Attack vectors at a glance sets the stage for this enthralling narrative, offering readers a glimpse into the intricate world of cybersecurity threats. We’ll explore the various ways malicious actors attempt to breach systems, from social engineering tactics to sophisticated network vulnerabilities. Understanding these attack vectors is crucial for developing robust security strategies. This overview will cover common attack vectors, their methodologies, impact analysis, and essential mitigation strategies.
Get ready to delve into the fascinating world of cybersecurity threats and defenses!
This exploration will delve into the different categories of attack vectors, examining their unique characteristics, potential impacts, and the methodologies used to exploit them. We’ll analyze real-world case studies to understand the effectiveness of security controls and strategies. The goal is to provide a comprehensive understanding of attack vectors for anyone seeking to enhance their cybersecurity knowledge.
Introduction to Attack Vectors
Attack vectors are the pathways or methods that malicious actors use to compromise a system or network. They represent the specific vulnerabilities exploited to gain unauthorized access or cause harm. Understanding attack vectors is crucial for effective cybersecurity strategies, allowing organizations to identify potential weaknesses and implement preventative measures.
Fundamental Concepts of Attack Vectors
Attack vectors are not just the actions of a hacker, but rather a detailed description of how a vulnerability is exploited. This includes the specific steps and techniques used, from initial reconnaissance to gaining access and causing damage. These techniques can be employed against a wide array of targets, from individual computers to entire corporate networks. A thorough understanding of attack vectors requires recognizing the underlying vulnerabilities that attackers exploit, which range from weak passwords to poorly configured systems.
This recognition leads to the implementation of robust defenses.
Quick look at attack vectors? Think vulnerabilities in systems. The Trump administration’s recent initiative to ban Chinese apps and cloud platforms, like the one detailed in this article , highlights a potential new vector for cyberattacks. Ultimately, understanding these attack vectors is crucial for bolstering digital security.
Importance of Understanding Attack Vectors in Cybersecurity
Recognizing attack vectors is paramount for proactive cybersecurity. By understanding the methods attackers use, organizations can identify and address potential vulnerabilities before they are exploited. This proactive approach significantly reduces the risk of successful attacks and minimizes potential damage. The identification of attack vectors also allows for the development and implementation of targeted security controls, which are more effective than broad-spectrum solutions.
Examples of Attack Vector Categories
Attack vectors manifest in various forms, categorized by their approach. Social engineering exploits human psychology to manipulate individuals into revealing sensitive information or performing actions that compromise security. Malware, including viruses, worms, and Trojans, infects systems and gains control through various methods. Network vulnerabilities, such as unpatched software or misconfigured firewalls, provide pathways for attackers to gain unauthorized access.
Attack Vector Categorization Table
| Attack Vector Type | Description | Potential Impact |
|---|---|---|
| Social Engineering | Manipulating individuals through psychological tactics to gain access to sensitive information or perform actions that compromise security. Examples include phishing, pretexting, and baiting. | Data breaches, financial losses, reputational damage, and operational disruption. |
| Malware | Software designed to damage or disable a computer system, often without the user’s knowledge or consent. Examples include viruses, worms, Trojans, ransomware, and spyware. | Data theft, system compromise, denial-of-service attacks, financial losses, and operational disruption. |
| Network Vulnerabilities | Weaknesses in network infrastructure or software that attackers can exploit to gain unauthorized access. Examples include unpatched software, misconfigured firewalls, and insecure network protocols. | Unauthorized access, data breaches, denial-of-service attacks, and network disruption. |
| Phishing | A type of social engineering attack that uses fraudulent emails or messages to trick individuals into revealing sensitive information, such as usernames, passwords, and credit card details. | Data breaches, financial losses, and identity theft. |
Common Attack Vectors
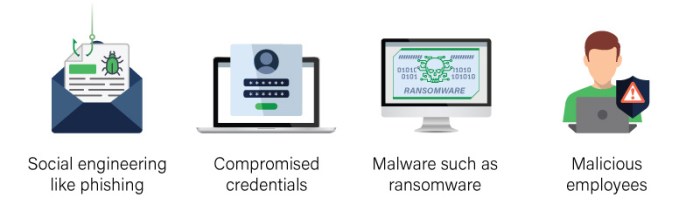
Understanding the various pathways attackers utilize to compromise systems is crucial for developing robust security strategies. Attack vectors represent the specific methods employed to gain unauthorized access or inflict harm. Knowing these vectors allows security professionals to anticipate potential threats and implement preventative measures.The digital landscape is constantly evolving, bringing new attack vectors and sophisticated techniques. Staying informed about the most prevalent approaches allows for proactive defense and mitigation of potential vulnerabilities.
This section details common attack vectors, highlighting their characteristics, targets, and countermeasures.
Web Application Attack Vectors
Web applications are frequent targets due to their widespread use and often complex functionalities. Common attack vectors exploit vulnerabilities in web application code, including SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). These vulnerabilities can lead to data breaches, unauthorized access, and the execution of malicious code. For instance, SQL injection allows attackers to manipulate database queries, potentially gaining access to sensitive data or even controlling the database.
Mobile Device Attack Vectors
Mobile devices are increasingly vulnerable due to their ubiquitous nature and often limited security measures. Attackers exploit vulnerabilities in operating systems, applications, and the devices themselves. Phishing attacks targeting mobile users are common, leading to the installation of malware. Malicious applications, disguised as legitimate ones, can steal sensitive information or compromise the device. For example, a user might download a seemingly harmless app that secretly records calls or accesses personal data.
IoT Device Attack Vectors
The proliferation of Internet of Things (IoT) devices introduces new attack surfaces. These devices often have limited security features and are vulnerable to exploitation. Attackers can exploit vulnerabilities in the device’s firmware or communication protocols. These vulnerabilities can lead to unauthorized access, data breaches, and even physical harm. For example, a compromised smart thermostat could be used to remotely manipulate the temperature of a home, potentially causing damage or discomfort.
Social Engineering Techniques
Social engineering techniques manipulate individuals into divulging sensitive information or performing actions that compromise security. These techniques often leverage human psychology and trust to gain access to systems or data. Phishing emails, pretexting calls, and baiting are examples of social engineering tactics. For example, a phishing email might appear to be from a legitimate bank, prompting the user to enter their login credentials on a fake website.
Malware Attack Vectors, Attack vectors at a glance
Malware, malicious software, can be introduced into systems through various channels. Malicious attachments in emails, infected websites, or compromised software downloads are common vectors. These infections can lead to data breaches, system disruption, and financial losses. For example, ransomware encrypts files and demands payment for their release, causing significant financial and operational disruption.
Network-Based Attack Vectors
Network-based attack vectors target the communication infrastructure. Denial-of-service (DoS) attacks overwhelm a system with traffic, preventing legitimate users from accessing it. Man-in-the-middle (MitM) attacks intercept communications between two parties, allowing attackers to eavesdrop or modify data. These attacks can have devastating consequences for businesses and individuals. For example, a DoS attack could shut down a website, preventing customers from making purchases or accessing information.
Comparison of Common Attack Vectors
| Attack Vector | Typical Targets | Countermeasures |
|---|---|---|
| SQL Injection | Web applications, databases | Input validation, parameterized queries |
| Cross-Site Scripting (XSS) | Web applications | Output encoding, input validation, Content Security Policy |
| Cross-Site Request Forgery (CSRF) | Web applications | Anti-CSRF tokens, double-submit cookie |
| Phishing | Users, organizations | Security awareness training, strong passwords, multi-factor authentication |
| Malware | Systems, devices, networks | Antivirus software, regular updates, secure configurations |
| Denial-of-Service (DoS) | Servers, networks | Firewalls, intrusion detection systems, load balancing |
| Man-in-the-Middle (MitM) | Networks, communications | Encryption, secure protocols, network segmentation |
Attack Vector Methodology
Understanding attack vectors goes beyond simply identifying them; it’s crucial to grasp the methodologies behind their exploitation. This involves recognizing the phases of an attack, the methods used to discover and leverage vulnerabilities, and the practical application of these techniques in diverse scenarios. Analyzing specific attack vectors reveals the steps involved in their execution, providing a comprehensive picture of the attacker’s tactics.Attack vector methodology encompasses a structured approach to exploiting vulnerabilities.
This involves a systematic process of reconnaissance, vulnerability assessment, exploitation, and post-exploitation activities. Understanding these steps allows for the development of effective defensive strategies to mitigate potential threats.
Attack vectors, at a glance, are essentially the pathways hackers use to exploit vulnerabilities. Understanding these paths is crucial for securing systems. A critical aspect of this is exploring how virtual CSS public-private architectures, like those detailed in virtual css public private , can affect security. Ultimately, a comprehensive understanding of attack vectors remains essential for robust defense strategies.
Typical Phases of Attack Exploitation
The exploitation of attack vectors often follows a series of well-defined phases. These phases, while not always rigidly sequential, provide a framework for understanding the attacker’s approach. Each phase plays a crucial role in the overall attack process.
- Reconnaissance: This initial phase involves gathering information about the target system. Attackers may use various tools and techniques to discover potential vulnerabilities, network configurations, and user accounts. This includes passive reconnaissance (e.g., searching for publicly available information) and active reconnaissance (e.g., scanning ports and services).
- Vulnerability Assessment: This phase focuses on identifying weaknesses within the target system. Attackers utilize various tools and techniques to probe the system for vulnerabilities. Examples include vulnerability scanners, penetration testing tools, and code analysis tools.
- Exploitation: Once vulnerabilities are identified, attackers attempt to exploit them to gain unauthorized access. Exploitation methods vary widely, depending on the specific vulnerability. Examples include exploiting buffer overflows, SQL injection vulnerabilities, or cross-site scripting (XSS) flaws.
- Post-Exploitation: After gaining access, attackers may attempt to maintain their presence, escalate privileges, or gather further information. This phase can involve actions such as installing malware, creating backdoors, and exfiltrating sensitive data.
Methods for Discovering and Leveraging Attack Vectors
Attackers employ various methods to identify and exploit vulnerabilities. These techniques involve a combination of automated tools, manual analysis, and social engineering.
- Automated Vulnerability Scanners: These tools automatically scan systems for known vulnerabilities, providing a comprehensive inventory of potential weaknesses. Examples include Nessus, OpenVAS, and QualysGuard.
- Manual Penetration Testing: Ethical hackers and security professionals conduct manual penetration tests to identify vulnerabilities that automated tools might miss. This involves simulating real-world attacks to assess the effectiveness of security controls.
- Social Engineering: This involves manipulating individuals to gain access to sensitive information or systems. Examples include phishing emails, pretexting, and baiting.
Examples of Attack Vector Methodologies in Different Contexts
The methodology for exploiting attack vectors varies depending on the context. Consider a web application attack versus a network-based attack. The steps and tools used differ significantly.
- Web Application Attacks: Attackers might use SQL injection to gain access to a database. This involves crafting malicious input to exploit vulnerabilities in the application’s code. Tools like SQLmap are commonly used for this purpose.
- Network-Based Attacks: A denial-of-service (DoS) attack aims to overwhelm a target system with traffic, preventing legitimate users from accessing it. Methods like flooding the target with SYN packets are frequently employed.
Steps in Executing an Attack Using Specific Attack Vectors
The precise steps involved in executing an attack vary significantly depending on the specific attack vector. A detailed breakdown is not exhaustive but provides insights into the process.
- SQL Injection: Steps include identifying an injection point in the web application, crafting a SQL query to exploit the vulnerability, executing the query, and retrieving or manipulating data. Tools such as SQLmap are commonly used.
Stages of an Attack and Actions Taken
This table Artikels the typical stages of an attack and the actions taken at each stage. It provides a framework for understanding the progression of an attack.
| Stage | Actions |
|---|---|
| Reconnaissance | Information gathering about the target, identifying vulnerabilities |
| Vulnerability Assessment | Probing the target for weaknesses, analyzing identified vulnerabilities |
| Exploitation | Attempting to gain unauthorized access using identified vulnerabilities |
| Post-Exploitation | Maintaining access, escalating privileges, exfiltrating data |
Attack Vector Impact Analysis
Understanding the potential consequences of successful cyberattacks is crucial for developing effective security strategies. Attack vectors, the pathways used by malicious actors to breach systems, can lead to a cascade of negative impacts. This section delves into the far-reaching effects of various attack methods, focusing on data security, financial repercussions, reputational damage, and legal implications.
Consequences of Successful Attacks
Successful exploitation of an attack vector can have significant ramifications. These consequences range from subtle data breaches to catastrophic system failures, impacting not only the targeted organization but also its customers and stakeholders. The severity of the impact hinges on several factors, including the specific vector used, the target’s defenses, and the attacker’s intent.
Impact on Data Security and Confidentiality
Attack vectors directly threaten the confidentiality, integrity, and availability of data. For instance, a phishing attack can compromise sensitive personal information, leading to identity theft and financial fraud. Malware infections can exfiltrate sensitive corporate data, impacting intellectual property and competitive advantage. Data breaches can result in severe regulatory penalties and substantial reputational damage.
Financial and Reputational Damage
The financial repercussions of a successful attack can be substantial. Costs include incident response, forensic analysis, data recovery, regulatory fines, and lost revenue. Furthermore, reputational damage can be long-lasting, impacting customer trust and brand loyalty. Consider the case of [Insert Example of a Large Data Breach]. The company suffered significant financial losses and saw a decline in its stock price and customer base.
Legal and Regulatory Implications
Exploiting attack vectors can lead to severe legal and regulatory implications. Compliance with data protection regulations like GDPR or CCPA is critical. Failure to comply can result in substantial fines and legal action. In addition, criminal charges can be filed against individuals or organizations involved in illegal activities like ransomware attacks.
Potential Impact of Various Attack Vectors
| Attack Vector | Potential Financial Losses (USD) | Estimated Recovery Time (Days) | Description |
|---|---|---|---|
| Phishing | $50,000 – $1,000,000+ | 7-30 | Tricking users into revealing sensitive information. |
| Malware (Ransomware) | $10,000 – $Millions+ | 1-30+ | Malicious software that encrypts data and demands payment for decryption. |
| SQL Injection | $10,000 – $1,000,000+ | 3-14 | Exploiting vulnerabilities in database queries to gain unauthorized access. |
| Denial-of-Service (DoS) | $1,000 – $Millions+ | 1-7 | Overwhelming a system with traffic to disrupt service. |
| Man-in-the-Middle (MitM) | $500 – $Millions+ | 3-14 | Interception of communication between two parties. |
Note: Financial losses and recovery times are estimates and can vary significantly based on the specific attack, organization, and response strategies.
Mitigation Strategies for Attack Vectors
Protecting systems and data from malicious attacks requires a multi-layered approach. Effective mitigation strategies encompass a combination of technical controls, security awareness training, and proactive threat intelligence. This proactive approach, rather than just reacting to attacks, is crucial in building resilient defenses against evolving threats.Understanding the specific vulnerabilities associated with each attack vector is paramount. Mitigating these vulnerabilities involves implementing security measures that directly address the weaknesses exploited by attackers.
This understanding, combined with a strong security posture, is essential for minimizing the risk of successful cyberattacks.
Security Controls for Attack Vector Mitigation
Security controls play a vital role in defending against various attack vectors. These controls act as barriers, preventing attackers from exploiting vulnerabilities and gaining unauthorized access. Different types of controls, each with its specific function, are essential for a comprehensive defense strategy.
- Network Security Controls: Firewalls, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs) are crucial for controlling network traffic and preventing unauthorized access. These controls monitor network activity for malicious patterns and block suspicious connections. Firewalls, for example, can be configured to filter specific types of traffic based on predefined rules.
- Endpoint Security Controls: Antivirus software, endpoint detection and response (EDR) solutions, and application whitelisting help protect individual devices from malware and other threats. These controls monitor and analyze activity on endpoints, such as computers and mobile devices, to identify and respond to suspicious behavior.
- Data Security Controls: Encryption, access controls, and data loss prevention (DLP) systems are vital for safeguarding sensitive data. Encryption protects data in transit and at rest, while access controls limit who can access specific data. DLP systems monitor for sensitive data leaving the network and prevent unauthorized disclosure.
Security Awareness Training for Users
User education is a critical component of any comprehensive security strategy. By raising awareness of potential attack vectors and educating users on safe practices, organizations can significantly reduce the risk of successful attacks. Training should focus on recognizing phishing attempts, avoiding suspicious links and attachments, and adhering to strong password policies.
- Phishing Awareness Training: Regular training sessions can help users identify phishing emails, text messages, and other deceptive communications. This includes recognizing common phishing tactics, such as spoofing, and understanding how to report suspicious activities.
- Password Management Training: Educating users on creating strong, unique passwords and using password managers is critical to preventing account breaches. This also includes the importance of not sharing passwords.
- Safe Browsing Practices: Users should be educated on safe browsing habits, including recognizing potentially malicious websites and avoiding suspicious downloads. This should include avoiding clicking on unknown or untrusted links.
Security Tools and Technologies
A wide range of security tools and technologies are available to detect, prevent, and respond to attacks leveraging different attack vectors. Choosing the right tools depends on the specific needs and resources of an organization.
- Vulnerability Scanning Tools: Tools like Nessus and OpenVAS identify vulnerabilities in systems and applications. Regular scanning helps organizations proactively address security weaknesses before attackers exploit them.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security logs from various sources, providing valuable insights into potential threats. This analysis allows for early detection of suspicious activity.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS systems monitor network traffic for malicious activity and can automatically block or mitigate attacks. These tools are crucial in preventing malicious traffic from reaching the network.
Mitigation Strategies Effectiveness Table
| Attack Vector | Mitigation Strategy | Effectiveness |
|---|---|---|
| Phishing | Security Awareness Training | High |
| Malware | Endpoint Security Controls (antivirus) | Medium-High |
| SQL Injection | Input Validation, Prepared Statements | High |
| Denial-of-Service (DoS) | Network Security Controls (firewalls, load balancers) | Medium-High |
| Man-in-the-Middle (MitM) | Network Security Controls (encryption), Secure Protocols | High |
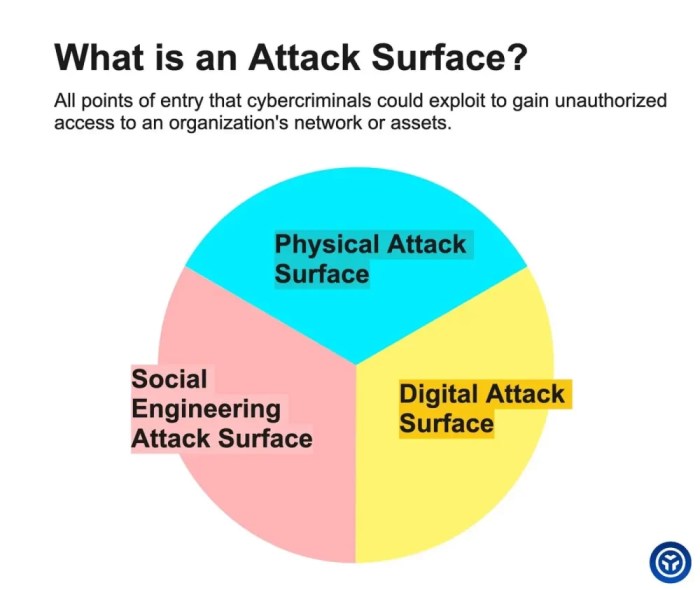
Attack Vector Categorization and Classification
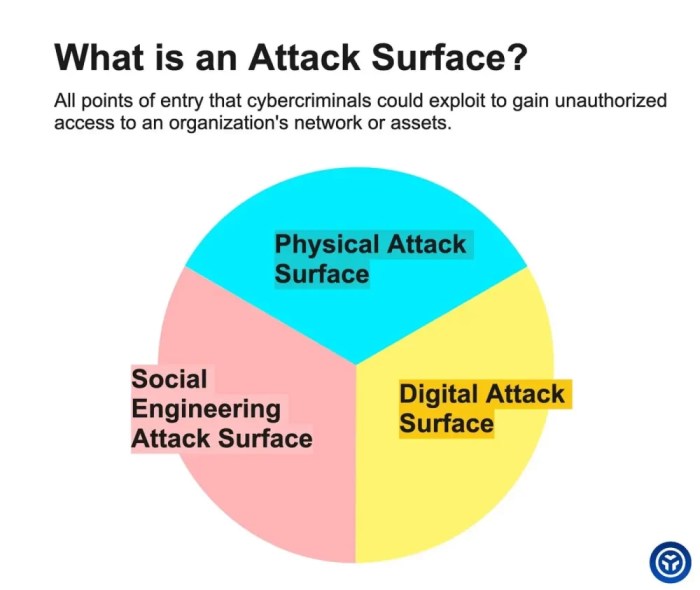
Categorizing attack vectors is crucial for understanding their nature and developing effective defenses. A well-defined classification system allows security teams to identify patterns, prioritize threats, and tailor mitigation strategies. This structured approach facilitates the development of comprehensive security policies and incident response plans.A robust categorization scheme provides a framework for analyzing and understanding the various ways an attacker might exploit a system.
This framework allows for a deeper comprehension of the attack surface and the vulnerabilities that are most susceptible to exploitation.
Categorization Schemes
Different frameworks categorize attack vectors based on various criteria. Some schemes focus on the origin of the attack, others on the target, and still others on the methods used. Understanding these different approaches allows for a more comprehensive view of the threat landscape.
Attack Vector Origin
This classification method groups attacks based on where they originate. This is a critical element for understanding the source of the threat and assessing the potential impact on an organization. Understanding the origin allows for more targeted and effective security measures.
Quick look at attack vectors – they’re essentially the pathways a threat actor can use to breach a system. Recently, there’s been a lot of buzz surrounding the Pixel 7a Tensor G2, specifically its alleged packaging design. This pixel 7a tensor g2 alleged packaging has some interesting implications for potential security vulnerabilities, which ultimately ties back to those attack vectors.
Understanding these attack surfaces is crucial for any security-conscious individual or organization.
- Internal Attacks: These originate from within the organization, often by malicious insiders or compromised accounts. These attacks can be particularly damaging because they are often undetected for extended periods. Examples include disgruntled employees, compromised administrative accounts, and insider trading.
- External Attacks: These originate from outside the organization, such as hackers, state-sponsored actors, or other malicious entities. They often involve sophisticated techniques and require a high level of vigilance and robust security measures.
- Third-Party Attacks: These attacks leverage vulnerabilities in the systems or data of organizations that are connected to the target organization, such as suppliers or partners. These attacks can be more difficult to detect and often require collaboration with third-party organizations.
Attack Vector Target
This categorization scheme focuses on the specific assets or systems targeted by the attack. Understanding the target is crucial for assessing the potential impact of a breach and developing targeted defenses.
- Network Attacks: These attacks target the network infrastructure, aiming to disrupt communication, gain unauthorized access, or steal data. These can include denial-of-service (DoS) attacks, man-in-the-middle (MitM) attacks, and network sniffing.
- Application Attacks: These attacks target the software applications that users interact with, exploiting vulnerabilities in the code or design. This can include SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) attacks.
- System Attacks: These attacks target the operating systems and underlying infrastructure of a system. These attacks can often lead to complete system compromise and data loss. Examples include privilege escalation attacks and malware infections.
- Data Attacks: These attacks specifically target sensitive data, aiming to steal, modify, or destroy confidential information. This can include phishing attacks, data breaches, and insider theft.
Attack Vector Methods
This method categorizes attacks based on the specific techniques employed by the attackers. Knowing the methods used can be invaluable in developing countermeasures and preventing future attacks.
- Social Engineering: This involves manipulating individuals into divulging sensitive information or performing actions that compromise security. This includes phishing, pretexting, and baiting.
- Malware Attacks: These attacks involve the use of malicious software to gain unauthorized access or control of systems. This includes viruses, worms, Trojans, ransomware, and spyware.
- Exploit-Based Attacks: These attacks leverage known vulnerabilities in software or hardware to gain unauthorized access. These vulnerabilities can be in operating systems, applications, or libraries.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm a system or service with traffic, making it unavailable to legitimate users. These attacks can be simple or highly sophisticated.
Comprehensive Classification Table
| Attack Vector Category | Origin | Target | Method |
|---|---|---|---|
| Internal Threats | Within the organization | Applications, Systems, Data | Social Engineering, Malware, Exploit |
| External Threats | Outside the organization | Networks, Applications, Systems | Exploits, DoS, Phishing |
| Third-Party Threats | Third-party organizations | Networks, Applications, Data | Vulnerabilities, Social Engineering, Malware |
Case Studies of Attack Vectors
Real-world examples of successful attacks and subsequent mitigations offer invaluable insights into the complexities of cybersecurity. Understanding how attackers exploit vulnerabilities allows us to develop more robust defenses. Analyzing these cases highlights the importance of proactive security measures and the evolving nature of cyber threats.Exploitation of vulnerabilities is not a theoretical concept; it’s a tangible reality with significant consequences.
These case studies, while specific to particular attack vectors, reveal broader trends in attack strategies and the persistent need for continuous improvement in cybersecurity practices.
The Equifax Data Breach: Exploiting a Vulnerability in a Web Application
The 2017 Equifax data breach, a significant incident impacting millions of individuals, serves as a prime example of a vulnerability in a web application being exploited. Attackers successfully exploited a vulnerability in Equifax’s systems, gaining unauthorized access to sensitive personal data, including social security numbers, birthdates, and addresses. This incident highlighted the critical need for regular security audits and vulnerability assessments.The breach exposed weaknesses in the company’s security posture.
This led to the implementation of stringent security measures, such as enhanced authentication protocols, improved data encryption, and more robust access controls. The case underscored the importance of a proactive approach to cybersecurity, rather than solely relying on reactive measures after an attack.
The SolarWinds Supply Chain Attack: Exploiting Trust in Software Updates
The 2020 SolarWinds supply chain attack demonstrates a sophisticated approach to exploiting trust in software updates. Attackers compromised the SolarWinds Orion platform, a widely used IT management tool. This attack leveraged the trust that organizations placed in SolarWinds’ software, injecting malicious code into legitimate updates. The attackers then used this access to infiltrate numerous organizations’ networks.This incident highlighted the vulnerability of supply chains and the importance of robust third-party risk management.
Organizations began implementing more thorough scrutiny of software updates, including employing automated tools for threat detection and investigation. The SolarWinds attack underscored the necessity of not only strengthening internal defenses but also carefully vetting and monitoring external software dependencies.
The NotPetya Ransomware Attack: Exploiting Malware and Network Propagation
The NotPetya ransomware attack of 2017 demonstrated the destructive potential of malware combined with network propagation techniques. This attack utilized a sophisticated malware payload that not only encrypted data but also spread rapidly across networks. The attack disrupted global operations in various sectors, causing significant financial losses.This case study underscored the importance of robust network segmentation and regular backups.
Organizations began implementing enhanced security controls, such as network monitoring tools, intrusion detection systems, and stringent data backup protocols. The incident revealed the need for proactive strategies that mitigate both the initial infection and the potential for widespread network compromise.
Mitigation Strategies Demonstrating Effectiveness
Several organizations have implemented security controls that effectively mitigated attacks using specific attack vectors. These strategies often involved a multi-layered approach, combining technical controls with human factors.For instance, companies might implement multi-factor authentication, which adds an extra layer of security beyond a simple username and password. This significantly reduces the risk of unauthorized access. Another example is robust endpoint detection and response (EDR) solutions that monitor systems for malicious activity.
These systems, coupled with security awareness training for employees, play a critical role in mitigating the impact of attacks.These case studies demonstrate that proactive measures, such as regular security audits, vulnerability assessments, and employee training, are crucial in preventing and mitigating cyberattacks. The effectiveness of security controls can be measured through their ability to detect and respond to threats, minimizing the impact on business operations.
Wrap-Up: Attack Vectors At A Glance
In conclusion, understanding attack vectors is paramount in today’s digital landscape. This exploration has illuminated the diverse range of methods used by attackers, from social engineering to sophisticated network breaches. Analyzing the potential impact of these attacks, coupled with effective mitigation strategies, is vital for safeguarding systems and data. By comprehending the intricacies of attack vectors, individuals and organizations can proactively bolster their security posture and effectively counter emerging threats.
Stay vigilant and informed.