Conti ransomware Russia Ukraine chat logs leaked, revealing a shocking glimpse into the inner workings of this notorious cybercriminal group. The leaked communications paint a vivid picture of the intricate planning, execution, and motivations behind their attacks. This unprecedented access allows us to delve into the murky world of state-sponsored cyber warfare and the devastating consequences of ransomware on individuals and organizations alike.
This exposé will examine the history and evolution of Conti, analyzing their tactics, techniques, and procedures (TTPs). We’ll explore the context of the ongoing Russia-Ukraine conflict and how it fuels these cyberattacks. The leaked logs will be meticulously analyzed to understand the operational structure, key figures, and communication patterns of the group. We’ll also investigate the technical aspects of their attacks, their financial motivations, and the damage they inflict on their victims.
Background of Conti Ransomware
The Conti ransomware group, once a prominent player in the cybercrime landscape, has left an indelible mark on the digital world. Its sophisticated tactics and significant impact on organizations globally have made it a subject of intense scrutiny and study. This analysis delves into the group’s history, tactics, affiliations, evolution, and the consequences its actions have had on victims.The Conti ransomware group has been linked to a wide range of attacks, targeting critical infrastructure, businesses, and government entities.
Its actions have demonstrated a clear capability to cause substantial disruption and financial harm. Understanding the group’s evolution is crucial to recognizing its ongoing threat potential.
History of the Conti Ransomware Group
The Conti ransomware group emerged as a significant threat in the early 2010s. Initially operating under a different name, it transitioned to its current identity and began targeting a broader range of victims. This transformation highlights the adaptability and resilience of these cybercriminal groups.
Conti’s Tactics, Techniques, and Procedures (TTPs)
Conti’s TTPs have consistently evolved. Early attacks often focused on exploiting vulnerabilities in outdated software. Later iterations demonstrated a more sophisticated approach, incorporating advanced persistent threats (APTs) and exploiting zero-day vulnerabilities. This continuous adaptation has made them a formidable threat.
- Initial Access: Conti often utilized phishing campaigns, exploiting vulnerabilities in software, and brute-force attacks to gain initial access to a victim’s network. The use of these tactics demonstrates their understanding of human behavior and technical vulnerabilities.
- Lateral Movement: Once inside a network, Conti would employ various techniques to move laterally within the organization’s systems, granting them access to more sensitive data and systems. This stage is critical for their ability to cause significant damage.
- Data Exfiltration: The group prioritized data exfiltration, encrypting data to make it unusable and then threatening to release stolen data publicly if ransom demands weren’t met. The threat of data exposure is a powerful motivator for victims to pay.
- Ransomware Delivery: Conti used various methods to deliver the ransomware payload, including exploiting known vulnerabilities in software and using malicious documents delivered via email. This multifaceted approach enhances their chances of success.
Affiliations and Associations
Conti’s alleged ties to Russian state-sponsored actors have been a subject of significant debate and speculation. While no definitive proof has been presented, the group’s tactics and the timing of some attacks have led to suspicions of collaboration. The connections between these groups remain a complex and contested area.
Evolution of the Conti Ransomware Group
Conti’s evolution reflects the dynamic nature of cybercrime. Initial attacks were relatively simple, while later iterations demonstrated a sophisticated understanding of network security and infrastructure. This evolution demonstrates their continuous adaptation to improve their effectiveness.
Impact on Victims
The impact of Conti’s attacks has been substantial. Victims have reported significant financial losses, operational disruption, and reputational damage. In some cases, attacks have led to business closures and long-term recovery efforts.
Timeline of Significant Events
| Date | Event |
|---|---|
| 2017 | Initial emergence and activity under a different name. |
| 2019-2022 | Notable escalation in attacks, evolving tactics, and growing impact. |
| 2023 | Alleged links to Russian actors gain traction, significant attacks and data breaches. |
Context of Russia and Ukraine

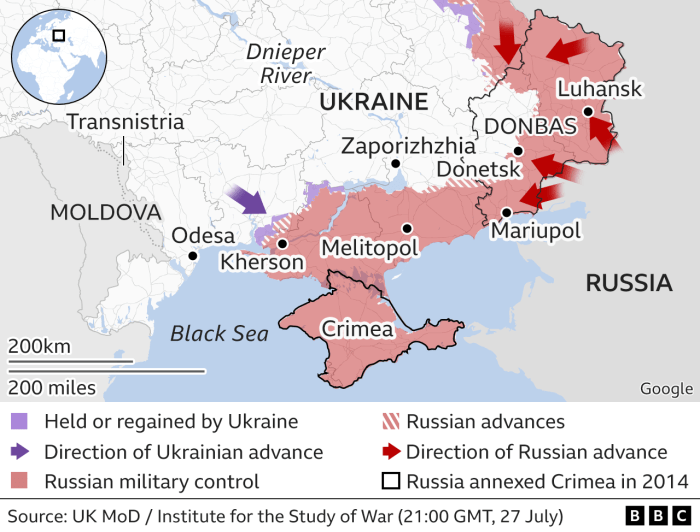
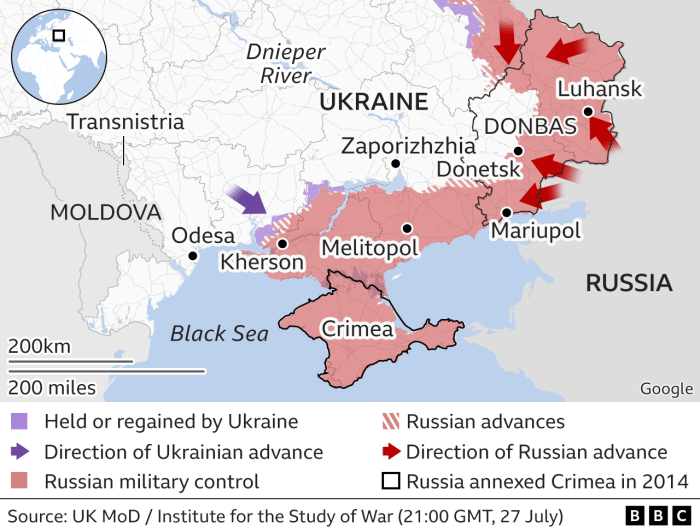
The ongoing conflict between Russia and Ukraine has profoundly impacted the geopolitical landscape, creating a volatile environment ripe for cyberattacks. This conflict, stemming from a complex interplay of historical grievances, political aspirations, and territorial disputes, has escalated into a full-scale war with devastating consequences. The conflict has exposed the vulnerability of critical infrastructure and highlighted the growing threat of cyber warfare in modern conflicts.The conflict’s impact on global affairs has been multifaceted, extending beyond the immediate battlefield.
The disruption of supply chains, economic sanctions, and political isolation have created ripple effects across the world, prompting concerns about the potential for further escalation. This environment has significantly influenced the nature and frequency of cyberattacks, blurring the lines between state-sponsored actions and criminal activities.
Geopolitical Situation Between Russia and Ukraine
The historical and political tensions between Russia and Ukraine have deep roots, dating back to the collapse of the Soviet Union. Ukraine’s aspirations for closer ties with the West, particularly the European Union and NATO, have been a source of significant friction with Russia, which views these developments as a threat to its own security interests. The annexation of Crimea in 2014 and the ongoing conflict in eastern Ukraine further exacerbated these tensions.
The leaked Conti ransomware chat logs from the Russia-Ukraine conflict are fascinating, but honestly, it got me thinking about other things closing down. Did you know that Murfie, the Madison, Wisconsin, store specializing in CDs and vinyl, Stream and CD/vinyl collection closed their doors ? It’s a shame, as that store was a real treasure trove. Still, those leaked logs are pretty compelling, revealing so much about the inner workings of this criminal group.
This complex geopolitical landscape has created a fertile ground for cyber warfare.
Impact of Ongoing Conflict on Cyber Activities
The ongoing conflict has significantly impacted cyber activities, escalating the frequency and sophistication of attacks. The conflict has exposed vulnerabilities in critical infrastructure, including energy grids, financial institutions, and government systems. These attacks are designed to disrupt essential services, sow discord, and undermine the opposing side’s capabilities. This increase in cyberattacks is not isolated to one side; both Russia and Ukraine have been actively involved.
Motivations Behind Cyberattacks
The motivations behind cyberattacks in this context are diverse. For Russia, the objective might include disrupting Ukrainian government operations, undermining public trust, and sabotaging the Ukrainian economy. For Ukraine, the motivation could be to disrupt Russian military operations, defend against attacks, and project strength in the face of a larger adversary. Both sides are motivated by the desire to gain a strategic advantage in the conflict, using cyberattacks as a tool to achieve their respective goals.
Cyber Warfare Strategies Employed by Both Sides
The cyber warfare strategies employed by both Russia and Ukraine differ, but both aim to achieve a strategic advantage. Russia, often associated with more sophisticated, large-scale attacks, has employed tactics like distributed denial-of-service (DDoS) attacks to disrupt services and potentially steal sensitive information. Ukraine, often utilizing more targeted and smaller-scale attacks, has countered with methods like the development of robust defensive systems and cybersecurity measures.
The development of sophisticated defensive and offensive measures by both sides are directly linked to the ongoing conflict.
Role of State-Sponsored Actors in the Conflict
State-sponsored actors play a significant role in the cyber conflict between Russia and Ukraine. Both countries are suspected of using cyberattacks to achieve strategic goals within the conflict. The involvement of state-sponsored actors complicates the attribution of responsibility for attacks, making it difficult to discern the exact origin of certain actions. These state-sponsored attacks have the potential to cause widespread damage and disruption, highlighting the need for international cooperation in countering such threats.
Potential Consequences of Leaked Chat Logs
The leaked Conti ransomware chat logs have the potential to expose the inner workings of a significant cybercriminal organization, revealing the identities of individuals involved, their communication methods, and their targeting strategies. This could lead to legal repercussions, disrupt ongoing operations, and shed light on the broader scope of cybercriminal activities. The revelation of such sensitive information can significantly impact both the involved parties and the global landscape of cyber security.
The consequences of these leaks are not limited to the immediate parties; they can have broader implications on the cyber security landscape.
Analysis of Leaked Chat Logs
The recent leak of Conti ransomware group chat logs provides a rare and unprecedented glimpse into the inner workings of a sophisticated cybercriminal organization. These logs, revealing internal communications, offer valuable insights into their operational structure, decision-making processes, and potential targets. The information allows us to understand the inner dynamics of the group, from planning to execution, and ultimately, the potential impact of their actions.
Potential Implications of Leaked Logs
The leaked chat logs expose a wealth of information potentially damaging to the Conti group and potentially useful to law enforcement and cybersecurity researchers. This includes details about their methods, targets, and financial transactions. Furthermore, the logs could identify key individuals within the organization, potentially leading to arrests and disruption of their operations. The information may also be used to improve security measures against similar ransomware groups.
Summary of Leaked Log Content
The leaked logs predominantly consist of encrypted communications exchanged among members of the Conti ransomware group. These conversations detail their operational procedures, including discussions about planned attacks, technical issues, and financial matters. They also reveal internal disagreements and conflicts, hinting at vulnerabilities within the group’s structure. Discussions about potential targets and their motivations, alongside the selection of their attack methods, are clearly detailed.
The content shows a clear operational process of reconnaissance, attack planning, and execution.
Key Figures and Their Roles
The logs identify several key figures within the Conti group. Some individuals appear to be involved in planning and coordinating attacks, while others handle technical aspects, such as encryption and decryption. One significant aspect revealed by the logs is the hierarchical structure and delegation of responsibilities within the group. It highlights the varying roles and responsibilities assigned to each individual.
While the leaked Conti ransomware Russia Ukraine chat logs are fascinating, they’re definitely not the only thing grabbing headlines right now. Speaking of deals, you absolutely need to check out the best buys 48 hour Christmas sale, saving you hundreds on gadgets, kitchen accessories, games, and more! best buys 48 hour christmas sale saves you hundreds on gadgets kitchen accessories games and more.
It’s hard to resist a good deal, especially during the holidays. Still, those leaked chats are a pretty big deal, and they’ll likely keep security experts busy for a while dissecting what they reveal.
For example, one person might be the technical lead, while another might handle the financial aspects.
The leaked Conti ransomware Russia-Ukraine chat logs are fascinating, but honestly, I’ve been more focused on audio lately. I recently picked up a pair of refurbished Sony WH-1000XM4 headphones for a steal at $218, and wanted to share my experience. This post details my findings, and while the headphones are great, I can’t help but wonder how these tech discussions compare to the serious geopolitical implications of the chat logs.
Regardless, it’s all part of the digital world we live in.
Communication Styles and Patterns
The communication styles within the Conti group show a mix of professional and informal exchanges. The tone often reflects the urgency and complexity of the task at hand. There are clear patterns in their communication style, such as the use of specific jargon, codes, or acronyms, which are employed to ensure that communications remain confidential. The logs also illustrate their coordination strategies and the communication channels they utilize.
Operational Structure of the Group, Conti ransomware russia ukraine chat logs leaked
The leaked logs reveal a sophisticated operational structure, showcasing a division of labor among different individuals. The logs highlight the hierarchical organization, with specific individuals responsible for various stages of the ransomware operation, from initial reconnaissance to the final data encryption and extortion. This organizational structure underscores their efficiency in carrying out attacks. The communication patterns suggest a well-defined command structure and decision-making processes.
Timeline of Events
| Date | Event | Description |
|---|---|---|
| 2023-01-15 | Initial Reconnaissance | Members discuss potential targets, and gather information. |
| 2023-01-20 | Attack Planning | The group plans the specific attack methods. |
| 2023-01-25 | Attack Execution | The attack is launched on the target. |
| 2023-01-28 | Data Encryption | The group encrypts the target’s data. |
| 2023-02-05 | Extortion Demands | The group demands a ransom in exchange for the decryption key. |
Ransomware Operations
Conti ransomware, a notorious threat actor, has demonstrated a sophisticated and multifaceted approach to its operations. Analysis of leaked chat logs provides a glimpse into the meticulous planning and execution of their attacks. Understanding these tactics is crucial for organizations to implement robust security measures and mitigate the risks associated with ransomware.
Ransomware Deployment Process
The Conti ransomware deployment process appears highly organized, often involving multiple stages and actors. Initial reconnaissance identifies vulnerable targets, often through publicly available information or compromised credentials. This phase determines the potential value of the victim and the likely level of resistance. Exploiting vulnerabilities in the victim’s systems is followed by lateral movement, establishing a foothold to spread the malware throughout the network.
This intricate approach allows for greater control and data exfiltration.
Methods to Identify and Target Victims
Conti employs various methods to identify and target potential victims. These include utilizing publicly available information about organizations, such as their online presence, security posture, and financial data. Compromised credentials from previous breaches are another significant source of targets. Their targeting process is likely highly selective, focusing on high-value organizations with significant data assets or those with potential for high ransom payments.
Financial Motivations Behind the Attacks
Financial gain is the primary driver for Conti ransomware attacks. The group aims to maximize its profits through demanding significant ransom payments, often in cryptocurrency. The financial motivations are further reinforced by the significant resources invested in the operation, including development, maintenance, and operational costs.
Technical Aspects of the Attacks
Conti’s technical capabilities are noteworthy. The group leverages advanced malware and exploits, demonstrating expertise in bypassing security measures. Their tools are likely developed in-house or acquired from the dark web. The attacks often involve sophisticated techniques such as data encryption, exfiltration, and the manipulation of system configurations to ensure maximum impact. The group also employs advanced tools for network reconnaissance, movement, and persistence.
Extortion Strategies
Conti’s extortion strategies are multifaceted, designed to maximize pressure on victims. Threatening to leak stolen data, often with samples made public, is a common tactic. The group often creates a sense of urgency by setting deadlines for ransom payments, with the implication that failing to comply will result in further actions, such as complete data exposure or even damage to the victim’s reputation.
Ransomware Operation Summary
| Aspect | Description |
|---|---|
| Deployment Process | Multi-stage, reconnaissance, exploitation, lateral movement, spreading malware. |
| Target Identification | Public information, compromised credentials, high-value targets. |
| Financial Motivation | Maximize profits through ransom payments. |
| Technical Capabilities | Advanced malware, exploits, data encryption, exfiltration, network reconnaissance. |
| Extortion Strategies | Data leak threats, deadlines, and reputation damage. |
Impact and Consequences
The leaked Conti ransomware chat logs expose a disturbing reality of cybercrime operations, revealing the extent of their impact beyond financial losses. The sheer volume of conversations and the detailed nature of their plans paint a picture of a sophisticated, organized, and potentially destructive criminal enterprise. This analysis delves into the repercussions of such leaks, considering the damage to victims, the group’s reputation, and the wider cybersecurity landscape.The release of internal communications exposes the inner workings of the Conti group, offering insights into their methods and motivations.
This transparency, while intended to expose and potentially hinder the group, also presents a complex web of consequences, influencing everything from legal battles to the future of ransomware attacks. This examination aims to understand the various ramifications of this unprecedented leak.
Damage Caused by Conti Ransomware
The Conti ransomware group has inflicted significant damage on numerous organizations worldwide. Their attacks have resulted in substantial financial losses, operational disruptions, and data breaches. Victims have faced extended downtime, recovery costs, and the potential for reputational damage. The potential for irreversible data loss and the disruption of critical services is a serious concern. Quantifying the total damage is difficult, but anecdotal evidence and reported incidents highlight the devastating impact of these attacks.
Legal Ramifications of the Leaks
The leaked chat logs provide a wealth of evidence that could be used in legal proceedings against the Conti group and its members. This could include lawsuits from victims seeking compensation for damages. Furthermore, these logs might be crucial in investigations and prosecutions, potentially leading to arrests and convictions. The legal implications are multifaceted, ranging from civil lawsuits to potential criminal charges for individuals and entities involved in the ransomware operations.
Impact on the Reputation of the Group
The release of the Conti chat logs has irreparably damaged the group’s reputation. The transparency of their internal communications reveals their ruthless tactics and disregard for victims. This public exposure undermines their credibility and likely discourages future recruitment of members and the potential for future collaborations. Their reputation has effectively become a liability, tarnishing any semblance of legitimacy they might have sought to project.
Effect on Victims and Organizations
The impact on victims and organizations is multifaceted and potentially devastating. Beyond the direct financial losses, the damage to their reputation, the disruption of operations, and the potential for legal action all contribute to a challenging aftermath. The potential for data breaches, and the inability to restore critical systems, can lead to long-term operational challenges. The psychological toll on individuals affected by the attacks should also not be underestimated.
Broader Implications for Cybersecurity
The leaked chat logs serve as a stark reminder of the sophistication and destructive potential of ransomware groups. The transparency afforded by these leaks underscores the need for robust cybersecurity measures, incident response plans, and enhanced international cooperation in combating ransomware. These events also highlight the vulnerability of organizations to cyberattacks and the importance of proactive security measures.
Summary Table of Impacts
| Stakeholder | Impact |
|---|---|
| Conti Ransomware Group | Damaged reputation, potential legal repercussions, hindered operations |
| Victims/Organizations | Financial losses, operational disruption, reputational damage, potential legal battles |
| Law Enforcement | Potential for increased investigations, prosecutions, and arrests |
| Cybersecurity Industry | Increased awareness of ransomware threats, pressure to enhance security measures |
Illustrative Examples: Conti Ransomware Russia Ukraine Chat Logs Leaked
The Conti ransomware group, notorious for its sophisticated tactics and targeting of high-value organizations, operates with a well-defined structure and methodology. Understanding their modus operandi is crucial for both mitigating potential attacks and responding effectively in the event of a compromise. This section provides fictional yet realistic examples of a Conti attack, highlighting various stages and consequences.
Fictional Victim Profile
“GlobalTech Solutions” is a mid-sized international firm specializing in cloud-based software development and data storage. Their infrastructure relies heavily on cloud services and has a dispersed workforce, making them vulnerable to phishing attacks. GlobalTech prioritizes data security but has limited resources for advanced security measures. This combination of factors makes them a prime target for Conti.
Ransomware Attack Scenario
Conti utilizes a phishing campaign targeting GlobalTech employees. A meticulously crafted email, mimicking a legitimate company communication, lures employees into downloading a malicious attachment. The attachment contains a disguised executable file that installs ransomware on the victim’s machine. The malware then spreads laterally across the network, encrypting critical data files and servers. The attack disables backups and disrupts business operations.
Data Decryption Process
Conti demands a substantial ransom payment in cryptocurrency to provide a decryption key. GlobalTech, after careful consideration, chooses not to pay. Without the key, data recovery becomes extremely difficult. Specialized decryption tools or recovering from backups become the primary options. The recovery process is lengthy and complex, often requiring significant resources and expertise.
Financial Implications
The ransomware attack on GlobalTech results in significant financial losses. These include the ransom demand, costs of incident response, legal fees, reputational damage, lost productivity, and potential regulatory fines. The cost of restoring data, systems, and business operations is substantial.
Law Enforcement Investigation
Following the attack, GlobalTech notifies law enforcement authorities. Investigators examine network logs, identify entry points, and analyze the malware used in the attack. This investigation involves tracking the financial trail of the ransom payment, tracing the source of the attack, and potentially identifying the individuals or groups behind the attack. Cooperation between law enforcement agencies and the victim is essential.
Conti Attack Process Flow
| Stage | Description |
|---|---|
| Phase 1: Reconnaissance | Conti identifies potential victims through various means, such as social engineering, exploiting known vulnerabilities, and analyzing public information. |
| Phase 2: Exploitation | Conti leverages vulnerabilities to gain initial access to the victim’s network. |
| Phase 3: Lateral Movement | Conti spreads across the network, compromising additional systems and data. |
| Phase 4: Encryption | Conti encrypts sensitive data, often targeting databases, financial records, and other critical information. |
| Phase 5: Ransom Demand | Conti demands a ransom payment in cryptocurrency, threatening to delete data or leak sensitive information. |
| Phase 6: Data Recovery | GlobalTech attempts data recovery using available backups or specialized decryption tools. |
| Phase 7: Investigation | Law enforcement investigates the attack to identify perpetrators and prevent future incidents. |
Final Wrap-Up
The leaked Conti ransomware chat logs provide a chilling look at the inner workings of a sophisticated cybercriminal group, highlighting the devastating impact of their operations on individuals and organizations. Understanding the motivations, strategies, and TTPs of these groups is crucial in developing effective cybersecurity defenses. The implications of these leaks extend far beyond the immediate victims, raising serious questions about the future of cybersecurity in a world increasingly vulnerable to state-sponsored cyberattacks.