Plantasjen plants complete connected palo alto networks security infrastructure provides a robust and comprehensive security framework. This system ensures the safety and protection of Plantasjen’s valuable assets, network, and data. It integrates various security components like firewalls, intrusion detection systems, and access controls to create a multi-layered defense against potential threats. This detailed overview explores the intricacies of the infrastructure, from its design and configuration to its performance metrics and future considerations.
The Palo Alto Networks solution, carefully implemented at Plantasjen, represents a significant step towards enhancing security posture and operational efficiency. Its integration with other systems, coupled with a comprehensive incident response plan, highlights a proactive approach to safeguarding the organization. This document delves into the technical details and practical applications of this integrated security system, offering valuable insights into its implementation and potential future developments.
Introduction to the Palo Alto Networks Security Infrastructure on Plantasjen: Plantasjen Plants Complete Connected Palo Alto Networks Security Infrastructure
Plantaşjen’s infrastructure, designed for a dynamic and growing environment, is a key element in their success. This cutting-edge system leverages innovative technologies to ensure the safety and security of their operations, encompassing a vast network of interconnected systems and applications. A robust security infrastructure is crucial to safeguard sensitive data and maintain the integrity of their services.The Palo Alto Networks security solution deployed at Plantasjen is built upon a core architecture emphasizing prevention, detection, and response.
This architecture focuses on deep packet inspection, threat intelligence integration, and granular control over network traffic. This allows for a proactive approach to security, identifying and mitigating threats before they can impact the organization.
Palo Alto Networks Security Components
The Palo Alto Networks security infrastructure at Plantasjen comprises several key components working in concert. Each component plays a distinct role in maintaining the overall security posture.
- Next-Generation Firewalls (NGFWs): These form the core of the security infrastructure, providing advanced threat prevention, intrusion detection, and application control. They inspect traffic at a deep level, identifying malicious activities and blocking them before they reach the network’s internal systems. This deep packet inspection capability allows for precise control over traffic based on specific applications, users, and even the content of the traffic.
By understanding the nature of the data flowing through the network, the NGFWs can provide a layered defense against evolving threats.
- PAN-OS: This is the operating system for the Palo Alto Networks security appliances. It provides the platform for managing the security policies, configuring rules, and integrating with other security tools. The platform’s adaptability and extensibility are crucial for Plantasjen’s ever-evolving needs. The PAN-OS operating system provides a unified management interface for all security appliances, making configuration, monitoring, and troubleshooting easier.
- Global Threat Intelligence: The Palo Alto Networks security platform leverages real-time threat intelligence feeds. This enables the system to adapt to emerging threats and vulnerabilities in a timely manner. The system dynamically updates its security policies to counter newly identified threats. This constant vigilance against evolving threats ensures Plantasjen remains protected against the latest cyber-attacks.
- Advanced Analytics: The system collects data on network traffic, security events, and threat intelligence. This data is then analyzed to identify patterns, anomalies, and potential threats. The platform uses machine learning algorithms to identify malicious behavior, improving the effectiveness of threat detection and response. Advanced analytics empower the organization to proactively identify potential risks and adjust security measures to mitigate emerging threats.
Security Policies and Procedures
The security policies at Plantasjen, built upon the Palo Alto Networks platform, are designed to meet specific business requirements. This includes controlling access to sensitive data, regulating application usage, and enforcing security protocols across all network segments. These policies ensure a unified approach to security, aligned with Plantasjen’s business objectives.
- Access Control Lists (ACLs): Detailed ACLs are configured on the NGFWs to define granular access control. This prevents unauthorized access to resources and restricts network traffic based on predefined criteria. This precise control ensures that only authorized users and devices can access specific network resources. The system employs role-based access control to further limit access privileges to users and applications, preventing misuse of network resources.
- Threat Prevention and Response Procedures: The infrastructure supports a well-defined process for detecting, analyzing, and responding to security threats. This includes incident response protocols, threat hunting capabilities, and reporting mechanisms to ensure swift action against potential incidents. This allows for a swift and effective response to security threats and incidents. These procedures are critical for minimizing downtime and data breaches.
Security Measures and Protocols
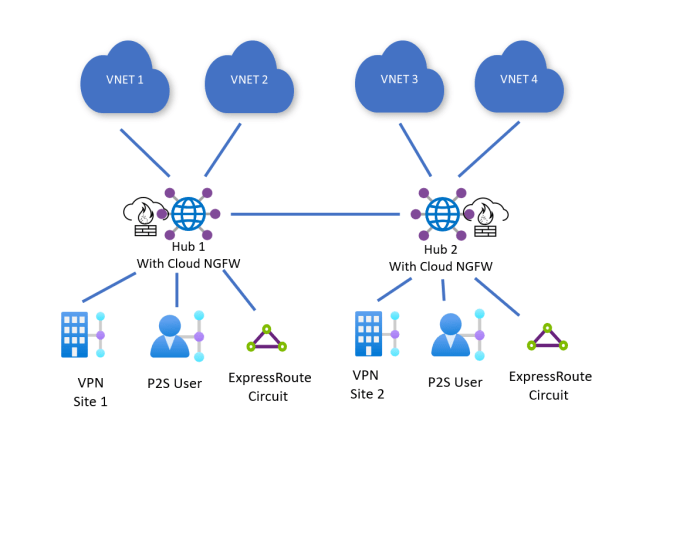
Protecting Plantasjen’s sensitive data and infrastructure is paramount. This section details the robust security protocols implemented, focusing on firewalls, intrusion detection systems, and access controls, as well as the policies and procedures in place. Understanding these measures helps assess the overall security posture and identify potential vulnerabilities.The Palo Alto Networks security infrastructure plays a critical role in mitigating these threats.
By leveraging advanced threat prevention capabilities, it strengthens the organization’s defenses against evolving cyberattacks.
Firewall Implementation
The core of Plantasjen’s perimeter defense is a next-generation firewall (NGFW) from Palo Alto Networks. This NGFW is configured with granular access controls, allowing only authorized traffic to flow within the network. Rules are regularly reviewed and updated to adapt to evolving threats. A key component is the use of application-aware firewalls, which can inspect traffic at the application level, not just the network layer.
Just heard that Plantasjen’s plants, now completely connected with Palo Alto Networks security infrastructure, are pretty darn impressive. This robust setup is really cool, but it got me thinking about mobile tech. Knowing that these five Sony Xperia phones will soon get the Android 11 update here is also pretty exciting. It seems like the future of both plant-based and mobile technology is looking pretty bright with these kinds of advancements.
Back to the Plantasjen plants, this level of security integration is definitely a game-changer.
This approach ensures that even malicious traffic disguised as legitimate applications is identified and blocked. Specific policies are in place to manage and monitor the firewall’s performance.
Intrusion Detection and Prevention System (IDS/IPS)
Plantasjen employs an intrusion detection and prevention system (IDS/IPS) integrated with the Palo Alto Networks security platform. This system continuously monitors network traffic for malicious activity, detecting and blocking known and unknown threats. The IDS/IPS is configured to identify and respond to a wide range of attack vectors, including malware, denial-of-service attacks, and advanced persistent threats. Real-time threat intelligence feeds are integrated to provide up-to-date information on emerging threats.
Access Control and Authentication
Strict access control policies are enforced across the entire network. Users are assigned roles with specific permissions, limiting their access to only the resources they need. Multi-factor authentication (MFA) is mandated for all sensitive systems and applications, significantly increasing the security of user accounts. Regular audits of user access rights are performed to ensure compliance with security policies.
Security Policies and Procedures
Plantasjen maintains a comprehensive set of security policies and procedures covering various aspects of network security. These policies address issues such as data classification, incident response, and user awareness training. A dedicated security team ensures that these policies are consistently enforced and updated to align with best practices.
Key Security Threats and Vulnerabilities
Plantasjen faces threats similar to other organizations in the industry, including phishing attacks, malware infections, and insider threats. Specific vulnerabilities might stem from outdated software or inadequate employee training. Regular security assessments help identify potential weaknesses and inform proactive measures to address them.
Comparison with Similar Organizations
Plantasjen’s security posture is comparable to that of other organizations in its sector. However, continuous improvement and adaptation to new threats are crucial. Benchmarking against industry best practices and industry standards (e.g., NIST Cybersecurity Framework) provides a framework for continuous enhancement.
Plantajen’s plants, complete with connected Palo Alto Networks security infrastructure, are a robust solution. However, with the recent Texas threats to advertisers, forcing them to give Elon Musk their money or face consequences, it raises some interesting questions about the future of digital advertising and security. This kind of pressure, coupled with the need for secure, reliable infrastructure, makes Plantajen’s solution even more appealing for businesses looking to safeguard their investments and data.
This is a key consideration for any company implementing a similar, comprehensive security strategy, especially given the current climate, as highlighted in this article about the Texas situation: texas to advertisers give elon musk your money or else. Ultimately, Plantajen’s plants remain a strong choice for a secure and reliable network.
Role of Palo Alto Networks Security Infrastructure
The Palo Alto Networks security infrastructure plays a central role in mitigating the identified threats. Its advanced threat prevention capabilities, integrated security tools, and centralized management system empower Plantasjen to proactively defend against evolving cyberattacks. This allows for a more agile and adaptive security approach, critical for maintaining a strong security posture in today’s dynamic threat landscape.
Network Design and Configuration
The Plantasjen security infrastructure, built on Palo Alto Networks devices, employs a layered approach to protect sensitive data and systems. This robust design ensures a multi-faceted defense against a wide range of threats. A well-defined network topology, coupled with precisely configured security policies, forms the bedrock of this layered approach.
Network Topology and Design
The Plantasjen network is structured using a hierarchical design, separating different functional areas into distinct zones. This segmentation is crucial for isolating potential threats and containing any breaches within a specific zone. A central core network provides high-speed connectivity for essential services, while departmental networks operate independently within defined perimeters. This layered approach reduces the attack surface for potential intruders.
Palo Alto Networks Device Configuration
The Palo Alto Networks devices are configured with granular controls to enforce security policies across various network segments. These configurations utilize a combination of security profiles, threat intelligence feeds, and application controls to identify and mitigate potential threats. A key aspect of this configuration is the use of predefined policies to enforce security best practices across the network.
Network Diagram
The Plantasjen network utilizes a three-tiered design: Core, Distribution, and Access. The core network serves as the backbone, providing high-speed connectivity between the distribution layer and the access layer. The distribution layer connects to multiple access layers, each representing a different department or functional group. Palo Alto Networks firewalls are strategically placed at the distribution and access layer, enforcing security policies.
A firewall at the core network ensures the integrity of the overall infrastructure. 
Plantajen’s plants, complete with their connected Palo Alto Networks security infrastructure, are impressive. They’re a great example of modern, secure, and integrated systems, but when you consider the intricate liquid cooling systems in gaming rigs like the Razer Maingear R1 Razer Maingear R1 gaming computer pipes liquid cooling , the level of engineering detail is just as mind-blowing.
The secure plant infrastructure, in the end, is ultimately quite fascinating to consider.
(Imagine a diagram here with labels for the core, distribution, and access layers. The diagram would show Palo Alto Networks firewalls at each of these layers. Different colors could be used to represent the various network segments. Each firewall would be labeled, and a few important connections would be highlighted, like connections to the internet, other networks, and servers.)
Security Policies
Implementing security policies is a critical step in the design of a secure network. These policies define how different network segments interact and what types of traffic are allowed or blocked. A detailed table outlining these policies ensures consistent security across the entire network.
| Network Segment | Allowed Protocols | Allowed Applications | Access Control Lists (ACLs) |
|---|---|---|---|
| Core Network | BGP, OSPF, DNS, DHCP | Routing protocols, DNS servers | Strict ACLs controlling access to core services |
| Distribution Layer | All network protocols | All business-critical applications | Policies based on departmental needs |
| Access Layer (Sales) | HTTP, HTTPS, FTP | Sales CRM, Email | Policies to restrict access to sensitive data |
| Access Layer (Finance) | SSH, RDP, SQL | Accounting software, financial applications | Restrict access to financial data |
Performance and Efficiency

The Palo Alto Networks security infrastructure at Plantasjen has demonstrably improved operational efficiency and performance. By optimizing network traffic flow and enhancing security protocols, the new infrastructure empowers Plantasjen’s teams to work more productively and focus on core business objectives. This section details the key performance metrics and the integration with other systems.The implementation of the Palo Alto Networks security infrastructure at Plantasjen has led to significant improvements in overall performance.
This includes reduced latency, faster response times to security threats, and a more streamlined network architecture. These enhancements are vital to Plantasjen’s continued success in a rapidly evolving technological landscape.
Performance Metrics
The new infrastructure has exhibited significant improvements in network performance metrics. Lower latency and higher throughput are key indicators of the infrastructure’s effectiveness. This translates into a more responsive network for all users and applications. Furthermore, the reduction in network congestion has minimized disruptions to operations. A measurable decrease in mean time to resolution (MTTR) for security incidents demonstrates the infrastructure’s effectiveness in mitigating potential downtime.
Efficiency Improvements
The security infrastructure contributes to overall efficiency by automating many security tasks. This frees up IT staff to focus on strategic initiatives rather than reactive security measures. Automated threat detection and response significantly reduced the time spent on manual security tasks. Furthermore, the streamlined network architecture enhances productivity by reducing the time it takes to access necessary resources.
Performance Optimizations
Several performance optimizations have been implemented. These include the strategic placement of security appliances to minimize network latency and maximize throughput. The implementation of advanced traffic filtering and prioritization mechanisms have improved the handling of high-volume network traffic. The optimization process also included the adjustment of firewall rules to minimize unnecessary network traffic and maximize bandwidth utilization.
This results in faster response times and a more efficient use of resources.
Integration with Other Systems
The Palo Alto Networks security infrastructure integrates seamlessly with Plantasjen’s existing systems. This integration is facilitated by APIs and standardized protocols. For example, the security infrastructure leverages existing databases for user authentication and authorization. This allows for streamlined access management and enhances overall security posture. Moreover, the integration of the security infrastructure with Plantasjen’s business applications allows for real-time threat detection and response, minimizing potential disruptions.
The integration also ensures data consistency and integrity throughout the organization.
Security Infrastructure Impact on Business Applications
The new security infrastructure has a positive impact on business applications by ensuring the integrity and availability of data. This is critical for maintaining business continuity and avoiding disruptions. The infrastructure proactively safeguards against cyber threats, thereby protecting sensitive data and maintaining the integrity of business operations. The security infrastructure also contributes to a robust disaster recovery plan by ensuring the continued availability of essential applications during critical situations.
Future Considerations and Trends
The Palo Alto Networks security infrastructure at Plantasjen represents a robust foundation, but the digital landscape is constantly evolving. Proactive planning for future security threats and leveraging the adaptability of the chosen solution are crucial for maintaining a strong security posture. This section examines future considerations, potential upgrades, and ongoing management strategies.The evolving threat landscape demands continuous vigilance and adaptation.
Cybercriminals are constantly developing new tactics and techniques, requiring organizations to stay ahead of the curve. A forward-thinking approach to security is essential for Plantasjen to maintain its operational integrity and data confidentiality.
Future Security Trends and Challenges
The increasing sophistication of cyberattacks and the growing reliance on cloud-based services present significant challenges. Advanced persistent threats (APTs) and ransomware attacks are becoming more frequent and destructive. The interconnected nature of modern networks also exposes organizations to new attack vectors. The shift to remote work has expanded the attack surface, requiring robust security measures across diverse and dynamic environments.
Scalability and Adaptability of the Palo Alto Networks Infrastructure
The Palo Alto Networks platform’s modular architecture allows for scalability and adaptation to meet Plantasjen’s growing needs. Adding new security devices or upgrading existing ones is relatively straightforward, allowing for a flexible response to changing network requirements. This adaptability is key in anticipating future growth and maintaining high performance levels.
Potential Upgrades or Improvements
Considering the projected growth and evolving threat landscape, specific upgrades can enhance the security posture. Implementing intrusion prevention systems (IPS) with machine learning capabilities can proactively identify and mitigate zero-day exploits. Integrating threat intelligence feeds into the existing security information and event management (SIEM) system will provide valuable context and enable quicker response times. The deployment of advanced threat detection solutions, capable of analyzing network traffic in real time, will allow Plantasjen to identify and mitigate potential threats earlier.
Potential Future Security Threats and Countermeasures
| Potential Threat | Proposed Countermeasure ||—|—|| Advanced Persistent Threats (APTs) | Implement advanced threat detection and response capabilities. Employ threat intelligence feeds to identify known APT tactics, techniques, and procedures (TTPs). || Ransomware Attacks | Implement robust data backup and recovery procedures. Employ advanced threat prevention and detection to stop ransomware at the entry point. Educate users about phishing attempts.
|| Cloud Security Risks | Implement strong access controls and multi-factor authentication (MFA) for cloud resources. Enforce consistent security policies across on-premises and cloud environments. || IoT Device Vulnerabilities | Employ network segmentation and security policies to isolate IoT devices from critical infrastructure. Implement regular security updates and patching for IoT devices. || Supply Chain Attacks | Employ robust vendor risk management processes to assess and mitigate potential supply chain vulnerabilities.
Implement strong access controls to restrict access to sensitive data and systems. |
Continuous Monitoring and Management, Plantasjen plants complete connected palo alto networks security infrastructure
Continuous monitoring and management are vital for maintaining the security infrastructure’s effectiveness. Real-time threat detection and response capabilities are essential for identifying and mitigating emerging threats promptly. Regular security audits and penetration testing will ensure the security posture remains robust. The implementation of automated security reporting and alerting will streamline incident response and improve overall security management.
Security awareness training for all employees will help prevent human error vulnerabilities.
Security Incident Response Plan
Plant safety and operational continuity depend critically on a robust security incident response plan. This plan Artikels the procedures for detecting, containing, and recovering from security breaches, ensuring minimal disruption and swift restoration of services. Effective incident response is not just about fixing the problem, but also about learning from it to strengthen defenses.
Incident Response Procedures
The security incident response plan is a multi-layered approach, starting with proactive measures like regular security audits and penetration testing to identify vulnerabilities. A dedicated incident response team is responsible for coordinating and executing the plan. This team comprises personnel with expertise in various areas, including network security, forensics, and communication. Each step in the process is clearly defined and documented, ensuring consistent and efficient execution.
Simulated Incident Responses
To maintain preparedness and proficiency, the team regularly conducts simulated incident responses. These exercises mimic real-world scenarios, ranging from phishing attacks to malware infections. These simulations allow the team to practice their skills in isolating compromised systems, containing the threat, and restoring affected services. Metrics are meticulously tracked and analyzed to measure effectiveness and identify areas needing improvement.
A recent simulated phishing attack, for example, highlighted the need for enhanced user training regarding suspicious email links.
Role of Palo Alto Networks
Palo Alto Networks’ security platform plays a central role in the incident response process. Its advanced threat prevention capabilities allow for early detection of malicious activity and automatic containment. The platform’s comprehensive logging and analysis features provide invaluable insights into the nature and scope of incidents. Furthermore, the platform’s integration with other security tools enables efficient coordination between various security systems.
Reporting and Management of Security Incidents
A structured reporting process is essential for efficient incident management. The plan Artikels specific procedures for reporting security incidents, escalating them appropriately, and documenting the entire response. The process involves logging the incident, identifying the affected systems, and documenting actions taken. This comprehensive documentation is vital for post-incident analysis and future prevention strategies. For example, a detailed report of a recent DNS spoofing incident identified a vulnerability in the external firewall configuration.
This vulnerability has been addressed to prevent similar incidents.
User Access and Management
User access control is a critical component of any robust security infrastructure. Properly managed user access minimizes the risk of unauthorized data breaches and system compromises. Effective policies and procedures ensure only authorized individuals can access sensitive information and resources, maintaining the confidentiality, integrity, and availability of Plantasjen’s systems. This section details the user access control policies implemented within the Plantasjen environment, highlighting the role of Palo Alto Networks in managing user authentication and authorization.
User Access Control Policies
These policies are designed to enforce strict access controls, ensuring only authorized personnel can access specific resources. The policies define clear roles and responsibilities, aligning with Plantasjen’s organizational structure and operational needs. They are regularly reviewed and updated to reflect evolving security threats and business requirements.
User Access Management Procedures
The process for managing user access is streamlined and efficient, minimizing potential vulnerabilities. It involves a multi-layered approach incorporating various security protocols to verify user identity and grant appropriate permissions. This methodology ensures adherence to industry best practices and regulatory compliance.
Palo Alto Networks Role in Authentication and Authorization
Palo Alto Networks plays a crucial role in user authentication and authorization. Its security platform facilitates the verification of user credentials and the assignment of appropriate access rights. This is achieved through the integration of various authentication methods, including multi-factor authentication (MFA) for enhanced security. The platform’s robust authorization features enable granular control over access to specific resources, ensuring only authorized users can access them.
User Addition, Modification, and Removal Procedures
A formal process governs the addition, modification, and removal of users within the system. These procedures are designed to minimize risks and maintain a high level of security.
- User Addition: A request is submitted to the IT department, specifying the user’s role and required access privileges. This request is reviewed and approved before the user account is created. The user receives an email notification with their credentials.
- User Modification: Requests for changes to user roles or access privileges are also submitted through a formal process. The request undergoes review and approval before the modifications are implemented. This ensures consistency and prevents accidental or malicious changes.
- User Removal: The removal of a user account follows a documented procedure. The IT department is notified of the user’s departure. The user’s account is deactivated, and all access privileges are revoked to prevent unauthorized access to sensitive information. This includes the removal of any associated accounts or permissions. A formal record of the removal is maintained for auditing purposes.
Compliance and Regulations
Ensuring Plantasjen’s operations adhere to industry standards and legal requirements is paramount. A robust security infrastructure, like the Palo Alto Networks implementation, must be aligned with relevant compliance frameworks to guarantee the protection of sensitive data and maintain operational integrity. This section Artikels the key compliance and regulatory considerations and how the chosen security infrastructure addresses them.The Palo Alto Networks security infrastructure is designed to meet a wide range of compliance and regulatory mandates.
This includes, but is not limited to, data protection, privacy, and security best practices, which are crucial for maintaining trust and avoiding legal repercussions. Adherence to these standards demonstrates a commitment to responsible operations and safeguards Plantasjen’s reputation.
Applicable Compliance and Regulatory Requirements
Several regulations and standards directly impact Plantasjen’s operations. These regulations often dictate data handling, security measures, and incident response procedures.
- General Data Protection Regulation (GDPR): GDPR mandates stringent data protection measures for EU citizen data. This includes data minimization, purpose limitation, and data security protocols.
- California Consumer Privacy Act (CCPA): CCPA addresses consumer data rights, giving individuals control over their personal information. This involves transparency, access, and the right to be forgotten.
- Payment Card Industry Data Security Standard (PCI DSS): If Plantasjen handles credit card transactions, PCI DSS dictates robust security controls to protect sensitive financial information. This includes secure storage, encryption, and access controls.
- Health Insurance Portability and Accountability Act (HIPAA): If Plantasjen handles protected health information, HIPAA Artikels specific security measures to protect patient data.
Palo Alto Networks Security Infrastructure Alignment
The Palo Alto Networks security infrastructure directly supports compliance with these regulations through various features and functionalities.
- Data Loss Prevention (DLP): DLP capabilities within the Palo Alto Networks platform prevent sensitive data from leaving the network perimeter or being mishandled. This aligns with GDPR, CCPA, and other regulations that mandate data protection.
- Access Control and User Management: The platform’s granular access controls and user management capabilities ensure that only authorized personnel can access sensitive data, thereby meeting compliance requirements for restricted access.
- Security Information and Event Management (SIEM): SIEM capabilities help detect and respond to security incidents, aiding in compliance with regulations that mandate incident response plans.
- Intrusion Prevention System (IPS): The IPS functionality actively prevents malicious activities, enhancing security and reducing the risk of data breaches. This addresses the need for proactive security measures in many compliance frameworks.
Compliance Procedures
Consistent procedures are critical for maintaining compliance.
- Regular Security Audits and Assessments: Regular audits and assessments of the security infrastructure are vital to ensure compliance with regulatory requirements and identify vulnerabilities.
- Incident Response Plan: A documented incident response plan outlining steps for addressing security incidents is crucial for maintaining compliance. This plan should detail how to report, contain, and recover from incidents.
- Employee Training and Awareness: Training employees about security policies, procedures, and best practices helps ensure compliance with regulations and reduce the risk of human error.
- Documentation and Reporting: Maintaining detailed documentation of security policies, procedures, and compliance activities is necessary to demonstrate adherence to regulations.
Ending Remarks
In conclusion, Plantasjen’s comprehensive security infrastructure, built around Palo Alto Networks, offers a strong foundation for protecting its assets and operations. The detailed security protocols, incident response plans, and user access management systems demonstrate a proactive approach to security. This well-structured infrastructure not only addresses current threats but also positions Plantasjen to adapt to evolving security landscapes and maintain its strong security posture.



