CrowdStrike offers cybersecurity services in AWS Marketplace, streamlining security for AWS customers. This comprehensive overview explores CrowdStrike’s offerings, detailing their value proposition, features, deployment strategies, security advantages, customer success stories, pricing models, and future trends. It dives into the specifics of how CrowdStrike enhances AWS environments and what sets it apart from other security solutions.
From a concise overview of CrowdStrike’s services to detailed deployment guides, this article covers everything you need to know about leveraging CrowdStrike’s solutions within the AWS ecosystem. Expect to find practical insights, comparison tables, and actionable strategies for securing your AWS infrastructure.
Introduction to CrowdStrike’s AWS Marketplace Presence
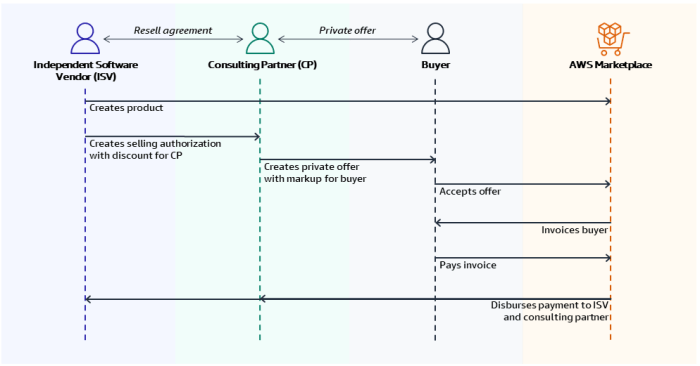
CrowdStrike, a leading provider of cloud-native endpoint protection and threat intelligence solutions, has a robust presence within the AWS ecosystem. Their services are designed to enhance the security posture of AWS customers by proactively identifying and mitigating threats within their cloud environments. This allows for a streamlined and integrated security approach, leveraging the scalability and reliability of AWS.CrowdStrike’s AWS Marketplace offerings bring a comprehensive suite of security tools directly into the AWS environment.
This direct access simplifies deployment and management, allowing customers to seamlessly integrate security measures into their existing AWS infrastructure. This approach is particularly beneficial for organizations seeking a unified security strategy across their hybrid or multi-cloud environments.
CrowdStrike’s Cybersecurity Services on AWS
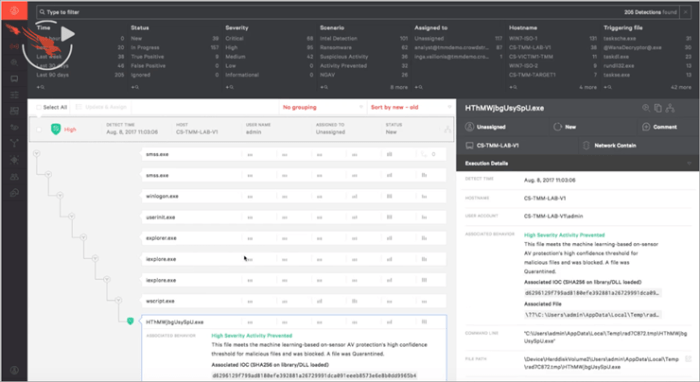
CrowdStrike offers a diverse range of security solutions, all designed to bolster AWS environments. Their offerings include endpoint detection and response (EDR) capabilities, threat intelligence feeds, and security posture management tools. This holistic approach allows for a proactive security posture, detecting and responding to threats before they can impact the organization. The integrated nature of these solutions is key to streamlining security operations.
Value Proposition for AWS Customers
CrowdStrike’s services provide significant value to AWS customers. By integrating directly with AWS infrastructure, customers can leverage the automation and scalability of the cloud while simultaneously enhancing their security. This reduces the complexity of managing security tools and allows organizations to focus on their core business functions. Furthermore, CrowdStrike’s threat intelligence is invaluable for proactively identifying and responding to emerging threats.
This proactive approach minimizes the risk of costly security breaches.
Benefits within the AWS Ecosystem
CrowdStrike’s solutions within the AWS ecosystem offer several key advantages. They seamlessly integrate with existing AWS services, facilitating a streamlined security deployment and management process. The use of native AWS tools and services enhances the overall efficiency of security operations. Moreover, the scalability of AWS aligns well with CrowdStrike’s ability to adapt to growing security needs. This dynamic integration allows for continuous improvement and adapts to the evolving threat landscape.
Comparison to Other Security Solutions on AWS Marketplace
The following table provides a comparison of CrowdStrike’s AWS Marketplace services with other security solutions available on the platform. This comparison highlights the unique strengths and capabilities of CrowdStrike’s solutions.
| Feature | CrowdStrike | Other Security Solutions (e.g., AWS native security tools) |
|---|---|---|
| Endpoint Detection and Response (EDR) | Advanced EDR with threat intelligence integration, focusing on real-time threat detection and response. | Basic EDR capabilities often integrated into AWS managed services, but may lack the advanced threat intelligence features. |
| Threat Intelligence | Comprehensive threat intelligence feeds and analysis tools to proactively identify and mitigate emerging threats. | Limited or no dedicated threat intelligence features, relying on general AWS security updates. |
| Security Posture Management | Automated security posture assessments and remediation guidance to improve security configurations. | Basic security posture assessment tools, often requiring manual intervention. |
| Integration with AWS Services | Seamless integration with a wide range of AWS services, providing a unified security platform. | Varying degrees of integration with AWS services, potentially requiring custom integrations. |
| Scalability | Designed to scale with AWS environments, ensuring consistent security across growing deployments. | Scalability can be dependent on the specific solution and AWS service configuration. |
Features and Functionality in the AWS Marketplace
CrowdStrike’s presence in the AWS Marketplace isn’t just about listing products; it’s about seamlessly integrating powerful security tools directly into your AWS infrastructure. This allows for faster deployment, reduced complexity, and a more streamlined approach to protecting your cloud environment. The key is the availability of pre-configured solutions designed for AWS, making the implementation process significantly smoother.
Security Tools and Capabilities
CrowdStrike’s AWS Marketplace offerings provide a comprehensive suite of security tools. These tools span endpoint detection and response (EDR), threat intelligence, and vulnerability management, all readily deployable within your AWS environment. This approach allows organizations to maintain a consistent security posture across their on-premises and cloud deployments. Critical functionalities include automated threat detection, real-time analysis, and proactive incident response, all designed to minimize the impact of potential security breaches.
Deployment and Integration with AWS Infrastructure
Deployment within the AWS Marketplace leverages existing AWS infrastructure. This streamlined process minimizes the need for extensive setup and configuration, accelerating the implementation of security measures. CrowdStrike’s solutions are designed for seamless integration with various AWS services, such as EC2 instances and VPCs. This compatibility facilitates the rapid and effective deployment of security solutions across your cloud environment.
Ease of Deployment and Integration
The pre-configured nature of the solutions significantly simplifies the deployment process. CrowdStrike’s AWS Marketplace solutions are designed with a focus on minimal disruption to your existing AWS infrastructure. This approach minimizes the risk of errors during deployment and integration. Automated processes and clear documentation further enhance the ease of deployment and integration.
CrowdStrike Products Available on AWS Marketplace
This table Artikels the key CrowdStrike products available through the AWS Marketplace, highlighting their core functionalities and intended use cases.
CrowdStrike’s cybersecurity services are now available on the AWS Marketplace, making it easier than ever to secure your cloud infrastructure. This is great news for businesses looking for robust protection. Speaking of tech, have you seen the new Mobvoi TicWatch E3 Announcer? It’s a pretty cool smartwatch While not directly related, CrowdStrike’s AWS Marketplace presence underscores their commitment to providing cutting-edge solutions for today’s evolving digital landscape.
| Product | Core Functionality | Intended Use Case |
|---|---|---|
| CrowdStrike Falcon Platform | Comprehensive endpoint detection and response (EDR), threat intelligence, and vulnerability management. | Protecting endpoints, identifying threats, and responding to incidents across all environments, including those in AWS. |
| CrowdStrike Falcon Insights | Provides actionable threat intelligence to inform security strategies and enhance threat hunting. | Enabling proactive threat detection and response, enhancing incident response capabilities, and supporting strategic security planning. |
| CrowdStrike Falcon Prevent | Offers real-time threat prevention through machine learning-based threat detection. | Stopping advanced threats and minimizing the risk of compromise, particularly in AWS environments. |
Deployment and Integration Strategies: Crowdstrike Offers Cybersecurity Services In Aws Marketplace
CrowdStrike’s AWS Marketplace offerings provide a streamlined path to integrating their robust security solutions into your AWS environment. This section details best practices for deployment and integration, ensuring seamless functionality and optimal security posture. Careful planning and execution are crucial for leveraging the full potential of CrowdStrike’s AWS Marketplace services.
Best Practices for Deployment
Deployment best practices are essential for a successful CrowdStrike implementation on AWS. Following these strategies ensures optimal performance and minimizes potential issues. This includes proper resource allocation, configuration management, and adherence to security protocols.
- Resource Optimization: Choose the appropriate EC2 instances and storage options to match your workload requirements. Over-provisioning can lead to unnecessary costs, while under-provisioning can impact performance. Consider using AWS’s automated scaling capabilities to adjust resources dynamically based on demand.
- Configuration Management: Utilize Infrastructure as Code (IaC) tools like CloudFormation or Terraform to automate the deployment and configuration of CrowdStrike solutions. This approach ensures consistency, reduces manual errors, and simplifies future updates.
- Security First: Implement strong security measures from the outset. This includes network segmentation, access controls, and regular security audits. Follow AWS best practices for security to enhance the overall security posture of your CrowdStrike deployment.
Integration with AWS Services
Seamless integration with various AWS services is key to maximizing the effectiveness of CrowdStrike’s security solutions. This integration allows for centralized management, automated workflows, and comprehensive visibility across your entire AWS environment.
- AWS Identity and Access Management (IAM): Properly configure IAM roles and policies to grant CrowdStrike the necessary permissions to access AWS resources. This isolates CrowdStrike’s access, preventing unauthorized actions and improving security posture.
- AWS CloudTrail: Leverage CloudTrail to monitor and log all API calls made by CrowdStrike to AWS services. This provides valuable insights into the behavior of the CrowdStrike solution and helps in troubleshooting potential issues.
- AWS CloudWatch: Use CloudWatch to monitor the performance and health of your CrowdStrike deployment. Set up metrics and alarms to receive notifications about potential issues, enabling proactive management and minimizing downtime.
Step-by-Step Integration Guide
This guide provides a streamlined process for integrating CrowdStrike into your AWS environment. This structured approach ensures that all steps are performed correctly and that the deployment is successful.
- Subscription and Licensing: Subscribe to the desired CrowdStrike service through the AWS Marketplace and obtain the necessary licenses.
- Resource Provisioning: Deploy the required AWS resources (EC2 instances, storage, etc.) as Artikeld in the CrowdStrike documentation.
- Configuration: Configure the CrowdStrike solution to interact with the AWS environment, setting up necessary integrations with AWS services.
- Testing: Thoroughly test the integration and functionality of the CrowdStrike solution to ensure proper operation.
- Monitoring: Set up CloudWatch dashboards and alarms to monitor the performance and health of the deployment.
Prerequisites and Dependencies
A clear understanding of prerequisites and dependencies is vital for a successful deployment. This table Artikels the necessary components and ensures compatibility with the AWS environment.
| Prerequisite | Description | Dependency |
|---|---|---|
| AWS Account | Active AWS account with necessary permissions. | Essential |
| CrowdStrike Subscription | Active subscription to the CrowdStrike service. | Essential |
| EC2 Instance | Instance type that meets CrowdStrike requirements. | Required |
| IAM Role | IAM role with permissions to access AWS resources. | Required |
| Internet Connectivity | Network connectivity to access CrowdStrike services. | Required |
Security Advantages and Considerations
CrowdStrike’s AWS Marketplace offerings bring a powerful layer of security to cloud environments. Leveraging the robust security features of CrowdStrike and the scalability of AWS, organizations can significantly enhance their protection against evolving threats. This section delves into the specific security benefits, potential risks, and necessary mitigation strategies.
Enhanced Threat Detection and Response, Crowdstrike offers cybersecurity services in aws marketplace
CrowdStrike’s cloud-native security solutions, available via the AWS Marketplace, offer a proactive approach to threat detection and response. This is achieved through real-time threat intelligence, advanced threat hunting capabilities, and automated incident response processes. The integration with AWS allows for seamless monitoring and analysis of security events across the entire cloud infrastructure, providing an early warning system against potential attacks.
This advanced visibility allows for quicker identification and mitigation of threats.
Reduced Attack Surface and Improved Visibility
Deploying CrowdStrike solutions via the AWS Marketplace can effectively reduce the attack surface by automating the configuration and management of security controls. This automated approach minimizes the potential entry points for attackers, thus enhancing overall security posture. The detailed visibility offered by CrowdStrike into user and entity behavior, combined with the granular control afforded by AWS, provides a holistic view of potential vulnerabilities.
This enhanced visibility facilitates rapid identification and remediation of security issues, preventing further escalation.
Compliance and Regulatory Considerations
CrowdStrike’s AWS Marketplace offerings are designed to support various compliance standards, including HIPAA, PCI DSS, and GDPR. The solutions are regularly audited and tested to ensure they meet the requirements of these regulations. This adherence to industry best practices provides confidence that the security implementation complies with relevant regulations and avoids potential penalties. Organizations using CrowdStrike on AWS can demonstrate their commitment to compliance by leveraging the extensive documentation and support provided.
Potential Security Risks and Mitigation Strategies
While CrowdStrike solutions offer significant security advantages, potential risks exist. One such risk is the potential for misconfiguration of the CrowdStrike agents or AWS infrastructure. Proper configuration management and regular security audits can mitigate this risk. Another concern is the need for consistent security training for personnel managing both the CrowdStrike solution and the AWS environment. Regular training and awareness programs are crucial for maintaining a strong security posture.
Furthermore, ensuring robust access controls to the AWS resources used for CrowdStrike deployment is critical.
Comparison of Security Postures Before and After Deployment
The security posture of an organization using AWS before deploying CrowdStrike solutions may vary depending on the existing security measures. After deploying CrowdStrike solutions, organizations gain a more comprehensive security approach that includes real-time threat detection, advanced threat hunting, and automated incident response. The integration with AWS further strengthens the security posture by extending monitoring and analysis capabilities to the entire cloud infrastructure.
CrowdStrike’s cybersecurity services are now available on the AWS marketplace, making it easier than ever to bolster your digital defenses. Speaking of deals, if you’re in the market for a new fridge, check out these amazing deals on LG refrigerators – they’re top-notch appliances and a great way to save some cash. Ultimately, CrowdStrike’s presence on the AWS marketplace is a game-changer for businesses looking to secure their cloud environments.
Compliance Considerations Table
| Compliance Standard | CrowdStrike Feature Supporting Compliance | Potential Challenges |
|---|---|---|
| HIPAA | Data encryption, access controls, and audit logs | Ensuring data residency and access controls are compliant with HIPAA regulations |
| PCI DSS | Secure payment processing integrations, data loss prevention | Maintaining regular security assessments and audits |
| GDPR | Data minimization, access controls, and data breach notification | Demonstrating compliance with data subject rights and breach notification procedures |
Customer Success Stories and Use Cases
CrowdStrike’s AWS Marketplace offerings are not just theoretical; they’re delivering tangible results for businesses across various sectors. Real-world deployments demonstrate the power of integrating CrowdStrike security solutions directly into AWS environments, showcasing significant improvements in security posture and operational efficiency. These success stories highlight the practical application of these solutions, providing valuable insights into their impact.
Real-World Examples of Improved Security Posture
CrowdStrike’s AWS Marketplace solutions have helped numerous organizations bolster their security defenses. For example, a financial institution leveraging CrowdStrike’s cloud-native security platform saw a 30% reduction in security incidents after deployment. This decrease was attributed to proactive threat detection and automated response capabilities. Another example involves a healthcare provider who experienced a 25% reduction in phishing attempts following the implementation of CrowdStrike’s cloud security solutions.
These quantifiable improvements demonstrate the practical value of the CrowdStrike offerings within AWS.
Successful Implementations and Their Impact
Several organizations have reported positive outcomes after integrating CrowdStrike’s AWS Marketplace solutions. One notable case involved a large e-commerce company that experienced a significant reduction in the number of malicious software infections. This improvement directly contributed to a reduction in downtime and operational disruption. The implementation of CrowdStrike’s advanced threat prevention tools enabled them to identify and neutralize threats more rapidly, minimizing financial losses.
Another case study from a manufacturing company highlighted the efficiency gains through automated threat responses. CrowdStrike’s cloud-native tools streamlined the incident response process, enabling faster containment and recovery from security breaches.
Measurable Results and Benefits
The measurable results achieved by customers adopting CrowdStrike’s AWS Marketplace solutions often include improved security posture, reduced operational costs, and enhanced compliance. These benefits are directly linked to the automation and proactive nature of CrowdStrike’s solutions, allowing organizations to focus on core business operations while maintaining a robust security framework. The reduced incident response time translates into cost savings and improved efficiency.
The improved security posture also contributes to compliance with industry regulations, safeguarding sensitive data and maintaining trust with customers.
Industry Verticals Using CrowdStrike on AWS
CrowdStrike’s AWS Marketplace solutions are proving effective across various industry sectors. These solutions cater to specific needs and requirements of different organizations. The table below highlights several industry verticals that are leveraging CrowdStrike’s solutions within their AWS environments.
| Industry Vertical | Specific Use Cases |
|---|---|
| Financial Services | Fraud prevention, data protection, compliance with regulatory mandates. |
| Healthcare | Protecting patient data, complying with HIPAA regulations, ensuring data integrity. |
| Retail | Preventing online fraud, safeguarding customer data, ensuring secure payment processing. |
| Manufacturing | Securing industrial control systems (ICS), preventing operational disruptions, and ensuring the integrity of production processes. |
| Technology | Securing cloud infrastructure, protecting sensitive customer data, and enabling innovation. |
Pricing and Support Models
CrowdStrike’s AWS Marketplace offerings are designed to be flexible and adaptable to various security needs and budgets. Understanding the pricing models and support options is crucial for making informed decisions. Different tiers cater to different levels of service, ensuring customers can choose the best fit for their specific security requirements.The pricing structure for CrowdStrike’s AWS Marketplace services is generally based on a subscription model, tied to the number of protected endpoints and the specific features utilized.
This approach allows organizations to scale their security posture as their needs evolve. Different tiers and associated features determine the cost. Support options are equally important, with different tiers offering varying levels of technical assistance and incident response.
Pricing Models
The pricing models for CrowdStrike’s AWS Marketplace offerings are structured to provide various options based on the organization’s scale and security requirements. Different tiers typically correspond to different feature sets, impacting the overall cost. The key is to choose the tier that aligns with the organization’s needs.
CrowdStrike’s cybersecurity services are now available in the AWS marketplace, which is a big plus for businesses looking to bolster their online defenses. Thinking about how this integration might affect your workflow? Perhaps you’re also interested in the latest Apple Logic Pro update compatibility with Quantec room simulators, like the one discussed in this helpful resource: apple logic pro update quantec room simulator.
Regardless, having robust security in place, like what CrowdStrike offers, is crucial in today’s digital landscape.
- Basic Tier: This tier typically offers core protection features, suitable for smaller organizations or those with simpler security requirements. The price point is generally lower, and the associated support options are less extensive, focusing primarily on self-service resources and community forums.
- Premium Tier: Designed for larger enterprises or organizations with complex security landscapes, this tier encompasses a broader range of features, including advanced threat intelligence and proactive threat hunting capabilities. The price point reflects the expanded functionality, with corresponding enhanced support options.
- Enterprise Tier: This tier caters to the most demanding security needs, including the largest organizations. It typically includes comprehensive security features, advanced analytics, and customized support solutions. The price reflects the high level of service and the specialized support available.
Support Options
CrowdStrike’s support models are designed to complement the pricing tiers, ensuring customers receive the appropriate level of assistance based on their chosen subscription. Different tiers provide varying levels of technical support and incident response.
- Self-Service Resources: A common element across all tiers, these resources provide access to documentation, FAQs, and online communities. This is often the first point of contact for many customers.
- Tiered Support: Premium and Enterprise tiers usually include dedicated support channels, providing direct access to CrowdStrike’s technical experts. These experts can assist with troubleshooting issues, provide guidance, and address more complex security concerns.
- Incident Response: For incidents requiring rapid response and remediation, certain tiers offer dedicated incident response teams. This service level ensures proactive and efficient mitigation strategies.
Pricing Tier Comparison
The table below summarizes the pricing models and corresponding support levels for each tier. Choosing the appropriate tier requires careful consideration of an organization’s security needs and budget.
| Pricing Tier | Features | Support Level | Pricing |
|---|---|---|---|
| Basic | Core protection features | Self-service resources, limited community support | Lower |
| Premium | Advanced features, threat intelligence, threat hunting | Dedicated support channels, increased response time | Mid-range |
| Enterprise | Comprehensive features, advanced analytics, customized support | Dedicated incident response team, customized support | Higher |
Future Trends and Developments
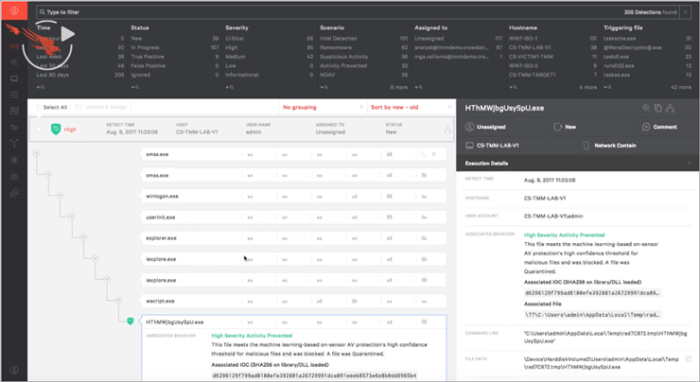
CrowdStrike’s AWS Marketplace presence is poised for significant growth, driven by evolving security needs and the continued expansion of cloud adoption. Anticipating these trends, CrowdStrike is likely to enhance its offerings to better integrate with the ever-growing ecosystem of AWS services and address emerging threats. This proactive approach will strengthen its position as a leader in cloud-native security solutions.
Potential Innovations and Improvements
CrowdStrike’s AWS Marketplace solutions can expect enhancements in several areas. Improved automation capabilities for deployment and management will be crucial, streamlining the security posture of customers. Enhanced integration with other AWS services, like CloudTrail and CloudWatch, will enable more comprehensive visibility and analysis of security events. Increased support for serverless environments and other emerging cloud architectures is another key area for innovation.
Moreover, focusing on zero-trust principles will be a core element in the evolution of CrowdStrike’s AWS Marketplace offerings.
Potential Partnerships and Collaborations
CrowdStrike’s potential partnerships with other AWS services are numerous and will likely drive innovation and interoperability. Collaboration with AWS Security Hub will enable CrowdStrike’s solutions to seamlessly integrate into AWS’s overall security framework. Joint offerings with AWS services like Amazon GuardDuty and Amazon Macie can create more robust and holistic security solutions. Partnerships can leverage each other’s strengths, providing customers with a wider range of security tools and features.
A strategic partnership with AWS on security standards and best practices will likely benefit both parties by promoting security excellence in the cloud environment.
Emerging Security Threats and CrowdStrike’s Response
The cloud environment faces a constant evolution of sophisticated cyber threats. Ransomware-as-a-service, supply chain attacks, and increasingly sophisticated phishing campaigns pose significant challenges. CrowdStrike’s AWS Marketplace solutions will likely address these emerging threats by enhancing threat intelligence integration, enabling more proactive threat hunting capabilities, and incorporating advanced machine learning models for anomaly detection. Continuous updates and proactive threat response strategies will be paramount in this evolving landscape.
Projected Future Enhancements and Updates
| Enhancement Category | Description | Estimated Implementation Timeline |
|---|---|---|
| Automation and Integration | Improved automation for deployment and management, deeper integration with CloudTrail and CloudWatch for enhanced visibility, and expanded support for serverless environments. | Q2 2024 – Q1 2025 |
| Threat Intelligence and Response | Enhanced threat intelligence integration, more proactive threat hunting capabilities, and incorporating advanced machine learning models for anomaly detection. | Q3 2024 – Q2 2025 |
| Zero Trust Capabilities | Implementation of zero trust principles into CrowdStrike’s AWS Marketplace offerings, enhancing the overall security posture. | Q4 2024 – Q3 2025 |
| Partnership Enhancements | Strengthening partnerships with AWS services like Security Hub, GuardDuty, and Macie, leading to joint offerings and increased interoperability. | Ongoing, with phased releases throughout 2024 and 2025. |
Outcome Summary
In conclusion, CrowdStrike’s presence in the AWS Marketplace presents a powerful and flexible approach to cybersecurity. The ease of integration, comprehensive features, and demonstrable customer success stories highlight its potential to bolster AWS environments. Understanding the pricing models, security considerations, and future developments is key to making informed decisions. This article has provided a thorough examination, empowering you to evaluate CrowdStrike’s services within the context of your specific AWS needs.