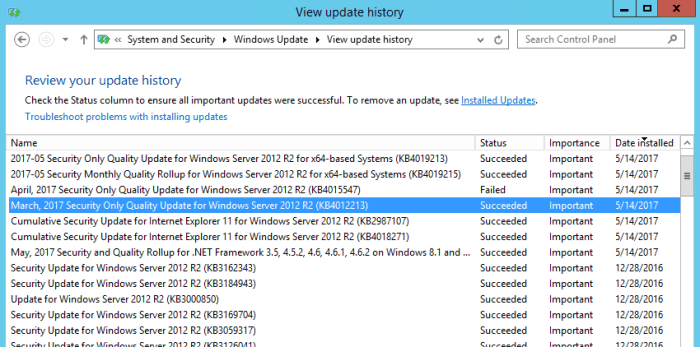
Microsoft Windows XP security patch WannaCry ransomware attack: This event exposed critical vulnerabilities in older Microsoft Windows XP systems, leading to widespread disruption and financial losses. The attack highlighted the urgent need for timely security updates and robust incident response plans. The ensuing chaos underscored the devastating impact of unchecked cyber threats and the vulnerability of outdated systems.
The attack exploited specific security flaws in Windows XP, making systems vulnerable to the WannaCry ransomware. This led to widespread infections across various industries and regions. This narrative explores the attack’s progression, the role of Microsoft’s security patches, and the lasting consequences for cybersecurity practices.
Introduction to the WannaCry Ransomware Attack
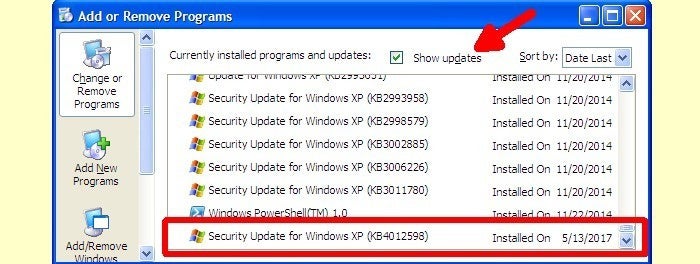
The WannaCry ransomware attack, a significant cybersecurity incident, crippled systems worldwide in May 2017. It exploited a critical vulnerability in older versions of Microsoft Windows, demonstrating the devastating impact of unchecked vulnerabilities. The attack showcased the global interconnectedness of digital infrastructure and the critical need for robust cybersecurity measures.The attack leveraged a known vulnerability in Microsoft Windows, specifically targeting systems lacking critical security updates.
This highlighted the importance of timely software patching and proactive security measures to prevent such widespread attacks. It underscored the vulnerability of systems without current security patches and the need for proactive security practices.
Vulnerabilities Exploited
The WannaCry ransomware attack exploited a critical vulnerability in Microsoft Windows, specifically targeting systems running older versions of the operating system, like Windows XP. This vulnerability, which was publicly disclosed prior to the attack, was related to a flaw in the Server Message Block (SMB) protocol. Attackers leveraged this flaw to gain unauthorized access to systems and deploy the ransomware.
Remember the WannaCry ransomware attack? It exploited vulnerabilities in outdated Microsoft Windows XP systems, highlighting the critical need for security patches. Modern photo editing tools, like the “magic eraser” feature in Google’s Tensor photo editing, offer amazing possibilities for fixing imperfections, but a neglected security patch like the one that caused WannaCry can still have devastating consequences.
It’s a stark reminder that keeping software up-to-date is just as important, if not more so, than fancy new tools like magic eraser google tensor photo editing. Even advanced tech won’t protect you from a vulnerable operating system.
Exploiting this vulnerability demonstrated the importance of maintaining updated security patches.
Initial Spread and Propagation Methods
The WannaCry ransomware initially spread through a worm-like mechanism, utilizing the EternalBlue exploit to propagate rapidly across networks. This exploit, which targeted the SMB protocol vulnerability, enabled the malware to automatically spread to vulnerable machines. This auto-spreading feature amplified the attack’s scope and impact. The attack exploited a known vulnerability in Microsoft Windows, specifically targeting systems lacking critical security updates.
This vulnerability was related to a flaw in the Server Message Block (SMB) protocol. Attackers leveraged this flaw to gain unauthorized access to systems and deploy the ransomware.
Affected Industries and Regions
The WannaCry ransomware attack had a wide-ranging impact, affecting various industries and regions globally. This demonstrated the vulnerability of systems without current security patches and the need for proactive security practices. It underscored the vulnerability of systems without current security patches and the need for proactive security practices.
| Industry | Region |
|---|---|
| Healthcare | Europe |
| Manufacturing | North America |
| Government | United Kingdom |
| Financial Institutions | Asia |
The Role of Microsoft Windows XP Security Patches
The WannaCry ransomware attack, a global cyber incident, highlighted the critical importance of timely security patching, especially for older operating systems like Windows XP. The attack exploited vulnerabilities that had been previously identified and addressed by Microsoft, but unfortunately, many users, particularly those using XP, had not applied the necessary security updates. This demonstrates the crucial role of proactive patching in mitigating the risk of such attacks.Microsoft’s response to the WannaCry attack involved releasing crucial security patches to address the exploited vulnerabilities.
These patches were not simply band-aid solutions but rather comprehensive fixes aimed at strengthening the system’s defenses against similar exploits. The effectiveness of these patches, in theory and in practice, depended on the speed and comprehensiveness of their deployment by users.
Remember the WannaCry ransomware attack? It exploited vulnerabilities in outdated Microsoft Windows XP systems, causing widespread chaos. While that’s a stark reminder of the importance of security patches, comparing the features of similar phones like the Motorola One Action and Moto G7 can also be fascinating. Looking at specs, performance, and camera capabilities, you can learn a lot about different phone options in the market, like how the Motorola One Action vs Moto G7 stacks up.
motorola one action vs moto g7. Ultimately, keeping your software updated is crucial, just like ensuring your device is equipped with the right features for your needs.
Critical Security Patches Released
The WannaCry ransomware attack leveraged vulnerabilities in the Server Message Block (SMB) protocol, specifically a flaw in the implementation of the SMBv1 protocol. Microsoft addressed this by releasing crucial security updates that patched the vulnerable components. These updates provided a crucial layer of protection, preventing the malicious code from exploiting the vulnerabilities and spreading the infection.
Vulnerabilities Patched and Their Impact
The primary vulnerability exploited by WannaCry involved a flaw in the handling of a specific SMBv1 function. This allowed attackers to exploit a remote code execution vulnerability, which could enable them to take control of vulnerable systems. The impact of this vulnerability was severe, leading to widespread infections and significant financial losses for organizations and individuals. Other, less significant vulnerabilities may have also been exploited in conjunction with the main flaw, but their relative importance was significantly lower.
Patch Deployment Comparison Before and After the Attack
| Feature | Patches Before WannaCry | Patches After WannaCry |
|---|---|---|
| Focus | General security updates addressing various potential threats | Specific patches focusing on the SMBv1 vulnerability exploited in WannaCry |
| Deployment Rate | Varied across user groups, often slow and uneven | Significant emphasis on rapid deployment and increased awareness campaigns |
| Effectiveness | Limited impact on the specific WannaCry exploit | Significantly improved protection against WannaCry and similar attacks |
| User Awareness | Limited understanding of the importance of security updates | Increased user awareness campaigns by Microsoft and others |
The table above illustrates a stark contrast in the focus and deployment rates of security patches. Before the attack, security patches were released for general vulnerabilities, but their impact on a specific attack like WannaCry was limited. Post-WannaCry, Microsoft focused specifically on patching the SMBv1 vulnerability and implemented aggressive measures to encourage prompt deployment.
Deployment Rates Across User Groups and Regions
Deployment rates of security patches varied significantly across different user groups and regions. Businesses, typically more aware of security threats and having better infrastructure for patching, often deployed updates more quickly than individual users. Similarly, countries with robust IT infrastructure and proactive cybersecurity policies saw faster patch deployment rates than regions with less developed cybersecurity environments. Geographical location, access to reliable internet connectivity, and individual user awareness significantly influenced patch deployment rates.
Impact and Consequences of the Attack: Microsoft Windows Xp Security Patch Wannacry Ransomware Attack
The WannaCry ransomware attack, leveraging a critical vulnerability in Microsoft Windows, had devastating consequences for organizations and individuals worldwide. Beyond the immediate financial losses, the attack caused significant disruption to business operations and fundamentally altered the perception of cybersecurity risks in various sectors. This analysis will explore the multifaceted impact of the attack.
Remembering the WannaCry ransomware attack highlighting the critical need for timely security patches, like those for Microsoft Windows XP, made me think about how a better gaming experience might be achieved. A physical keyboard for the Nintendo Switch, like the Hori one, Hori Nintendo Switch keyboard might be a game changer. Ultimately, though, robust security measures remain crucial for preventing similar widespread attacks like WannaCry, even if gaming peripherals evolve.
Financial Losses
The WannaCry ransomware attack resulted in substantial financial losses across numerous sectors. Small businesses, particularly those reliant on outdated software, were particularly vulnerable. The cost of recovery, including data restoration, system rebuilding, and legal fees, added to the financial strain. The attack also impacted larger corporations, causing disruptions in supply chains and impacting productivity. Estimates vary, but the overall financial impact was substantial, highlighting the potential for significant losses from such attacks.
Disruption to Business Operations
The ransomware attack caused widespread disruption to business operations. Critical infrastructure, including healthcare facilities and transportation networks, experienced significant downtime. Hospitals were forced to postpone surgeries and divert resources to address the ransomware infections. This downtime resulted in substantial losses, both financially and in terms of patient care. Many organizations were unable to access crucial data, leading to delays in operations and impacting productivity across the board.
Long-Term Effects on Cybersecurity Practices
The WannaCry attack served as a stark reminder of the critical need for robust cybersecurity measures. Organizations were forced to re-evaluate their security protocols and invest in more comprehensive solutions. The incident significantly impacted the perception of cybersecurity risks in various sectors.
| Aspect | Long-Term Effect |
|---|---|
| Patch Management | The attack underscored the importance of timely patching and vulnerability management. Organizations increased their focus on proactively addressing known vulnerabilities to prevent similar attacks. |
| Security Awareness Training | Increased emphasis on educating employees about phishing attacks, suspicious emails, and other social engineering tactics to mitigate the risk of human error. |
| Data Backup and Recovery | Organizations realized the necessity of robust data backup and recovery strategies. Regular backups, along with a tested recovery plan, are now considered critical components of security infrastructure. |
| Incident Response Planning | A greater focus on developing and testing incident response plans became paramount. The ability to quickly identify, contain, and recover from cyberattacks became a key priority. |
| Cybersecurity Budget Allocation | Organizations began allocating more resources to cybersecurity, recognizing it as a critical investment to protect their assets. |
Impact on Cybersecurity Perception
The WannaCry attack significantly impacted the perception of cybersecurity risks. Before the attack, many organizations underestimated the potential impact of ransomware attacks. After WannaCry, there was a heightened awareness of the risks associated with outdated software and the importance of proactive security measures. The attack exposed vulnerabilities in critical infrastructure, prompting a greater understanding of the potential for widespread disruption and the need for robust defenses.
The attack highlighted the importance of a layered approach to security, including technical controls, user training, and incident response planning.
Response Strategies and Mitigation Techniques
The WannaCry ransomware attack exposed critical vulnerabilities in security protocols, highlighting the urgent need for proactive measures. Organizations struggled to contain the spread and recover from the damage, prompting a significant shift in cybersecurity strategies. This section analyzes the response strategies, Microsoft’s actions, and preventive measures to mitigate future ransomware attacks, focusing on the importance of patching older systems.
Organizational Response Strategies
Affected organizations faced a complex challenge in containing the ransomware. Initial responses varied, reflecting the diverse range of resources and preparedness levels. Some organizations opted for immediate system shutdowns to prevent further infection, while others focused on isolating compromised systems to limit the spread. Data recovery efforts were crucial, often involving restoring backups or utilizing specialized recovery tools.
The need for robust incident response plans and dedicated security teams became apparent. Communication with affected users and stakeholders was also vital to manage anxieties and maintain trust.
Microsoft’s Response
Microsoft played a critical role in addressing the vulnerabilities exploited by WannaCry. The company quickly released security patches to fix the EternalBlue exploit, which was the core of the attack. The rapid release of these patches demonstrated the importance of swift action in mitigating widespread threats. Additionally, Microsoft actively worked with security researchers to understand the attack vector and to identify further vulnerabilities.
This proactive approach was essential in preventing future attacks and demonstrated the critical role of collaboration in the fight against cybercrime.
Preventing Ransomware Attacks
Effective prevention strategies are crucial to safeguarding systems from ransomware attacks. Proactive measures are far more effective than reactive measures. Implementing robust security measures can prevent attacks from happening in the first place.
- Regular Software Updates: Maintaining up-to-date software is essential. Software vulnerabilities are frequently exploited by attackers. Keeping operating systems, applications, and security software current significantly reduces the attack surface and mitigates the risk of successful exploits.
- Strong Passwords and Multi-Factor Authentication (MFA): Implementing strong passwords and MFA adds an extra layer of security. This makes it harder for attackers to gain unauthorized access to systems. Using a password manager and enabling MFA can significantly enhance security posture.
- Email Security: Implementing email security measures, such as spam filters and anti-phishing tools, is critical. Ransomware often spreads through malicious email attachments or links. By filtering out these threats, the risk of infection can be significantly reduced.
- Regular Backups: Regular data backups are crucial for recovering from ransomware attacks. Data backups provide a means to restore systems and data without paying ransoms. Offsite backups are recommended for added security.
Preventing Ransomware on Older Operating Systems
Older operating systems, such as Windows XP, often lack the latest security updates and patches. This leaves them vulnerable to exploits.
| Method | Description | Relevance to Older Systems |
|---|---|---|
| System Isolation | Isolating vulnerable systems from the network can prevent the spread of malware. | Essential; limits the potential damage from compromised systems. |
| Regular Scans | Employing antivirus and anti-malware software for regular scans. | Critical; older systems often lack up-to-date threat definitions. |
| User Education | Training users to recognize and avoid phishing attempts and suspicious links. | Highly relevant; user error is a common vector for ransomware attacks. |
| Endpoint Detection and Response (EDR) | Implementing advanced threat detection and response tools. | Provides a valuable layer of protection; however, may not be feasible for all older systems. |
Importance of Regular Updates
Regular security updates and software patching are paramount in preventing future ransomware attacks.
Failing to apply security patches leaves systems vulnerable to known exploits. The WannaCry attack underscored the criticality of prompt updates. By keeping software current, organizations can significantly reduce their attack surface and bolster their security posture. Proactive patching is crucial to mitigating the risk of future attacks.
Lessons Learned and Future Implications
The WannaCry ransomware attack, a devastating global cyber incident, exposed critical weaknesses in the cybersecurity landscape. It underscored the vulnerability of outdated systems and the potential for widespread disruption when exploits target those systems. Understanding the lessons learned from this attack is crucial for building more resilient defenses against future threats.The WannaCry attack highlighted the urgent need for proactive security measures and robust incident response plans.
It also revealed the interconnectedness of the digital world, demonstrating how a single vulnerability can quickly escalate into a significant global crisis. This understanding is paramount to shaping future security strategies.
Key Lessons Learned Regarding Cybersecurity Vulnerabilities and Incident Response
The WannaCry attack exposed the critical importance of timely patching. Organizations, especially those utilizing older operating systems like Windows XP, often failed to apply critical security updates promptly. This failure created a substantial vulnerability, allowing the ransomware to spread rapidly. Furthermore, the attack highlighted the need for robust incident response plans and the ability to quickly contain and mitigate the impact of cyberattacks.
Effective communication, rapid threat identification, and decisive action are vital for successful incident response.
Influence of the Attack on the Development of New Security Tools and Protocols
The WannaCry attack prompted a significant evolution in cybersecurity tools and protocols. Development of advanced threat detection systems capable of identifying and responding to zero-day exploits became a critical priority. Furthermore, improved vulnerability management practices were adopted, with emphasis on proactive patching and vulnerability scanning. The development of automatic security update deployment systems gained momentum.
Emerging Trends in Ransomware Attacks and Implications for Security Practices
Ransomware attacks are evolving, adopting new tactics and targeting diverse systems. The increasing sophistication of ransomware, its targeting of critical infrastructure, and the rise of double extortion tactics (threatening to leak data in addition to encrypting it) pose considerable risks. Organizations need to anticipate these evolving threats and adjust their security strategies accordingly. Furthermore, the trend toward ransomware-as-a-service (RaaS) models empowers less-skilled actors to launch sophisticated attacks, further complicating the threat landscape.
Comparison of Pre- and Post-WannaCry Security Landscape
| Aspect | Pre-WannaCry | Post-WannaCry |
|---|---|---|
| Vulnerability Management | Often reactive, relying heavily on manual patching and infrequent vulnerability assessments. | Proactive, incorporating automated patching, vulnerability scanning, and security information and event management (SIEM) systems. |
| Incident Response | Often slow and disorganized, with limited ability to contain and mitigate the impact of attacks. | More structured and well-defined, with incident response teams trained and equipped to respond to sophisticated threats. |
| Security Awareness Training | Limited, often focusing on basic computer hygiene. | More comprehensive, addressing the growing sophistication of social engineering and phishing attacks. |
| Security Tooling | Limited in scope and functionality. | More sophisticated, incorporating advanced threat detection, intrusion prevention systems (IPS), and threat intelligence feeds. |
The table illustrates the substantial shift in cybersecurity practices and technologies. The WannaCry attack served as a catalyst for significant advancements in protecting systems against advanced attacks.
Illustrative Case Studies
The WannaCry ransomware attack showcased the devastating consequences of unpatched systems, particularly impacting organizations lacking robust cybersecurity measures. This section delves into specific case studies, highlighting the varied responses and outcomes, from initial impact to recovery and future mitigation strategies. Understanding these real-world scenarios provides valuable insights into the importance of proactive security measures and well-defined incident response plans.
Impact on a Healthcare Organization
The WannaCry attack crippled a major European healthcare provider, disrupting critical operations and patient care. The ransomware encrypted sensitive patient data, halting diagnostic tools and emergency services. This disruption underscored the severe consequences of cyberattacks on essential services, especially those reliant on interconnected digital systems. The attack exposed vulnerabilities in the organization’s outdated infrastructure and lack of comprehensive security protocols.
Recovery Steps Taken by a Multinational Corporation
A multinational corporation, heavily reliant on its global network, adopted a phased recovery approach. First, the organization isolated infected systems to prevent further spread. Second, a forensic analysis team meticulously investigated the attack vector and identified vulnerabilities. Third, the company implemented emergency backup and restoration procedures, restoring critical data from secure offsite backups. Finally, a comprehensive security audit was conducted to identify and address weaknesses in the system.
These steps demonstrated the need for a structured recovery plan and the importance of secure data backups.
Mitigation Strategies Employed by a Small Business, Microsoft windows xp security patch wannacry ransomware attack
A small business, initially unaware of the threat, implemented several mitigation strategies after the attack. They upgraded their operating systems to patched versions, implemented robust antivirus software, and educated employees on phishing and social engineering tactics. The company also established a security awareness training program to raise employee vigilance. These proactive measures, though seemingly simple, helped prevent similar future attacks and demonstrated the effectiveness of basic security practices for all businesses.
Importance of Incident Response Plans and Recovery Processes
A research organization, known for its sensitive data, experienced a WannaCry attack. Their pre-existing incident response plan proved crucial in containing the damage. The plan, which Artikeld specific roles and responsibilities, allowed for a swift and coordinated response, isolating infected systems, initiating data recovery, and communicating with stakeholders. The organization’s ability to recover swiftly and maintain operations highlighted the value of a well-defined incident response plan and the importance of data backups.
Closure
In conclusion, the Microsoft Windows XP security patch WannaCry ransomware attack served as a stark reminder of the critical importance of timely security updates and robust incident response strategies. The attack highlighted the vulnerabilities of outdated systems and the devastating financial and operational consequences of neglecting cybersecurity best practices. Lessons learned from this incident continue to shape modern cybersecurity protocols, emphasizing the need for proactive measures to prevent similar future attacks.