EDU 220 Strata Firewalls at Scale ILT Promo dives deep into the world of network security. This intensive, hands-on training will equip you with the knowledge and skills to master Strata firewalls in a large-scale environment. We’ll explore key features, benefits, and practical application, using real-world case studies to solidify your understanding.
Designed for experienced network professionals, this ILT course provides a structured curriculum covering everything from foundational concepts to advanced strategies. Interactive exercises, group activities, and a supportive learning environment will ensure your success in mastering these crucial technologies. Get ready to elevate your network security expertise!
Introduction to EDU 220 Strata Firewalls at Scale ILT Promo
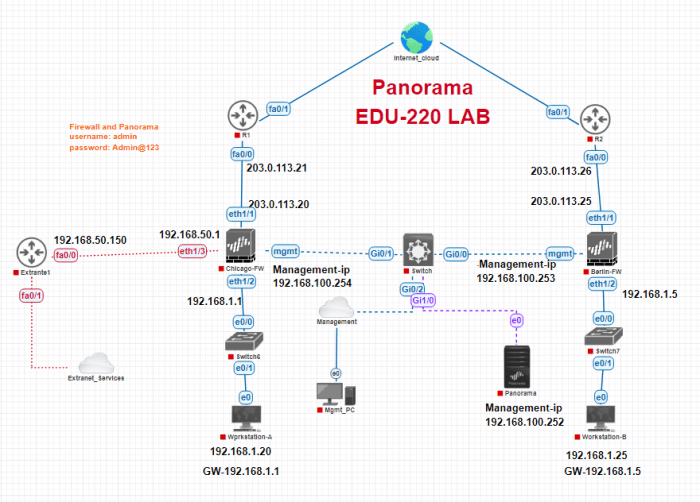
This ILT (Instructor-Led Training) promotion for EDU 220 focuses on the critical role of Strata Firewalls in modern network security. The course dives deep into the intricacies of deploying and managing these sophisticated systems at scale, equipping participants with the knowledge and skills necessary to secure complex network infrastructures. This comprehensive training will provide a practical understanding of how to effectively utilize Strata Firewalls to mitigate threats and enhance network resilience.Strata firewalls represent a significant advancement in network security, leveraging advanced algorithms and sophisticated architectures to protect against a wide array of cyber threats.
They are specifically designed to provide high-performance, comprehensive security across large-scale networks, offering granular control and advanced threat intelligence integration.
Definition of Strata Firewalls
Strata firewalls are high-performance, next-generation firewalls engineered for large-scale network environments. They incorporate advanced threat intelligence and deep packet inspection capabilities, enabling comprehensive protection against various cyberattacks. They are distinguished by their ability to process massive amounts of network traffic with minimal latency, a critical feature for modern enterprise networks.
Key Features and Benefits of Strata Firewalls
Strata firewalls offer a multitude of features designed to enhance network security and efficiency. These features include:
- High Performance: Designed to handle massive volumes of network traffic, enabling high-speed data transfer and processing with minimal latency. This is crucial for large enterprises handling significant bandwidth demands. For example, a large e-commerce company handling millions of transactions per day will require a firewall that can keep pace.
- Granular Control: Allow for precise control over network traffic through advanced rule-based filtering and access control lists (ACLs). This granular control enables customized security policies tailored to specific organizational needs and sensitive data. For example, a financial institution might need extremely granular control over access to its trading systems.
- Advanced Threat Intelligence: Integrate real-time threat intelligence feeds, enabling proactive detection and mitigation of emerging cyber threats. This helps organizations stay ahead of evolving attack vectors, crucial in today’s dynamic threat landscape. For example, the integration of an up-to-the-minute database of known malware can provide crucial insights into threats.
- Deep Packet Inspection: Analyze the contents of network packets to identify malicious activities beyond basic header information. This allows for a more comprehensive security posture by detecting sophisticated attacks that evade basic signature-based detection methods. For example, a deep packet inspection can uncover hidden malicious code within a seemingly benign file.
Target Audience for this ILT Promotion
This ILT is designed for network administrators, security engineers, and IT professionals responsible for deploying and managing Strata firewalls within large-scale enterprise networks. This includes those who are seeking advanced knowledge and practical experience in deploying and managing such complex systems, ensuring that the target audience is well-equipped to handle the tasks required.
Learning Objectives for EDU 220
Upon successful completion of the EDU 220 course, participants will be able to:
- Understand the fundamental architecture and functionalities of Strata firewalls.
- Deploy and configure Strata firewalls within a large-scale network environment.
- Implement and manage security policies and access control lists (ACLs).
- Monitor and troubleshoot Strata firewall performance and security issues.
- Integrate threat intelligence feeds into the Strata firewall system.
Format of the ILT Promo
The EDU 220 ILT promotion will be delivered via an instructor-led, interactive format, ensuring maximum engagement and knowledge retention. The course will span five days and will be held at the training facility. Detailed course schedules and material information will be provided.
Curriculum Overview
This section details the structure and content of the EDU 220 Strata Firewalls at Scale ILT course. It Artikels the modules, their objectives, and the practical exercises to solidify understanding of large-scale firewall deployments. The course is designed to equip students with the skills and knowledge to effectively manage and configure strata firewalls in a complex environment.
Course Modules and Time Allocation
The course is divided into modules to facilitate focused learning and progressive skill development. The following table provides a breakdown of each module, its description, learning objectives, and estimated duration.
| Module Name | Description | Learning Objectives | Estimated Time |
|---|---|---|---|
| Introduction to Strata Firewalls | Overview of Strata firewall architecture, key components, and their functionalities. | Define strata firewalls and their purpose. Identify key components and their roles. Understand the core concepts of strata firewall deployment. | 2 days |
| Configuration and Management | Detailed hands-on configuration of Strata firewalls, covering policies, rules, and access control lists. | Configure basic and advanced firewall rules. Manage users and access control effectively. Implement security policies. | 3 days |
| High Availability and Redundancy | Understanding and configuring high availability features to ensure continuous operation of the firewall system. | Configure failover mechanisms for firewall systems. Implement load balancing strategies. | 2 days |
| Security Policies and Best Practices | Implementing and maintaining effective security policies for a strata firewall system. | Develop and implement comprehensive security policies. Understand security best practices for strata firewalls. Identify and mitigate potential security vulnerabilities. | 2 days |
| Troubleshooting and Advanced Topics | Troubleshooting common issues in strata firewall configurations and exploring advanced features. | Diagnose and resolve common firewall issues. Explore advanced firewall features like intrusion prevention systems. | 2 days |
Module Content Details
Each module dives deep into specific aspects of strata firewall management. The Introduction module lays the groundwork for understanding the core concepts of strata firewall architecture. The configuration and management module emphasizes practical application of firewall rules and policies. High availability and redundancy is crucial for maintaining business continuity, and the corresponding module provides hands-on experience in setting up such configurations.
Security policies and best practices module focuses on ensuring that the firewalls are correctly configured to match the organization’s security needs. Finally, the troubleshooting and advanced topics module covers advanced topics such as intrusion prevention systems.
Key Concepts and Skills
Students will gain a comprehensive understanding of the following key concepts:
- Strata firewall architecture and components
- Firewall rule creation and management
- High availability and redundancy implementation
- Security policy development and enforcement
- Firewall troubleshooting and issue resolution
They will also develop practical skills in configuring, managing, and troubleshooting strata firewalls in large-scale deployments.
Practical Exercises and Labs
The course incorporates hands-on exercises and labs throughout each module to reinforce theoretical concepts. These exercises provide practical experience in configuring and managing strata firewalls.
- Hands-on configuration of firewall rules and policies.
- Implementing high availability and failover mechanisms.
- Troubleshooting common firewall issues.
- Developing and implementing security policies for large-scale deployments.
Key Technologies
The course utilizes various key technologies, including:
- Strata firewall platform (specific vendor/product)
- Network management tools (e.g., command-line interfaces, GUI)
- Security policy development tools
- Troubleshooting tools and techniques
AL Strategies for Strata Firewall Training
Effective Strata Firewall training at scale requires a multi-faceted approach that leverages various learning styles and engagement techniques. This approach should go beyond passive lecture and instead actively involve learners in the learning process, promoting deeper understanding and knowledge retention. This section will Artikel best practices for teaching Strata Firewalls, emphasizing interactive elements, real-world applications, and diverse learning methodologies.
Best Practices for Teaching Strata Firewalls at Scale
Strategies for delivering effective training at scale necessitate a departure from traditional, lecture-based approaches. Successful instructors should adapt their teaching methods to engage learners and maximize knowledge retention. This involves a shift towards active learning, where learners are not just passive recipients of information but active participants in the learning process.
- Prioritize Active Learning Techniques: Active learning strategies like group discussions, case studies, and hands-on exercises enhance engagement and comprehension. This approach promotes deeper understanding and long-term knowledge retention compared to passive learning methods.
- Employ Interactive Exercises: Interactive exercises are crucial for solidifying theoretical concepts and applying them to real-world scenarios. These could include simulations, quizzes, and practical labs where learners configure and troubleshoot Strata Firewalls. For instance, simulating common attack vectors allows learners to experience firsthand how firewalls mitigate them.
- Leverage Real-World Case Studies: Real-world case studies illustrate how Strata Firewalls are deployed and managed in diverse environments. These examples provide practical context, demonstrating how theoretical knowledge translates into tangible applications. For instance, a case study detailing a successful implementation of a Strata Firewall in a high-security environment can inspire practical applications for future deployments.
Role of Interactive Exercises and Group Activities
Interactive exercises and group activities foster a collaborative learning environment. These activities encourage learners to work together, discuss concepts, and share insights. This fosters a deeper understanding of the material and promotes knowledge retention.
Just saw the Edu 220 Strata Firewalls at Scale ILT promo, which is super interesting. Meanwhile, the Android 12 beta 4 rolling out now brings us closer to the final release and improved platform stability, as seen here. This means more stable systems, and that’s a positive for future network security developments. Hopefully, the Edu 220 Strata Firewalls at Scale ILT promo will address those very concerns, keeping pace with the latest advancements.
- Collaborative Problem Solving: Group activities, such as collaborative problem-solving sessions, allow learners to engage in critical thinking and apply their knowledge to complex scenarios. This can involve designing firewall rules to address specific security threats, which is a key aspect of understanding Strata Firewall configurations.
- Peer-to-Peer Learning: Group activities encourage peer-to-peer learning, where learners can explain concepts to each other, clarify doubts, and gain different perspectives. This dynamic exchange of ideas promotes a richer understanding of the material.
Utilizing Real-World Case Studies for Practical Application
Incorporating real-world case studies offers a practical approach to Strata Firewall training. By drawing upon real-world examples, learners gain a clearer understanding of how theoretical knowledge translates into practical applications.
- Demonstrate Practical Applications: Case studies demonstrate how firewalls are implemented and managed in various environments. This is critical for learners to grasp the practical applications of Strata Firewalls.
- Analyze Security Threats and Mitigation Strategies: Analyzing case studies that detail security breaches or vulnerabilities, alongside the mitigation strategies used, allows learners to comprehend the importance of proper Strata Firewall configuration.
Comparing Different AL Methods for Knowledge Retention
Different active learning methods have varying effects on knowledge retention. Choosing the most suitable method depends on the specific learning objectives and the learner’s characteristics.
- Gamification: Incorporating game mechanics, such as points, badges, and leaderboards, can enhance learner motivation and engagement, making the learning process more enjoyable and effective. This is especially useful in promoting active participation in simulations.
- Simulations and Practical Labs: Simulations and practical labs allow learners to apply their knowledge in a risk-free environment, providing invaluable experience and improving their understanding of real-world scenarios.
- Discussion Forums and Online Collaboration: Facilitating online discussion forums and collaborative projects can foster peer-to-peer learning, enabling learners to share their knowledge and gain different perspectives.
Visual Aids and Demonstrations in Training
Visual aids and demonstrations play a vital role in making complex concepts easier to grasp.
- Visual Representations: Diagrams, flowcharts, and other visual representations can effectively illustrate the inner workings of Strata Firewalls, enhancing understanding and retention. For instance, visualizing firewall rule sets using flowcharts can provide a clearer picture of how data packets are processed.
- Hands-on Demonstrations: Hands-on demonstrations of firewall configuration and troubleshooting procedures provide practical insights and reinforce theoretical knowledge. This includes showing how firewalls respond to different types of network traffic.
Assessment and Evaluation: Edu 220 Strata Firewalls At Scale Ilt Promo
Assessing student understanding of complex topics like strata firewalls requires a multifaceted approach. This section Artikels the methods we’ll employ to gauge learning and ensure effective knowledge retention. We’ll look at different assessment types, criteria for evaluating comprehension, and the vital role of practical exercises and feedback. Finally, we’ll explore ways to measure the success of this entire ILT program.
Assessment Methods
A comprehensive assessment strategy is crucial for measuring student learning outcomes. Different assessment methods offer unique insights into understanding and application.
| Assessment Type | Description | Purpose | Weighting |
|---|---|---|---|
| Quizzes | Short, frequent assessments covering specific modules. | Assess immediate understanding of key concepts and identify areas needing further attention. | 20% |
| Midterm Exam | Comprehensive exam evaluating understanding of core concepts across multiple modules. | Measure overall knowledge and identify potential gaps in learning. | 30% |
| Practical Exercises | Hands-on activities applying learned concepts to real-world scenarios. | Assess students’ ability to apply knowledge in practical situations and develop problem-solving skills. | 30% |
| Final Exam | A final, comprehensive assessment covering all the material. | Determine the overall mastery of the entire curriculum. | 20% |
Evaluation Criteria
Evaluating student comprehension goes beyond simply getting correct answers. We’ll assess understanding of key concepts like firewall rule creation, security protocols, and network topology. This includes assessing not only the factual knowledge but also the ability to apply that knowledge to novel situations.
- Accuracy: Correct application of firewall rules and configurations. Example: Correctly blocking malicious IP addresses.
- Efficiency: Ability to achieve the desired outcome with minimal resources or time. Example: Creating firewall rules that effectively block malicious traffic without unnecessarily impacting legitimate users.
- Problem-Solving: Demonstrating the ability to analyze scenarios, identify problems, and develop effective solutions. Example: Troubleshooting a firewall issue and devising a solution.
- Understanding: The ability to explain the “why” behind the “how.” Example: Articulating the rationale behind a particular firewall rule.
Role of Quizzes, Exams, and Practical Exercises
Quizzes provide regular feedback on student comprehension. Exams are designed to assess a broader range of knowledge and skills, and practical exercises are crucial for applying those skills in realistic settings.
- Quizzes: Frequent quizzes reinforce learning and identify areas needing attention. They focus on immediate understanding of specific concepts.
- Exams: Midterm and final exams assess comprehensive knowledge and the application of key concepts across the entire course. This broader assessment allows for a deeper understanding of the student’s overall grasp.
- Practical Exercises: Practical exercises simulate real-world scenarios. They test students’ abilities to implement and troubleshoot firewall configurations. This hands-on experience is vital for mastery.
Constructive Feedback
Providing feedback that is both informative and supportive is key to student development. Constructive criticism helps students identify areas for improvement and reinforces good practices.
- Specific and Detailed Feedback: Focus on specific aspects of the student’s work. Provide clear explanations and examples. Avoid general comments like “good job.” Instead, offer feedback like “Your firewall rule for port 80 is correctly configured, but you could enhance it by adding a description for future reference.”
- Emphasis on Learning: Frame feedback in terms of learning and development, not just grades. Help students understand their mistakes and how to avoid them in the future. Example: “This firewall rule configuration has a minor vulnerability; consider using more robust authentication protocols to mitigate this risk.”
- Opportunities for Improvement: Suggest specific steps for improvement and offer resources to help students achieve those improvements. This could involve specific readings, online tutorials, or follow-up exercises.
Measuring ILT Promo Effectiveness
Evaluating the success of the ILT program requires measuring not just student performance but also the overall impact on the program.
- Pre- and Post-Assessments: Measuring student knowledge and skills before and after the program helps quantify the learning gained. This allows us to compare the initial knowledge base with the post-training knowledge level.
- Course Completion Rates: Tracking the percentage of students who complete the entire program provides an indication of its engagement and effectiveness.
- Post-Program Feedback: Gathering feedback from participants about the program’s quality and usefulness helps in improving future iterations.
Technology and Resources
This section dives into the crucial technical aspects of the Strata Firewall at Scale ILT promo. We’ll Artikel the necessary hardware, software, and networking configurations, along with the supporting materials required for a successful learning experience. Understanding these prerequisites is essential for both participants and instructors to ensure a smooth and effective training program.
Technical Requirements for Participation
The ILT promo requires participants to have a basic understanding of networking concepts, including IP addressing, routing protocols, and firewall principles. A laptop with a recent operating system (Windows, macOS, or Linux) is necessary. Virtualization software like VMware Workstation Player or VirtualBox is also highly recommended for practicing hands-on exercises in a controlled environment. Participants should also have a stable internet connection with sufficient bandwidth to support online resources and interactive exercises.
Tools and Technologies for Hands-On Practice
Effective hands-on practice is crucial for mastering Strata Firewall deployments. We recommend using a virtualized lab environment. This will allow participants to experiment with configurations without impacting production networks. The virtualized environment should mirror real-world setups as closely as possible. Comprehensive documentation on the specific virtual machines or emulators used in the labs is vital for participants.
Software tools like Wireshark or tcpdump can be helpful for analyzing network traffic and debugging issues.
Supporting Documentation and Supplementary Materials
A comprehensive set of supporting documents will be provided, including detailed lab guides, configuration examples, and troubleshooting steps. These materials will be accessible through a dedicated online portal. Additionally, supplementary readings and reference materials will enhance understanding of the core concepts and advanced functionalities of Strata Firewalls. White papers, technical articles, and links to relevant online resources will be provided for further study.
Secure and Stable Learning Environment
Creating a secure and stable learning environment is paramount. A virtual lab environment with isolation features is ideal. The labs should be regularly updated to reflect the latest Strata Firewall features. This ensures the hands-on exercises remain relevant and practical. Network administrators should be involved in designing the virtual environment to ensure accurate representations of real-world scenarios.
This includes simulating various network topologies and potential security threats.
I’m digging into the EDU 220 Strata Firewalls at Scale ILT promo, and it got me thinking about cybersecurity vulnerabilities. Recent news about Kaspersky, Russian hackers, and the NSA document breach highlights the ever-present threat of malicious actors. Understanding how to secure networks like the ones covered in the EDU 220 Strata Firewalls at Scale ILT promo is more critical than ever, especially considering the risks highlighted by incidents like this kaspersky russian hackers nsa document breach.
This promo seems like a great way to learn practical skills to defend against similar attacks.
Resources for Successful Implementation
The resources needed for the ILT promo’s successful implementation include a dedicated instructor with extensive Strata Firewall expertise, a reliable virtual lab environment, and access to the online learning portal. Participants should have access to the lab environment and materials in advance of the training sessions. The necessary tools and documentation will be made available through the portal.
A dedicated support team will be available to address any technical issues that may arise during the training.
Promotion and Marketing Strategies
Promoting the EDU 220 Strata Firewall ILT effectively is crucial for attracting the right participants and maximizing ROI. A well-defined marketing strategy will ensure that the course reaches the target audience and generates the desired enrollment numbers. A targeted approach that considers various channels and compelling messaging is essential for success.
Promotion Channels
A multi-faceted approach utilizing diverse channels is key to reaching a broad spectrum of potential students. This approach considers various platforms and preferences to ensure maximum visibility and engagement.
| Channel | Description | Target Audience | Metrics |
|---|---|---|---|
| Social Media Marketing (LinkedIn, Twitter, Facebook) | Targeted ads, engaging posts, and collaborations with relevant influencers. | IT professionals, cybersecurity enthusiasts, and network administrators. | Reach, engagement (likes, shares, comments), website traffic, leads generated. |
| Industry Events and Conferences | Exhibiting at relevant industry events to network and showcase the course. | Professionals actively seeking upskilling opportunities. | Leads generated, brand awareness, course inquiries. |
| Email Marketing | Targeted email campaigns to nurture leads and promote the course to specific segments. | Previous course participants, IT professionals, and those who have expressed interest in networking. | Open rates, click-through rates, conversion rates, and email list growth. |
| Online Advertising (Google Ads, LinkedIn Ads) | Paid advertising campaigns on relevant platforms to reach a wider audience. | Individuals searching for specific cybersecurity training. | Cost-per-click, conversion rate, impressions, and qualified leads. |
| Partnerships with Educational Institutions | Collaborating with universities and colleges to promote the course to their students and alumni. | Students and alumni in computer science, cybersecurity, and related fields. | Partnership agreements, course enrollment numbers, and referrals. |
Key Messages
The key messages should clearly communicate the value proposition of the course. These messages should highlight the course’s unique benefits and position it as a valuable investment for participants.
Clear and concise messaging is paramount for successful promotion. Highlight the practical skills gained, the industry recognition, and the career advancement opportunities.
* Focus on practical application: Emphasize the hands-on experience and real-world scenarios covered in the course.
Highlight industry recognition
Showcase the course’s reputation and accreditation to build trust and credibility.
Showcase career advancement
Clearly Artikel how the course can help participants advance their careers and enhance their professional skillsets.
Value proposition
I’m digging into the EDU 220 Strata Firewalls at Scale ILT promo, and it got me thinking about the future of security. Recent news about Apple’s new vape tech patent application apple files new vape tech patent application is pretty interesting, but it also makes me wonder how these advancements will affect network security. Hopefully, the EDU 220 course will help me understand these complex issues better.
Clearly communicate the benefits of attending the course, emphasizing the return on investment.
Marketing Materials
Compelling marketing materials are essential for grabbing attention and generating interest. These materials should effectively communicate the course’s value proposition and appeal to the target audience.* Course brochure: A visually appealing brochure outlining the course curriculum, key features, and benefits.
Promotional videos
Short, engaging videos showcasing the course’s highlights and testimonials from past participants.
Landing page
A dedicated landing page providing detailed information about the course, including registration links.
Social media posts
Engaging posts that showcase the course content, speaker expertise, and student testimonials.
Call to Action
A clear and compelling call to action is essential for encouraging enrollment. The call to action should be concise, specific, and easy to understand.
“Enroll Now” or “Learn More” are effective examples of call to action phrases.
* Use compelling language: Employ strong action verbs to motivate potential students.
Make it prominent
Place the call to action prominently on all marketing materials.
Provide clear instructions
Guide participants effortlessly through the enrollment process.
Building Awareness, Edu 220 strata firewalls at scale ilt promo
Building awareness about the ILT promo requires a proactive and consistent effort. This involves reaching out to a wide audience using various platforms and strategies.* Engage with relevant communities: Participate in industry discussions and share valuable content.
Leverage social media
Share engaging content that resonates with the target audience.
Use paid advertising
Reach a wider audience through targeted advertising campaigns.
Participant Experience

This section delves into the anticipated learning journey for participants in the Strata Firewalls at Scale ILT program. It Artikels the interactive learning methods, the support infrastructure, and the processes for addressing any technical hurdles. A positive and productive learning environment is crucial for optimal knowledge absorption and skill development.
Interactive Learning Activities
The program emphasizes active learning through a variety of interactive methods. This approach ensures participants engage deeply with the material. Hands-on exercises and simulations are integral to developing practical skills in managing and configuring strata firewalls. These activities will provide opportunities for immediate feedback and reinforcement of concepts. For example, participants will engage in group problem-solving sessions, simulating real-world firewall management scenarios.
This collaborative approach fosters critical thinking and practical application of the knowledge acquired. Interactive demonstrations, case studies, and real-world examples further enhance understanding.
Support System
A comprehensive support system is in place to ensure a smooth learning experience for all participants. This includes dedicated instructors available throughout the program to answer questions and provide guidance. A dedicated online forum will be available for participants to connect, share insights, and seek assistance from their peers and instructors. Technical mentors will be available to provide individualized support.
This multi-layered support ensures participants feel supported and empowered to address challenges effectively.
Addressing Technical Issues
A structured process is in place to address any technical issues that may arise during the training. A dedicated helpdesk is available to provide prompt and effective assistance. Participants will receive clear instructions on how to report technical issues. Detailed troubleshooting guides and FAQs are readily accessible. The helpdesk is staffed by knowledgeable personnel who can resolve technical difficulties efficiently.
This proactive approach ensures a positive and productive learning environment, allowing participants to focus on learning without interruption.
Creating a Positive Learning Environment
Creating a positive and productive learning environment is paramount. This environment fosters an atmosphere of respect, collaboration, and active engagement. Facilitating open communication channels ensures participants feel comfortable asking questions and sharing their insights. Constructive feedback and encouragement are integral to the learning experience. Recognizing and appreciating individual contributions will motivate participants to actively participate and maximize their learning.
This supportive atmosphere allows participants to excel.
Outcome Summary
In conclusion, the EDU 220 Strata Firewalls at Scale ILT Promo offers a comprehensive and engaging learning experience. From introductory concepts to advanced strategies, participants will gain valuable skills and knowledge to effectively manage and secure large-scale networks. The course’s emphasis on practical application and interactive learning ensures that attendees leave with the ability to apply their new skills immediately.



