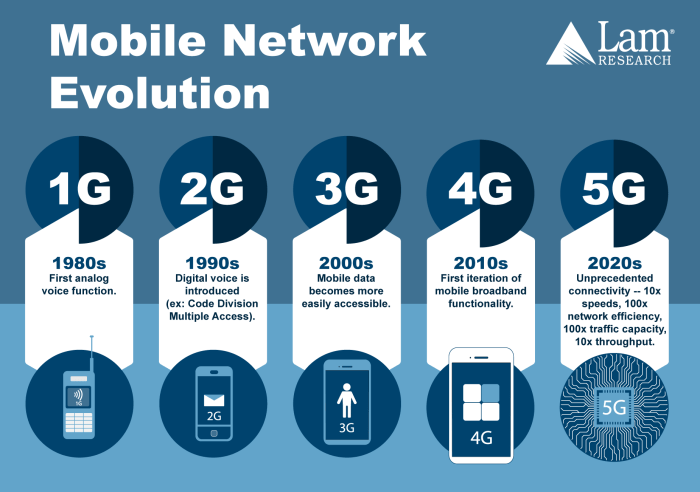
The evolution of modern networking challenges presents a fascinating journey through the ever-changing landscape of connectivity. From the early days of localized networks to the globalized, data-rich environments we inhabit today, the challenges have grown exponentially in complexity. This exploration delves into the historical context, emerging issues, and the crucial role of globalization, data, and security in shaping the future of networking.
This article examines the intricate interplay of technological advancements, global trends, and security concerns that define the modern networking landscape. It explores how factors like the Internet of Things (IoT) are reshaping our connected world, and the unique challenges this presents for different sectors.
Historical Context of Networking

The journey of modern networking is a fascinating tale of innovation and interconnectedness. From rudimentary systems connecting a handful of computers to the global network we rely on today, the evolution has been nothing short of remarkable. Understanding this history provides crucial context for navigating the complexities of today’s networks and anticipating future challenges.
Key Advancements in Networking Technologies
The development of networking technologies has been a gradual process, marked by significant milestones. Each advancement built upon the previous, leading to the sophisticated systems we use today. This evolution involved not only technological breakthroughs but also the development of crucial communication protocols.
| Date | Technology | Description | Impact |
|---|---|---|---|
| 1960s | ARPANET | The Advanced Research Projects Agency Network (ARPANET) was a pioneering packet-switching network. It served as the foundation for the internet, demonstrating the feasibility of connecting computers across vast distances. | Established the basis for internet communication, laying the groundwork for decentralized and robust network architecture. |
| 1970s | TCP/IP | The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols emerged, defining the fundamental rules for data transmission over networks. This standardization enabled diverse networks to communicate seamlessly. | Enabled interoperability between different networks, a crucial step towards global interconnectedness. The adoption of TCP/IP became the cornerstone of the internet’s architecture. |
| 1980s | Ethernet | Ethernet emerged as a dominant local area network (LAN) technology, enabling efficient communication within a confined area. | Revolutionized local network communication, making it faster and more accessible for businesses and institutions. |
| 1990s | World Wide Web | The World Wide Web, built upon TCP/IP and HTTP, made the internet accessible to a wider audience. | Brought the internet into the mainstream, opening doors for global communication, information sharing, and e-commerce. |
| 2000s | Wireless Networking | Wireless technologies like Wi-Fi and mobile networks expanded network accessibility and flexibility, allowing for mobile and remote connectivity. | Dramatically expanded network reach, making it accessible from virtually anywhere. Facilitated the rise of mobile computing and ubiquitous connectivity. |
| 2010s-present | Cloud Computing | Cloud computing technologies shifted computing power and data storage to centralized servers, enabling greater scalability and accessibility. | Enabled on-demand access to computing resources and applications, fundamentally changing how businesses and individuals interact with technology. |
Shift from Localized Networks to Global Interconnectedness
The transition from localized networks to global interconnectedness was a gradual but significant change. Initially, networks were confined to specific locations, serving limited purposes. The development of standardized protocols and advancements in hardware and software made global interconnectedness possible.
“The internet’s architecture, based on TCP/IP, allowed for seamless communication between diverse networks, paving the way for global interconnectedness.”
Evolution of Communication Protocols
Communication protocols are the set of rules that govern how data is transmitted and received over a network. Their evolution has been instrumental in the development of modern networking. Early protocols were simple and limited in scope, while modern protocols are complex and support a wide range of applications.
“The evolution of communication protocols, from simple to complex, has been a crucial factor in the development of modern networking.”
Early Networking Challenges and Their Solutions
Early networking faced various challenges. These challenges included limited bandwidth, lack of standardization, and security concerns. These issues were addressed through technological advancements, standardization efforts, and security protocols.
Emerging Challenges in Modern Networking
The digital world’s relentless expansion has dramatically increased the complexity and demands placed on modern networking infrastructure. This constant growth brings forth a multitude of challenges, ranging from the limitations of existing technologies to the ever-evolving threat landscape. Understanding these challenges is crucial for navigating the future of networking and ensuring its continued reliability and security.The limitations of current technologies, while providing impressive capabilities, are starting to show cracks under the weight of increasing data volumes, stringent latency requirements, and the proliferation of devices.
These constraints directly impact the efficiency and scalability of networks, potentially hindering innovation and the delivery of critical services. The rising tide of cyber threats further complicates the situation, demanding robust security measures to safeguard sensitive data and maintain network integrity.
Pressing Challenges in Infrastructure
Modern networking infrastructure faces numerous challenges, ranging from bandwidth limitations to the increasing complexity of managing diverse network elements. The escalating demand for data transfer and processing capacity strains existing infrastructure, potentially leading to network congestion and performance degradation. The sheer number of connected devices, particularly in the Internet of Things (IoT) era, further compounds this issue, creating a complex web of interactions that can be difficult to manage and secure.
Limitations of Current Technologies
Current networking technologies, while foundational, face limitations in scaling to meet the growing demands of modern applications. For example, traditional Ethernet protocols struggle to maintain low latency and high bandwidth for demanding applications like real-time video streaming or cloud gaming. The inherent limitations of these technologies can restrict the performance of critical services and hinder the development of future innovations.
Emerging Threats and Vulnerabilities
The digital landscape is constantly evolving, bringing with it a proliferation of emerging threats and vulnerabilities. Sophisticated cyberattacks are becoming increasingly sophisticated, exploiting vulnerabilities in network protocols and systems. The rise of ransomware and other malware poses significant risks to data integrity and network availability. Furthermore, the expanding attack surface, resulting from the interconnection of devices and systems, increases the potential for breaches and compromises.
Comparative Analysis of Security Risks, The evolution of modern networking challenges
Different networking models exhibit varying levels of security risk. For instance, cloud-based networks offer centralized management but can be susceptible to cloud-based attacks if proper security measures are not implemented. On the other hand, traditional on-premise networks provide greater control over security policies but often require significant capital investment and maintenance. A careful assessment of the specific security risks associated with each model is essential for implementing effective security strategies.
Networking Types and Vulnerabilities
- Wired Networks: Wired networks, while generally secure, are susceptible to physical breaches if not properly secured. Unauthorized access to physical infrastructure, such as cabling or network equipment, can compromise the entire network. Additionally, vulnerabilities within the hardware or software of the network devices themselves can lead to exploitation.
- Wireless Networks: Wireless networks offer greater mobility and flexibility but are more vulnerable to eavesdropping and unauthorized access. The use of encryption protocols, such as WPA2 and WPA3, is crucial to protect data transmitted over wireless channels. Compromised access points or weak encryption can expose the network to a wide range of threats.
- Cloud Networks: Cloud networks offer scalability and flexibility but require careful management of access controls and data encryption. Misconfigurations of cloud security settings can expose sensitive data to unauthorized access. The shared responsibility model between the cloud provider and the user necessitates careful attention to security best practices.
Vulnerability Analysis Table
| Networking Type | Primary Vulnerabilities | Mitigation Strategies |
|---|---|---|
| Wired Networks | Physical breaches, hardware/software vulnerabilities | Physical security measures, regular patching, strong access controls |
| Wireless Networks | Eavesdropping, unauthorized access, weak encryption | WPA3 encryption, strong passwords, access point security |
| Cloud Networks | Misconfigurations, cloud-based attacks, shared responsibility | Regular security audits, strict access controls, adherence to cloud provider guidelines |
The Impact of Globalization on Networking
Globalization has dramatically reshaped the landscape of modern networking. The interconnected nature of the world demands sophisticated and resilient networks capable of handling vast amounts of data and diverse communication protocols. This interconnectedness has introduced new challenges in terms of stability, security, and management.The interconnected global economy has driven a significant increase in the demand for high-bandwidth and low-latency networks.
Companies need to communicate seamlessly with partners and customers across the globe, demanding network infrastructures that can support this global reach. This translates to a need for more robust, reliable, and scalable network architectures.
Influence on Network Design and Implementation
Globalization has forced a paradigm shift in network design. Networks are no longer confined to national borders; they span continents. This necessitates the integration of diverse technologies and protocols, often involving multiple providers and jurisdictions. The focus has shifted from localized networks to distributed, interconnected systems. This has led to the development of sophisticated routing protocols and advanced network management tools capable of handling the complexity of globally dispersed networks.
Challenges of Maintaining Global Network Stability and Security
Maintaining global network stability and security is a significant challenge. Disruptions in one part of the world can quickly ripple through interconnected systems. Geopolitical events, natural disasters, and cyberattacks can all impact the reliability and security of global networks. Furthermore, the diversity of network infrastructure across the globe introduces vulnerabilities that need careful consideration. International collaborations are essential to mitigate these risks and ensure the robustness of global networks.
Increasing Complexity of Managing Diverse Networks and Protocols
Managing diverse networks and protocols poses significant challenges. Different countries and regions often employ various network technologies and standards. The heterogeneity of these networks requires sophisticated management tools that can monitor, troubleshoot, and optimize diverse infrastructures. Standardization is critical to streamline operations and ensure interoperability.
Modern networking challenges have evolved dramatically, from simple local area networks to complex global systems. This evolution has been fuelled by factors like the increasing reliance on cloud services, and the need for seamless connectivity across devices. For example, understanding how to leverage Xbox One Dev Mode Windows Apps, like those detailed on xbox one dev mode windows apps , can offer unique insights into the complexities of managing network traffic and resource allocation in today’s digital landscape.
This further highlights the constant need to adapt and innovate in the ever-changing world of modern networking.
Need for Standardized Protocols in a Globalized Environment
The need for standardized protocols in a globalized environment cannot be overstated. Interoperability between different networks is crucial for seamless communication and data exchange. Without standardized protocols, networks may not be able to communicate effectively, hindering collaboration and business transactions. International organizations play a pivotal role in developing and promoting these standards.
Role of International Collaborations in Addressing Networking Challenges
International collaborations are essential to address the networking challenges arising from globalization. Organizations like the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C) play a critical role in developing and maintaining standards. Such collaborations facilitate the sharing of best practices, the development of common solutions, and the addressing of security vulnerabilities in a coordinated manner.
Modern networking is constantly evolving, throwing up new hurdles. One key challenge, especially for businesses, is keeping up with shifting demands. Upgrading from a legacy G Suite free edition to Google Workspace, like legacy g suite free edition upgrade to google workspace , can significantly impact a company’s efficiency and security. This upgrade often solves connectivity and storage issues, but it’s crucial to consider the broader implications for the evolving networking landscape, which will always continue to change.
These collaborative efforts are crucial for the continued evolution and resilience of global networks.
The Role of Data in Modern Networking: The Evolution Of Modern Networking Challenges
The digital age is characterized by an unprecedented explosion of data. This relentless growth is fundamentally reshaping how we design, build, and utilize modern networks. From social media interactions to streaming video, data is the lifeblood of the internet, and its ever-increasing volume presents both exciting opportunities and formidable challenges. The sheer magnitude of this data demands innovative solutions to ensure efficient transmission, storage, and processing.The exponential growth of data significantly impacts network capacity and performance.
Modern networking challenges are constantly evolving, and staying ahead of the curve is crucial. One prime example of this is the recent SQL injection campaign that CrowdStrike successfully thwarted. Their proactive measures in stopping this attack highlight the ever-increasing need for robust security solutions to protect against these evolving threats, demonstrating how critical security measures are in the ongoing evolution of modern networking challenges.
how crowdstrike stopped an sql injection campaign shows just how important this is.
Networks are being pushed to their limits by the continuous influx of data from various sources. This surge in data volume necessitates upgrades to existing infrastructure, including faster transmission speeds and enhanced storage capabilities. Without these upgrades, networks can experience bottlenecks, slowdowns, and even complete failures, hindering the smooth operation of critical applications.
Data-Intensive Applications and Network Strain
Data-intensive applications, such as cloud computing, big data analytics, and video streaming services, place immense strain on network resources. These applications require substantial bandwidth to handle the constant transfer of large datasets, impacting network performance and reliability. For example, live video streaming platforms require high-speed connections to deliver video content in real-time to numerous users. Similarly, cloud storage services rely on robust networks to allow users to upload and download large files seamlessly.
The increasing demands of these data-intensive applications necessitate innovative approaches to network design and management.
Importance of High-Speed Data Transmission and Storage
High-speed data transmission is critical for supporting the demands of modern applications. The ability to transmit data quickly and efficiently is paramount for maintaining network performance. Similarly, robust storage solutions are essential to accommodate the growing volume of data. The increasing reliance on cloud storage and big data analytics necessitates the availability of reliable storage options that can handle massive datasets.
Failure to invest in high-speed transmission and storage technologies can result in significant performance issues and disruptions in critical services.
Different Data Transmission Methods and Their Efficiency
Various methods are employed to transmit data over networks, each with its own strengths and weaknesses in terms of speed, reliability, and cost. Understanding these methods is crucial for optimizing network performance and ensuring efficient data transfer.
| Data Transmission Method | Pros | Cons |
|---|---|---|
| Fiber Optics | Extremely high bandwidth, low error rate, long distances | Expensive installation, susceptible to physical damage |
| Copper Wire (Ethernet) | Relatively inexpensive, widely available | Lower bandwidth compared to fiber optics, higher error rate over longer distances |
| Wireless (Wi-Fi, Cellular) | Mobility, flexibility | Lower bandwidth, higher latency, security concerns, signal interference |
| Satellite | Global coverage, long distances | High latency, limited bandwidth, weather dependency |
Different data transmission methods have varying degrees of efficiency depending on the specific application and network requirements. Factors like distance, data volume, and desired latency play a crucial role in choosing the appropriate transmission method.
Security Concerns in Modern Networks
Modern networks, interwoven with countless devices and applications, are increasingly vulnerable to sophisticated cyber threats. The interconnected nature of these networks, while facilitating seamless communication and collaboration, creates new avenues for malicious actors to exploit vulnerabilities. This vulnerability necessitates a robust and proactive approach to network security, encompassing a layered defense strategy and constant adaptation to emerging threats.The escalating sophistication of cyberattacks, ranging from ransomware to phishing attempts, poses a significant challenge to maintaining the integrity and availability of network resources.
These attacks can cripple organizations, disrupt critical services, and cause substantial financial losses. Understanding the nature of these threats and the measures taken to counter them is crucial for effective network security management.
Growing Sophistication of Cyber Threats
The landscape of cyber threats is constantly evolving. Traditional security measures are often insufficient against advanced persistent threats (APTs), which are characterized by stealthy, long-term infiltration and exploitation of vulnerabilities. Sophisticated malware, often disguised as legitimate software, can infiltrate networks undetected for extended periods, leading to significant data breaches and operational disruption. For example, the SolarWinds attack demonstrated how seemingly trusted software updates can be exploited to gain widespread access to a network.
Furthermore, the rise of social engineering tactics, like phishing emails, exploits human weaknesses to gain unauthorized access, demonstrating the importance of user education and awareness programs.
Key Security Protocols and Measures
Protecting modern networks requires a multi-faceted approach that includes various security protocols and measures. These include firewalls, intrusion detection and prevention systems (IDS/IPS), antivirus software, and strong access controls. Regular software updates, patch management, and vulnerability assessments are essential for mitigating known weaknesses. The implementation of strong authentication mechanisms, such as multi-factor authentication (MFA), adds an extra layer of security, making it more difficult for unauthorized individuals to access network resources.
Furthermore, robust encryption protocols, such as Transport Layer Security (TLS), protect sensitive data during transmission, reducing the risk of interception.
Trade-offs Between Security and Performance
Implementing robust security measures can sometimes impact network performance. For instance, firewalls and intrusion detection systems may introduce latency or bandwidth consumption, potentially impacting the speed of data transfer. A carefully designed network architecture and the selection of appropriate security tools are crucial to minimizing these performance trade-offs. Balancing security requirements with performance needs is a critical aspect of network design, requiring a thorough understanding of the specific needs and constraints of the network.
Network Segmentation and Access Control
Network segmentation divides a network into smaller, isolated segments, limiting the impact of a security breach to a specific area. This isolation approach helps contain potential attacks and reduces the risk of widespread compromise. Access control mechanisms, including role-based access control (RBAC), restrict access to network resources based on user roles and privileges, preventing unauthorized individuals from accessing sensitive data or critical systems.
Implementing strict access control policies and regularly reviewing and updating them is essential for maintaining network security.
Layered Approach to Network Security
A layered approach to network security is essential for comprehensive protection. This model involves implementing multiple layers of defense, each with a specific role in securing the network. A robust network security architecture should include physical security measures, network security devices (firewalls, IDS/IPS), application security, and user education. Each layer provides a different level of protection and contributes to the overall security posture.
| Layer | Description |
|---|---|
| Physical Security | Protecting physical access to network equipment and infrastructure. |
| Network Security Devices | Employing firewalls, intrusion detection/prevention systems, and VPNs. |
| Application Security | Implementing security measures within applications and services. |
| User Education | Training users on security best practices and awareness. |
The Future of Networking
The digital landscape is rapidly evolving, and networking technologies are at the forefront of this transformation. From the ubiquitous connectivity of today to the interconnected future, networking is poised to play an even more critical role in our lives, shaping how we communicate, work, and interact. This evolution necessitates a robust understanding of emerging trends, the challenges ahead, and the potential advancements that will define the future of networking.The future of networking hinges on the integration of cutting-edge technologies, demanding resilient architectures, and a profound understanding of the complex data flows that will define our interconnected world.
We’re moving beyond simply connecting devices; we’re striving for intelligent, adaptive, and secure systems that seamlessly integrate into our daily lives.
Potential Advancements in Networking Technologies
The future of networking promises significant advancements in speed, efficiency, and reliability. We can expect to see a dramatic increase in bandwidth, enabling faster data transmission and supporting more demanding applications. Quantum networking, while still in its early stages, holds the potential to revolutionize communication, providing near-instantaneous data transfer. Moreover, advancements in optical fiber technology and wireless communication protocols will further enhance the performance and capabilities of networks.
The Role of Emerging Technologies
Emerging technologies like 5G, the Internet of Things (IoT), and Artificial Intelligence (AI) are reshaping the networking landscape. 5G’s high-speed, low-latency capabilities are essential for supporting real-time applications, such as augmented reality and virtual reality experiences. The proliferation of IoT devices necessitates robust network infrastructure capable of handling the massive influx of data generated by these devices. AI can be instrumental in optimizing network performance, proactively identifying and resolving potential issues, and enhancing security measures.
Robust and Resilient Network Architectures
Developing robust and resilient network architectures is crucial to ensuring network stability and security. Distributed architectures, leveraging multiple interconnected nodes, can improve fault tolerance. Redundancy in network components ensures continued operation even in the event of failures. Implementing advanced security protocols and intrusion detection systems is paramount to mitigating cyber threats and safeguarding sensitive data.
A Futuristic Network Environment
Imagine a future network environment where intelligent sensors and devices seamlessly communicate with each other, sharing data in real-time. This interconnected system could optimize traffic flow, predict potential issues, and even anticipate user needs. The network would be self-healing, proactively adapting to changing conditions and maintaining optimal performance. This concept transcends the physical boundaries of traditional networks, integrating seamlessly with our daily lives.
Potential Benefits and Challenges of Future Networking Solutions
Future networking solutions offer numerous benefits, including increased efficiency, enhanced security, and improved user experience. These solutions will enable new applications and services, revolutionizing industries and impacting society. However, challenges remain, such as the need for interoperability between different technologies, managing the vast amount of data generated by connected devices, and ensuring the security and privacy of sensitive information.
The complexity of these networks necessitates careful planning, robust design, and ongoing maintenance to realize their full potential.
Networking in Specific Sectors
Networking is no longer a generic utility; it’s a sector-specific necessity. Different industries demand different levels of performance, security, and accessibility. Understanding these nuanced requirements is crucial for developing effective and reliable network infrastructure. From the rapid data flow in finance to the sensitive patient information in healthcare, each sector presents its own set of unique challenges.
Healthcare Sector Challenges
The healthcare sector faces unique networking challenges due to the sensitive nature of patient data and the need for real-time access to critical information. Maintaining high availability and security is paramount. Real-time communication between medical devices, electronic health records (EHRs), and remote monitoring systems necessitates robust and reliable network infrastructure. Latency and data breaches are critical concerns.
Finance Sector Challenges
Financial institutions require high-speed, low-latency networks to process transactions, execute trades, and maintain financial stability. The speed and reliability of the network are crucial for preventing operational disruptions and maintaining customer confidence. Security is of utmost importance, with robust authentication and authorization protocols essential for preventing fraud and data breaches.
Education Sector Challenges
Educational institutions face the challenge of providing reliable network access for students and faculty, often with diverse and fluctuating needs. Providing high-bandwidth access for online learning, video conferencing, and collaborative tools is vital. Maintaining network security to protect sensitive student and educational data is critical.
Comparative Analysis of Networking Requirements
| Sector | Challenges | Solutions | Security Protocols |
|---|---|---|---|
| Healthcare | Data security, real-time access, high availability, integration of diverse devices | Dedicated, high-speed networks, cloud-based solutions, robust data encryption, secure access controls | HTTPS, VPNs, multi-factor authentication, encryption at rest and in transit |
| Finance | High-speed transactions, low latency, fraud prevention, regulatory compliance | High-performance networks, geographically distributed data centers, robust transaction processing systems, compliance with industry regulations | SSL/TLS encryption, intrusion detection systems, fraud monitoring, access control lists |
| Education | Scalability, bandwidth requirements, access control, data protection | Cloud-based learning platforms, high-bandwidth internet connections, access control systems, secure file sharing | Firewall protection, antivirus software, intrusion detection systems, strong password policies |
Networking and the Internet of Things (IoT)
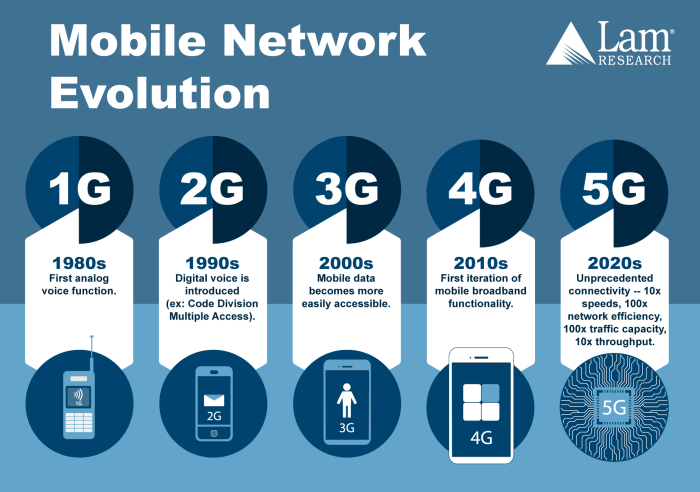
The Internet of Things (IoT) is rapidly transforming modern networking, connecting billions of devices and generating unprecedented amounts of data. This interconnectedness presents both exciting opportunities and significant challenges for network architects and security professionals. The increasing complexity of IoT networks requires a comprehensive understanding of their unique characteristics to ensure effective and secure operation.The IoT is no longer a futuristic concept but a present reality.
From smart homes and industrial automation to wearable devices and connected cars, the proliferation of IoT devices is reshaping how we interact with technology and the world around us. This connectivity brings significant benefits, but also introduces new vulnerabilities and operational complexities that must be addressed.
Influence of IoT Devices on Modern Networking
The integration of IoT devices fundamentally alters modern networking. These devices, often with limited processing power and memory, generate a vast volume of data that needs to be transmitted and processed. This influx necessitates significant network bandwidth and infrastructure upgrades. Furthermore, the diverse range of protocols and communication standards used by different IoT devices can create interoperability issues, demanding standardization efforts.
The heterogeneous nature of IoT devices further increases the complexity of network management and security.
Security Concerns in IoT Networks
IoT networks are particularly vulnerable to security threats due to their inherent characteristics. Many IoT devices have weak or default passwords, making them easy targets for hackers. The interconnected nature of these devices means a breach in one can potentially compromise the entire network. Lack of security updates and patches on older or less sophisticated devices exacerbates the vulnerability.
The potential for data breaches and unauthorized access to sensitive information necessitates robust security measures, including strong authentication, encryption, and intrusion detection systems. Furthermore, the lack of visibility and control over devices in large-scale deployments makes it difficult to detect and respond to attacks.
Scalability and Management Challenges of IoT Devices
Managing the sheer number of IoT devices presents a significant scalability challenge. The sheer volume of devices, each with unique communication requirements, demands robust network infrastructure. Managing the configuration, monitoring, and updating of these devices across different geographical locations is also complex. Centralized management platforms and automated deployment processes are crucial for effective management. The variety of operating systems and protocols used by these devices adds to the complexity.
Addressing these issues requires innovative solutions for device discovery, authentication, and overall network governance.
Role of Cloud Computing in Managing IoT Data and Resources
Cloud computing plays a crucial role in managing the massive amount of data generated by IoT devices. The cloud provides scalable storage and processing capabilities to handle the ever-increasing volume of data. Cloud platforms also facilitate remote device management, allowing for efficient updates, monitoring, and troubleshooting. This centralized approach streamlines the management of diverse IoT devices and data.
Cloud-based security solutions enhance the security posture of IoT networks.
Visual Representation of an IoT Network
A visual representation of an IoT network would show interconnected devices communicating with each other and a central hub (possibly a cloud-based server). Each device would be represented by a different shape or icon, reflecting its function. Connections between devices would depict the data flow and communication protocols. The network’s overall structure would showcase the interconnected nature of the IoT devices and their dependency on a robust network infrastructure. The visualization should also highlight the crucial role of cloud computing in handling and processing the data generated by these devices.
Final Wrap-Up
In conclusion, the evolution of modern networking challenges is a continuous process, demanding constant adaptation and innovation. From historical precedents to the future of 5G and AI, the dynamic interplay of technology, globalization, and security concerns will continue to shape our interconnected world. Understanding these challenges is crucial for building resilient, secure, and efficient networks that serve the needs of a globalized society.