | Phase 2 (12-18 months) |
| AI/ML Integration | Using AI/ML for automated analysis and incident response. | Increased efficiency in threat detection. | Phase 3 (24-36 months) |
| Cross-Platform Compatibility | Enhanced interoperability across diverse security platforms. | Faster information exchange and improved threat visibility. | Phase 1 (6-12 months) |
Illustrative Scenarios
The CrowdStrike and industry partners’ open cybersecurity schema framework provides a standardized approach to cybersecurity incident response. This standardized framework can be applied to various scenarios, from detecting and preventing threats to streamlining incident response procedures and fostering collaboration among industry partners. These scenarios highlight the practical application of the framework and its impact on improving overall security posture.
Real-World Cybersecurity Incident Response
The framework facilitates a structured incident response process. In a hypothetical scenario, a company experiences a ransomware attack targeting its critical financial systems. The framework guides the response team through a defined series of actions. This includes immediate containment of the threat, data recovery efforts, and communication with affected parties. The standardized procedures and shared definitions of terms ensure consistency and reduce ambiguity.
This structured approach allows for a more efficient and effective response, minimizing downtime and financial losses.
“The framework’s standardized terminology and defined steps streamlined the incident response process, leading to a more effective containment and recovery of the system.”
Threat Detection and Prevention
The framework enables a standardized approach to threat detection and prevention. By leveraging shared threat intelligence, organizations can identify and analyze suspicious activities more effectively. For example, a security analyst notices unusual network traffic patterns matching a known malware signature. The framework provides a standardized process for reporting and analyzing the incident, leading to the rapid identification and containment of the threat.
The framework allows for a more coordinated and proactive approach to threat detection, minimizing the potential for widespread damage.
“Shared threat intelligence, as Artikeld in the framework, facilitated a rapid identification and containment of the suspicious network activity, preventing a potential major breach.”
Streamlined Incident Response Procedures
The framework simplifies incident response procedures by establishing clear roles, responsibilities, and communication channels. In a scenario where a data breach occurs, the framework guides the response team on handling notifications, communication protocols, and data recovery. The predefined steps ensure consistency across organizations, minimizing confusion and improving the efficiency of the response. This standardized process leads to a quicker and more efficient response to the breach, ultimately reducing the impact on the affected parties.
“The framework’s defined communication channels and responsibilities minimized response time during the data breach, enabling a faster and more organized recovery.”
Collaborative Approach Among Industry Partners
The framework fosters collaboration among industry partners by providing a common language and shared understanding of security threats and vulnerabilities. For example, a software vendor detects a vulnerability in their product. The framework enables them to report the vulnerability to other partners and organizations using their product, facilitating a coordinated response to mitigate the risk for all parties.
This collaborative approach enables rapid sharing of threat intelligence and best practices, ultimately strengthening the overall cybersecurity posture of the industry.
“The framework’s collaborative approach among industry partners allowed for a rapid dissemination of the vulnerability information, enabling a collective response and a swift patch deployment.”
Improved Incident Response Efficiency
The framework promotes efficient incident response by standardizing procedures and tools. A hypothetical scenario involves a phishing attack targeting employees. The framework provides a standardized process for identifying, containing, and recovering from the attack. This structured approach minimizes the time required to respond to the incident and the resources needed. The standardized reporting mechanisms enable organizations to collectively identify trends and patterns in attacks, improving future threat detection and prevention.
“The framework’s standardized procedures and reporting mechanisms significantly reduced the time required to identify and contain the phishing attack, improving overall incident response efficiency.”
Concluding Remarks
In conclusion, the crowdstrike and industry partners release open cybersecurity schema framework presents a significant opportunity for a more collaborative and effective approach to cybersecurity. Its open structure and modular design offer flexibility and adaptability to the ever-evolving threat landscape. By fostering industry collaboration and standardized data exchange, this framework promises to strengthen security posture across various sectors.
The potential for enhanced threat detection, incident response, and streamlined workflows is substantial, making this framework a key advancement in the ongoing battle against cybercrime.