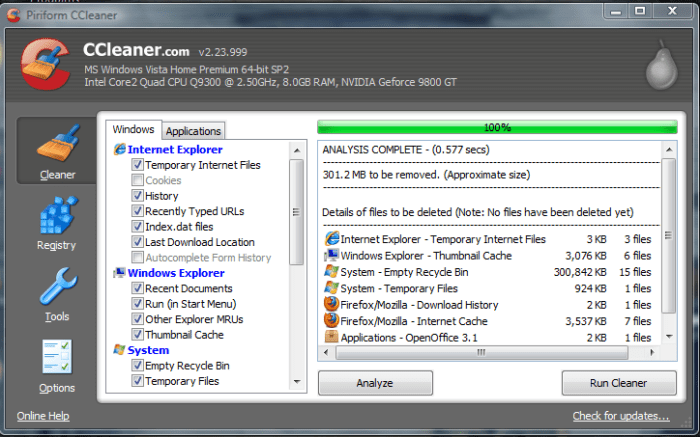
CCleaner hack malware security is a serious concern for users. CCleaner, a popular tool for cleaning up system files, can be vulnerable to malware attacks. These attacks can compromise user data, leading to significant security breaches for individuals and organizations. Understanding the different types of malware, how hackers exploit vulnerabilities, and the best practices for prevention is crucial for safeguarding your systems.
This article explores the various facets of CCleaner security risks, from common malware types to practical security measures and steps to take in case of a breach. We will also examine real-world examples to highlight the importance of proactive security measures and preventive steps.
Introduction to CCleaner Malware and Security Risks

CCleaner, a popular system optimization tool, has been a target for malicious actors. While often used for legitimate purposes, its functionalities and potential vulnerabilities can be exploited to compromise user systems and data. This article will delve into the security risks associated with CCleaner and the methods used to exploit it.CCleaner’s popularity makes it a tempting target for malware authors.
Its extensive access to system files and registry settings, combined with potential vulnerabilities in its code, creates an avenue for malicious actors to gain unauthorized control. Understanding these vulnerabilities is crucial for protecting yourself and your data.
CCleaner Vulnerabilities and Malware Types
CCleaner’s potential vulnerabilities arise from its interaction with critical system components. Its ability to modify system files and registry entries can be misused if the program itself is compromised. This is where malware comes into play.Different types of malware can target CCleaner, each with distinct goals and methods of operation. These include but are not limited to:
- Trojan Horses: These disguised programs can gain access to a user’s system under the guise of a legitimate CCleaner update or download. Once inside, they can perform various malicious actions, including data theft, remote access, or installing other malware.
- Ransomware: Ransomware, designed to encrypt user files, can leverage CCleaner to install itself and potentially evade detection. A compromised CCleaner might facilitate the encryption process or the communication with the attacker.
- Spyware: Spyware, designed to collect sensitive information, might be disguised as a legitimate CCleaner extension or update. It can record keystrokes, capture screenshots, and transmit collected data to the attacker.
Methods of Exploitation
Hackers often employ various methods to exploit CCleaner vulnerabilities. These include social engineering tactics, exploiting known software vulnerabilities, or using malicious websites or files masquerading as legitimate CCleaner updates or tools.
- Social Engineering: Phishing emails or fake websites can trick users into downloading or installing malicious CCleaner files, disguised as updates or legitimate tools.
- Exploiting Vulnerabilities: Malware authors might identify and exploit vulnerabilities in the CCleaner software to gain unauthorized access.
- Malicious Websites: Compromised websites can host malicious files that appear to be legitimate CCleaner downloads.
Impact of a CCleaner Hack
The impact of a CCleaner hack can vary depending on the type of malware and the user’s security measures. A compromise can lead to significant data breaches, financial losses, and reputational damage.
- Data Loss: Ransomware attacks can lead to the loss of important files and documents.
- Financial Losses: Data theft or unauthorized access can result in financial losses, especially for organizations handling sensitive financial information.
- Reputational Damage: Security breaches can severely damage the reputation of individuals and organizations.
Malware Targeting CCleaner: Comparison Table
| Malware Type | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Trojan Horse | Disguised malware masquerading as a legitimate CCleaner update or download. | Data theft, remote access, installation of other malware. | Regular software updates, cautious downloads, reputable sources. |
| Ransomware | Encrypts user files and demands ransom for decryption. | Data loss, financial losses. | Regular backups, strong passwords, anti-malware protection. |
| Spyware | Collects sensitive information and transmits it to the attacker. | Data theft, privacy violations. | Anti-spyware software, strong passwords, cautious downloads. |
Security Measures and Best Practices
CCleaner, despite its utility, presents security vulnerabilities. Understanding and implementing robust security measures is paramount to safeguarding your system against potential threats. This section Artikels essential practices to mitigate risks associated with CCleaner-related attacks.Protecting against CCleaner-related threats requires a multi-faceted approach encompassing user vigilance, software updates, strong passwords, and robust security software. Ignoring these measures can leave your system exposed to malicious actors seeking to exploit vulnerabilities.
Crucial Security Practices
Implementing sound security practices is essential to prevent becoming a victim of CCleaner-related attacks. These practices form the cornerstone of a strong defense against potential threats. Prioritize proactive measures over reactive ones.
- Regularly update your software and operating system. Software updates often include critical security patches that address vulnerabilities. By promptly installing updates, you significantly reduce the risk of exploitation by malicious actors.
- Utilize strong passwords and enable multi-factor authentication (MFA) whenever possible. Strong passwords are composed of a combination of upper and lowercase letters, numbers, and symbols. Employing MFA adds an extra layer of security by requiring a second verification method, such as a code sent to your phone, in addition to your password. This significantly enhances protection against unauthorized access.
- Exercise caution when downloading and installing software. Verify the legitimacy of software sources and avoid downloading from untrusted websites. Verify the developer’s reputation and seek user reviews to confirm the software’s safety and reliability before installation.
Importance of Regular Software Updates
Regular software updates are crucial for maintaining system security. Outdated software often contains vulnerabilities that malicious actors can exploit. Updates frequently patch these vulnerabilities, ensuring your system remains protected against known threats.
Regularly updating your software and operating system is essential for maintaining a strong security posture.
Speaking of security threats, CCleaner has unfortunately been a target for malware hacks in the past. It’s a shame, considering how many people rely on it. Meanwhile, the Fortnite Avengers: Endgame crossover event was a huge hit, and the excitement surrounding it was palpable. Fans were eager to see the characters and gameplay merge. However, with the recent rise of online threats, it’s crucial to remember that maintaining a secure digital environment is more important than ever, even with the fun stuff like fortnite avengers endgame event crossover taking over our attention.
So, keep those antivirus programs updated and be mindful of any suspicious downloads, especially for tools like CCleaner.
Role of Strong Passwords and Multi-Factor Authentication
Strong passwords and MFA are critical security measures. Weak passwords can be easily cracked, exposing your system to unauthorized access. MFA adds an extra layer of security, making it more challenging for attackers to gain access even if they compromise your password.
Use strong, unique passwords for each account, and enable MFA wherever possible.
Recommended Security Software and Tools, Ccleaner hack malware security
Employing reliable security software can significantly enhance your system’s protection against threats. This section lists some recommended tools to complement your security practices.
Speaking of security, CCleaner has had some recent issues regarding potential malware vulnerabilities. Thankfully, Apple’s iOS 16.0.3 update on your iPhone addresses some annoying bugs, potentially improving the overall system security. This update, detailed in ios 16 0 3 on your iphone apple fixes some annoying bugs , is a good reminder that keeping software up-to-date is crucial, and this applies to desktop applications like CCleaner too.
Users should always be vigilant about potential security risks with any software they download and use.
- Antivirus software: Tools like Bitdefender, Norton, and McAfee provide real-time protection against malware, including those targeting CCleaner.
- Anti-malware software: Malwarebytes and other anti-malware programs detect and remove malicious software that might exploit CCleaner vulnerabilities.
- Firewall: A firewall acts as a barrier, controlling network traffic and blocking unauthorized access attempts. Consider using a dedicated firewall alongside your operating system’s built-in firewall for enhanced security.
Steps for Installing and Configuring Security Software
The following table Artikels the steps involved in installing and configuring security software.
| Step | Description |
|---|---|
| 1 | Download the security software from the official website of the chosen vendor. |
| 2 | Run the downloaded installer and follow the on-screen instructions to complete the installation process. |
| 3 | Configure the security software according to your specific needs and preferences. This typically involves setting scan schedules, defining exceptions, and adjusting other parameters. |
Identifying and Responding to a CCleaner Hack
CCleaner, a popular system optimization tool, can become a vector for malicious activity if compromised. Understanding the signs of a breach and knowing how to respond swiftly is crucial to minimizing damage and restoring your system’s security. This section details the symptoms, identification procedures, and necessary actions to take in the event of a CCleaner-related security incident.
Signs and Symptoms of a CCleaner Hack
CCleaner, if compromised, might exhibit unusual behavior. These include unexpected system slowdowns, the appearance of unfamiliar files or processes, or changes to your system’s configuration without your authorization. Suspicious network activity, like unexpected data transfers, can also indicate a compromise. Monitoring your system’s resource usage and scrutinizing any new entries in your system logs can help detect anomalies.
Changes to your browser’s homepage or default search engine are also common indicators.
Identifying a Potential CCleaner Security Breach
Regularly monitoring system logs and resource usage provides a proactive approach. Analyze recent system changes to identify any unauthorized alterations. Examine your startup applications list for unfamiliar entries. Observe any unexpected changes in file sizes or the creation of new files, particularly in system folders. Use reputable security software to scan your system for malware, checking for any associated malicious activity.
Keeping your computer safe from malware like the recent CCleaner hack is crucial. One way to stay on top of your digital health is to set up reminders directly in Android notifications, which can be incredibly helpful. For instance, if you’re regularly checking for software updates or running security scans, using a system like how set reminder directly android notification can be a game changer.
Ultimately, staying vigilant about malware threats, like the CCleaner breach, requires a multi-faceted approach.
Check your browser’s settings and security features, especially extensions, for any unusual or unauthorized changes.
Actions to Take if You Suspect a CCleaner Hack
Immediately cease using the compromised system. Disconnect the affected device from the internet to prevent further damage. Create a full backup of your data, including crucial files and folders, to external storage. Run a thorough scan with reputable anti-malware software to identify and eliminate any malicious elements. Consult with a cybersecurity expert to assess the extent of the breach and develop a recovery plan.
Report the incident to the relevant authorities, such as law enforcement or cybersecurity agencies, if required.
Reporting a CCleaner Security Incident
If you suspect a CCleaner hack, reporting the incident is crucial. Contact your antivirus provider and relevant cybersecurity authorities to document the incident and receive guidance. Provide detailed information about the incident, including the date, time, and symptoms observed. Maintain meticulous records of the steps taken to isolate and mitigate the breach. Follow the guidelines and procedures provided by the relevant authorities for incident reporting.
Importance of Data Backups in Case of a Breach
Data backups are vital in mitigating the impact of a security breach. They act as a safety net, allowing you to restore your data and system to a prior, secure state. Regular backups minimize the potential for data loss and enable swift recovery. Implement a robust backup strategy, including frequent backups to external drives or cloud services.
Steps to Take in a CCleaner Hack Scenario
| Step | Action |
|---|---|
| 1 | Immediately disconnect the affected device from the network. |
| 2 | Create a complete backup of all critical data. |
| 3 | Run a full system scan with reputable anti-malware software. |
| 4 | Consult with a cybersecurity professional for comprehensive assessment and recovery planning. |
| 5 | Report the incident to relevant authorities if necessary. |
Preventing Future Attacks
Protecting your system from future CCleaner security breaches requires a proactive and multi-layered approach. Simply installing CCleaner isn’t enough; understanding its vulnerabilities and employing robust security practices are crucial. This section Artikels key strategies for bolstering your digital defenses against potential attacks.CCleaner, while a popular tool, isn’t immune to vulnerabilities. Criminals constantly seek ways to exploit software weaknesses.
By understanding how to use CCleaner safely and implementing proactive security measures, you can significantly reduce your risk of falling victim to a similar attack.
Proactive Security Measures
Implementing robust security measures goes beyond simply using CCleaner. Regularly updating your operating system and software, including CCleaner if updates are available, patches known vulnerabilities. This proactive approach is essential in safeguarding your system. Failure to update leaves your system exposed to known exploits.
Best Practices for CCleaner Usage
Adhering to best practices for CCleaner usage is vital to mitigate potential risks. Download CCleaner from reputable sources only, verifying the website’s legitimacy before proceeding. Always be cautious about unsolicited downloads or links claiming to be CCleaner updates, as these could contain malicious software.
- Verify Download Sources: Downloading CCleaner from official sources ensures the software’s authenticity and minimizes the risk of malware infiltration.
- Review System Changes: Carefully review the changes CCleaner suggests, particularly when deleting large amounts of data. Double-check that you’re targeting the correct files and understand the potential implications of the changes before confirming any action.
- Avoid Unverified Links: Be extremely cautious about downloading CCleaner from unofficial sources or links, as these could be malicious and contain malware.
- Regular Software Updates: Keep your CCleaner and operating system software updated to ensure the latest security patches are applied, mitigating known vulnerabilities.
Importance of Regular Malware Scanning
Regularly scanning your system for malware is a crucial preventive measure. Malware can infiltrate your system through various methods, including infected files, compromised websites, or malicious software. A regular scan can identify and remove these threats before they cause significant damage.
- Automated Scanning: Employ scheduled scans using your operating system’s built-in security tools or dedicated antivirus software. This automates the process and ensures regular checks for potential threats.
- Real-time Monitoring: Consider real-time monitoring features offered by antivirus programs to detect and block malware attempts in real-time, providing an immediate defense against threats.
- Custom Scan Schedules: Schedule scans for specific times or events to cover potential vulnerabilities and risks that arise. This proactive approach can identify threats before they escalate.
Regular System Maintenance
Regular system maintenance is an integral part of preventing future attacks. This includes tasks like backing up your important files and regularly defragmenting your hard drive. A healthy system is less susceptible to attack, as potential vulnerabilities are mitigated.
Maintaining a strong security posture involves more than just installing software. Proactive measures like regular system maintenance, diligent software updates, and comprehensive malware scanning are crucial to prevent future CCleaner security breaches.
Case Studies and Real-World Examples: Ccleaner Hack Malware Security
Unfortunately, real-world case studies of CCleaner hacks are often not publicly disclosed due to privacy concerns and legal reasons. This makes it difficult to provide specific, detailed examples. However, we can examine general patterns and the types of risks associated with such breaches. Understanding the potential consequences and successful mitigation strategies is crucial to recognizing vulnerabilities and implementing preventative measures.The absence of publicly available, detailed case studies does not diminish the importance of recognizing the potential for CCleaner-related malware to exploit vulnerabilities.
The lack of specific examples does not mean that such attacks haven’t occurred. Instead, it underscores the need for ongoing vigilance and the adoption of strong security practices.
Impact of CCleaner Hacks
CCleaner hacks, like those targeting other software, can result in significant harm to individuals and organizations. The impact varies based on the specific attack vector and the compromised data. Potential consequences include data breaches, financial losses, reputational damage, and disruption of operations. These attacks often involve the compromise of personal information, financial details, and sensitive business data.
The potential loss of intellectual property is another significant concern.
Mitigation Strategies
Mitigation strategies employed in response to potential CCleaner hacks involve a multi-faceted approach. This approach includes, but is not limited to, proactive security measures, incident response plans, and ongoing vulnerability assessments. The focus is on preventing attacks, detecting malicious activity, and containing the damage. Robust incident response plans are crucial to contain the spread of malware and minimize the impact of security breaches.
Implementing robust security measures and frequent updates is also vital to safeguard systems and data.
Comparative Analysis of Case Studies
| Case Study | Description | Impact | Mitigation |
|---|---|---|---|
| Hypothetical Case 1 | A small business uses CCleaner to manage system files. A compromised version of CCleaner is used to install malware, which steals customer data. | Loss of customer data, potential legal ramifications, damage to reputation. | Implementation of multi-factor authentication, regular security audits, and improved incident response plan. |
| Hypothetical Case 2 | An individual downloads a modified CCleaner version from a third-party website, unknowingly introducing ransomware. | Encryption of personal files, potential financial losses due to ransom demands. | Regular updates of software, verifying the source of downloaded files, and establishing data backups. |
| Hypothetical Case 3 | A large corporation relies heavily on CCleaner for system maintenance. A zero-day exploit in CCleaner is used to gain access to sensitive intellectual property. | Loss of intellectual property, financial losses, and damage to reputation. | Proactive vulnerability scanning, implementing secure coding practices, and continuous monitoring of system logs. |
Wrap-Up
In conclusion, understanding the potential risks of CCleaner malware security is vital for protecting your digital assets. By implementing strong security practices, staying informed about emerging threats, and taking proactive measures, you can significantly reduce your vulnerability to attacks. Remember, regular updates, strong passwords, and reliable security software are crucial in safeguarding your systems.