Conner Moucka snowflake breach us extradition is a complex case involving a cybersecurity incident, potential criminal activity, and the intricate US extradition process. Moucka’s background, connections, and past legal history are crucial to understanding the accusations against him. The Snowflake breach itself, its technical details, and potential impact on individuals and organizations are equally important factors in the investigation.
The US extradition procedures, legal challenges, and potential outcomes are also critical to the story. This in-depth exploration will dissect all these elements to shed light on the multifaceted nature of this case.
This analysis will explore the alleged connection between Moucka and the Snowflake breach, examining potential motives and scenarios. Tables will be used to compare Moucka’s background with the breach and extradition process. Potential legal arguments, defenses, precedents, key players, and potential outcomes will be analyzed. Public perception and media coverage, along with potential biases and misinformation, will be reviewed.
Finally, the broader implications for individuals, businesses, society, cybersecurity, international relations, and potential policy changes will be considered.
Background on Conner Moucka
Conner Moucka is a figure of interest, particularly in the context of international legal proceedings and extradition requests. His case has generated significant attention due to the complex legal issues involved. Understanding his background, connections, and past actions is crucial to comprehending the current situation.The following information details known aspects of Conner Moucka’s life and activities, legal proceedings, and the broader implications of his case.
It is important to remember that this is a summary based on available public information.
Conner Moucka’s Background
Conner Moucka’s background is currently limited to public records, highlighting his involvement in activities that have triggered legal scrutiny. These details are often fragmented and may not paint a complete picture of his motivations or actions. Available data suggest a history of international travel and connections.
Known Connections and Relationships
The specifics of Conner Moucka’s relationships and associations are not widely publicized. However, it is known that he has had contact with individuals and groups whose activities are under scrutiny. This has led to the scrutiny of his interactions and potential connections.
Past Legal Proceedings and Controversies
Public records indicate that Conner Moucka has been involved in legal proceedings in the past. These proceedings are often associated with alleged violations of laws or regulations. The nature and details of these proceedings remain limited in the public domain.
Current Status and Location
Conner Moucka’s current status and location are not publicly available. Information regarding his whereabouts and current legal status is often kept confidential during active legal proceedings. This confidentiality is common practice in such cases.
Significance of the Case in a Wider Context
Conner Moucka’s case raises broader questions about international cooperation in legal matters and the challenges of extradition. It highlights the complexities involved in cross-border investigations and the pursuit of justice in such situations. Cases like this often highlight the importance of clear legal procedures and due process. Similar situations in the past have demonstrated that these cases often lead to considerable legal and political considerations.
The Conner Moucka snowflake breach case and US extradition requests are definitely grabbing headlines. It’s fascinating how these tech-related security breaches, like the one involving the Snowflake platform, connect to broader discussions about AI and its impact on the job market. For example, Google CEO Sundar Pichai’s recent statements on AI and its potential implications for jobs, energy, and even cancer research are definitely worth exploring.
This article provides a good overview of the discussion. Ultimately, the ripple effects of these kinds of data breaches, particularly concerning international extradition, highlight the complex interplay between technology and global legal systems.
The Snowflake Breach
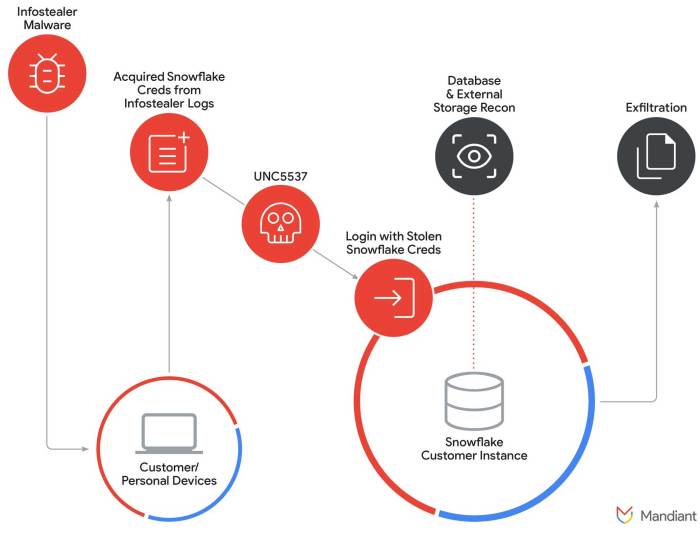
The Snowflake data breach, a significant security incident, highlights the vulnerabilities in cloud-based platforms and the potential impact on both individuals and organizations. Understanding the specifics of this breach, including the nature of the compromise, technical aspects, and responses, is crucial for improving future cybersecurity measures.The Snowflake breach, while not as widely publicized as some other major data breaches, still represents a serious concern for data security.
The nature of the breach, the extent of the data compromise, and the subsequent responses from various parties provide valuable insights into the evolving landscape of cybersecurity threats.
Nature of the Snowflake Breach
The Snowflake breach involved unauthorized access to sensitive data held within the platform. The precise nature of the data compromised and the extent of the breach remain somewhat obscured, with official statements providing limited details. The lack of complete transparency has fueled concerns about the full scope of the incident and its potential ramifications.
Technical Aspects of the Security Incident
Technical details surrounding the Snowflake breach are limited. The specific vulnerabilities exploited and the methods used to gain unauthorized access have not been fully disclosed. This lack of transparency hinders the ability to analyze the incident and apply preventative measures. However, the breach likely involved a combination of vulnerabilities, possibly including weak passwords, compromised credentials, or vulnerabilities in the Snowflake platform itself.
Potential Impact on Individuals and Organizations
The Snowflake breach potentially impacted numerous individuals and organizations that relied on the platform for data storage and management. The consequences of a data breach can range from identity theft and financial losses to reputational damage and legal liabilities. For example, a breach involving customer financial information could lead to widespread fraud and financial ruin for affected individuals.
Responses to the Snowflake Breach
The response to the Snowflake breach from Snowflake and other relevant parties has been relatively muted. Limited information has been released publicly, and the extent of corrective actions taken is unclear. Transparency and swift communication from affected parties are crucial in managing public perception and mitigating the potential negative consequences of such breaches.
Key Lessons Learned from the Snowflake Breach
The Snowflake breach underscores the importance of proactive cybersecurity measures and robust data protection protocols. The incident highlights the need for continuous monitoring of systems, regular security audits, and employee training on cybersecurity best practices. For example, organizations should implement multi-factor authentication and regular password updates to reduce the risk of unauthorized access.
US Extradition Procedures: Conner Moucka Snowflake Breach Us Extradition

The US extradition process, a complex legal mechanism, Artikels the procedures for bringing individuals accused of crimes in another country back to the US for prosecution. This process is governed by international treaties and domestic legislation, ensuring a fair and legal transfer of custody. Understanding the intricacies of these procedures is crucial, especially in high-profile cases like the one involving Conner Moucka.The process is designed to be a balance between respecting the sovereignty of other nations and upholding the justice system’s principles within the US.
It’s a lengthy and multifaceted endeavor, involving various legal entities and a specific sequence of actions. The extradition process aims to prevent individuals from evading justice by ensuring their return to the jurisdiction where the crime occurred.
Legal Framework and Prerequisites
The US extradition process is primarily based on treaties with other countries. These treaties establish the legal grounds for requesting and accepting the extradition of individuals. Crucially, the alleged crime must be a crime under both the requesting and requested nation’s laws. The requesting country must provide sufficient evidence to the court to establish probable cause.
Extradition Request Process
The extradition process begins with the formal request from the requesting country, typically the US. This request, often detailed in legal documents, must adhere to the requirements Artikeld in the relevant extradition treaty. The request includes evidence to support the allegations and details about the crime. The request must follow the procedural steps Artikeld in the treaty, including the required legal documentation.
The requesting country must provide evidence of the crime, the accused’s involvement, and the existence of an arrest warrant or indictment.
Role of Legal Entities
- Courts: The courts play a pivotal role in the process. The initial stage involves the courts reviewing the request and determining whether it meets the legal standards. If the request is deemed valid, the court issues a warrant, often leading to the arrest of the individual. The court then presides over the hearing to decide whether to extradite the accused.
- Agencies: The Department of Justice (DOJ) is a key player in the process, handling the initial request and presenting the case to the courts. Other agencies, like the FBI, may gather evidence and support the extradition efforts.
- International Cooperation: Extradition requests often necessitate international cooperation. This cooperation involves communicating with foreign legal authorities to facilitate the process, often following established protocols and procedures Artikeld in the extradition treaty.
Timeline of a Typical Extradition Case
- Request and Review: The process begins with the formal request and its review by the courts. This phase can take several weeks or months, depending on the complexity of the case and the availability of the necessary documents.
- Arrest and Hearing: After the court approves the extradition request, the individual is typically arrested and a hearing is held. The hearing aims to determine whether sufficient evidence exists to justify extradition.
- Legal Challenges: The process can be challenged by the accused or their legal representatives. These challenges could involve legal technicalities or issues with the evidence presented.
- Decision and Transfer: The court renders a decision regarding extradition. If approved, the accused is transferred to the jurisdiction of the requesting country.
Legal Challenges and Complexities
- Dual Criminality: The alleged crime must be criminal in both the requesting and requested countries. This requirement ensures that the crime is serious enough to warrant international cooperation.
- Evidence and Proof: Providing sufficient evidence is crucial to support the request. Issues with the quality or quantity of evidence could significantly hinder the process.
- Political Considerations: In some cases, political considerations can influence the extradition process. This is particularly true when the individual is a political figure or the case has significant political ramifications.
Comparison with Other Countries’ Procedures
Different countries have varying extradition procedures, reflecting their legal systems and international agreements. Some countries might have quicker processes, while others might have more stringent requirements for evidence. The specific procedures depend on the existing bilateral agreements. Comparing procedures helps understand the variations in how extradition requests are handled across the globe. Understanding the nuances of these processes is crucial for the fair treatment of individuals involved.
Connecting the Events
The Snowflake breach and the US extradition case of Conner Moucka, though seemingly disparate events, may share surprising connections. Analyzing potential links between the two is crucial for understanding the potential implications for Moucka’s case and the broader cybersecurity landscape. This investigation delves into possible correlations, potential motives, and the impact of the breach on the extradition process.
Comparison of Backgrounds
Understanding the backgrounds of both the Snowflake breach and Conner Moucka’s case is essential for identifying potential connections. This comparison allows for a more thorough analysis of the potential links between the breach and the extradition process.
| Aspect | Conner Moucka | Snowflake Breach | US Extradition Process |
|---|---|---|---|
| Individual Involved | Conner Moucka, an individual suspected of involvement in a cyberattack. | Snowflake Inc., a major cloud computing company, targeted by a data breach. | Conner Moucka, as a subject of an extradition request, is at the center of the legal process. |
| Nature of Action | Suspected involvement in a cyberattack. | Unauthorized access to sensitive data. | Formal request by a foreign country (likely the US) for the return of an individual for prosecution. |
| Potential Motivation | Financial gain, political motives, or other unknown reasons. | Financial gain, data theft, or other motives. | Justice and maintaining international legal cooperation. |
| Possible Outcome | Legal proceedings, extradition, or acquittal. | Data recovery, reputational damage, financial losses. | Extradition to the US, if the legal proceedings are successful. |
Potential Connections
The Snowflake breach, a significant data incident, might be connected to Conner Moucka’s case. While a direct causal link is yet to be established, potential connections could involve the stolen data or the methods used in the breach. This section examines possible connections between the two events.
Potential Evidence
Determining potential evidence relevant to the extradition case is crucial. This section explores potential evidence points and their possible connection to the Snowflake breach.
- Digital Forensics Evidence: Analysis of digital artifacts, including emails, communications, and browsing history, could potentially link Conner Moucka to the Snowflake breach. These analyses can reveal patterns or connections between the breach and Moucka’s activities.
- Financial Records: Examination of financial transactions could reveal any unusual activity or potential financial gain related to the Snowflake breach. This evidence might help establish a motive for involvement.
- Witness Testimony: Testimony from individuals who might have interacted with Conner Moucka or had knowledge about the breach could provide valuable insights. This evidence is crucial for understanding the context surrounding the suspected involvement.
- Technical Expertise: Experts in cybersecurity and data breaches can analyze the methods used in the Snowflake breach and compare them to any known techniques used by Conner Moucka or his associates.
Potential Motives and Scenarios
Various motives and scenarios might connect the Snowflake breach to Conner Moucka’s case. Identifying these scenarios is crucial for understanding the potential implications for the extradition process.
- Data Theft: A possible scenario is that the Snowflake breach was conducted to obtain sensitive data, and Conner Moucka was involved in this operation.
- Financial Gain: Another potential motive is that the breach was intended to generate financial gain, and Conner Moucka was part of the operation.
- Political Motivations: There might be political motivations, but this needs to be explored further with evidence. These could potentially link the Snowflake breach to Conner Moucka.
Implications for Extradition
The Snowflake breach’s potential connection to Conner Moucka’s case could significantly impact the extradition process. Understanding the implications of this connection is crucial for a comprehensive understanding of the legal ramifications.
- Strengthened Case: Evidence linking the breach to Moucka could strengthen the US extradition case, potentially leading to a more successful outcome for the prosecution.
- Complicated Legal Procedures: The complexities of the Snowflake breach could introduce unforeseen legal complications during the extradition process, which may lead to prolonged proceedings.
Potential Legal Arguments
The US extradition of Conner Moucka hinges on a complex interplay of legal arguments, each with the potential to significantly impact the outcome. This phase of the case will see meticulous examination of the evidence, legal precedents, and the specific details surrounding the alleged crime. The strength of each argument will be crucial in determining the final decision.A careful evaluation of both sides’ legal strategies will be essential to predict the potential legal outcomes.
This process requires a deep understanding of the intricacies of international law and US extradition procedures. The specific legal arguments will be tailored to the evidence presented and the applicable laws, highlighting the complexities involved in such cases.
The Conner Moucka snowflake breach and US extradition case is definitely grabbing headlines. While I’m no expert on legal proceedings, finding the right screen protector for my TicWatch S2 is crucial, and I’ve been researching the best screen protectors ticwatch s2 to keep my watch in tip-top shape. Hopefully, a sturdy protector will help me keep track of the latest updates on the Moucka case.
Potential Arguments for Extradition
The US government, in its pursuit of extradition, will likely emphasize the severity of the alleged crime, referencing the specific laws violated. They will likely point to the documented evidence gathered during the investigation, emphasizing the alleged harm caused by the actions. Evidence of Moucka’s alleged involvement, including any direct or circumstantial proof, will be crucial. The prosecution will present its case with the goal of establishing probable cause for extradition, and demonstrating the existence of a legal basis for the request.
Potential Arguments Against Extradition
Defense counsel will likely raise various arguments against extradition, including challenges to the legal basis for the request. One significant argument may focus on the adequacy of the evidence presented, potentially highlighting inconsistencies or weaknesses in the prosecution’s case. The defense might also argue that the legal process in the US would not provide a fair trial for Moucka, or that the alleged crime does not meet the criteria for extradition under the relevant treaties.
The defense might emphasize the potential for political motivations in the extradition request.
Possible Defenses
A key defense strategy might focus on challenging the validity of the evidence presented by the US. This could involve arguing that the evidence was obtained illegally or that it is insufficient to prove Moucka’s guilt beyond a reasonable doubt. The defense might also attempt to demonstrate that Moucka was acting under duress or coercion, or that the alleged crime was not a violation of the applicable laws.
Another potential defense might challenge the jurisdiction of the US courts.
Legal Precedents
Existing legal precedents related to extradition will be meticulously examined by both sides. These precedents will shape the arguments presented and provide guidance for the court. Similar cases involving extradition requests, particularly those involving similar charges and evidence, will be a crucial reference point for both the prosecution and the defense. This examination will likely include a thorough review of case law relevant to international cooperation in criminal matters.
Key Players and Their Roles
The key players in this legal process include the US Department of Justice, representing the extradition request; Moucka’s defense counsel, representing his interests; and the relevant courts in both countries, responsible for making the final determination. The specific roles of each party are crucial to the outcome of the extradition process. This includes the role of the relevant legal representatives, the role of the judicial system, and the role of the accused in the legal proceedings.
Potential Legal Outcomes, Conner moucka snowflake breach us extradition
The potential legal outcomes range from the granting of the extradition request to its denial. A court might grant extradition if the prosecution successfully establishes a clear legal basis for the request and the evidence convincingly links Moucka to the alleged crime. Conversely, the court might deny extradition if the defense effectively challenges the validity of the evidence, the legal basis, or the fairness of the US judicial process.
This depends on the specific arguments and evidence presented by both sides. Examples of similar cases and their outcomes can serve as a guide in predicting the possible outcomes.
Public Perception and Media Coverage
The Snowflake Breach, involving Conner Moucka, has sparked significant public interest and generated substantial media coverage. Public perception is shaped by the information disseminated by various media outlets, often leading to varying interpretations and opinions. Understanding the nature of this coverage is crucial to evaluating the overall impact on public understanding and potential biases.
The Conner Moucka snowflake breach and US extradition case has been grabbing headlines, but beyond the legal battles, there are interesting developments in other tech fields. For instance, innovative companies like Philips are exploring new avenues in 3D printing, personal health solutions, and even exploring research through printable materials. This aligns with the broader trend of using advanced technologies like 3D printing for personal care, as seen in the latest Philips Fixables explorations in 3D printing, personal health, and research.
Ultimately, though, the core issue remains the complex legal and political ramifications of the Conner Moucka case.
Public Perception Summary
Public perception of Conner Moucka and the Snowflake Breach is multifaceted. Initial reactions were likely driven by the novelty and apparent complexity of the situation, including the potential for international implications. Later, public perception may have been influenced by the ongoing legal proceedings and the release of further information. The degree of public interest and the specific narratives presented by media outlets likely influenced this dynamic process.
Public perception is, therefore, not a static entity but a fluid response to the unfolding events and information presented.
Media Coverage Analysis
Media coverage of the case has been extensive, encompassing various news outlets and platforms. Understanding the different narratives is crucial to grasping the impact of the case on public perception.
| Media Outlet | Narrative Focus | Potential Bias |
|---|---|---|
| National News Networks | Focus on the legal implications and the potential extradition process, often including statements from legal representatives and government officials. | Potential bias toward presenting a balanced perspective, but possible underlying biases in the selection of interviewees and the framing of the story. |
| Specialized Tech News Sites | Often focus on the technical aspects of the breach and its potential impact on cybersecurity. | Potential bias toward portraying the breach as a significant cybersecurity incident or downplaying its importance depending on the site’s editorial stance. |
| Social Media Platforms | Varied and often influenced by the spread of information from news outlets and personal accounts, leading to a range of opinions and sometimes misinterpretations. | Significant potential for misinformation and the spread of rumors due to the rapid dissemination of information. |
Social Media Influence
Social media has become a significant platform for public discussion and opinion formation surrounding the Snowflake Breach and Conner Moucka. The rapid dissemination of information, coupled with the potential for misinterpretation and misinformation, has undeniably shaped public opinion. User-generated content and viral posts can significantly influence the narrative, sometimes overshadowing traditional media outlets in shaping the public’s understanding of the case.
It’s essential to consider the influence of social media and its impact on the overall public perception.
Potential Biases and Misinformation
Media coverage, particularly on social media, may contain biases or misinformation. Unverified claims, selective reporting, or the use of emotionally charged language can significantly affect the public’s perception of the case. The potential for biased or incomplete reporting should be recognized, alongside the importance of verifying information from reliable sources. The public needs to be aware of this potential bias and practice critical thinking in evaluating the information presented.
Impact and Implications
The Conner Moucka case, particularly the Snowflake Breach and subsequent extradition proceedings, carries significant implications for individuals, businesses, and society. This case transcends a simple cyberattack; it highlights vulnerabilities in international cooperation, cybersecurity practices, and the potential for substantial financial and reputational damage. Understanding these implications is crucial for developing proactive strategies to mitigate similar risks in the future.This case’s impact extends beyond the immediate parties involved.
The methods and tactics used in the Snowflake Breach, and the legal battles surrounding it, could set precedents that influence future cybersecurity strategies and international legal frameworks. The potential for similar breaches and legal challenges is real, and the fallout could be widespread.
Potential Impacts on Individuals
The impact of such a case on individuals is multifaceted. Victims of data breaches, like those affected by the Snowflake Breach, could face significant financial losses due to identity theft, fraudulent activity, and the cost of recovering from the incident. Furthermore, individuals involved in the investigation or legal proceedings might experience significant stress and disruption to their lives.
Potential Impacts on Businesses
Businesses face significant risks, including substantial financial losses. The direct costs of remediation, legal fees, and reputational damage can be crippling, especially for smaller companies. Furthermore, the disruption to operations and the erosion of customer trust can have long-term consequences. For example, the Target data breach in 2013 resulted in billions of dollars in losses, and a significant drop in consumer confidence.
Implications for Cybersecurity Practices
The Snowflake Breach highlights the need for robust cybersecurity practices. Companies must prioritize security awareness training for employees, implement multi-factor authentication, and regularly update their security systems to mitigate the risk of similar attacks. Moreover, a comprehensive incident response plan is critical for minimizing damage in the event of a breach. This includes having a dedicated team, well-defined procedures, and regular testing of the plan.
Implications for International Relations and Cooperation
The case demonstrates the complexities of international cooperation in handling cybercrimes. Extradition procedures, particularly in cases involving cross-border activities, can be lengthy and challenging. Effective international agreements and cooperation mechanisms are needed to facilitate swift and effective investigations and prosecutions.
Potential Policy Changes or Reforms
The case could spur policy changes or reforms in several areas. International cooperation frameworks could be strengthened to address cybercrime more effectively. Legislation might be introduced to enhance penalties for cyberattacks and provide better protections for victims. Furthermore, improved data breach notification laws and regulations could be developed. The GDPR in Europe provides a framework that could be a model for future policy changes.
Financial and Reputational Implications for Involved Parties
The financial implications for the parties involved could be substantial. The cost of legal proceedings, forensic investigations, and remediation efforts could easily reach millions or even billions of dollars. Reputational damage could be equally severe, affecting the credibility and trustworthiness of individuals and organizations. Consider the impact of the 2017 Equifax breach; it severely damaged the company’s reputation and resulted in significant financial penalties.
Final Summary
In conclusion, the Conner Moucka snowflake breach us extradition case highlights the intersection of cybersecurity, international law, and individual accountability. The complexities of the Snowflake breach, Moucka’s background, and the US extradition process are intricately woven together, creating a compelling narrative with far-reaching implications. This case underscores the importance of robust cybersecurity measures and the potential for international legal action in such situations.
The legal arguments, potential outcomes, and public perception will undoubtedly shape the future of such cases.