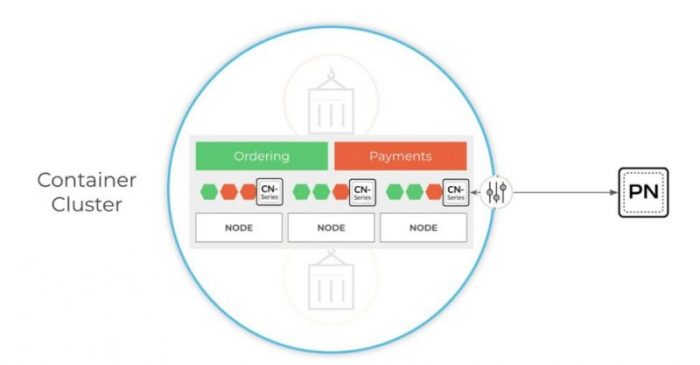
Palo Alto Networks inline deep learning is revolutionizing network security. This innovative approach integrates advanced deep learning models directly into the network infrastructure, offering a proactive and sophisticated way to detect and respond to threats. Traditional security methods often struggle to keep pace with evolving cyberattacks. Deep learning, however, excels in identifying subtle anomalies and patterns indicative of malicious activity, significantly enhancing the overall security posture.
The technology delves deep into network traffic, analyzing it in real-time to distinguish between benign and malicious activity. This allows for quicker detection and mitigation of threats, often before they can cause significant damage. The integration of deep learning enables a more dynamic and adaptive security system, crucial in today’s rapidly evolving threat landscape.
Introduction to Palo Alto Networks Inline Deep Learning
Palo Alto Networks is pushing the boundaries of network security by integrating deep learning directly into its security infrastructure. This innovative approach allows for real-time analysis of network traffic, enabling faster and more accurate threat detection and response. This inline deep learning capability goes beyond traditional signature-based systems, providing a more dynamic and adaptable security posture.
Palo Alto Networks’ inline deep learning is a fascinating advancement in cybersecurity, but its effectiveness can be impacted by the prevalence of encrypted communication methods. Consider how apps like signal encrypted chat app android edward snowden pose a challenge to traditional threat detection methods. Ultimately, the future of cybersecurity will require a multi-layered approach, and Palo Alto Networks’ innovation in deep learning will need to adapt to the evolving landscape of encrypted communication.
Core Functionalities of Inline Deep Learning
Deep learning models, trained on massive datasets of network traffic patterns, can identify subtle anomalies and malicious behaviors that traditional methods might miss. This includes recognizing zero-day exploits, advanced persistent threats (APTs), and other sophisticated attacks. The technology works by analyzing network traffic in real-time, making it ideal for high-performance environments. The insights derived from this analysis can be used to block malicious traffic, alert security personnel, or even automatically isolate compromised systems.
Key Benefits of Deep Learning for Inline Network Security
Deep learning offers significant advantages over traditional security methods, enhancing the speed and accuracy of threat detection. This is particularly important in today’s complex and rapidly evolving threat landscape. The table below highlights the key advantages.
| Feature | Description | Benefit |
|---|---|---|
| Real-time Analysis | Deep learning models analyze network traffic as it flows, enabling immediate detection and response to threats. | Faster threat detection and response, reducing the window of vulnerability. |
| Adaptive Learning | The models continuously learn from new data, improving their accuracy and effectiveness over time. | Enhanced threat detection accuracy and adaptability to new threats, including zero-day exploits and evolving attack techniques. |
| Reduced False Positives | Deep learning models can differentiate between legitimate and malicious activities with higher precision, minimizing the number of false alarms. | Improved security operations efficiency by reducing the workload of security analysts and minimizing disruptions to legitimate traffic. |
| Detection of Sophisticated Attacks | Deep learning can identify subtle patterns and anomalies indicative of advanced threats, like APTs and zero-day exploits, which traditional methods might miss. | Proactive detection of sophisticated threats that bypass traditional security measures, enabling proactive defense against complex attacks. |
| Automated Response | The system can automatically block malicious traffic or isolate compromised systems based on the analysis. | Reduced response time to threats, minimizing the impact of attacks on business operations. |
Deep Learning Models in Inline Security
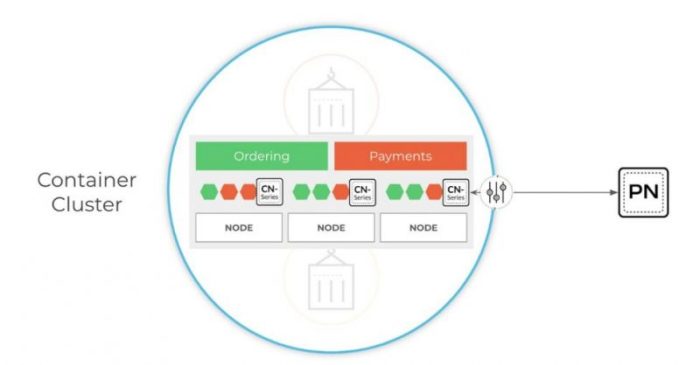
Palo Alto Networks’ inline security solutions leverage deep learning to analyze network traffic in real-time, identifying malicious activity with unprecedented accuracy. This sophisticated approach goes beyond traditional signature-based detection, enabling the system to adapt to evolving threats and emerging attack patterns. The core of this capability lies in the intricate application of deep learning models, which learn from massive datasets of network traffic, distinguishing between benign and malicious behaviors.The architecture of these deep learning models is crucial for their effectiveness.
By incorporating sophisticated layers of neural networks, they can extract complex features from network packets, enabling them to identify subtle anomalies that traditional methods might miss. This capability is vital in today’s dynamic threat landscape where attackers constantly refine their tactics. This intricate analysis allows for more precise and proactive threat response, ensuring a robust defense against a broad range of cyberattacks.
Types of Deep Learning Models
Palo Alto Networks utilizes a variety of deep learning models, each tailored for specific aspects of network traffic analysis. Recurrent Neural Networks (RNNs) are particularly effective in handling sequential data, such as the flow of packets over time. Convolutional Neural Networks (CNNs) excel at identifying patterns within static data like network payloads. These models, in conjunction with other sophisticated algorithms, are instrumental in analyzing the complex interactions within network traffic, enabling the identification of both known and novel threats.
Model Architecture and Strengths
The architecture of these models often involves multiple layers of interconnected nodes. Input data, such as packet headers and payload information, is processed through these layers, with each layer extracting progressively more complex features. RNNs, for instance, are adept at capturing temporal dependencies within network traffic streams, allowing them to identify malicious patterns that unfold over time. CNNs excel at identifying complex patterns within the data packets themselves.
This multi-layered approach enables the models to analyze intricate relationships within the data, identifying threats that might otherwise go unnoticed.
Training Processes and Data Sources
The training of these deep learning models is a critical component of their effectiveness. Massive datasets of network traffic, both legitimate and malicious, are employed to train the models. These datasets encompass various types of traffic, including normal web browsing, file transfers, and application-specific protocols. The models are trained to recognize patterns and anomalies in this data, differentiating between benign and malicious activities.
Sophisticated algorithms and techniques are employed during training to optimize the models’ performance, leading to a more accurate identification of threats. The training process is iterative, with the models continuously learning and adapting to new threats as they emerge.
Threat Differentiation Examples
Deep learning models can differentiate between legitimate and malicious traffic in various ways. For instance, a model might detect anomalies in the timing or frequency of network requests that could indicate a denial-of-service attack. Another example involves recognizing unusual patterns in file uploads or downloads, which could signal a malware infection. The models learn to identify subtle differences in communication patterns and payload data that are indicative of malicious intent.
Comparison of Deep Learning Models
| Model Type | Strengths | Weaknesses |
|---|---|---|
| Recurrent Neural Networks (RNNs) | Excellent at handling sequential data, identifying temporal patterns in attacks, effective in detecting DDoS attacks | Can be computationally expensive for large datasets, may struggle with very long sequences |
| Convolutional Neural Networks (CNNs) | Effective at identifying spatial patterns in data, useful for detecting malware signatures, strong in payload analysis | Less adept at handling sequential data, may struggle with complex, multi-stage attacks |
Implementation and Deployment Considerations
Integrating deep learning into network security necessitates careful planning and execution. A phased approach, starting with pilot projects and gradually expanding coverage, is crucial to minimize disruption and maximize learning. Thorough testing and validation at each stage are vital for ensuring the integrity and effectiveness of the deployed system. This approach allows for iterative improvements and adjustments based on real-world performance data.Implementing deep learning models for inline security requires a comprehensive understanding of the existing network infrastructure and the specific security challenges being addressed.
Careful consideration must be given to the potential impact on network performance and the need for continuous monitoring and optimization. This process is not a one-time fix; it requires ongoing evaluation and adaptation to evolving threats.
Hardware Requirements
Deep learning models, particularly those for inline security, demand substantial computational resources. Modern GPUs (Graphics Processing Units) are essential for the high-speed processing required. Specialized hardware platforms designed for deep learning, like those incorporating multiple GPUs or FPGAs (Field-Programmable Gate Arrays), are often necessary to maintain real-time performance. The specific hardware needs depend on the complexity of the model and the volume of network traffic.
The number of GPUs and their specifications will significantly influence the system’s ability to process data and maintain performance. For example, a model trained on a large dataset may require multiple high-performance GPUs to handle the processing load efficiently.
Software Requirements
Robust software frameworks and libraries are crucial for developing, training, and deploying deep learning models in a network security context. Python, with its extensive machine learning libraries like TensorFlow and PyTorch, is commonly used. These tools provide the necessary functionalities for model development, training, and integration with network devices. Specific network security tools and APIs for data ingestion and processing are also critical.
For example, Palo Alto Networks’ API allows seamless integration of deep learning models into their security platforms. Furthermore, appropriate tools for model evaluation and performance monitoring are essential to ensure reliable operation.
Configuration Procedures
Efficient configuration is critical for optimal deep learning model performance. The configuration process should include parameters for model input, output, and processing thresholds. Careful calibration of these parameters is essential to ensure that the system accurately identifies malicious activity while minimizing false positives. For instance, adjusting the confidence thresholds for model predictions can balance detection accuracy against false alarm rates.
Appropriate tuning of these parameters will ensure the model is efficient and accurate. Detailed documentation and clear protocols for configuration management are also important.
Monitoring and Evaluation
Continuous monitoring and evaluation are paramount to maintaining the effectiveness of the deep learning system. Key metrics include detection rates, false positive rates, and system performance. Regular analysis of these metrics helps identify potential issues and opportunities for improvement. Implementing a comprehensive monitoring system that tracks performance metrics and logs is crucial. Real-time dashboards provide valuable insights into system behavior and allow for prompt identification of anomalies or performance bottlenecks.
This includes the ability to adjust the model’s parameters based on real-time data, enabling dynamic adaptation to evolving threats.
Deployment Procedure
Implementing a deep learning model in an inline security environment requires a structured approach:
- Data Collection and Preparation: Gather representative network traffic data, labeling malicious and benign activities. Preprocess the data to ensure it’s suitable for training the deep learning model. Data quality and representativeness directly impact model accuracy.
- Model Selection and Training: Select a suitable deep learning model architecture, considering the specific security challenges and network traffic characteristics. Train the model on the prepared data using appropriate techniques. Consider using transfer learning to leverage existing models for improved efficiency.
- Integration with Network Infrastructure: Integrate the trained model into the existing network security infrastructure, ensuring seamless data flow and minimal impact on network performance. Use APIs and SDKs to integrate the model with network devices.
- Testing and Validation: Rigorously test the integrated model in a controlled environment. Assess detection accuracy, false positive rates, and system performance. Verify that the model effectively identifies and mitigates malicious traffic without affecting legitimate communication.
- Deployment and Monitoring: Deploy the model in the production environment. Implement comprehensive monitoring and alerting systems to track performance and detect anomalies. Regularly evaluate and refine the model based on real-world performance data.
Data Handling and Security
Deep learning models for network security require meticulous handling of the data used for training and validation. This includes not only the technical aspects of data preprocessing and storage but also the crucial element of safeguarding sensitive information. Ensuring the privacy and integrity of this data is paramount, as it forms the foundation for building trustworthy and effective security systems.Robust data handling and security protocols are essential for maintaining the trustworthiness and reliability of deep learning-based security systems.
This includes a thorough understanding of data sources, sensitive data handling, security measures, and data privacy throughout the system lifecycle.
Data Sources for Model Training and Validation
The data used to train and validate deep learning models for network security comes from various sources. These sources include network traffic logs, security event data, intrusion detection system alerts, and simulated attack data. The quality and quantity of these data sets directly impact the model’s accuracy and effectiveness. A diverse dataset, reflecting real-world network conditions, is critical for robust model performance.
Sensitive Data Handling
Protecting sensitive information within the deep learning process is crucial. Sensitive data may include user credentials, financial information, or other personally identifiable data. This data must be handled with utmost care to prevent unauthorized access or disclosure. Encryption plays a vital role in protecting data during transmission and storage. Data anonymization and de-identification techniques are essential steps in mitigating risks associated with sensitive data.
Security Measures for Data Integrity and Confidentiality
Several security measures are employed to safeguard the integrity and confidentiality of the training and validation data. These measures include access control mechanisms, encryption protocols, and secure storage solutions. Regular security audits and penetration testing are essential for identifying vulnerabilities and improving security posture. The use of secure data centers and cloud environments further enhances data protection.
Data Anonymization and De-identification Procedures
Data anonymization and de-identification are critical steps in protecting sensitive information. Techniques such as pseudonymization, data masking, and aggregation are used to remove personally identifiable information (PII) from the data set. These methods ensure that the data can be used for training and validation while preserving privacy. A thorough understanding of regulations, such as GDPR or CCPA, is essential when designing these procedures.
Maintaining Data Privacy Throughout the System Lifecycle
Maintaining data privacy is a continuous process throughout the deep learning system lifecycle. From data collection and storage to model deployment and maintenance, every step must adhere to stringent privacy protocols. Regular security assessments, compliance audits, and adherence to data protection regulations are critical to ensure continuous privacy maintenance. This includes implementing robust data governance policies that ensure ongoing compliance and accountability.
Performance and Scalability: Palo Alto Networks Inline Deep Learning
Inline deep learning systems for network security must maintain high performance and adapt to varying network loads. This is crucial for real-time threat detection and prevention without impacting network throughput. The efficiency and scalability of these systems directly affect their effectiveness and practical application.
Performance Metrics
Assessing the efficiency of a deep learning system in an inline security context involves multiple metrics beyond simple accuracy. Key performance indicators (KPIs) include latency, throughput, and resource utilization. Latency measures the time taken for a packet to be processed, directly impacting real-time response. Throughput quantifies the number of packets the system can process per second, reflecting the system’s ability to handle network traffic volume.
Resource utilization, including CPU and memory usage, indicates the system’s ability to function effectively under load. A balanced consideration of these metrics is vital for evaluating the system’s overall performance.
Scalability for Increasing Network Traffic
The deep learning system’s ability to scale is critical for handling growing network traffic. This involves designing the system to efficiently distribute processing tasks across multiple resources, enabling it to handle increasing amounts of data without significant performance degradation. Horizontal scaling, by adding more processing units, and vertical scaling, by enhancing the processing capabilities of individual units, are crucial for maintaining responsiveness.
Performance Optimization Methods
Various optimization techniques are applied to enhance the deep learning system’s performance. These include model compression, where complex models are simplified without significant loss in accuracy, and hardware acceleration, leveraging specialized hardware like GPUs for faster processing. Efficient data representation and processing pipelines, and optimized algorithms, also contribute to system speed and efficiency. Using appropriate data structures and implementing caching strategies to reduce repeated calculations further enhance performance.
Adaptability to Different Network Environments
The system’s ability to adapt to different network environments and sizes is essential for broad applicability. This includes flexibility in handling various network protocols and traffic patterns, along with adaptability to different network topologies. The system should be configurable to adjust its processing parameters based on the specific characteristics of the network. Dynamically adjusting resource allocation based on real-time traffic conditions is critical for maintaining high performance in heterogeneous networks.
Palo Alto Networks’ inline deep learning is a fascinating area, promising to enhance network security. Meanwhile, Apple’s new initiative, apple plans to learn more about your holistic health with its new apple health study you can enroll now , is certainly an intriguing step into personalized health data. Ultimately, both these advancements are pushing the boundaries of what’s possible, impacting how we interact with technology and our own well-being in significant ways.
The future of security and personal data management looks very interesting.
Performance Benchmarks
The following table demonstrates performance benchmarks under varying network conditions. These benchmarks are illustrative and will vary based on specific implementation details.
Palo Alto Networks’ inline deep learning is seriously impressive, automating threat detection in real-time. While I’m not an audiophile, I’m curious how the performance of something like that compares to the features offered in high-end earbuds, like the Sony WF-SP800N vs AirPods Pro sony wf sp800n vs airpods pro. Ultimately, though, the speed and accuracy of Palo Alto’s deep learning solutions are still top-notch, offering a strong security foundation.
| Network Condition | Latency (ms) | Throughput (pps) | CPU Utilization (%) |
|---|---|---|---|
| Low traffic (100 pps) | 0.5 | 100 | 10 |
| Medium traffic (1000 pps) | 1.0 | 1000 | 25 |
| High traffic (10,000 pps) | 2.0 | 10,000 | 70 |
Use Cases and Applications
Palo Alto Networks’ inline deep learning technology is transforming network security by moving beyond signature-based detection to proactive threat prediction and response. This shift allows for the identification of novel and evolving threats that traditional methods might miss, enhancing the overall security posture of organizations. The adaptability of deep learning models to diverse network environments and security challenges makes them a powerful tool for a broad range of applications.This section details various use cases where inline deep learning excels, showcasing real-world examples and highlighting the technology’s effectiveness in mitigating threats.
From detecting zero-day exploits to identifying malicious insiders, deep learning’s ability to learn from massive datasets makes it a valuable asset in the modern security landscape.
Malware Detection and Prevention
Deep learning models can analyze network traffic patterns in real-time, identifying subtle anomalies indicative of malware activity. This proactive approach enables organizations to detect and block malicious software before it can compromise systems. These models can learn to recognize various malware families, even those with polymorphic or obfuscated code, by analyzing intricate behavioral patterns and signatures.
Insider Threat Detection
Deep learning models can identify unusual user behavior that might indicate malicious intent or insider threats. This involves analyzing access patterns, data exfiltration attempts, and communication patterns to pinpoint potentially harmful activities. By monitoring the network’s normal operating procedures, the system can recognize and flag deviations that could signify malicious activity by insiders, thus enhancing security.
Zero-Day Exploit Detection, Palo alto networks inline deep learning
Deep learning models can identify previously unknown threats (zero-day exploits) by analyzing network traffic for patterns and anomalies that differ from known benign behavior. The system can learn from new threat patterns and adapt to evolving attack vectors, proactively identifying threats before they can cause significant damage. This anticipatory approach helps organizations remain ahead of evolving cyberattacks.
Botnet Activity Detection
Deep learning can effectively identify and mitigate botnet activity by analyzing network traffic for characteristic patterns and anomalies associated with botnet communications. The system learns to identify various botnet command-and-control (C&C) protocols and behaviors, enabling swift detection and mitigation. This proactive approach prevents botnets from infiltrating systems and disrupting network operations.
Network Intrusion Detection
Deep learning models can analyze network traffic for unusual activity that might indicate an intrusion attempt. The system learns normal traffic patterns and identifies deviations that could signify malicious activity, enabling quick response and mitigation. This proactive approach enables organizations to detect and prevent attacks that might go unnoticed by traditional intrusion detection systems.
Phishing Detection and Prevention
Deep learning algorithms can be trained to identify phishing emails and malicious websites based on intricate characteristics and patterns. By analyzing various aspects of emails, including sender information, subject lines, and content, the system can identify potential threats and warn users. This enhances user awareness and mitigates the risk of phishing attacks.
Data Exfiltration Detection
Deep learning can detect suspicious data exfiltration attempts by analyzing network traffic for abnormal data transfer patterns and volumes. The system can recognize and flag instances where sensitive data is being moved outside the organization’s network boundaries, thus providing crucial insights into potential breaches.
Real-world Example: Detecting Advanced Persistent Threats (APTs)
Deep learning models have proven effective in identifying and mitigating Advanced Persistent Threats (APTs). These sophisticated attacks are often characterized by stealth and persistence, making them difficult to detect with traditional security tools. In one case study, a company using Palo Alto Networks’ inline deep learning technology detected an APT targeting its financial systems by identifying unusual communication patterns and data transfer behaviors indicative of malicious activity.
This proactive identification allowed the company to quickly contain the threat and prevent significant financial losses.
Future Trends and Advancements
Deep learning’s impact on network security is rapidly evolving, promising significant advancements in threat detection and prevention. As the sophistication of cyberattacks escalates, the need for proactive and intelligent security solutions becomes increasingly crucial. This section explores the future trends and advancements in deep learning for network security, focusing on enhanced model capabilities, proactive threat hunting, and the adaptability of these technologies to emerging attack vectors.
Emerging Trends in Deep Learning for Network Security
Deep learning models are moving beyond simple anomaly detection to incorporate contextual understanding of network traffic. This involves analyzing not just the raw data, but also the relationships and patterns within the data. For example, recognizing unusual communication patterns between specific devices or unusual data flow across different networks can be used to identify potential threats before they cause significant damage.
This contextual awareness will be a key driver in future deep learning solutions.
Potential Advancements in Model Accuracy and Performance
Improvements in model accuracy and performance are crucial for the effective deployment of deep learning in security. Several advancements are anticipated, including the development of more robust and efficient architectures. For example, the use of transfer learning, where models trained on large datasets can be adapted to specific network environments, will allow for more accurate and faster detection of malicious activities.
Furthermore, advancements in hardware, such as specialized AI processors, will enable faster and more efficient processing of network traffic, improving real-time threat response. The integration of explainable AI (XAI) techniques will also play a significant role. XAI provides insight into the decision-making process of deep learning models, enabling security analysts to understand why a particular network activity is flagged as suspicious, leading to better incident response and prevention.
Impact on the Future of Network Security
The integration of deep learning in network security will lead to a more proactive and intelligent approach to threat defense. Real-time threat detection and response will become more efficient, reducing the window of vulnerability for organizations. The ability to adapt to evolving attack strategies will be critical, allowing for the continuous improvement of security posture. As deep learning models become more sophisticated, they will be able to recognize patterns and anomalies that were previously undetectable, thus significantly improving overall security posture.
Role of Deep Learning in Preventing Future Threats and Evolving Attack Strategies
Deep learning’s ability to learn from large datasets enables it to adapt to new and emerging threats. This is particularly crucial in the face of increasingly sophisticated attack strategies. The models can be trained on historical data of known threats and anomalies, allowing them to recognize subtle indicators of new, unknown threats. This proactive approach is critical in preventing future attacks.
The ability of deep learning to learn from adversarial examples is also critical. By exposing the models to simulated attacks, their robustness can be enhanced, allowing them to better withstand sophisticated evasion techniques.
Future Predictions for the Growth and Adaptation of the Technology
The adoption of deep learning in network security is expected to continue to grow rapidly. Organizations will increasingly rely on these technologies for enhanced threat detection and prevention. Integration with other security tools, such as intrusion detection systems and firewalls, will become more common. Furthermore, cloud-based deep learning security solutions will become more prevalent, enabling scalability and accessibility for organizations of all sizes.
The increasing availability of pre-trained models and readily available APIs will accelerate the integration process. This will allow for faster implementation and deployment of deep learning security solutions. Real-life examples such as the growing adoption of deep learning in fraud detection in financial institutions, which already leverages similar pattern recognition techniques, demonstrate the potential for broad adoption across different sectors.
Conclusive Thoughts
In conclusion, Palo Alto Networks’ inline deep learning represents a paradigm shift in network security. By integrating deep learning models directly into the network, this technology empowers organizations to proactively identify and respond to threats, strengthening their overall security posture. The future of network security is undoubtedly intertwined with the evolution of deep learning, and Palo Alto Networks is at the forefront of this exciting development.