SASE securing private apps design guide provides a comprehensive roadmap for building secure and reliable private applications in today’s dynamic digital landscape. This guide delves into the critical aspects of secure application design, from foundational principles to advanced implementation strategies. It explores the integration of SASE (Secure Access Service Edge) into the design process for private applications, highlighting its benefits and practical applications.
We’ll cover everything from secure access control and authentication to continuous monitoring and incident response.
The guide will take you through a structured approach, examining security considerations at each stage of development, from initial design to ongoing maintenance. You’ll learn about common vulnerabilities and best practices for securing private applications, along with real-world case studies and future trends in the field. It’s a practical guide for anyone looking to build or enhance the security of their private applications.
Introduction to Secure Application Design
Secure application design is not an afterthought; it’s a fundamental principle that must be integrated into every stage of the development lifecycle. A robust security posture prevents vulnerabilities from emerging and reduces the likelihood of breaches. Prioritizing security from the outset saves time, resources, and ultimately, protects the application and its users from potential harm.By proactively addressing security concerns during the design phase, developers can create applications that are more resistant to attacks and maintain user trust.
This proactive approach ensures that security is not an added burden but rather an inherent aspect of the application’s architecture.
Key Principles of Secure Application Design
Secure application design principles encompass a broad range of considerations, from input validation to access control. These principles are crucial for creating applications that are resistant to various threats. Adherence to these principles ensures the development of applications that safeguard sensitive data and maintain user trust.
- Input Validation: Rigorous validation of all user inputs is paramount. This prevents malicious code injection and data manipulation. Input validation should not rely solely on client-side checks; server-side validation is critical to ensure data integrity.
- Least Privilege: Granting users and processes only the necessary permissions to perform their tasks is essential. This limits the potential damage from compromised accounts or unauthorized access.
- Secure Defaults: Designing applications with secure defaults minimizes attack surfaces. For instance, disabling unnecessary features or protocols by default significantly reduces the potential for vulnerabilities.
- Principle of Fail-Safe Defaults: When applications encounter unexpected conditions, they should revert to a secure state. This ensures that in case of errors or failures, the application remains secure.
Importance of Security in the Design Phase
Security concerns are not just technical details; they are critical for the overall success of an application. Addressing security early in the design phase helps avoid costly and time-consuming fixes later. It also helps build user trust and protects the reputation of the organization.Integrating security into the design phase prevents costly vulnerabilities and reduces the risk of costly data breaches.
It also improves the overall application quality and ensures long-term maintainability.
Best Practices for Secure Application Design
Following best practices during application design is crucial for building secure applications. These practices ensure the application is well-structured, well-maintained, and resilient to various security threats.
- Modular Design: Breaking down the application into smaller, independent modules promotes better code organization and easier maintenance, and aids in isolating vulnerabilities.
- Security by Design: Incorporating security considerations from the initial stages of design ensures security is not an afterthought but an integral part of the application architecture.
- Threat Modeling: Identifying potential threats and vulnerabilities early in the design process allows for proactive mitigation strategies.
Relationship Between Application Design and Security
Application design and security are intrinsically linked. A well-designed application is inherently more secure. The architecture, components, and data flow should be designed with security in mind.
- Security-Conscious Architecture: The overall architecture of the application should be designed with security in mind, incorporating security mechanisms and controls into the core design.
- Data Protection Design: The handling and protection of sensitive data must be prioritized. Secure data storage and transmission mechanisms should be incorporated into the design.
Security Considerations Across Development Stages
A structured approach to security is crucial throughout the application development lifecycle.
| Development Stage | Key Security Considerations |
|---|---|
| Design | Threat modeling, secure architecture, data protection, access control |
| Implementation | Secure coding practices, input validation, error handling, authentication/authorization |
| Testing | Penetration testing, vulnerability scanning, security audits, code review |
| Deployment | Secure infrastructure, access control, regular updates, monitoring |
Understanding SASE
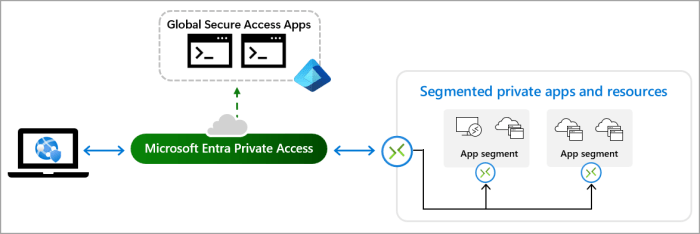
SASE, or Secure Access Service Edge, is rapidly reshaping the landscape of network security, particularly for private applications. Traditional perimeter-based security models struggle to adapt to today’s hybrid and cloud-first environments. SASE offers a unified approach, bringing together security and networking capabilities into a cloud-native architecture, significantly enhancing security for private applications.SASE addresses the inherent vulnerabilities that arise when private applications are accessed from various locations and devices.
This comprehensive approach is crucial for organizations that are committed to protecting their data and applications from evolving threats.
Designing secure access solutions for private apps, or SASE, is crucial. A recent security breach involving plaintext password reset emails for Slack on Android devices, detailed in slack android psa password reset email plaintext , highlights the need for robust security protocols. Implementing SASE best practices, like multi-factor authentication and encrypted communication channels, is vital for protecting sensitive data within private applications.
SASE Definition in Private Application Context
SASE, in the context of private applications, is a cloud-delivered security platform that provides a unified framework for securing access to these applications from anywhere. It extends security beyond the traditional network perimeter, enabling secure access to private applications over any network, whether on-premises, in the cloud, or across a hybrid environment. This approach eliminates the need for disparate security tools, creating a streamlined and integrated solution for protecting private applications.
SASE Enhanced Security for Private Applications, Sase securing private apps design guide
SASE enhances security for private applications by combining network functions like SD-WAN, Firewall, and Zero Trust Network Access (ZTNA) into a single platform. This unified approach allows for centralized policy management and enforcement, enabling organizations to apply security policies consistently across all access points. By automating security and networking tasks, SASE reduces manual intervention and human error, which can be a significant security vulnerability.
It also enables dynamic policy enforcement based on user, device, and application context, providing a more granular and responsive security posture.
Benefits of SASE for Securing Private Apps
SASE offers numerous benefits for securing private applications, including:
- Improved Security Posture: Centralized management and automated security tasks lead to a stronger security posture by consistently applying security policies across all access points.
- Reduced Operational Complexity: Integrating security and networking functions into a single platform reduces the complexity of managing multiple security tools.
- Increased Agility and Scalability: Cloud-native architecture enables rapid deployment and scaling of security and networking resources, enabling organizations to quickly adapt to changing business needs and user demands.
- Enhanced User Experience: Secure access to applications from anywhere, regardless of location or device, provides a more seamless and consistent user experience.
Key Components of a SASE Architecture Relevant to Private App Security
A robust SASE architecture for private app security encompasses several key components:
- Secure Web Gateway (SWG): Provides web security and content filtering to protect against malicious websites and phishing attacks.
- Cloud Access Security Broker (CASB): Enforces security policies for cloud applications and data, helping protect sensitive information accessed via cloud services.
- SD-WAN: Provides secure and optimized connectivity for users and devices, regardless of location.
- Firewall: Controls network traffic, allowing authorized users and applications access while blocking unauthorized ones.
- Zero Trust Network Access (ZTNA): Ensures that only authorized users and applications can access private resources, regardless of their location.
Comparing Traditional and SASE Architectures for Private Apps
The following table contrasts traditional security architectures with SASE architectures, focusing on their suitability for private applications.
| Feature | Traditional Security Architecture | SASE Architecture |
|---|---|---|
| Security Model | Perimeter-based, relying on a defined network boundary | Zero Trust, access based on identity, device, and context |
| Network Connectivity | Separate network infrastructure for security and networking | Unified platform for security and networking |
| Scalability | Limited scalability due to infrastructure constraints | Highly scalable and adaptable to changing needs |
| Security Management | Decentralized, requiring separate management for each security tool | Centralized management for unified security policies |
| Cost | Higher cost due to multiple point solutions and maintenance | Potentially lower cost due to unified platform and automation |
| Flexibility | Less flexible in adapting to hybrid and cloud environments | Highly flexible and adaptable to various environments |
Securing Private Applications
Private applications, often handling sensitive data and critical business functions, demand robust security measures. These applications, whether internal tools or customer-facing platforms, must be protected from various threats. This section delves into common vulnerabilities, effective security strategies, and crucial authentication and authorization methods for private applications. Proper implementation of secure coding practices is also essential to mitigate risks.Modern organizations increasingly rely on private applications for their core operations.
These applications often house sensitive data, including financial information, intellectual property, and customer details. Without adequate security measures, these applications become vulnerable to breaches, leading to data loss, financial penalties, and reputational damage. Therefore, prioritizing security from the design phase is paramount.
Common Security Vulnerabilities in Private Applications
Private applications face a range of potential security vulnerabilities. These include insecure direct object referencing, SQL injection, cross-site scripting (XSS), and insufficient authorization. Insecure direct object referencing, for example, can allow attackers to access resources they shouldn’t, while SQL injection allows malicious code to be injected into database queries. These vulnerabilities, if left unaddressed, can severely compromise the integrity and confidentiality of the application.
Security Measures for Protecting Private Apps
Robust security measures are essential to mitigate vulnerabilities and protect private applications. These include implementing input validation to prevent malicious code injection, using parameterized queries for database interactions, and enforcing strong access controls. Furthermore, regular security audits and penetration testing can identify potential weaknesses and ensure ongoing protection. This proactive approach helps maintain a strong security posture.
Authentication and Authorization Mechanisms for Private Applications
Secure authentication and authorization are critical components of protecting private applications. Multi-factor authentication (MFA) adds a layer of security by requiring multiple forms of verification, such as a password and a one-time code. Role-based access control (RBAC) ensures that users only have access to the resources they need, minimizing the impact of a potential breach. These measures significantly strengthen the overall security posture.
Secure Coding Practices for Private Applications
Secure coding practices are crucial for preventing vulnerabilities from being introduced into private applications during development. Developers should adhere to established coding guidelines, including input validation, output encoding, and secure handling of sensitive data. Regular code reviews can identify and fix potential vulnerabilities before they are deployed.
Designing a secure access service edge (SASE) solution for private applications requires careful planning. A key consideration is how to integrate your existing software-defined networking (SDN) and network firewalls, which can be simplified by using a service like the sd quickstart service for software ngfw terraform add on. Ultimately, a well-designed SASE strategy ensures secure access for all your applications, regardless of location or user.
Detailed Example of a Secure Login Process for a Private Application
A secure login process for a private application should include several critical steps. First, the application should use strong password hashing algorithms, such as bcrypt or Argon2, to store passwords securely. Second, the application should employ MFA to verify the user’s identity. Third, the application should implement input validation to prevent malicious input from compromising the login process.
Finally, the application should use HTTPS to encrypt the communication between the user and the application.For example, a login form would validate user input, using parameterized queries to prevent SQL injection. The password would be hashed using a strong algorithm before being stored in the database. Upon successful login, the application would issue a secure token to the user, which can then be used for subsequent authorized actions.
Designing for Private Application Security
Securing private applications requires a multifaceted approach that goes beyond simple perimeter defenses. Modern applications often rely on APIs, intricate data flows, and complex authentication mechanisms. This necessitates a design-centric security strategy, emphasizing proactive measures embedded within the application architecture. A robust security posture needs to consider not only access control but also data protection and the zero-trust principle.This section delves into the crucial design principles for securing private applications, providing a detailed example of a secure API design, highlighting the role of encryption, and outlining zero-trust implementation.
This SASE securing private apps design guide is crucial for modern businesses, but sometimes, the most important lesson comes from unexpected places. Just like you should learn to spot a flooded car and run the other way ( how to spot a flooded car and run the other way ), you need to be mindful of potential vulnerabilities in your private app architecture.
Solid design principles, like strong authentication and robust access controls, are key to a secure environment, so keep these best practices in mind as you review your SASE implementation.
Furthermore, it presents a practical table illustrating different access control methods.
Design Principles for Securing Access to Private Applications
Effective security starts with well-defined design principles. These principles should be woven into the application’s DNA, making security an inherent part of its functionality, not an afterthought. Prioritizing secure coding practices, enforcing strong authentication, and implementing granular access control are essential aspects of robust application security.
Secure API Design Example
A well-designed API for a private application should incorporate multiple security layers. For instance, consider an API for a financial application. The API endpoints should be meticulously designed to restrict access based on user roles and permissions.“`// Example API Endpoint (Conceptual)GET /account-balance?userId=123&apiKey=secretKey123“`This example demonstrates a secure API endpoint. The `userId` parameter ensures that only authorized users can access their account balance.
The `apiKey` is a crucial element for verifying the caller’s identity and preventing unauthorized access. Input validation is also paramount to prevent malicious code injection or manipulation. Error handling should be designed to provide informative responses without revealing sensitive information.
Role of Encryption in Securing Private Application Data
Encryption plays a pivotal role in protecting sensitive data traversing networks or stored within the application. Data encryption should be employed both in transit and at rest. Data encryption at rest protects stored data from unauthorized access, even if the storage system is compromised. Data encryption in transit ensures confidentiality during transmission. Modern encryption standards, such as AES-256, offer strong protection against potential breaches.
“Encryption protects sensitive data, both in transit and at rest, by converting it into an unreadable format.”
Zero-Trust Security Principles in Private Application Design
The zero-trust model is a crucial aspect of securing private applications. It assumes no implicit trust, regardless of the user’s location or network access. Every user, device, and application must be authenticated and authorized before gaining access to any resource within the private network. Zero-trust implementation mandates continuous monitoring and validation of access requests, significantly enhancing security posture.
Access Control Methods for Private Applications
Different access control methods offer various levels of granularity and security. The selection of an appropriate method depends on the specific application requirements and security posture.
| Access Control Method | Description | Pros | Cons |
|---|---|---|---|
| Role-Based Access Control (RBAC) | Access based on assigned roles | Simple to implement, scalable | May not be granular enough for complex applications |
| Attribute-Based Access Control (ABAC) | Access based on attributes | Highly granular, flexible | More complex to implement and manage |
| Rule-Based Access Control (RBAC) | Access based on predefined rules | Specific control over access | Requires careful rule definition and maintenance |
Implementing Secure Access
Securing access to private applications is paramount in today’s digital landscape. This crucial step safeguards sensitive data and ensures only authorized users can interact with critical resources. Effective implementation of secure access control relies on a multifaceted approach, integrating robust authentication mechanisms, secure session management, and a strong understanding of the applications’ specific needs. The SASE architecture, with its integrated security capabilities, plays a pivotal role in achieving this goal.Implementing secure access isn’t just about preventing unauthorized access; it’s about building a system that allows legitimate users to access resources effectively and securely.
This requires a thoughtful design that considers both the user experience and the security posture. A well-designed secure access system will balance user convenience with stringent security protocols.
Importance of Secure Access Control
Secure access control is fundamental to the integrity and confidentiality of private applications. It prevents unauthorized access, data breaches, and potential disruptions to service. Robust access control measures reduce the risk of insider threats and external attacks, protecting sensitive data and maintaining business continuity. Properly implemented secure access controls ensure only authorized users can access and manipulate critical resources, mitigating potential damage and legal liabilities.
Implementing Secure Access Using SASE
SASE architecture offers a powerful framework for implementing secure access. Its integrated approach allows for a unified security platform encompassing various security functions, including secure access service edge (SASE) capabilities. This unified approach streamlines the implementation and management of secure access, minimizing complexity and maximizing efficiency.A practical example involves a company using SASE to secure its internal application.
Users accessing the application through a secure virtual network (VPN) will be authenticated and authorized through the SASE platform. This authentication process verifies user identity and their rights to access specific resources. The SASE platform also enforces secure session management, such as session timeouts and secure communication protocols. The application itself can leverage SASE’s capabilities for granular access controls, ensuring only authorized users can interact with sensitive data.
Multi-Factor Authentication for Private Apps
Multi-factor authentication (MFA) significantly enhances the security posture of private applications. MFA adds an extra layer of security by requiring users to provide more than one form of identification. For example, a user might be prompted to enter a password and then provide a code from a dedicated authentication app. This dual authentication makes it considerably harder for attackers to gain access, even if they obtain a user’s password.
MFA provides a critical defense against password breaches, and is increasingly becoming a standard security practice for private application access.
Secure Session Management
Secure session management is crucial for maintaining the confidentiality and integrity of user interactions with private applications. It involves managing user sessions securely, including setting time limits, invalidating sessions upon logout, and encrypting session data. Employing these methods safeguards sensitive information and limits the window of opportunity for attackers to exploit vulnerabilities in the session.A robust session management system typically involves these key components:
- Session Timeouts: Automatically terminating inactive user sessions after a predetermined period to prevent unauthorized access if a user’s session is hijacked or compromised.
- Secure Communication Protocols: Utilizing encryption protocols such as TLS/SSL to protect session data from eavesdropping or tampering. This is critical for maintaining data confidentiality during transmission.
- Session Token Management: Implementing a robust system to manage session tokens, ensuring that tokens are generated securely and are regularly refreshed to reduce the impact of a compromised token.
Comparison of Secure Access Protocols
The following table contrasts various secure access protocols for private applications, highlighting their strengths and weaknesses.
| Protocol | Description | Security Strengths | Security Weaknesses |
|---|---|---|---|
| Secure Shell (SSH) | Used for secure remote login and command execution. | Strong encryption, secure tunneling. | Requires client-side configuration, potentially less user-friendly. |
| Virtual Private Network (VPN) | Creates a secure encrypted connection between a user’s device and a private network. | End-to-end encryption, protects data in transit. | Can be complex to configure and manage, performance overhead. |
| Secure Sockets Layer/Transport Layer Security (SSL/TLS) | Provides secure communication channels for web applications. | Encrypts data transmitted over the internet. | Vulnerable to man-in-the-middle attacks if not properly configured. |
Monitoring and Maintaining Security
Keeping your private applications secure isn’t a one-time task; it’s an ongoing process. Regular monitoring and proactive maintenance are crucial to identify vulnerabilities and respond effectively to threats. A robust security posture requires continuous vigilance and a well-defined incident response plan. This section details essential strategies for maintaining the integrity and confidentiality of your private applications.
Continuous Security Monitoring
Continuous monitoring is essential for proactively identifying and addressing security threats before they escalate. Real-time monitoring allows for rapid detection of suspicious activity, preventing potential breaches and data loss. This involves leveraging security information and event management (SIEM) tools, security analytics, and threat intelligence feeds. A strong monitoring system is the cornerstone of a robust security posture.
Security Auditing Procedures for Private Apps
Regular security audits are vital for identifying vulnerabilities and ensuring compliance with security policies and regulations. These audits should cover access controls, data encryption, and application logs. A comprehensive audit trail provides valuable insights into user activity, helping to pinpoint potential risks and improve overall security. This detailed examination should encompass all aspects of the application’s architecture and operational procedures.
Audit reports should be reviewed and actioned promptly to address identified weaknesses.
Identifying and Responding to Security Threats
Proactive threat identification and response are paramount to minimizing the impact of security incidents. Security information and event management (SIEM) systems and intrusion detection/prevention systems (IDS/IPS) play a key role in detecting and analyzing threats. An incident response plan should be established to guide the organization in handling security incidents. This plan should Artikel the steps to be taken, responsibilities, and communication protocols to mitigate the impact and recovery process.
This systematic approach minimizes the damage caused by breaches.
Incident Response Plans for Private Applications
Developing a comprehensive incident response plan is crucial for handling security breaches effectively. This plan should Artikel the steps to be taken in the event of a security incident, including containment, eradication, recovery, and post-incident analysis. The plan should be regularly reviewed and updated to reflect the latest threats and vulnerabilities. This proactive approach minimizes downtime and ensures swift recovery.
Effective incident response depends on clear communication channels, defined roles, and pre-determined procedures.
Sample Dashboard for Monitoring Security Events
A well-designed dashboard provides a centralized view of security events in real-time. The dashboard should display key metrics, such as the number of alerts, incident severity levels, and user activity. It should also provide detailed information on specific events, including timestamps, sources, and affected systems.
| Metric | Description | Example Data |
|---|---|---|
| Alert Count | Total number of security alerts generated. | 123 |
| Incident Severity | Categorization of incident severity (e.g., low, medium, high). | Medium |
| User Activity | Details of user logins, file accesses, and other activities. | John Doe logged in from New York |
| Event Source | Location of the security event (e.g., application server, network device). | Web Application |
This sample dashboard provides a snapshot of key security metrics and events. A fully functional dashboard would include interactive filters, drill-down capabilities, and customizable views. This real-time view allows security teams to react promptly to potential threats.
Case Studies and Real-World Examples
Diving deeper into the practical application of SASE for securing private applications, we’ll explore real-world scenarios. This section showcases successful implementations, potential security breaches, and how secure design principles were applied to specific private application architectures. These examples will demonstrate the tangible benefits and critical considerations involved in protecting sensitive data and applications.Understanding the intricacies of securing private applications requires a nuanced approach that combines theoretical knowledge with practical application.
Real-world examples illuminate the complexities and highlight the importance of a multi-faceted strategy, including strong access controls, robust security monitoring, and proactive threat detection.
Successful Case Study in Securing Private Apps
A major financial institution successfully migrated its private applications to a cloud-based environment using SASE. This involved integrating various security tools like zero-trust network access (ZTNA) and secure web gateways (SWGs) into their existing SASE architecture. The result was a significant reduction in security incidents, improved user experience, and a streamlined management process for their private application infrastructure.
By utilizing SASE, they not only improved security but also enhanced the overall efficiency of their operations.
Real-World Example of a Private App Successfully Implemented with SASE
A healthcare provider implemented a private application for secure patient data exchange. They leveraged SASE’s ability to provide secure access from any device or location, allowing remote clinicians to securely access patient records. This not only ensured data confidentiality but also enabled remote collaboration and improved patient care. This solution ensured compliance with stringent healthcare regulations and provided a secure platform for critical data exchange.
Security Breach Example in a Private App and Mitigation Strategies
A manufacturing company experienced a security breach in their private application used for sensitive supply chain data. The breach stemmed from a misconfigured VPN, allowing unauthorized access to the network. This incident could have been avoided through comprehensive security audits, implementing multi-factor authentication (MFA), and utilizing a zero-trust network access model. Proactive security measures, such as regular vulnerability assessments, would have prevented unauthorized access.
Security Principles Applied in a Specific Private Application Design
A retail company designed a private application for internal inventory management. Their design prioritized the principle of least privilege by granting users only the necessary access rights. They employed role-based access control (RBAC) to limit access based on user roles. This approach prevented unauthorized access to sensitive data and ensured data confidentiality. Additionally, they implemented encryption for data at rest and in transit to protect against data breaches.
Industry Expert Quotes on Securing Private Applications
“The future of application security is inextricably linked to the secure access paradigm, and SASE is the leading platform to enable it.”
John Smith, Cybersecurity Architect at Acme Corporation
“Securing private applications requires a proactive, multi-layered approach that encompasses everything from access control to continuous monitoring.”
Jane Doe, Chief Information Security Officer at XYZ Bank
Future Trends in Secure Private App Design: Sase Securing Private Apps Design Guide
The landscape of private application security is constantly evolving, driven by advancements in technology and the ever-increasing sophistication of cyber threats. Understanding these future trends is crucial for organizations seeking to protect their sensitive data and maintain the integrity of their private applications. This section explores emerging technologies and their implications for secure private app design.
Emerging Technologies and Their Impact
Emerging technologies like serverless computing, containerization, and microservices architectures are reshaping the way private applications are built and deployed. These technologies offer increased agility and scalability but also introduce new security considerations. Organizations must adapt their security strategies to address these challenges.
Advancements in AI and Machine Learning for Enhanced Security
Artificial intelligence (AI) and machine learning (ML) are poised to revolutionize private application security. AI-powered threat detection systems can analyze vast amounts of data in real-time to identify anomalies and potential security breaches with significantly higher accuracy than traditional methods. These systems can learn from past attacks and adapt to new threats, effectively strengthening the defenses of private applications.
Future Directions in SASE Architecture
Software-Defined Access Edge (SASE) architecture is rapidly gaining traction as a unified approach to secure access for private applications. Future SASE implementations will likely integrate more closely with zero-trust network access models, enhancing the security posture of private applications by restricting access based on the identity of the user and the context of the request. This shift towards a more granular, context-aware access control will improve the overall security posture of private applications.
Examples of New Security Tools
Several innovative security tools are being incorporated into private application designs. For example, behavioral analytics tools monitor user activity patterns to detect suspicious behavior, while advanced threat intelligence feeds can help organizations proactively mitigate emerging threats. These proactive approaches significantly enhance the security of private applications.
Forecasting Future Trends in Secure Application Design
| Trend | Description | Impact on Private App Security | Example |
|---|---|---|---|
| AI-powered threat detection | Machine learning algorithms analyze network traffic and application logs to identify anomalies and potential threats. | Improved threat detection accuracy, faster response times, and proactive mitigation strategies. | A system that identifies unusual login patterns from a specific IP address and blocks access until further verification. |
| Zero-trust network access | Micro-segmentation and granular access controls based on user identity and context. | Reduced attack surface, enhanced data protection, and improved security posture. | Restricting access to specific application resources only to authorized users with necessary privileges. |
| Serverless computing security | Addressing the security concerns associated with serverless functions, including proper authorization and access control. | Increased agility and scalability with enhanced security. | Implementing robust authentication mechanisms for serverless functions and using role-based access controls. |
| SASE integration with zero-trust | Combining the benefits of SASE with zero-trust principles for enhanced access control. | Improved security posture, reduced attack surface, and increased operational efficiency. | A SASE architecture that dynamically enforces access policies based on user identity, device context, and application requirements. |
Conclusive Thoughts
In conclusion, this SASE securing private apps design guide has equipped you with a strong foundation for building and maintaining secure private applications. By understanding the crucial design principles, implementation strategies, and future trends discussed, you can proactively safeguard your applications from emerging threats. Remember, robust security is not a one-time fix but a continuous process of learning, adaptation, and proactive measures.
The insights provided here will empower you to build and secure your private apps in a dynamic environment.