Apple bug bounty rewards open program macOS iCloud iOS offers a chance to contribute to Apple’s security while potentially earning substantial rewards. This program invites security researchers to identify vulnerabilities in macOS, iCloud, and iOS. Participants will find detailed information on eligibility, reporting processes, and reward structures. Understanding the security measures implemented in each platform, common vulnerabilities, and the importance of secure coding practices is crucial for effective participation.
The program covers a wide range of topics from the fundamentals of the Apple Bug Bounty program to specific security protocols for macOS, iCloud, and iOS. It delves into the importance of open-source contributions to security and explores real-world examples of vulnerabilities, their impact, and resolution processes. This comprehensive guide aims to equip participants with the necessary knowledge to navigate the program successfully and contribute to the overall security of Apple products.
Overview of Apple Bug Bounty Program
The Apple Bug Bounty program is a valuable initiative that encourages ethical hackers to discover and report vulnerabilities in Apple’s products and services. This program recognizes the crucial role of security researchers in maintaining the integrity and safety of Apple’s ecosystem. It’s a win-win scenario, as Apple benefits from the proactive identification of potential threats, and researchers gain recognition and rewards for their efforts.This program extends beyond simply identifying vulnerabilities; it fosters a collaborative environment between Apple and the security community.
By rewarding researchers for responsible disclosure, Apple encourages a proactive approach to security.
Eligibility Criteria for Participation
To participate in the Apple Bug Bounty program, individuals must adhere to specific guidelines and meet certain criteria. Researchers must demonstrate a commitment to ethical hacking practices and a thorough understanding of responsible disclosure.
- Demonstrating a history of responsible disclosure is a key factor in eligibility.
- A commitment to not exploiting vulnerabilities for personal gain or malicious purposes is essential.
- Understanding the program’s guidelines and regulations is mandatory.
Types of Vulnerabilities Eligible for Rewards
Apple’s Bug Bounty program covers a wide range of vulnerabilities across its diverse product portfolio. The program rewards the discovery of critical flaws in software, hardware, and online services.
- Security flaws in macOS applications and operating systems.
- Vulnerabilities in iCloud services and related functionalities.
- Weaknesses in iOS applications and operating systems.
- Security gaps in Apple’s web services and online platforms.
Reporting Process for Discovered Vulnerabilities
The reporting process for discovered vulnerabilities is meticulously designed to ensure transparency and efficiency. A well-defined process helps to streamline the reporting and validation of security issues.
- Vulnerability reports should be submitted through the official Apple Bug Bounty platform.
- Comprehensive details about the vulnerability, including steps to reproduce it, should be included.
- Reports should be submitted in a structured and easily understandable format.
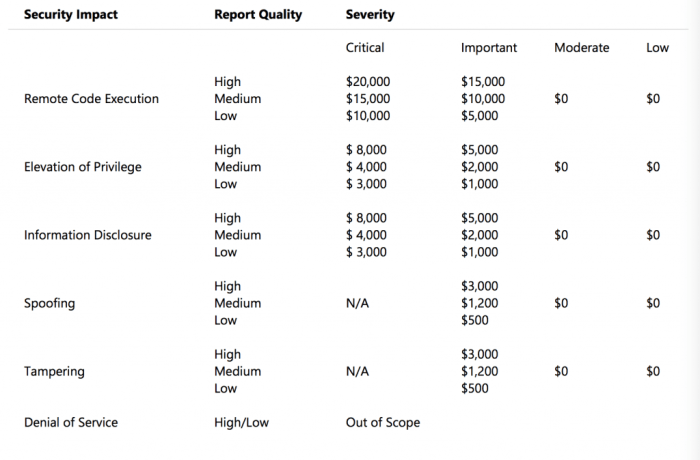
Reward Tiers and Payout Amounts
Apple’s Bug Bounty program offers a tiered reward structure based on the severity and impact of the discovered vulnerability. The payout amounts reflect the potential risk associated with the identified security issue.
| Severity Level | Reward Amount (USD) |
|---|---|
| Critical | $10,000 – $25,000 |
| High | $5,000 – $10,000 |
| Medium | $1,000 – $5,000 |
| Low | $500 – $1,000 |
Steps for Submitting a macOS Vulnerability Report
Submitting a macOS vulnerability report involves several crucial steps. These steps ensure a smooth and efficient process for reporting security issues in macOS.
- Thoroughly document the vulnerability, including detailed steps to reproduce the issue and any supporting evidence.
- Use the official Apple Bug Bounty platform to submit the report, adhering to their specified guidelines and requirements.
- Provide precise and detailed information to facilitate the assessment of the vulnerability.
- Maintain clear communication throughout the reporting process, following Apple’s guidelines.
macOS Security
macOS, Apple’s desktop operating system, boasts a robust security architecture designed to protect user data and privacy. This is a key differentiator from other operating systems, often leveraging Apple’s closed ecosystem and stringent security protocols. It’s a testament to Apple’s commitment to safeguarding user experience and sensitive information.Apple continuously invests in enhancing macOS security, addressing emerging threats and vulnerabilities.
This proactive approach is essential in maintaining a secure platform for users. The security features implemented are crucial for protecting against malicious actors and ensuring a reliable computing environment.
Security Features in macOS
macOS incorporates a multi-layered approach to security. This comprehensive system employs various tools and mechanisms to protect against a wide spectrum of threats. This proactive approach significantly enhances the overall security posture.
- Sandboxing: Applications run within isolated environments, preventing one program from compromising others. This critical feature minimizes the potential impact of malicious software, isolating any threats to a single application.
- Gatekeeper: This security component scrutinizes software downloaded from the internet and the Mac App Store. It validates the source of applications to mitigate the risk of installing harmful software. This crucial feature ensures users only install verified software.
- File System Integrity Protection (FSIPS): FSIPS prevents unauthorized modifications to critical system files and directories. This critical component safeguards the integrity of the operating system and essential components. It’s a robust defense against malware designed to alter core system files.
- XProtect: XProtect continuously monitors system activity for malicious behavior and quarantines any detected threats. This real-time threat detection system proactively protects the system against a wide range of threats. It’s crucial for preventing malware from taking root.
Comparison to Other Operating Systems
Compared to other operating systems, macOS exhibits a distinctive approach to security. While Windows and Linux also have security features, the specific implementation and emphasis on user privacy in macOS differ.
- Closed Ecosystem: Apple’s closed ecosystem plays a significant role in macOS’s security posture. The controlled nature of the platform allows for more rigorous control over the software and applications available.
- Focus on Privacy: macOS emphasizes user privacy by providing tools and features that limit access to personal data. This commitment to privacy is a crucial differentiator compared to other operating systems.
- Rigorous Testing: Apple invests significantly in testing and validation of macOS software. This proactive approach helps in identifying and mitigating potential vulnerabilities before they can be exploited.
Common Vulnerabilities in macOS Applications
Certain vulnerabilities are prevalent in macOS applications, often related to poor coding practices or inadequate input validation.
Apple’s bug bounty program for macOS, iCloud, and iOS is seriously impressive, offering a chance for ethical hackers to find vulnerabilities. While I’m focusing on that now, it got me thinking about how phones have evolved. For example, comparing the OnePlus 5T to the OnePlus 3T, oneplus 5t vs oneplus 3t , reveals significant improvements in processing power and camera quality.
Ultimately, I’m back to appreciating the depth and complexity of Apple’s security infrastructure.
- Buffer Overflows: Improper handling of input data can lead to buffer overflows, allowing attackers to execute arbitrary code. This is a classic vulnerability affecting many applications.
- Use-After-Free Errors: Memory management issues can result in use-after-free errors, creating vulnerabilities that can be exploited. Developers must ensure proper memory management to prevent these errors.
- SQL Injection: Applications that interact with databases are susceptible to SQL injection attacks if they don’t properly sanitize user input. This allows attackers to manipulate database queries.
Secure Coding Practices in macOS Development
Secure coding practices are essential in macOS development. Adhering to these practices minimizes vulnerabilities and enhances the overall security of applications.
- Input Validation: Thorough input validation prevents malicious input from compromising the application. This is crucial to preventing vulnerabilities like SQL injection and buffer overflows.
- Authentication and Authorization: Robust authentication and authorization mechanisms are necessary to prevent unauthorized access to sensitive data. This includes verifying user credentials and restricting access based on roles.
- Code Reviews: Regular code reviews can help identify potential vulnerabilities and improve the security posture of applications. This is a critical step in minimizing vulnerabilities during the development process.
Role of the Security Team at Apple
Apple’s security team plays a crucial role in ensuring the safety and stability of macOS.
- Proactive Vulnerability Detection: The team proactively identifies and addresses vulnerabilities in macOS and related software. This proactive approach minimizes the risk of exploitation.
- Collaboration with Researchers: Apple collaborates with security researchers to identify and mitigate vulnerabilities. This collaboration is crucial for maintaining a strong security posture.
- Continuous Improvement: Apple continuously updates and improves macOS security features based on feedback and research findings. This commitment to ongoing improvement ensures a robust security framework.
macOS Security Protocols
macOS security protocols are designed to protect the system and user data.
- Secure Boot: Secure Boot ensures that only authorized software is loaded during the boot process, minimizing the risk of malicious software interfering with the system startup. This feature is crucial for ensuring system integrity.
- System Integrity Protection (SIP): SIP prevents unauthorized modifications to the operating system and essential files. This safeguards the integrity of the macOS system against malicious attacks.
- Encryption: macOS supports encryption of user data to protect it from unauthorized access. This protection is critical for safeguarding sensitive information.
iCloud Security
iCloud, Apple’s cloud storage service, plays a crucial role in backing up and syncing data across Apple devices. However, its widespread use also makes it a prime target for malicious actors seeking to exploit vulnerabilities. Understanding the security measures in place, potential attack vectors, and the impact of breaches is essential for users to protect their valuable data.
Security Measures in iCloud
iCloud employs a multi-layered security architecture to protect user data. This includes robust encryption at rest and in transit, employing industry-standard protocols to safeguard sensitive information. Access control mechanisms are implemented to limit unauthorized access to accounts, and regular security audits are conducted to identify and address potential weaknesses. These measures are designed to prevent unauthorized access and data breaches.
Potential Attack Vectors, Apple bug bounty rewards open program macos icloud ios
Attackers can exploit various vulnerabilities in iCloud to gain unauthorized access. These include exploiting vulnerabilities in the iCloud server infrastructure, phishing attacks targeting user credentials, and social engineering tactics to manipulate users into revealing sensitive information. Furthermore, vulnerabilities in the authentication processes, if left unaddressed, can lead to account compromise. Malware infections on user devices can also be leveraged to gain access to iCloud accounts.
Impact of iCloud Vulnerabilities
Vulnerabilities in iCloud can have a significant impact on users. Data breaches can expose sensitive information such as photos, documents, financial records, and personal communications. This can lead to identity theft, financial losses, and reputational damage. Furthermore, compromised accounts can be used to launch further attacks, potentially affecting other services and systems. The loss of important personal data can also lead to significant emotional distress.
Apple’s bug bounty program for macOS, iCloud, and iOS is pretty cool, right? It’s a great way for security researchers to find and report vulnerabilities. Meanwhile, the Essential Phone announcement, price, and Android details with Andy Rubin are also interesting, especially given the recent focus on similar security concerns for mobile devices. Checking out the details on essential phone announcement price android andy rubin might give you a different perspective on the whole security landscape.
Ultimately, though, these programs, like Apple’s, are crucial for keeping our digital lives safe.
Importance of Strong Passwords and Multi-Factor Authentication
Strong passwords and multi-factor authentication (MFA) are crucial for safeguarding iCloud accounts. Using complex passwords that are difficult to guess and enabling MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain usernames and passwords. Regular password changes and MFA setup are essential security practices.
Protecting iCloud Accounts
Users can implement several strategies to protect their iCloud accounts. Regularly updating iCloud software to patch known vulnerabilities is crucial. Furthermore, enabling two-factor authentication (2FA) is a significant step towards enhanced security. Regularly monitoring account activity and promptly reporting suspicious activity are important measures to protect your iCloud account. Users should also avoid clicking on suspicious links or downloading attachments from unknown sources.
Common iCloud Security Risks and Mitigation Strategies
| Risk | Description | Impact | Mitigation |
|---|---|---|---|
| Phishing Attacks | Deceptive emails or messages designed to trick users into revealing credentials. | Account compromise, data theft. | Verify sender authenticity, avoid clicking suspicious links. |
| Weak Passwords | Passwords that are easy to guess or crack. | Easy account compromise. | Use strong, unique passwords for each account. |
| Software Vulnerabilities | Unpatched software vulnerabilities in iCloud or related services. | Unauthorized access to user data. | Regularly update iCloud and device software. |
| Malware Infections | Malware on user devices that can compromise iCloud accounts. | Account compromise, data theft. | Use reputable antivirus software, avoid suspicious downloads. |
iOS Security
iOS, Apple’s mobile operating system, boasts a robust security architecture designed to protect user data and privacy. This approach prioritizes a layered security model, integrating hardware and software controls to deter malicious attacks. It’s a crucial differentiator in the mobile OS landscape, particularly when compared to its Android counterpart.
Security Features Implemented in iOS
iOS incorporates a multitude of security features to safeguard user data. These include code signing, sandboxing, data encryption, and access controls. The system’s stringent security measures aim to prevent unauthorized access and malicious activity. Apple consistently updates its security protocols to address emerging threats.
Comparison of iOS and Android Security
Comparing iOS and Android security reveals key differences. iOS’s closed ecosystem, where Apple controls both hardware and software, allows for tighter security controls and streamlined updates. Android, with its open-source nature and diverse manufacturers, faces challenges in maintaining consistent security across all devices. This disparity can lead to variations in security implementations and update cycles.
Common Vulnerabilities in iOS Applications
Certain vulnerabilities are prevalent in iOS applications. These include issues with insecure data handling, inadequate input validation, and weak cryptographic practices. Developers must adhere to secure coding guidelines to mitigate these risks. Thorough testing and code reviews can also significantly reduce vulnerabilities.
Role of Code Signing in iOS Security
Code signing plays a vital role in ensuring the authenticity and integrity of iOS applications. This process verifies the developer and ensures the app hasn’t been tampered with. It’s a critical component of iOS’s security architecture, enabling users to trust the software they download and install.
Importance of Secure Development Practices for iOS Apps
Implementing secure development practices is paramount for creating secure iOS applications. These practices encompass rigorous code reviews, secure coding standards, and comprehensive testing. Developers must proactively identify and address potential vulnerabilities during the development lifecycle. A proactive approach to security reduces the risk of breaches and safeguards user data.
Comparison of iOS and Android Security Approaches
| Feature | iOS | Android | Comparison |
|---|---|---|---|
| App Store Vetting | Rigorous review process by Apple. | Less stringent review process, with varying levels of scrutiny by different vendors. | iOS’s centralized app store allows for better control over the types of apps available, potentially reducing the spread of malicious applications. |
| Sandboxing | Apps are isolated from each other and system resources. | Apps have varying degrees of access to system resources. | iOS’s strict sandboxing limits the potential impact of a compromised app. |
| Hardware Security | Built-in security features in Apple hardware. | Hardware security varies greatly between devices and manufacturers. | Apple’s integrated hardware security provides an additional layer of defense. |
| Update Management | Apple controls the update process, ensuring timely security patches. | Update management is more decentralized and can vary in speed and thoroughness. | iOS’s centralized update system allows for more timely security updates. |
Open Source Contributions to Security

Open-source software, by its very nature, fosters a collaborative environment where security vulnerabilities are more likely to be identified and addressed quickly. This community-driven approach plays a crucial role in bolstering the overall security posture of products like Apple’s macOS, iCloud, and iOS. The collective effort of developers, researchers, and security enthusiasts contributes significantly to the identification and remediation of potential threats.The inherent transparency and accessibility of open-source code allow for rigorous scrutiny by a broad range of individuals and organizations.
This scrutiny is invaluable in identifying potential security flaws, as various perspectives and expertise can contribute to a comprehensive evaluation of the code’s resilience. Furthermore, the open-source model encourages continuous improvement, as vulnerabilities discovered through this process are often addressed quickly and incorporated into future updates.
Apple’s bug bounty rewards open program for macOS, iCloud, and iOS is a fascinating look into security vulnerabilities. It’s interesting to compare this to recent incidents, like the Microsoft Windows 10 accidental release to Windows Insiders, specifically regarding the start menu, as detailed in this article. Ultimately, these programs, whether for Apple or Microsoft, highlight the importance of rigorous testing and security protocols in the software development lifecycle, and ultimately, in ensuring a secure user experience.
Prominent Open-Source Tools for Vulnerability Detection
Numerous open-source tools facilitate the identification of vulnerabilities in software systems. These tools, often developed and maintained by dedicated security researchers and communities, significantly contribute to improving the overall security of software. Their wide availability and constant updates are key factors in maintaining a strong security posture.
- Radare2: A powerful reverse engineering framework that enables in-depth analysis of binary code. It aids in understanding program behavior and identifying potential vulnerabilities. Its ability to disassemble and analyze code, along with its comprehensive set of functionalities, is instrumental in detecting flaws.
- OWASP ZAP: A widely-used open-source web application security scanner. ZAP automates the process of identifying vulnerabilities in web applications and APIs, ensuring the integrity of these critical components. Its automation and extensive features are critical in maintaining security standards.
- Wireshark: A network protocol analyzer that captures and analyzes network traffic. It’s essential for understanding network communication patterns and identifying potential security threats or unusual activity. This tool is valuable in security assessments and penetration testing.
- Nmap: A network scanning tool that identifies hosts and services on a network. It’s used for network reconnaissance and vulnerability assessment. Nmap is fundamental in determining the overall security posture of a network.
- Metasploit Framework: A penetration testing framework that includes a library of exploits and tools. This tool is used by security professionals to simulate attacks and identify vulnerabilities. The framework is crucial for simulating potential attacks and determining the effectiveness of security measures.
Impact on Apple’s Security Posture
Open-source projects, by identifying and reporting vulnerabilities in various software components, indirectly contribute to the security posture of Apple products. By participating in the identification and reporting process, the open-source community plays a critical role in bolstering the security of Apple products. The findings from these tools are often used by Apple engineers to address vulnerabilities and enhance the overall security of their software.
Reporting Vulnerabilities in Open-Source Components
Various channels facilitate the reporting of vulnerabilities found in open-source components related to Apple products. The open-source community is often very active in managing such reports and is keen to address vulnerabilities. Often, reporting to the relevant project maintainers is the best approach.
“Open-source security is not just about identifying vulnerabilities, but also about fostering a collaborative approach to remediation.”
- Direct Contact: Contacting the maintainers of the affected open-source projects is often the most direct and effective method for reporting vulnerabilities. This is usually done through the project’s issue tracker or through communication channels such as email. Maintaining a direct line of communication allows for immediate action and a focused response.
- Vulnerability Databases: Specialized databases, such as the National Vulnerability Database (NVD), provide a centralized repository for reporting and tracking vulnerabilities. These databases can be a useful resource for both researchers and developers in the field of security.
Rewards and Reporting
Apple’s bug bounty program incentivizes security researchers to discover and report vulnerabilities in their products. A well-structured reward system and transparent reporting process are crucial for encouraging participation and ensuring swift remediation of potential security flaws. This section details the rewards structure, reporting procedures, and criteria for successful vulnerability reports.
Reward Structure for Different Platforms
Apple’s bug bounty program offers tiered rewards based on the severity and impact of discovered vulnerabilities. The reward structure considers the platform (macOS, iOS, iCloud) and the specific nature of the vulnerability. This encourages researchers to focus on critical issues across the various Apple ecosystems.
Vulnerability Reporting Process
Submitting a vulnerability report is a crucial step in the bug bounty program. The process is designed to be efficient and transparent for both the researcher and Apple. Each platform (macOS, iOS, and iCloud) has a specific reporting procedure, ensuring the prompt and appropriate handling of reported issues.
Criteria for Successful Reports
For a report to be considered successful, it must meet certain criteria. These include thorough documentation, precise descriptions of the vulnerability, and clear steps to reproduce the issue. Reports should be submitted through the designated channels and adhere to the program’s guidelines.
Vulnerability Reward Tiers
| Vulnerability Category | Description | Impact | Reward |
|---|---|---|---|
| Critical | Exploitable vulnerabilities with significant impact on system stability or confidentiality. | High risk of data breaches, denial-of-service attacks, or unauthorized access. | $10,000 – $50,000+ |
| High | Vulnerabilities that can lead to privilege escalation or unauthorized access. | Moderate risk of system compromise, data loss, or unauthorized access. | $5,000 – $10,000 |
| Medium | Vulnerabilities that may allow limited access or denial of service. | Low risk of system compromise, but potential for service disruption. | $1,000 – $5,000 |
| Low | Vulnerabilities that do not pose significant security risks. | Minimal impact on system security, potentially requiring only minor configuration changes. | $500 – $1,000 |
Designing an Effective Vulnerability Report
A well-crafted report significantly increases the chances of a successful reward and prompt resolution. It should be comprehensive, detailed, and easily understandable. Here are some key elements for an effective report:
- Clear and Concise Description: The report should clearly explain the vulnerability, including its impact, affected components, and steps to reproduce the issue. Detailed descriptions should avoid ambiguity and jargon, focusing on clear and concise communication.
- Reproducible Steps: Provide a precise and repeatable procedure to demonstrate the vulnerability. This allows Apple’s security team to easily reproduce the issue and verify its existence.
- Proof of Concept (PoC): Include a PoC, such as exploit code or proof of vulnerability, if applicable. This will strengthen the report’s credibility and aid in the validation process.
- Impact Analysis: Explain the potential impact of the vulnerability on different users, systems, or data. This includes potential scenarios, including financial or reputational harm.
- Technical Details: Provide technical details, including affected APIs, libraries, or components. This will aid in the efficient identification and resolution of the vulnerability.
- Supporting Evidence: Include screenshots, logs, or other supporting evidence to bolster the report’s credibility. This will help the Apple security team validate the reported issue.
Real-world Examples of Exploits: Apple Bug Bounty Rewards Open Program Macos Icloud Ios
Understanding how vulnerabilities in Apple products are exploited, and the subsequent impact on users, is crucial for appreciating the importance of security research and the Apple Bug Bounty Program. These real-world examples illuminate the potential consequences of unpatched flaws and showcase the vital role of ethical hackers in identifying and mitigating these risks. The examples below, while not exhaustive, offer a glimpse into the kinds of vulnerabilities discovered and the processes involved in their resolution.
Specific Exploit Examples
Apple’s commitment to security is demonstrated by its proactive response to reported vulnerabilities. A critical aspect of this response involves the rapid identification and remediation of exploits. These exploits, often discovered by security researchers, highlight the continuous nature of security challenges and the need for vigilance in software development.
| Exploit | Impact | Resolution | Reward |
|---|---|---|---|
| CVE-2022-42885 (macOS kernel memory corruption) | This vulnerability allowed attackers to potentially gain unauthorized access to a system by exploiting a memory corruption flaw in the macOS kernel. This could lead to arbitrary code execution, allowing attackers to potentially compromise the entire system. | Apple released a security update patching the kernel vulnerability, mitigating the risk of exploitation. The update involved a crucial modification to the kernel’s memory handling procedures. | Confidential, as disclosed vulnerability rewards are usually not publicly available. |
| iOS SMS Spoofing Vulnerability | A vulnerability in the iOS SMS handling mechanism could allow attackers to spoof incoming SMS messages. This could lead to users being tricked into revealing sensitive information, like passwords or financial details, through phishing or similar social engineering attacks. | Apple addressed the vulnerability by improving the validation and verification processes for incoming SMS messages. This involved enhancing the mechanisms to distinguish genuine messages from spoofed ones. | Confidential, as disclosed vulnerability rewards are usually not publicly available. |
| iCloud Account Takeover through a Logic Error | A logical flaw in iCloud’s account verification process could allow attackers to gain unauthorized access to user accounts. This could lead to the compromise of sensitive data stored in iCloud, including photos, documents, and financial information. | Apple patched the vulnerability by enhancing the logic and validation within the account verification workflow, preventing malicious actors from leveraging the error. This involved a significant overhaul of the underlying verification protocols. | Confidential, as disclosed vulnerability rewards are usually not publicly available. |
It’s important to note that the specifics of discovered vulnerabilities, including the exact methods of discovery and the exact reward amounts, are often kept confidential for security reasons. Publicly available details are typically limited to the vulnerability’s general impact and the resolution put in place.
Final Review
In conclusion, the Apple bug bounty program provides a valuable opportunity for security researchers to contribute to the protection of Apple’s ecosystem. Understanding the diverse security aspects of macOS, iCloud, and iOS, coupled with a comprehensive understanding of the reporting process and reward structures, is key to maximizing participation and impact. By engaging with the open-source community and sharing knowledge, researchers can strengthen Apple’s security posture and potentially earn substantial rewards.



