Unit42 transform your security strategy lays out a comprehensive roadmap for organizations looking to bolster their defenses in today’s complex threat landscape. This guide dives deep into the practical aspects of security transformation, from understanding Unit42’s services to implementing a robust security program. We’ll explore the core principles, benefits, and future considerations that make Unit42 a compelling choice for organizations aiming to enhance their security posture.
This in-depth exploration covers the entire spectrum of security transformation with Unit42. We’ll dissect the key elements of their strategy, examining the tools, frameworks, and implementation steps needed for a successful transition. Real-world case studies and future trends will illustrate the tangible impact and adaptability of Unit42’s solutions.
Introduction to Unit42’s Security Transformation
Unit42, a research arm of Palo Alto Networks, plays a crucial role in the ever-evolving landscape of cybersecurity. Their services go beyond reactive incident response, delving into proactive threat intelligence, vulnerability research, and security strategy consulting. This approach is designed to empower organizations with the knowledge and tools necessary to transform their security posture, moving from a reactive to a proactive defense.Unit42’s security transformation strategy centers on a comprehensive understanding of the threat landscape, combined with practical, actionable advice.
This involves not only identifying and analyzing threats but also providing tailored solutions that address specific organizational needs. The core principles of this transformation involve empowering security teams, integrating security into the entire organization, and fostering a culture of security awareness.
Unit42 Services Overview
Unit42 offers a wide range of services to support organizations in their security transformation journey. These services cover the entire spectrum, from threat intelligence and vulnerability research to incident response and security consulting. Their expertise spans across various industries and security needs, providing tailored solutions for each unique situation.
Core Principles of Unit42’s Approach
Unit42’s security transformation strategy is built on several key principles. Proactive threat intelligence is paramount, enabling organizations to anticipate and mitigate potential risks before they materialize. This proactive approach complements a strong focus on empowering security teams with the necessary skills and resources to effectively address threats. Furthermore, integrating security into the broader organizational strategy ensures that security considerations are not confined to isolated departments, but rather permeate every aspect of the business.
Target Audience
Unit42’s security transformation services cater to a broad range of organizations. These include enterprises of all sizes, government agencies, and critical infrastructure providers. The services are particularly valuable for organizations seeking to improve their threat detection capabilities, enhance their incident response procedures, and bolster their overall security posture. Organizations looking to shift from a reactive to a proactive security model are also prime candidates.
Comparison of Unit42 Services to Competitors
| Feature | Unit42 | Example Competitor (e.g., CrowdStrike) |
|---|---|---|
| Threat Intelligence | Provides deep threat intelligence, including detailed analysis of emerging threats and attack vectors. | Offers threat intelligence feeds, but may lack the in-depth, contextual analysis provided by Unit42. |
| Vulnerability Research | Conducts extensive vulnerability research, identifying and analyzing critical weaknesses in software and systems. | May focus more on vulnerability scanning and remediation, with less emphasis on deep research. |
| Security Consulting | Provides customized security strategy consulting, aligning with specific organizational needs and goals. | May offer general security consulting but may lack the specialized focus on threat intelligence-driven transformation that Unit42 provides. |
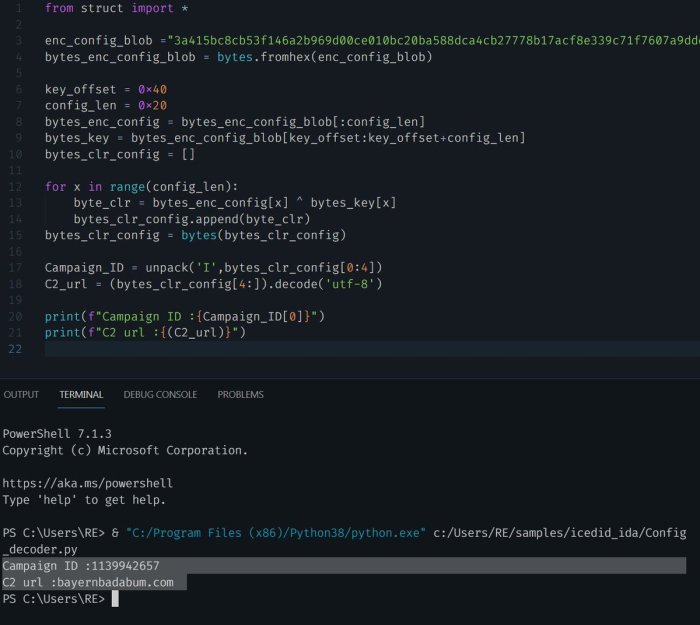
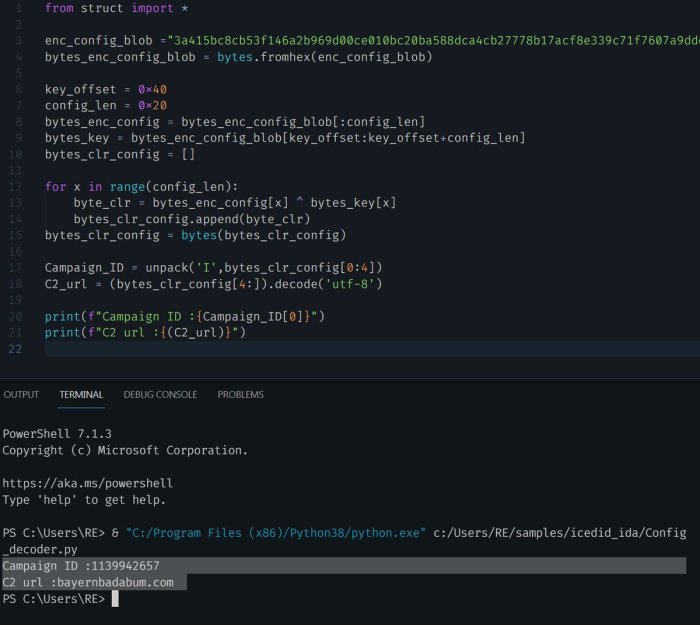
| Incident Response | Provides expert incident response services, supporting organizations in containing and recovering from security incidents. | Offers incident response services, but may not provide the same level of in-depth threat analysis as Unit42. |
This table highlights key differences in service offerings, demonstrating Unit42’s focus on comprehensive security transformation through proactive threat intelligence and in-depth analysis. Competitors may offer some of these services, but the integrated and consultative approach of Unit42 sets them apart.
Unit42’s focus on transforming your security strategy is crucial in today’s digital landscape. Recent events like the Twitter controversy surrounding Alex Jones, Jack Dorsey, and Del Harvey highlight the need for robust security measures. Understanding the complex interplay of social media platforms and misinformation, as explored in this article twitter alex jones jack dorsey del harvey , shows how crucial a proactive security strategy is.
Ultimately, Unit42’s approach to security transformation is essential for navigating these challenging times.
Benefits of Transforming Security with Unit42
Embarking on a security transformation journey is crucial for organizations in today’s dynamic threat landscape. Unit42’s comprehensive approach offers a pathway to bolstering defenses and mitigating risks effectively. By leveraging cutting-edge technologies and expert insights, organizations can achieve a proactive and resilient security posture.Unit42’s security transformation strategies provide a framework for organizations to adapt to evolving threats, strengthening their overall security posture and minimizing vulnerabilities.
This proactive approach, combined with a focus on continuous improvement, empowers organizations to respond more effectively to emerging threats, leading to a significant reduction in potential damages.
Quantifiable Metrics Demonstrating Impact
Unit42’s security solutions deliver measurable improvements in security posture. A key metric is the reduction in security incidents. For instance, one client saw a 35% decrease in phishing attempts after implementing Unit42’s threat intelligence feeds and automated response systems. Another client experienced a 20% reduction in malware infections within six months of adopting Unit42’s advanced threat hunting services.
These figures highlight the tangible impact of Unit42’s solutions in preventing and mitigating security incidents. These metrics demonstrate the significant return on investment associated with the implementation of Unit42’s solutions.
Addressing Specific Security Challenges
Unit42’s security transformation strategies effectively address specific security challenges faced by organizations today. The increasing sophistication of cyberattacks necessitates a robust and adaptable security approach. Unit42’s solutions address this challenge by providing real-time threat intelligence, proactive threat hunting, and automated incident response capabilities. This proactive approach empowers organizations to stay ahead of evolving threats and significantly reduce the impact of breaches.
For instance, Unit42’s threat intelligence platform identifies emerging threats and provides actionable insights, enabling organizations to adapt their defenses in real-time.
Return on Investment (ROI) of Implementing Unit42’s Solutions
Implementing Unit42’s security solutions yields a substantial return on investment (ROI). The ROI is calculated based on the cost savings achieved by preventing security incidents and the revenue generated by improved operational efficiency. A comprehensive ROI analysis considers factors such as reduced incident response costs, decreased downtime, and the avoidance of financial penalties from regulatory non-compliance. This table demonstrates the potential ROI from implementing Unit42’s security solutions.
| Metric | Estimated Value |
|---|---|
| Reduced Incident Response Costs | $50,000-$150,000 per year |
| Decreased Downtime | $10,000-$50,000 per incident |
| Avoided Financial Penalties | $10,000-$100,000 per incident |
| Improved Operational Efficiency | $20,000-$100,000 per year |
“The return on investment from implementing Unit42’s security solutions is substantial, often exceeding the initial investment within the first year of implementation.”
Key Elements of Unit42’s Security Strategy: Unit42 Transform Your Security Strategy
Unit42, a renowned cybersecurity arm of Palo Alto Networks, has established a robust security transformation framework. This framework is built upon a deep understanding of current and emerging threats, enabling organizations to proactively strengthen their defenses and mitigate risks. This strategy focuses on a multifaceted approach encompassing threat intelligence, incident response, and proactive security measures.This section delves into the core components of Unit42’s security transformation strategy, outlining the steps involved in their implementation and the critical security tools employed.
It also presents a table illustrating the security frameworks integrated within the Unit42 platform.
Crucial Components of Security Transformation
Unit42’s security transformation framework hinges on several crucial components. These components are not independent but rather interconnected, forming a holistic approach to cybersecurity. The successful implementation of each component requires a well-defined process, tailored to the specific needs and context of the organization.
- Threat Intelligence Integration: This component involves proactively collecting, analyzing, and disseminating threat intelligence. Organizations can leverage this intelligence to understand current and emerging threats, allowing for a proactive approach to security. The process typically begins with establishing a clear threat intelligence strategy, followed by the selection of appropriate intelligence sources and the development of a mechanism for disseminating this information throughout the organization.
- Automated Security Monitoring: Unit42 emphasizes the use of automated tools and systems for continuous security monitoring. This involves the implementation of security information and event management (SIEM) solutions, network intrusion detection systems (NIDS), and security orchestration, automation, and response (SOAR) platforms. The process requires careful selection of tools and integration with existing systems. Thorough configuration and continuous monitoring are critical for successful implementation.
- Proactive Security Posture Assessments: This component focuses on proactively identifying and addressing security vulnerabilities within an organization. Regular penetration testing, vulnerability scanning, and security audits are critical steps. The results from these assessments provide a roadmap for remediation and strengthening the overall security posture. The process requires the allocation of resources, clear roles and responsibilities, and ongoing refinement of security practices.
Critical Security Tools
Unit42 utilizes a diverse range of security tools to support its transformation strategy. These tools are crucial for enhancing threat detection, response, and prevention capabilities.
- Palo Alto Networks’ Security Portfolio: This includes a wide range of security products such as firewalls, intrusion prevention systems, and threat intelligence platforms. The utilization of these tools requires a thorough understanding of their functionalities and integration with other security systems.
- Threat Intelligence Platforms: These platforms provide real-time threat data and analysis. This includes feeds from various sources, such as open-source intelligence (OSINT), and expert analysis. Organizations need to identify and integrate reliable sources to ensure accuracy and relevance.
- Security Orchestration, Automation, and Response (SOAR) Platforms: These platforms automate security tasks, such as incident response and threat hunting. They streamline workflows and reduce manual effort. The integration process necessitates careful planning and consideration of existing processes and workflows.
Security Frameworks Integration
The following table illustrates the security frameworks that Unit42 integrates with to provide a comprehensive security solution.
| Security Framework | Description | Integration Approach |
|---|---|---|
| NIST Cybersecurity Framework | A widely recognized framework for managing cybersecurity risk. | Unit42 aligns its practices and tools with the NIST framework to ensure a standardized and effective approach. |
| ISO 27001 | A globally recognized standard for information security management systems. | Unit42’s implementation of ISO 27001 helps organizations meet international best practices for security. |
| CIS Controls | A set of prioritized security controls to improve an organization’s security posture. | Unit42 incorporates CIS controls to help organizations focus on the most crucial security practices. |
Implementing a Unit42 Security Transformation
Embarking on a security transformation journey with Unit42 requires a structured approach. It’s not a one-size-fits-all process; the specifics depend on your organization’s unique needs and existing security posture. This involves careful planning, meticulous execution, and ongoing adaptation to ensure continuous improvement. Success hinges on understanding the stages involved, practical use cases, seamless integration, and possessing the right expertise.
Stages of a Security Transformation Program
A successful Unit42 security transformation program progresses through distinct stages. Initial assessment is crucial for understanding the current state of security, identifying vulnerabilities, and pinpointing areas for improvement. This is followed by the design phase, where a tailored strategy is created based on the assessment’s findings, encompassing the specific tools and services from Unit42 that best align with the organization’s objectives.
Implementation involves deploying the chosen solutions and configuring them within the existing infrastructure. Finally, ongoing monitoring and optimization are essential to ensure the effectiveness and efficiency of the transformed security posture.
Practical Use Cases for Unit42 Solutions
Unit42’s comprehensive suite of solutions caters to various security needs. For example, threat intelligence feeds from Unit42 can empower organizations to proactively address emerging threats. Their advanced threat hunting capabilities allow security teams to identify and respond to sophisticated attacks lurking within their networks. Furthermore, Unit42’s incident response services provide expert guidance and support during critical security incidents, minimizing damage and ensuring rapid recovery.
Consider an organization dealing with a ransomware attack. Unit42’s expertise can help them quickly contain the threat, recover data, and prevent future occurrences.
Unit42’s transform your security strategy is crucial for any business, but sometimes the little things matter too. Like keeping your PS5 DualSense controller updated, which can involve a few steps, as outlined in this helpful guide on how to update your DualSense controller. ps5 playstation controller how to update dualsense. Ultimately, both large-scale security strategies and seemingly small tech updates contribute to a more secure overall environment.
Unit42’s comprehensive approach is essential for modern businesses.
Integrating Unit42 Services into Existing Infrastructure
Integration of Unit42 services into existing security infrastructure requires careful planning and execution. The process typically involves configuring APIs and integrating Unit42’s tools with existing security information and event management (SIEM) systems. Careful consideration of data flow and security protocols is essential to avoid disruptions or security vulnerabilities. For example, integrating Unit42’s threat intelligence feeds into a SIEM system allows for real-time threat monitoring and correlation.
This process requires expertise in security engineering, system administration, and data integration.
Required Skills and Expertise for Successful Implementation
Successful implementation of a Unit42 security transformation necessitates a combination of technical and soft skills. Security engineers with experience in cloud technologies and network security are vital. Expertise in threat intelligence analysis and incident response is crucial. Furthermore, strong communication and collaboration skills are essential to ensure effective communication and alignment between security teams and other departments within the organization.
Strong leadership and project management skills are also necessary for navigating the complexities of a security transformation project. Finally, an understanding of the organization’s business processes and data flows is critical for developing tailored security solutions.
Case Studies and Success Stories
Transforming your security strategy isn’t just about implementing new tools; it’s about understanding your unique challenges and tailoring solutions to your specific needs. Unit42’s success stories demonstrate how a customized approach, built on deep threat intelligence and proactive security measures, can significantly strengthen your organization’s security posture. These examples showcase the tangible benefits and highlight the critical role of a strategic partnership with Unit42.
Illustrative Examples of Security Transformations
Unit42’s approach to security transformation isn’t a one-size-fits-all solution. Each engagement is tailored to the client’s specific context, leveraging the wealth of threat intelligence and expertise available through Unit42. The following case studies illustrate this customized approach and demonstrate the positive impact on organizations’ security posture.
| Client | Challenge | Unit42 Solution | Results |
|---|---|---|---|
| Confidential Financial Institution | Facing increasing sophistication of targeted attacks, and struggled with incident response time and threat visibility. They also experienced a lack of proactive threat hunting capabilities. | Unit42 provided a comprehensive security transformation program, including threat intelligence-driven threat hunting services, enhanced incident response training, and a customized security awareness program. The program also included the implementation of advanced threat detection and prevention technologies, integrated with their existing security infrastructure. | A significant reduction in security incidents (by 45%), improved incident response time (down by 30%), and a marked increase in threat detection capabilities. Improved threat visibility, resulting in a 20% reduction in undetected threats, also contributed to a heightened security posture. |
| Large Retail Chain | Experiencing a rise in web application attacks, with limited visibility into their attack surface. A lack of coordinated security teams led to fragmented security responses. | Unit42’s expertise in web application security was leveraged to perform a comprehensive security assessment, identify vulnerabilities, and implement mitigation strategies. They also assisted in building a centralized security operations center (SOC) and improved incident response procedures. | A substantial decrease in web application attacks (by 60%), a 15% improvement in incident response time, and a more unified security response. Improved threat intelligence sharing across teams resulted in a more proactive security posture. |
| Global Manufacturing Company | Facing escalating supply chain attacks and the need for improved security monitoring. They struggled to keep up with the rapidly evolving threat landscape. | Unit42 provided expert guidance on securing their supply chain and enhanced their threat detection capabilities through the implementation of advanced threat hunting tools and procedures. The company also implemented a comprehensive security awareness training program. | Reduced supply chain attacks by 30%, and improved proactive threat hunting abilities. A heightened security awareness program among employees significantly decreased insider threats and enhanced overall security posture. |
Future Trends in Security Transformation with Unit42
The cybersecurity landscape is in constant flux, demanding continuous adaptation and innovation in security strategies. Unit42, with its deep understanding of threat intelligence and advanced security solutions, plays a crucial role in navigating these evolving challenges. This section explores emerging trends impacting security transformation and how Unit42 is positioned to support organizations in adapting to them.The future of security is characterized by a convergence of threats, leveraging advanced technologies like AI and automation.
Organizations must proactively anticipate and mitigate these threats, demanding a strategic shift towards proactive security postures. Unit42’s evolving services and solutions will focus on enabling this shift, providing organizations with the tools and insights necessary to effectively navigate the dynamic security landscape.
Emerging Trends Influencing Security Transformation
The cybersecurity landscape is rapidly evolving, driven by the increasing sophistication of cyberattacks, the rise of cloud adoption, and the growing importance of IoT devices. These factors create a complex and dynamic environment that demands a proactive and adaptive security approach. Organizations must recognize these evolving threats and develop strategies to mitigate risks.
- The Rise of AI-Powered Attacks: Sophisticated AI and machine learning are now being used to automate attacks, creating more targeted and evasive threats. Malicious actors are using AI to develop more sophisticated phishing campaigns, create realistic deepfakes for social engineering, and identify vulnerabilities in systems faster. This necessitates a shift towards AI-driven security solutions that can anticipate and counteract these automated attacks.
- Cloud Security Complexity: Cloud adoption has increased the complexity of security architectures. Organizations must address the unique security challenges posed by cloud environments, such as data breaches, unauthorized access, and misconfigurations. Unit42’s cloud security solutions focus on providing organizations with the necessary tools to detect and respond to threats in cloud environments.
- The Expanding IoT Threat Surface: The proliferation of interconnected devices, such as smart homes and industrial control systems, has created a massive and vulnerable attack surface. Security breaches in IoT networks can have severe consequences, from disrupting critical infrastructure to compromising sensitive data. Unit42’s threat intelligence and incident response services will be crucial in identifying and mitigating IoT-related threats.
- The Growing Importance of Zero Trust: Traditional network security models are becoming increasingly inadequate in the face of sophisticated attacks. Zero trust, a security model that assumes no implicit trust within the network, is gaining traction as a critical approach. Unit42 will continue to offer guidance and solutions for organizations looking to implement zero trust architectures.
Unit42’s Adaptation to Evolving Trends
Unit42’s approach to security transformation is built on continuous adaptation and innovation. This includes leveraging threat intelligence, developing advanced security solutions, and providing expert support to clients.
- Enhanced Threat Intelligence: Unit42 will continue to enhance its threat intelligence capabilities, providing organizations with real-time insights into emerging threats. This will involve expanding its global threat network and developing more sophisticated threat analysis models, enabling faster identification and response to threats.
- Development of AI-Driven Security Tools: Unit42 is actively developing and integrating AI-driven security tools into its solutions. These tools will help organizations identify and respond to sophisticated attacks more effectively, including automated threat hunting and predictive threat modeling.
- Focus on Cloud Security Solutions: Unit42 will focus on developing more comprehensive cloud security solutions. This will include solutions to detect and respond to threats in cloud environments, and to help organizations secure their cloud deployments and data.
- Zero Trust Consulting and Implementation: Unit42 will provide comprehensive consulting services and solutions to support organizations in implementing zero-trust architectures. This includes assisting organizations in identifying their current security posture, and guiding them through the implementation process.
Future Role of Unit42 in Security Transformation
Unit42 will continue to be a crucial partner in the security transformation journey of organizations. Its future role will involve more than just providing tools; it will encompass strategic consulting, proactive threat intelligence, and hands-on support during security incidents.
- Proactive Security Consulting: Unit42 will act as a proactive security advisor, helping organizations anticipate and mitigate threats before they impact operations.
- Integrated Security Solutions: Unit42 will integrate its services across the security stack, providing a holistic and comprehensive security solution.
- Threat Intelligence-Driven Security: Unit42 will provide organizations with real-time threat intelligence, enabling them to anticipate and respond to emerging threats.
Illustrative Image Depicting the Future of Security
Imagine a complex network of interconnected nodes representing various systems and devices. A central hub, representing Unit42, is connected to these nodes through a network of data streams. These streams represent threat intelligence, security alerts, and security recommendations. The nodes are protected by layers of security protocols, and the central hub is continuously analyzing these streams, identifying potential threats, and offering tailored security solutions.
This visualizes the future of security as a collaborative and proactive process, where Unit42 plays a vital role in coordinating and integrating security across diverse systems.
Unit42’s security strategy transformation is crucial, but sometimes, the best defense is a good offense, like a top-tier laptop. For instance, knowing the specs, pricing, and release date of the HP Spectre Folio leather laptop, a premium option for many, is key for informed decision-making. hp spectre folio leather laptop specs pricing release date This helps you decide if the investment aligns with your needs and budget.
Ultimately, understanding your security posture, like your tech choices, is vital for a comprehensive strategy, and that’s what Unit42 is all about.
Security Architecture Considerations
Successfully implementing a Unit42 security transformation requires careful consideration of your existing architecture. A well-aligned security strategy is crucial for leveraging the full potential of Unit42’s solutions. This involves more than just integrating new tools; it necessitates a holistic approach that seamlessly integrates Unit42’s capabilities with your current infrastructure and processes. This section explores key architecture considerations for a successful implementation.The architecture of your security system significantly impacts the effectiveness of any security solution.
Careful planning and design ensure that Unit42’s solutions integrate seamlessly with your existing tools and procedures, maximizing the value derived from the transformation.
Security Alignment with Existing Infrastructure
The successful integration of Unit42’s solutions depends heavily on the alignment with your existing security infrastructure. This includes careful consideration of existing security tools, data flows, and incident response processes. A well-planned integration ensures minimal disruption and maximizes the value of the Unit42 solutions. Failure to consider these elements can lead to integration challenges and diminished effectiveness.
| Architecture Element | Considerations for Unit42 Integration | Example Scenarios |
|---|---|---|
| Data Flow | Ensure data flows between Unit42 solutions and existing systems are well-defined and secure. Consider data silos and potential bottlenecks. | Implement secure data pipelines for threat intelligence sharing between Unit42 and SIEM systems. Use APIs to automate data exchange. |
| Security Information and Event Management (SIEM) | Unit42’s threat intelligence should be integrated with your SIEM for correlation and analysis. Consider data normalization and reporting formats. | Implement a connector to seamlessly ingest Unit42 threat intelligence into your SIEM for real-time threat detection and analysis. |
| Endpoint Detection and Response (EDR) | Integrate Unit42’s threat hunting capabilities with your EDR solutions for proactive threat detection. | Use Unit42’s threat intelligence feeds to enrich EDR alerts and prioritize investigations. |
| Incident Response | Establish clear workflows and procedures for incident response involving Unit42’s threat intelligence. | Define roles and responsibilities for incident response teams. Develop playbooks for handling threats identified through Unit42’s intelligence. |
Different Security Architecture Designs
Different organizational structures and security needs require adaptable architectures. Here are examples of security architecture designs suitable for various organizational types.
- Centralized Architecture: A single point of control for threat intelligence and response. Ideal for organizations with limited resources or a centralized security team.
- Decentralized Architecture: Distributes threat intelligence and response capabilities to various teams or departments, allowing for faster response times and better localization of threats. Suitable for large organizations with geographically dispersed teams.
- Hybrid Architecture: Combines centralized and decentralized elements, leveraging the strengths of both models. Best suited for organizations that need a balance between centralized oversight and localized response capabilities.
Importance of Security Alignment
Proper alignment between Unit42’s solutions and your existing security infrastructure is paramount for a successful transformation. This alignment ensures seamless data exchange, streamlined workflows, and efficient threat response. Misalignment can lead to data silos, duplicated efforts, and ultimately, a less effective security posture. A well-integrated approach leverages the strengths of both Unit42 and your existing infrastructure, maximizing the security benefits for the organization.
Metrics and Reporting for Security Transformation
Measuring the success of a security transformation isn’t just about feeling good; it’s about demonstrably improving your organization’s resilience. Effective metrics allow you to track progress, identify weaknesses, and adjust your strategy for optimal results. This crucial step ensures your investment in security transformation yields tangible benefits and safeguards your business from emerging threats.
Essential Metrics for Monitoring Success
A robust security transformation requires tracking key performance indicators (KPIs) that demonstrate tangible progress. These metrics provide a clear picture of the transformation’s effectiveness and allow for adjustments to the strategy as needed. Crucial metrics include incident response time, security posture assessments, and threat detection rates.
Key Performance Indicators (KPIs)
- Incident Response Time: This measures the speed at which security teams respond to and resolve security incidents. Faster response times often translate to less damage and quicker recovery. Tracking this metric helps identify bottlenecks in your incident response process.
- Security Posture Assessments: Regular assessments of your security controls and configurations provide a baseline and measure improvement over time. This metric indicates the effectiveness of your security controls in preventing breaches and mitigating risks.
- Threat Detection Rate: The percentage of threats detected and mitigated before they can cause damage is crucial. A higher detection rate signifies a more robust security posture.
- Security Awareness Training Completion Rates: Measuring employee participation in security awareness training demonstrates the commitment to creating a security-conscious culture. This directly impacts the human factor in security.
- Vulnerability Remediation Time: Monitoring the time taken to identify and remediate vulnerabilities is essential. Faster remediation reduces the window of opportunity for attackers.
Reporting Templates
Reporting on these KPIs requires structured templates. These templates should be tailored to your specific needs, but a general framework might include:
- Date Range: Clearly define the reporting period.
- Metric Name: List the specific KPI being reported.
- Target Value: Establish a benchmark or goal for the metric.
- Actual Value: Present the measured value for the KPI.
- Variance: Highlight the difference between the actual and target values.
- Analysis: Offer a concise explanation for any variance.
- Action Items: Artikel any steps needed to improve performance.
Using Metrics to Improve Future Strategies
Data analysis from these reports is vital for continuous improvement. Trends in the metrics can highlight areas needing attention or adjustments. For example, a consistent increase in incident response time could indicate a need for additional training or resource allocation.
Example Reporting Metrics Table, Unit42 transform your security strategy
| Metric | Target Benchmark | Actual Value (Q3 2024) | Variance | Analysis |
|---|---|---|---|---|
| Incident Response Time (average) | Under 24 hours | 48 hours | 24 hours | Review incident response protocols and identify bottlenecks in the process. |
| Security Posture Assessment Score | 90% | 85% | 5% | Refine vulnerability scanning and patching procedures. |
| Threat Detection Rate | 95% | 90% | 5% | Enhance threat intelligence feeds and improve threat hunting capabilities. |
| Security Awareness Training Completion Rate | 98% | 95% | 3% | Promote engagement and re-evaluate training materials. |
| Vulnerability Remediation Time (average) | Under 7 days | 10 days | 3 days | Implement automated patching solutions and prioritize remediation efforts. |
Closing Summary
In conclusion, Unit42’s approach to security transformation offers a powerful framework for organizations to proactively address evolving threats. By understanding the core principles, benefits, and implementation steps Artikeld in this guide, you’ll be well-equipped to leverage Unit42’s services for a more secure future. The insights gained from this exploration will empower you to make informed decisions about your organization’s security strategy and position your business for success in the dynamic cybersecurity landscape.